 Technology peripherals
Technology peripherals AI
AI To prevent and control 'fake grass planting”, Xiaohongshu's technical team has done these major things
To prevent and control 'fake grass planting”, Xiaohongshu's technical team has done these major thingsThis article mainly focuses on the best practice area of community and e-commerce risk control in Xiaohongshu - brush volume management.
As a content community, the number of monthly active users of Xiaohongshu has been growing steadily since it exceeded 200 million in October 2021. Based on the continuous accumulation of UGC content assets, Xiaohongshu is becoming a diverse lifestyle gathering place for more and more users. All these have made Xiaohongshu a target for illegal production.
From the user perspective, security needs to solve two problems on the content platform: Ensure that user information is safe on the Internet, and ensure that the information users obtain on the Internet is authentic.
Volume brushing, as a common cheating method in the community and transactions, will cause the information obtained by users to be untrue. Whether it is community traffic such as note reading, likes, and comments, or e-commerce data such as product views and sales, obtained through brushing, it will undermine our content security and affect users' trust in the platform.
1. Enter the black industry to understand the realization of brush volume
1.1 What is brush volume?
In a basic understanding, volume brushing can be understood as data fraud, such as using cheating methods to obtain false likes, collections and other data, in order to obtain higher commercial value. In the e-commerce scenario, brushing is more concentrated at the merchant level, such as hiring brushing users and using fake logistics to structure transactions and fabricate high GMV.
In order to deeply understand the nature of brush volume, we visited a group of companies specializing in the brush volume industry chain. The following is an introduction to three of them and their implementation methods:
1.1.1 Group Control Brushing Company
This company provides flushing services, mainly based on group control devices of machines to brush the volume, including jailbroken machines and normal iPhones. They took advantage of Apple's security mechanisms, such as the image packaging of Apple mobile phones: the client containing the user login status in the entire phone is packaged and stored into a file, and then these files are stored in a sandbox environment. Based on this method, a single mobile phone is used to restore batch sandbox environments and accounts to achieve good group control effects.
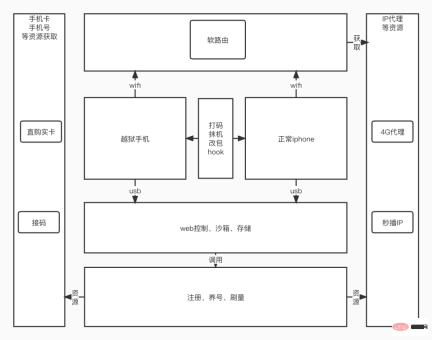
1.1.2 Account raising and diversion company
This is an e-commerce company that sells high imitation clothes through diversion. The main method is to register an account through a virtual hall card and then maintain the account. When the account used is blacklisted, it needs to open a nearby offline second-hand mobile phone store to replace the blacklisted phone at a lower price (5-10 yuan). After getting the new equipment, hire a group of real people, register an account and continue to publish and operate content. Finally, do brand promotion and get paid. It is understood that one account can attract hundreds of thousands of GMVs. Considering the number of accounts, the company's income is considerable.
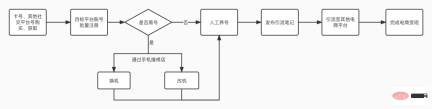
##1.1.3 Crowdsourced brushing company
Crowdsourcing black products usually have professional organizations that look for tasks on major platforms and recruit people to do part-time jobs. Part-time workers can get paid by completing tasks using their own accounts.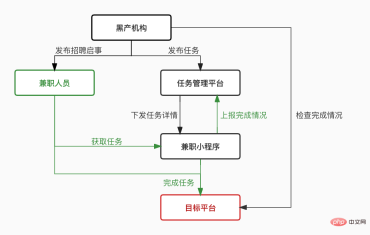
1.2 Redefinition of brush volume
Does brushing likes and likes mean brush volume? Yes, but not completely. We need to understand brush volume from a higher perspective. In the community environment of Xiaohongshu, we divide users into two categories: content publishers and content consumers. Content publishers are responsible for producing and providing quality content to consumers. Content consumers, in contrast, pay time costs, opportunity costs, information costs, emotional costs, and the value of the information contained in the content they view. In other words, publishers and consumers are actually engaging in a type of transaction, and the content platform is a market economy platform. When there is a market, there must be currency in circulation. In the content community, currency is units that can be measured such as readings, likes, collections, and comments.
##Under this analogy,
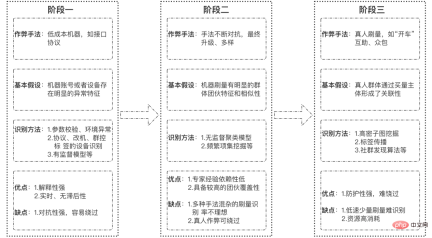
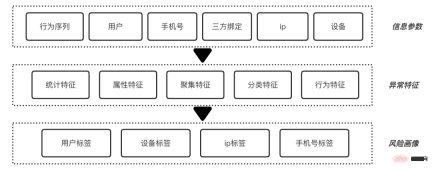
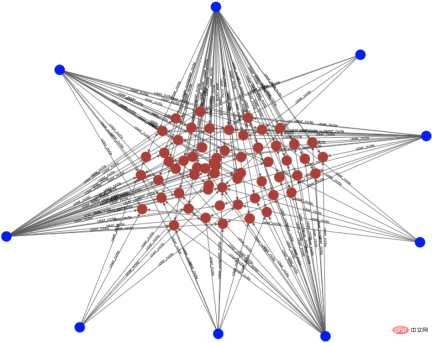
, the release of false content is similar to fake goods and will lead to inflation in the overall market. Although these tokens exist in the secondary market (community), they will eventually be traded with the primary market (e-commerce, advertising) to realize traffic monetization. For Xiaohongshu, washing is equivalent to counterfeit currency, and it needs to be managed sparing no effort. Since it has been classified as counterfeit currency, why does the wash volume still exist for a long time? Here we must mention several challenges facing anti-cheating: It is difficult to identify, difficult to govern, and difficult to consolidate. The difficulty in identification can be summarized into three parts: Uncontrollable terminal, AI versus AI, real person versus real person. 2.1.1 The terminal is uncontrollable In the community brushing scene, the terminal is actually uncontrollable, and it is difficult for adversaries to judge whether the client is A normal user is still a black product. Theoretically speaking, if the communication method is not trustworthy, there is no way to make it trustworthy. We once tried to reverse engineer an interface protocol attack tool, disassembled the code inside, and sent a request to the server disguised as our client by cracking the signature algorithm. This is by far the easiest one, the other methods are more difficult to control. (*Protocol attack) 2.1.2 AI versus AI Although risk control is constantly improving and AI computing has been used on a large scale to fight against it, our opponents are also constantly breaking through and upgrading. Take the black and gray group control method as an example. Utilize the vulnerability of third-party authorization to generate batches of third-party accounts on the public platform, and use the third-party accounts to complete the registration of Xiaohongshu accounts. Then use the UI's automatic script clicking tool to control clicks and keystrokes, and operate on your mobile phone to gain likes and followers in batches. The current popular method is to use 4G mobile phone/EC20 chips to conduct hybrid attacks to avoid our identification of black IPs. #The promotion of AI intelligence in risk control is slow. The reason is that AI algorithms are good at solving first-order problems, such as whether a picture contains a payment QR code. However, in actual scenarios, what we need to judge is whether the chat content is risky. From a human perspective, there is no risk in sending payment QR codes between friends who are in frequent contact, but sending payment QR codes between strangers who have just chatted is a high-risk behavior. The risk here depends on the aggregation of these two levels of information, payment QR code and stranger chat. Compared with humans, it is difficult for AI to automatically judge the aggregate recognition of these two dimensions, so it requires a lot of human intervention. 2.1.3 Real-person vs. real-person Recruit people through online group chats, offline small tasks, and even through formal recruitment channels. These people are mixed with real users and there is real normal behavior. At a certain point, they will charge money to increase their volume, which makes the entire identification extremely complicated. . After the brand releases its marketing needs, MCN accepts the task and distributes it to K on major platforms, allowing K to publish relevant notes to attract users, and finally achieve the purpose of marketing promotion. In this process, MCN has the motivation to increase the volume in order to complete the exposure requirements on the brand side and gain profits. Similarly, in order to complete the tasks issued by MCN and make up for his own lack of traffic, K also has the motivation to increase his traffic. Different roles on the brand side, such as the operations side, may also brush up the volume in order to complete the company's tasks. Some competitors, in order to frame their peers, will also gather C-end users to brush their notebooks, resulting in risk control penalties for bloggers and notebooks. What’s even more troublesome is that a large number of real people will be mixed in the entire group, making it difficult to accurately distinguish brushing behavior. Even if you can tell, how can you tell whether the person's current behavior is normal? There will be issues of recall and accidental damage. It is necessary to ensure a complete recall without accidentally damaging a batch of users, which will affect the smooth operation of the business. At the same time, the cold start of the Any safe operation will eventually fall into the problem of input-output ratio. In scenarios where content is flushed, it is difficult to measure the ROI of risk control investments because there is no direct revenue calculation. The second difficulty is measuring the effectiveness of prevention and control. We talked about CTR earlier, but is the CTR value enough to judge the effect of risk control? the answer is negative. The results of prevention and control will involve multiple dimensions. Among the brushing cases we manage, many of the fraudulent brushings come from real-person crowdsourcing. Should the effectiveness of prevention and control be judged based on the user dimension or the number of abnormal behaviors? The management of brush volume is a confrontation between people. After one method of risk control and governance, opponents will use new means and technologies to launch the next round of attacks. Therefore, the effect of prevention and control is constantly fluctuating. We Continuous confrontation is required. Xiaohongshu is a platform for sincere sharing and friendly interaction. For us, what is more important than technical capabilities is the attitude of the platform. This also means that our attitude towards volume washing behavior is to severely crack down on zero tolerance. Within the Security Technology Department, we have proposed three solution directions, which are: Engine-based risk control infrastructure, process-based risk control countermeasures, and intelligent risk control identification. 3.1 Engineizing risk control infrastructure According to domestic statistics, there are 1.5 million black industry employees, far more than our risk control technical team. How to fight on a small scale What about the entire industry chain? The solution we proposed is quick to iterate and easy to trial and error, and the risk control infrastructure is engine-based. It connects the engineering engine with the entire upstream and downstream links to improve the overall risk control efficiency. The risk control engine here not only refers to deploying strategies on an independent node, but also includes information access across the entire link, and uses upstream and downstream information to identify risks. Taking the near-line platform as an example, we have highly abstracted the existing quasi-real-time tasks, allowing users to quickly go online by assembling tasks in a short time, thus improving efficiency. The engine capability of this platform can combine multiple data sources and historical data in the background to provide risk control identification results in relatively real-time. It also combines behavioral sequence analysis, graph analysis and algorithm models to improve the effectiveness of risk control capabilities. The near-line platform makes up for the limitations of single rule identification, integrates with the original real-time risk control system, and is an effective supplement to other prevention and control methods. The near-line platform supports the ability to comprehensively process data and events, and also supports multi-source data access. It has flexible data processing capabilities. More importantly, it provides functions that can support algorithms and strategies and students’ customized data processing logic. Free up manpower and improve accuracy while engineering processes. The following figure shows the overall system and architecture of the near-line system: the general business gateway side (edith2.0) has also been unified to improve the access efficiency and stability of new services as a whole and achieve minute-level access to services . Risk perception, capacity building, risk identification, risk treatment, and effect assessment. Risk perception: Rely on the indicator system to discover risks faster, change passive firefighting into active defense, and drive capacity building and subsequent processes. Capacity building: Establish rapid response capabilities for confrontation and quickly access a flexibly configurable risk control system. Risk identification: Improve identification accuracy, establish a feature system, mine cheating features, and provide demand feedback on missing capabilities. Risk disposal: Choose more effective ways to reduce the cost of confrontation, intercept behaviors, limit the flow of notes, and deal with users, and can form effective feedback on strategy iterations. Effectiveness evaluation: Also relies on the indicator system to evaluate changes in risk levels, such as cheating and leakage, black product service prices, account prices, etc., and can also provide feedback on manslaughter and leakage. After discovering a new intelligence or sensing a new cheating attack, operate according to this process, and analyze and determine from the process what went wrong: Is it because the intelligence is not discovered enough, or is it The transformation of intelligence into identification is not fast enough, or the identification, processing and recall are insufficient. Take the purchase volume analysis in intelligence operations as an example. After discovering illegal services through intelligence or price fluctuations, purchase tests are conducted, and then the techniques are analyzed and appropriate strategies or models are selected for identification and disposal. As for the effects, The evaluation requires secondary purchasing or continuous monitoring of the price of black products. The current process will not end until the feedback on the identification and disposal has been implemented and the effect evaluation reaches the standard. In terms of the level of confrontation and the intensity of prevention and control, the intelligent identification of risk control can be roughly divided into three stages: the first stage, Low-cost machine techniques for black production, are analyzed and judged based on the characteristics of the behavioral subjects; in the second stage, in the high-frequency confrontation with black production, are based on the characteristics of the group Gang mining; in the third stage, in the identification of real-person brushing, based on the association of the brushing community, graph-based algorithm is used to discover the subject relationship. At present, these three stages have been implemented and practiced in Xiaohongshu. 