 Technology peripherals
Technology peripherals AI
AI Human and machine intelligence: Artificial intelligence in security operations
Human and machine intelligence: Artificial intelligence in security operationsHuman and machine intelligence: Artificial intelligence in security operations
Most commercial AI success is related to supervised machine learning ML. Examples include smart home assistants’ understanding of spoken language and self-driving cars’ object recognition, all leveraging the vast amounts of labeled data and computation required to train complex deep learning models. However, in the field of network security, although AI can be used to improve the efficiency and scale of security operations teams, it requires a high degree of human participation, otherwise it cannot solve most network security problems, at least for now.

#In addition, the digital noise generated by human behavior in the enterprise environment makes anomalies in the system common, making it impossible to determine whether they represent attacks. . Therefore, the effect of abnormal behavior detection based on artificial intelligence is not ideal. For example, a large enterprise that produces 1 billion remote sensing data per day uses machine learning to detect threats. Even if its accuracy is 99.9%, it means finding the real attack event among 1 million false positives. Overcoming this imbalance in detection data requires a lot of professional knowledge and a multi-pronged approach. detection strategy.
But obviously without AI, things can only get worse. There are still ways to harness the power of machine learning to improve operational efficiency. Here are three principles that security operations teams are advised to consider:
1. Human and machine intelligence
Artificial intelligence is a supplement to human intelligence, not a replacement. In the environment of complex systems, especially when confronting rapidly adapting and intelligent opponents, automation technology with active learning as its core will bring extremely high value. The main job of humans is to regularly check the machine learning system, add new examples, and continuously adjust and iterate.
2. Choose the right tools
#You don’t need to be an AI expert to make good decisions, but the premise is to make sure you choose the right tools The right tools.
- First, it’s important to understand the difference between anomalous behavior and malicious behavior, as they are often two different things and rely on very different detection techniques. The former is easily discovered through unsupervised anomaly detection and does not require labeled training data. But the latter requires supervised learning, often requiring many historical examples.
- Secondly, alerts with a high signal-to-noise ratio are critical for security operations teams to fully understand the possible impact of detection results, as these systems will not be 100% accurate.
- Finally, although almost all kinds of machine learning techniques are already used in the field of network security, it is still very important to accumulate a large number of threat intelligence signatures, because once running into these signatures, the attack is almost certain, saving a lot of correlation analysis work. At all times, signatures are a critical baseline for detecting known threats.
3. Security operations require automation
It’s ironic that many cybersecurity professionals who trust AI to drive their cars, Skeptical about the role of artificial intelligence in cybersecurity countermeasures. However, today, when massive amounts of data and alarms need to be processed, automated operations are one of the most effective ways to improve the efficiency of the security operations team, and it is basically the only solution in the future.
Automation frees creative minds from time-consuming operational tasks, especially useful when detecting advanced threats, correlating analysis, prioritizing, and automating low-risk control measures (such as quarantining suspicious files or requiring users to re-verify), these can significantly improve security operation efficiency and reduce network risks.
To sum up, artificial intelligence or machine learning cannot become the only cybersecurity strategy, at least in the foreseeable future. When looking for clues in the vast sea of data, combining machine intelligence with the human intelligence of security experts is the most practical and effective technical means.
The above is the detailed content of Human and machine intelligence: Artificial intelligence in security operations. For more information, please follow other related articles on the PHP Chinese website!
 Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AM
Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AMScientists have extensively studied human and simpler neural networks (like those in C. elegans) to understand their functionality. However, a crucial question arises: how do we adapt our own neural networks to work effectively alongside novel AI s
 New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AM
New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AMGoogle's Gemini Advanced: New Subscription Tiers on the Horizon Currently, accessing Gemini Advanced requires a $19.99/month Google One AI Premium plan. However, an Android Authority report hints at upcoming changes. Code within the latest Google P
 How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AM
How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AMDespite the hype surrounding advanced AI capabilities, a significant challenge lurks within enterprise AI deployments: data processing bottlenecks. While CEOs celebrate AI advancements, engineers grapple with slow query times, overloaded pipelines, a
 MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AM
MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AMHandling documents is no longer just about opening files in your AI projects, it’s about transforming chaos into clarity. Docs such as PDFs, PowerPoints, and Word flood our workflows in every shape and size. Retrieving structured
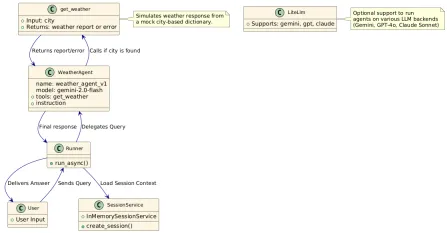 How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AM
How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AMHarness the power of Google's Agent Development Kit (ADK) to create intelligent agents with real-world capabilities! This tutorial guides you through building conversational agents using ADK, supporting various language models like Gemini and GPT. W
 Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AM
Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AMsummary: Small Language Model (SLM) is designed for efficiency. They are better than the Large Language Model (LLM) in resource-deficient, real-time and privacy-sensitive environments. Best for focus-based tasks, especially where domain specificity, controllability, and interpretability are more important than general knowledge or creativity. SLMs are not a replacement for LLMs, but they are ideal when precision, speed and cost-effectiveness are critical. Technology helps us achieve more with fewer resources. It has always been a promoter, not a driver. From the steam engine era to the Internet bubble era, the power of technology lies in the extent to which it helps us solve problems. Artificial intelligence (AI) and more recently generative AI are no exception
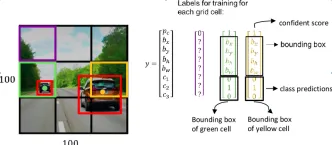 How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AM
How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AMHarness the Power of Google Gemini for Computer Vision: A Comprehensive Guide Google Gemini, a leading AI chatbot, extends its capabilities beyond conversation to encompass powerful computer vision functionalities. This guide details how to utilize
 Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AM
Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AMThe AI landscape of 2025 is electrifying with the arrival of Google's Gemini 2.0 Flash and OpenAI's o4-mini. These cutting-edge models, launched weeks apart, boast comparable advanced features and impressive benchmark scores. This in-depth compariso


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment






