Large, sensitive data sets are often used to train AI models, creating privacy and data leakage risks. The use of artificial intelligence increases an organization’s threat vectors and expands its attack surface. AI further creates new opportunities for benign errors to adversely impact models and business results.

Risks that are not understood cannot be mitigated. A recent Gartner survey of chief information security officers revealed that most organizations have not considered the new security and business risks posed by artificial intelligence or the new controls they must put in place to mitigate those risks. Artificial intelligence requires new risk and safety management measures and mitigation frameworks.
Here are the top five priorities security and risk leaders should focus on to effectively manage AI risk and security within their organizations:
1. Capture AI exposure
Machine learning models are opaque to most users, and unlike general software systems, their inner workings are unknown to even the most skilled experts. Data scientists and model developers often understand what their machine learning models are trying to do, but they cannot always decipher the internal structure or algorithmic means by which the model processes the data.
This lack of understanding severely limits an organization’s ability to manage AI risks. The first step in AI risk management is to list all AI models used in the organization, whether they are components of third-party software, developed in-house, or accessed through software-as-a-service applications. This should include identifying interdependencies between the various models. Models are then ranked based on operational impact, taking into account that risk management controls can be applied incrementally based on identified priorities.
Once the models are laid out, the next step is to make them as interpretable or explainable as possible. “Explainability” means the ability to generate details, reasons, or explanations that clarify the functionality of the model for a specific audience. This will provide risk and security managers with an environment to manage and mitigate business, social, liability and security risks arising from model outcomes.
2. Improve employee awareness through artificial intelligence risk education activities
Employee awareness is an important component of artificial intelligence risk management. First, let all players, including CISOs, chief privacy officers, chief data officers, and legal and compliance officers, recalibrate their mindsets about AI. They should understand that AI is “unlike any other application” – it poses unique risks and requires specific controls to mitigate such risks. Then, engage with business stakeholders to expand understanding of the AI risks that need to be managed.
Work with these stakeholders to determine the best way to build AI knowledge across teams and over time. For example, see if you can add a course on basic AI concepts to your enterprise’s learning management system. Work with application and data security departments to help develop AI knowledge among all organizational members.
3. Eliminate AI data exposure with a privacy plan
According to a recent Gartner survey, privacy and security have been viewed as artificial. The main obstacles to the realization of intelligence. Adopting data protection and privacy procedures can effectively eliminate the exposure of internal and shared data within AI.
There are a range of methods that can be used to access and share essential data while still meeting privacy and data protection requirements. Determine which data privacy technology, or combination of technologies, makes the most sense for your organization’s specific use cases. For example, investigate techniques such as data masking, synthetic data generation, or differential privacy.
Data privacy requirements should be met when exporting or importing data to external organizations. In these scenarios, techniques like fully homomorphic encryption and secure multi-party computation should be more useful than protecting data from internal users and data scientists.
4. Incorporate risk management into model operations
AI models require special-purpose processes as part of model operations or ModelOps to enable human Smart, reliable and efficient. As environmental factors continue to change, AI models must continuously monitor for business value leakage and unpredictable (and sometimes adverse) outcomes.
Effective monitoring requires an understanding of AI models. Dedicated risk management processes must become an integral part of ModelOps to make AI more trustworthy, accurate, fair, and resilient to adversarial attacks or benign errors.
Controls should be applied continuously—for example, throughout model development, testing and deployment, and ongoing operations. Effective controls will detect malicious behavior, benign errors, and unintended changes in AI data or models that lead to unfairness, corruption, inaccuracies, poor model performance and predictions, and other unintended consequences.
5. Use artificial intelligence security measures to deal with adversarial attacks