3.3.1 Behavior Subject Characteristics Analysis Traffic data as a form of expression, its basic component is each interactive behavior of the user , risk control is also analyzed and identified based on behavioral characteristics. In the process of identification, the quality of behavioral characteristics is directly related to the identification and recall of black products, so the construction of data characteristics is particularly important. "A sharpened knife will never waste time cutting firewood." At this stage, we established a set of feature systemsbased on users, devices, etc. of behavioral subjects, laying the foundation for intelligent identification of risk control. The purpose of black production is to complete the volume brushing task at the lowest cost. At this stage, black production often uses machine means to carry out automatic or semi-automatic batch brushing, not only Low cost and high efficiency. Our basic assumption is that when performing machine brushing, there must be clear and explainable abnormal characteristics on the machine account or device. Therefore, how to analyze and identify abnormal characteristics is a proposition that needs to be solved in the first stage of risk control. In terms of identification and division of labor, we implement the end-cloud prevention and control model. End-defense designs reasonable device reporting and detection methods to complete preliminary prevention and control of devices. Cloud defense is based on user characteristics, device characteristics and behavioral characteristics. Conduct abnormal analysis and identification of behaviors. Take the protocol interface request as an example. The black product directly requests the back-end interface by cracking the signature algorithm of the platform. It can complete the brushing without the need of real equipment. It is the lowest cost and most efficient brushing commonly used by black products. means. The lack of real devices also results in no real front-end management and device reporting. Even if the device information is forged, the fields and device environment of the device reporting information cannot be effectively faked to be the same as normal devices. In addition to identifying and preventing environmental anomalies through verification of relevant characteristic parameters, we also established supervised identification relying on a comprehensive characteristic system and precipitated black production samples. Model. In the entire model, feature engineering is an important link to ensure model recall, and the processing of model results is the guarantee of accuracy. Feature engineering: In feature engineering, we divide it into two parts and proceed sequentially. Result processing: In terms of design, we trained the regression model as an infer, that is, the input value is a continuous score, which is more efficient in result processing than the classification model. flexible. 3.3.2 Group Feature Mining As mentioned before, confrontation always exists. When black manufacturers find that low-cost machine techniques cannot bypass risk control verification, they will constantly try to use real machines, fake device parameters, use cheating tools and other countermeasures, and upgrade the techniques to eliminate low-cost techniques. In the constant confrontation, the analysis of subject characteristics in the first stage appears relatively passive and cannot carry out active prevention and control. From the perspective of risk control, our basic assumption at this stage is: no matter how black products are forged or bypassed, the nature of the gang cannot be changed. There must be similarities and differences in the data characteristics. Gather . Therefore, at this stage, using gangs as the identification target to mine group characteristics and using structured data feature systems is the second line of defense that needs to be established. Take the constantly changing methods of machine brushing as an example. The black production methods gradually transformed from protocol interfaces to modified machine group control, and evolved into automated click tools. In order to proactively prevent and control, we use the equipment clustering model to identify and recall , and have completed effective containment of the above machine techniques. The device clustering model is characterized by basic device information (such