Home >Java >javaTutorial >How to solve the problem of specifying jackson version in SpringBoot upgrade
How to solve the problem of specifying jackson version in SpringBoot upgrade
- 王林forward
- 2023-05-12 14:13:352774browse
[Vulnerability Notice]
On February 19, NVD issued a security notice disclosing the remote code execution
vulnerability (CVE-2020-8840) in jackson-databind caused by JNDI injection. The CVSS score is 9.8. The affected version of jackson-databind lacks
certain xbean-reflect/JNDI blacklist classes, such as org.apache.xbean.propertyeditor.JndiConverter,
which can lead to attackers using JNDI injection to implement remote code implement. At present, the manufacturer has released a new version to complete the vulnerability repair.
Relevant users are requested to upgrade in time for protection.
Since the Springboot version used in the project is 2.1.3, and the built-in jackson version is 2.9.8, which is lower than the safe version
2.9.10.6, so the jackson version needs to be upgraded.
Modify the jackson version in Springboot
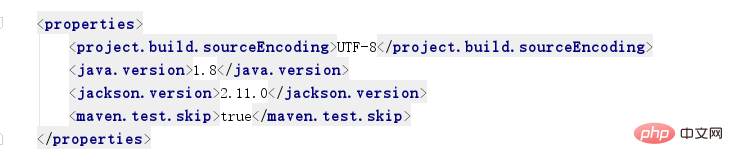
Add the jackson.version attribute under the properties tag in the project's pom.xml
<jackson.version>2.11.0</jackson.version>
If you only want to modify the jackson-databind version, add the jackson.version.databind attribute
<jackson.version.databind>${jackson.version}</jackson.version.databind>The above is the detailed content of How to solve the problem of specifying jackson version in SpringBoot upgrade. For more information, please follow other related articles on the PHP Chinese website!