Detecting and blocking attacks on artificial intelligence requires new technologies. Malicious attacks on AI can result in significant organizational damage and loss, including financial, reputational, or data related to intellectual property, sensitive customer data, or proprietary data. Application leaders working with security must add controls to their AI applications to detect anomalous data input, malicious attacks, and benign input errors.
Implement a comprehensive set of traditional enterprise security controls around AI models and data, as well as new integrity measures for AI, such as training models that tolerate adversarial AI. Finally, use fraud, anomaly detection and bot detection technologies to prevent AI data poisoning or input error detection.
The above is the detailed content of How to manage AI risk and safety?. For more information, please follow other related articles on the PHP Chinese website!
 How to Run LLM Locally Using LM Studio? - Analytics VidhyaApr 19, 2025 am 11:38 AM
How to Run LLM Locally Using LM Studio? - Analytics VidhyaApr 19, 2025 am 11:38 AMRunning large language models at home with ease: LM Studio User Guide In recent years, advances in software and hardware have made it possible to run large language models (LLMs) on personal computers. LM Studio is an excellent tool to make this process easy and convenient. This article will dive into how to run LLM locally using LM Studio, covering key steps, potential challenges, and the benefits of having LLM locally. Whether you are a tech enthusiast or are curious about the latest AI technologies, this guide will provide valuable insights and practical tips. Let's get started! Overview Understand the basic requirements for running LLM locally. Set up LM Studi on your computer
 Guy Peri Helps Flavor McCormick's Future Through Data TransformationApr 19, 2025 am 11:35 AM
Guy Peri Helps Flavor McCormick's Future Through Data TransformationApr 19, 2025 am 11:35 AMGuy Peri is McCormick’s Chief Information and Digital Officer. Though only seven months into his role, Peri is rapidly advancing a comprehensive transformation of the company’s digital capabilities. His career-long focus on data and analytics informs
 What is the Chain of Emotion in Prompt Engineering? - Analytics VidhyaApr 19, 2025 am 11:33 AM
What is the Chain of Emotion in Prompt Engineering? - Analytics VidhyaApr 19, 2025 am 11:33 AMIntroduction Artificial intelligence (AI) is evolving to understand not just words, but also emotions, responding with a human touch. This sophisticated interaction is crucial in the rapidly advancing field of AI and natural language processing. Th
 12 Best AI Tools for Data Science Workflow - Analytics VidhyaApr 19, 2025 am 11:31 AM
12 Best AI Tools for Data Science Workflow - Analytics VidhyaApr 19, 2025 am 11:31 AMIntroduction In today's data-centric world, leveraging advanced AI technologies is crucial for businesses seeking a competitive edge and enhanced efficiency. A range of powerful tools empowers data scientists, analysts, and developers to build, depl
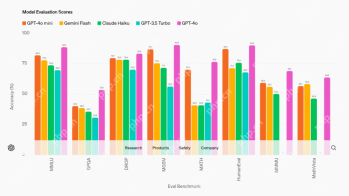 AV Byte: OpenAI's GPT-4o Mini and Other AI InnovationsApr 19, 2025 am 11:30 AM
AV Byte: OpenAI's GPT-4o Mini and Other AI InnovationsApr 19, 2025 am 11:30 AMThis week's AI landscape exploded with groundbreaking releases from industry giants like OpenAI, Mistral AI, NVIDIA, DeepSeek, and Hugging Face. These new models promise increased power, affordability, and accessibility, fueled by advancements in tr
 Perplexity's Android App Is Infested With Security Flaws, Report FindsApr 19, 2025 am 11:24 AM
Perplexity's Android App Is Infested With Security Flaws, Report FindsApr 19, 2025 am 11:24 AMBut the company’s Android app, which offers not only search capabilities but also acts as an AI assistant, is riddled with a host of security issues that could expose its users to data theft, account takeovers and impersonation attacks from malicious
 Everyone's Getting Better At Using AI: Thoughts On Vibe CodingApr 19, 2025 am 11:17 AM
Everyone's Getting Better At Using AI: Thoughts On Vibe CodingApr 19, 2025 am 11:17 AMYou can look at what’s happening in conferences and at trade shows. You can ask engineers what they’re doing, or consult with a CEO. Everywhere you look, things are changing at breakneck speed. Engineers, and Non-Engineers What’s the difference be
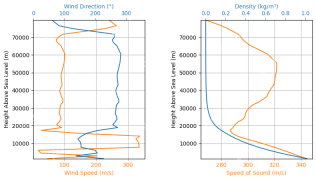 Rocket Launch Simulation and Analysis using RocketPy - Analytics VidhyaApr 19, 2025 am 11:12 AM
Rocket Launch Simulation and Analysis using RocketPy - Analytics VidhyaApr 19, 2025 am 11:12 AMSimulate Rocket Launches with RocketPy: A Comprehensive Guide This article guides you through simulating high-power rocket launches using RocketPy, a powerful Python library. We'll cover everything from defining rocket components to analyzing simula


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Mac version
God-level code editing software (SublimeText3)

SublimeText3 English version
Recommended: Win version, supports code prompts!

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.