as device model, app version, system kernel, etc.), and performs feature engineering and similarity calculation on the basic device information of users who interact with the same note or the same blogger. , use clustering algorithm to delineate device groups with high similarity. After identification, on the one hand, black devices are recorded and subsequent behavior interception is performed; on the other hand, the device tags of the black device group are output to expand the device black database. This model is an unsupervised model and can well adapt to the characteristics of black products that frequently change cheating methods. It can also supplement online strategies and expand recall. The following is the model flow chart and cluster identification case: In the entire model, we rely on Feature Engineering and Cluster Screening High recall and high accuracy clustering of black production equipment: 3.3.3 Graph-based subject discovery As mentioned above, the method of brushing volume will gradually evolve into real people versus real people. When black producers find that machine methods cannot bypass risk control, they will choose to recruit crowdsourcing or organize mutual brushing, and try to use real people's behavior to brush up the volume. Although they are all actions of real people, their essence is that they lack real will and are "counterfeit coins." Not only can the analysis of the main characteristics of real people’s behavior fail to detect abnormalities, but also group characteristics cannot be found on the equipment. Due to the particularity of the volume washing behavior, our reasonable assumption is that no matter how we change the method, the ultimate direction of the volume washing behavior is the main body of the buying volume. As long as there is subject correlation, Behaviors can be identified and recalled through data features. At this stage, Xiaohongshu relies on unique communities, e-commerce behavior graphs, and volume and order brushing graphs to actively discover and mine a group of behavioral subjects. It uses entity association and graph algorithms to identify real cheating users or those who are raising accounts. Users' recall can effectively find "fish that slipped through the net". *Figure 1: Association diagram of notes liked by normal users (red The dots are notes, the blue dots are users) ##*Figure 2: Association of notes liked by cheating users Figure (The red dots are notes, the blue dots are users) Figure 1 : Among the notes liked by 7 normal users, only one note overlaps, that is, the note with a red dot in the middle. Figure 2: The notes liked by 9 cheating users are the same batch of notes, the height of the liked notes Overlapping and not liked other notes other than this batch of notes. The tag propagation model is based on the risk control map to diffuse seed users. The seed users come from the brush users who have been identified and precipitated by risk control. The associated entities are buying notes and buying blogs. Mainly, etc., propagated through the point-edge correlation relationship in the risk control graph. Real people are used to brush the volume, and the equipment and accounts are limited. In order to achieve the purpose of brushing the volume, behavioral users will enable small accounts to repeatedly accept multiple tasks. The purpose of tag propagation is to spread the brushing tags to other brushing users in the community through the correct path to complete the identification and recall of brushing. Start by eliminating the impact of trouble, then solve the people who cause trouble, and finally eliminate the motivations that cause trouble. Eliminate Trouble Impact solve those who cause trouble Address the motivations for causing trouble The purpose of the volume buyers in the community scenario is to realize his commercial value through cheating, and what we have to do is to reduce the commercial value of these users or institutions. Risk Control Joint Ecology and Operation Department, will punish cheating traffic in accordance with platform rules, laws and regulations, etc. After continuous crackdowns, the cost of black accounts has become higher, the price of brushing services continues to rise, the unit price of likes and collections has increased by more than 300%, and the willingness of users to cheat is gradually decreasing. Since 2022, Xiaohongshu has cleaned up 3.1 billion cheating like behaviors. It can be seen that the platform’s attitude towards the matter of brushing up the volume has always been very resolute. (Author of this article: Xiaohongshu Security Technology Department Lu Xun Shiying Wang Ma Ye Feng Shi Hao Lao Pi)2. Challenges faced by risk control
2.1 Difficulty in identification

 On the Xiaohongshu platform, the content community is divided into K (bloggers), B (brands/merchants), MCN organizations ( intermediary), C-side (ordinary users). The question that has troubled us for a long time is who is doing this behavior for profit, is it the K-side, B-side, MCN side or C-side? And is this person's behavior at the moment good or bad? While managing, how to avoid accidental injuries?
