Consumer drones were originally just expensive toys, but now they have become swords on the battlefield. They can be turned into high-altitude monitoring platforms that can search and detect battlefields, and can throw weapons. The operator can hide in the distance to ensure safety. . However, hackers have now found a loophole in DJI drones that can locate the operator and leave him nowhere to hide.

In fact, the drone has been broadcasting the operator's location information. Only cheap radio hardware and software tools are needed to eavesdrop on the radio signal and obtain the operator's coordinates after decoding it. .
Not long ago, at the NDSS (Network and Distributed System Security Symposium) in San Diego, the United States, researchers from Ruhr-Universität Bochum in Germany and the Helmholtz Center for Information Security in Germany (CISPA) Prove to the public that they can crack DJI drone radio signals and decode a radio protocol used by DJI called DroneID. After cracking it, researchers found that the DroneID of each DJI drone not only transmitted the machine's own GPS location and unique drone identity information, it also transmitted the operator's GPS coordinate information.
Researchers found 16 vulnerabilities and they have notified DJI. The drones tested included Mini 2, Air 2, and Mavic 2.
The reason why the DroneID system was originally designed was mainly to facilitate the government, regulatory agencies, and law enforcement departments to monitor drones and prevent drones from being abused. But hackers and security researchers warn that DroneID is not encrypted and is open to anyone who can receive the radio signal. German researchers have proven that radio signals can be completely deciphered and hackers can easily obtain the coordinates of the operator.
If this is the case, using consumer drones to fight on the battlefield will become very dangerous. In September this year, the U.S. FAA will implement new regulations that require all consumer drones to be equipped with a system similar to DroneID. This regulation may make safety risks more serious.
Moritz Schloegel, a researcher at Ruhr-University Bochum, said: "This problem is serious, isn't it? You think that the drone only transmits the machine's own position, but it also transmits the operator's position. If you If you value privacy or are in a conflict zone, you will definitely be uneasy."
In fact, there is nothing new in determining the operator's coordinates. DJI sells a device called Aeroscope to government regulators and law enforcement agencies. A device that can receive and decode DroneID data to determine the drone's location and determine where the operator is, up to 30 miles (48 kilometers) away. Aeroscope can protect airport runways from interference and can protect public venues.
German researchers dug deeper. They analyzed DJI drone firmware and drone radio communication mechanisms, reverse engineered DroneID, and developed a new set of tools that can receive DroneID transmission signals. The components used in the tool are very simple, including Ettus software-defined radio equipment and the cheaper HackRF. Most Ettus equipment sells for just over $1,000, and HackRF is even cheaper, only a few hundred dollars. By assembling cheap equipment together and using software developed by researchers, it is possible to completely decipher the signal and determine the operator's position, which is similar to an Aeroscope.
Although the German researchers only eavesdropped on DJI drones within a range of 15-25 feet (4.6 meters-7.6 meters), they believe that with a little engineering effort they can expand the coverage. Last summer hacker Conner Bender published an article in which he discovered that DroneID data could be obtained from hundreds or even thousands of feet away using a HackRF-based system paired with a custom antenna.
The U.S. government once issued an order that it needed a drone monitoring system. In response, Brendan Schulman, former vice president of policy and legal affairs at DJI, participated in the development of DroneID in 2017. He said that the requirement at that time was that the signal could not be encryption. The FAA and the U.S. Congress believe that from a public safety perspective, anyone should be able to determine the location of a drone and its operator without the need for hacking tools or DJI-specific tools. It can be easily monitored using a mobile phone or tablet.
Schulmany said: “During lengthy FAA advisory committee discussions in 2017, we were told that operator location should be an important component of remote identification for U.S. government security purposes. The United States wants location to be available to the public. The information, like a car license plate, can be seen by everyone, so if people are concerned about drone interference, they can report it to regulatory agencies."
The United States wants drones to broadcast the operator's location, and it also wants Drones can be connected to surveillance service networks that record detailed flight trajectories of each operator, and government agencies can access the database at any time. Schulman believes that the U.S. request is too "intrusive." Schulman also said that the DroneID problem is not unique to DJI. After the new FAA regulations are implemented this year, all consumer drones on the market will have a DroneID-like system. (Knife)
The above is the detailed content of What? Hackers can pinpoint DJI drone operator's location. For more information, please follow other related articles on the PHP Chinese website!
 Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AM
Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AMCyberattacks are evolving. Gone are the days of generic phishing emails. The future of cybercrime is hyper-personalized, leveraging readily available online data and AI to craft highly targeted attacks. Imagine a scammer who knows your job, your f
 Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AM
Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AMIn his inaugural address to the College of Cardinals, Chicago-born Robert Francis Prevost, the newly elected Pope Leo XIV, discussed the influence of his namesake, Pope Leo XIII, whose papacy (1878-1903) coincided with the dawn of the automobile and
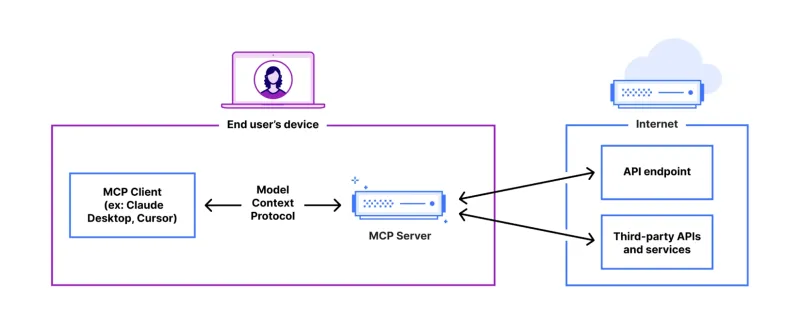 FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AM
FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AMThis tutorial demonstrates how to integrate your Large Language Model (LLM) with external tools using the Model Context Protocol (MCP) and FastAPI. We'll build a simple web application using FastAPI and convert it into an MCP server, enabling your L
 Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AM
Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AMExplore Dia-1.6B: A groundbreaking text-to-speech model developed by two undergraduates with zero funding! This 1.6 billion parameter model generates remarkably realistic speech, including nonverbal cues like laughter and sneezes. This article guide
 3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AM
3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AMI wholeheartedly agree. My success is inextricably linked to the guidance of my mentors. Their insights, particularly regarding business management, formed the bedrock of my beliefs and practices. This experience underscores my commitment to mentor
 AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AM
AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AMAI Enhanced Mining Equipment The mining operation environment is harsh and dangerous. Artificial intelligence systems help improve overall efficiency and security by removing humans from the most dangerous environments and enhancing human capabilities. Artificial intelligence is increasingly used to power autonomous trucks, drills and loaders used in mining operations. These AI-powered vehicles can operate accurately in hazardous environments, thereby increasing safety and productivity. Some companies have developed autonomous mining vehicles for large-scale mining operations. Equipment operating in challenging environments requires ongoing maintenance. However, maintenance can keep critical devices offline and consume resources. More precise maintenance means increased uptime for expensive and necessary equipment and significant cost savings. AI-driven
 Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AM
Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AMMarc Benioff, Salesforce CEO, predicts a monumental workplace revolution driven by AI agents, a transformation already underway within Salesforce and its client base. He envisions a shift from traditional markets to a vastly larger market focused on
 AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AM
AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AMThe Rise of AI in HR: Navigating a Workforce with Robot Colleagues The integration of AI into human resources (HR) is no longer a futuristic concept; it's rapidly becoming the new reality. This shift impacts both HR professionals and employees, dem


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 Linux new version
SublimeText3 Linux latest version

WebStorm Mac version
Useful JavaScript development tools