On the Xiaohongshu platform, the content community is divided into K (bloggers), B (brands/merchants), MCN organizations ( intermediary), C-side (ordinary users). The question that has troubled us for a long time is who is doing this behavior for profit, is it the K-side, B-side, MCN side or C-side? And is this person's behavior at the moment good or bad? While managing, how to avoid accidental injuries? The real situation is that
every end may participate in brushing 3. Xiaohongshu’s governance practices
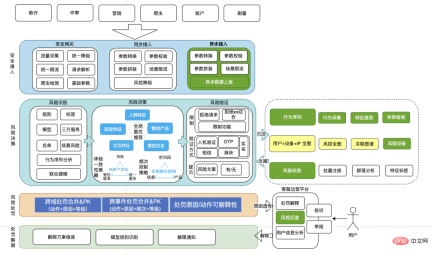
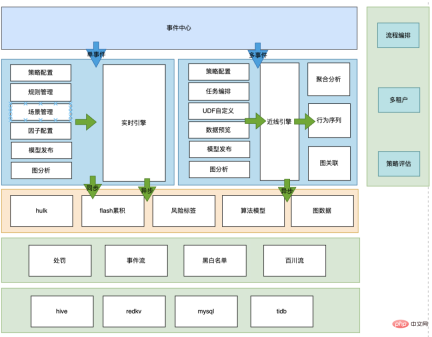
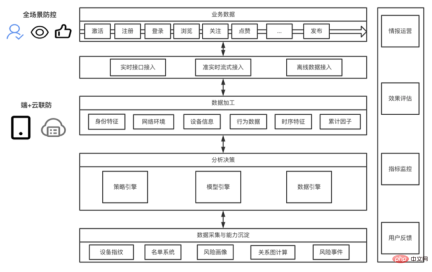
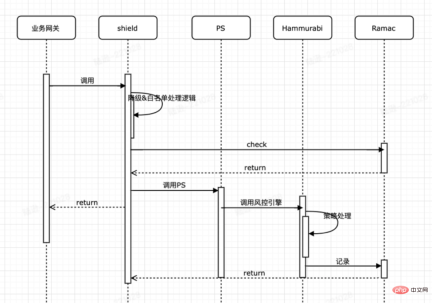
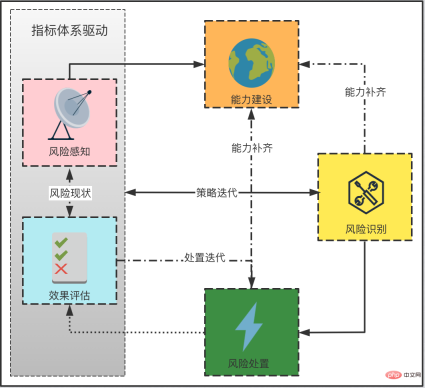
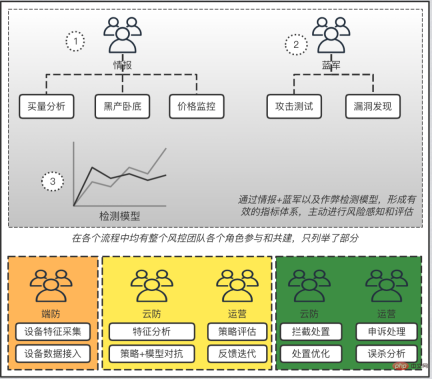
3.3 Intelligent risk control identification
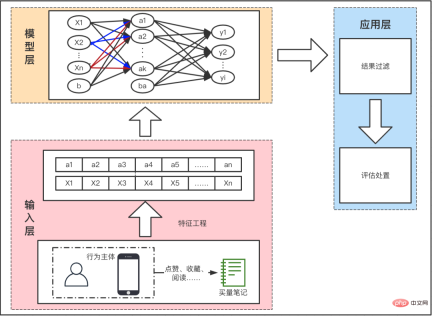
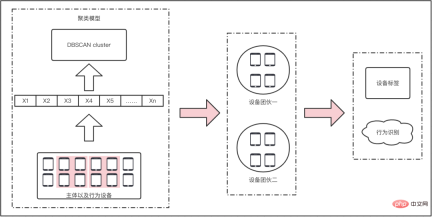
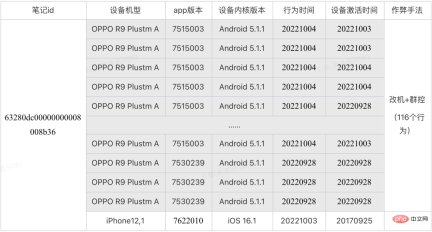
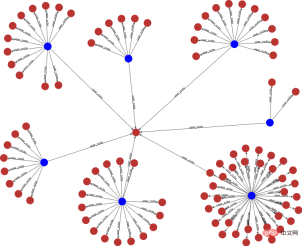
4. Thinking outside of technology to solve problemsThe above are mainly based on technology to solve problems, but in actual work, we also need to think outside of technology and from a more macro perspective. From the perspective of helping business and improving security. Based on this purpose, while delving deeply into technology, we have developed a set of practical and effective methodologies: 
The above is the detailed content of To prevent and control 'fake grass planting”, Xiaohongshu's technical team has done these major things. For more information, please follow other related articles on the PHP Chinese website!
 I Tried Vibe Coding with Cursor AI and It's Amazing!Mar 20, 2025 pm 03:34 PM
I Tried Vibe Coding with Cursor AI and It's Amazing!Mar 20, 2025 pm 03:34 PMVibe coding is reshaping the world of software development by letting us create applications using natural language instead of endless lines of code. Inspired by visionaries like Andrej Karpathy, this innovative approach lets dev
 How to Use DALL-E 3: Tips, Examples, and FeaturesMar 09, 2025 pm 01:00 PM
How to Use DALL-E 3: Tips, Examples, and FeaturesMar 09, 2025 pm 01:00 PMDALL-E 3: A Generative AI Image Creation Tool Generative AI is revolutionizing content creation, and DALL-E 3, OpenAI's latest image generation model, is at the forefront. Released in October 2023, it builds upon its predecessors, DALL-E and DALL-E 2
 How to Use YOLO v12 for Object Detection?Mar 22, 2025 am 11:07 AM
How to Use YOLO v12 for Object Detection?Mar 22, 2025 am 11:07 AMYOLO (You Only Look Once) has been a leading real-time object detection framework, with each iteration improving upon the previous versions. The latest version YOLO v12 introduces advancements that significantly enhance accuracy
 Top 5 GenAI Launches of February 2025: GPT-4.5, Grok-3 & More!Mar 22, 2025 am 10:58 AM
Top 5 GenAI Launches of February 2025: GPT-4.5, Grok-3 & More!Mar 22, 2025 am 10:58 AMFebruary 2025 has been yet another game-changing month for generative AI, bringing us some of the most anticipated model upgrades and groundbreaking new features. From xAI’s Grok 3 and Anthropic’s Claude 3.7 Sonnet, to OpenAI’s G
 Elon Musk & Sam Altman Clash over $500 Billion Stargate ProjectMar 08, 2025 am 11:15 AM
Elon Musk & Sam Altman Clash over $500 Billion Stargate ProjectMar 08, 2025 am 11:15 AMThe $500 billion Stargate AI project, backed by tech giants like OpenAI, SoftBank, Oracle, and Nvidia, and supported by the U.S. government, aims to solidify American AI leadership. This ambitious undertaking promises a future shaped by AI advanceme
 Sora vs Veo 2: Which One Creates More Realistic Videos?Mar 10, 2025 pm 12:22 PM
Sora vs Veo 2: Which One Creates More Realistic Videos?Mar 10, 2025 pm 12:22 PMGoogle's Veo 2 and OpenAI's Sora: Which AI video generator reigns supreme? Both platforms generate impressive AI videos, but their strengths lie in different areas. This comparison, using various prompts, reveals which tool best suits your needs. T
 Google's GenCast: Weather Forecasting With GenCast Mini DemoMar 16, 2025 pm 01:46 PM
Google's GenCast: Weather Forecasting With GenCast Mini DemoMar 16, 2025 pm 01:46 PMGoogle DeepMind's GenCast: A Revolutionary AI for Weather Forecasting Weather forecasting has undergone a dramatic transformation, moving from rudimentary observations to sophisticated AI-powered predictions. Google DeepMind's GenCast, a groundbreak
 Which AI is better than ChatGPT?Mar 18, 2025 pm 06:05 PM
Which AI is better than ChatGPT?Mar 18, 2025 pm 06:05 PMThe article discusses AI models surpassing ChatGPT, like LaMDA, LLaMA, and Grok, highlighting their advantages in accuracy, understanding, and industry impact.(159 characters)


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Notepad++7.3.1
Easy-to-use and free code editor

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Dreamweaver CS6
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment






