 Technology peripherals
Technology peripherals AI
AI Understand car-grade security chips and chip security testing technology in one article
Understand car-grade security chips and chip security testing technology in one articleUnderstand car-grade security chips and chip security testing technology in one article
With the development of intelligence and Internet of Vehicles in the global automotive industry, people in the new era are increasingly enjoying convenient travel and comfortable driving experience. However, various risks brought by the networked environment are also coming quietly, whether it is the Internet, emergency calls, navigation systems, automatic charging, on-demand power supply, or location-based service advertisements, maintenance updates and traffic alerts, they will all become Potential loopholes in hacker attacks and frequent car security incidents make it urgent to build an information security protection system for intelligent connected cars. In the automotive information security protection system, automotive security chips are a very critical link. By adding security chips to vehicle-mounted devices such as central gateways, domain controllers, and ECUs, they can implement encryption of in-vehicle communications, identification of in-vehicle devices, and OBD Secure access to diagnostic devices. It can effectively prevent bus attacks such as CAN Ethernet, prevent illegal OBD devices from reading and writing, identify malicious nodes and send illegal messages, etc., and provide security guarantee for communication between vehicles and between vehicles and things, as well as the operation of vehicle systems. .
This article is based on automotive security chips. It first introduces the relevant standards of automotive-grade security chips, and then lists the main forms of automotive security chips based on different application scenarios, as well as their role in automotive electronic and electrical architecture. Through research and comparison with domestic and foreign mainstream automotive security chip solutions to understand the current situation and future trends, chip security testing technology is introduced as an important guarantee for the development of automotive security chips.
Related Standards for Automotive Security Chips
First of all, the automotive security chip is a car-grade chip. For car-grade chips, it mainly includes standards such as AEC and ISO 26262 .
AEC is the Automotive Electronics Council, which aims to establish common parts qualification and quality system standards. For specific standard details, please refer to Table 1:

Table 1 Types of AEC standards
Car security chips belong to Integrated circuit chips, which belong to standard AEC-Q100, include grade details as shown in Table 2:

Table 2 AEC-Q100 standard grade description
ISO 26262 is an international standard for road vehicle functional safety. It is mainly aimed at functional safety and is used to determine the automotive safety integrity level ASIL (Automotive Safety Integrity Level). ASIL levels are divided into A, B, C and D. Automotive security chips need to meet this standard and corresponding level requirements.
At the same time, as a kind of security chip, automobile security chips also need to meet the relevant rating assessment of security chips. The current industry security rating standards for security chips include international, domestic EAL and national secret ratings.
The international evaluation assurance level EAL (Evaluation Assurance Level) includes 7 levels (EAL1 to EAL7). It is a standard that fully complies with the international standard CC (Common Criteria) and is developed to evaluate the security of IT products or systems. Numeric level. The domestic EAL level assessment is conducted by the China Cybersecurity Review Technology and Certification Center and includes 5 levels (EAL1 to EAL5).
The national secret level is evaluated according to the standards set by the State Cryptozoological Security Bureau, and is mainly divided into 3 levels of security. Security level 1 stipulates the minimum security standards that security capabilities need to meet, and provides basic protection measures for keys and sensitive information. Security level 2 is stipulated on the basis of level 1, with logical or physical protection measures to meet medium security level requirements. Security level 3 is the highest security level and requires comprehensive protection capabilities against various security risks.
Automotive security chip applications
There are three main types of application forms for automotive security chips. The first type is embedded in processors such as microcontrollers, microprocessors and ADAS. HSM (Hardware Security Module) hardware security module is mainly used in various controllers in the car to provide support for security functions such as safe startup and security algorithms. The second category is secure memory chips. This type of chip has a secure storage area and provides encrypted read and write functions. It is mainly used in areas with high security requirements for important data storage. The third category is a discrete security controller, including programmable SE (Secure Element) security unit or programmable security eSIM (V2X communication), which is mainly used in areas of vehicle external communication and frequent external access. It is worth mentioning that in the entire scenario of V2X secure communication, not only data encryption, data signature, and identity verification are required, but also end-to-end reliability and security must be ensured. In addition, V2X security chips must be able to achieve high performance. Meet the current requirements of the "new four modernizations". The classification of automotive security chip application forms and the layout of in-car applications are shown in Figure 1.

Figure 1 Main forms of automotive security chips and their application layout in automobiles
Automotive security chip products abroad Companies mainly include: ST, NXP, Infineon, Renesas, TI and Microchip, etc. Domestic companies include: Ziguang Tongxin, Huada Microelectronics, Hongsi Electronics, Core Titanium, National Technology, Fudan Microelectronics, Corechi, Black Sesame and Horizon, etc. After market research, relevant products of domestic and foreign manufacturers can be found in Table 3.

Table 3 Car-grade safety chip solutions from domestic and foreign manufacturers
Chip safety test Technology
There is no doubt that for vehicle-mounted security chips, when applied to vehicle terminal systems, their information security characteristics need to undergo strict and standardized testing and evaluation by third-party organizations. The security testing technology of automotive chips is inherited from the integrated circuit security testing technology. It is mainly performed by simulating hacker security attacks. The actual situation of the chip's resistance to various security attacks is combined with systematic analysis as its security indicator.
Security attack testing technology for chips mainly includes active and passive categories:
Active attack testing: The tester controls the input or operating environment of the chip to make the security chip operation behavior appear Abnormality, in this case, by analyzing the abnormal behavior of the chip operation, key sensitive information such as keys in the chip can be obtained. Common fault injection methods for active attacks include electromagnetic, laser, infrared, high voltage injection and other testing methods.
Passive attack test: The tester makes cryptographic devices such as chips run according to their specifications in most cases, or even run completely according to their specifications. In this case, by observing the physical characteristics of the chip (such as execution time, energy consumption, etc.), the tester may obtain key sensitive information such as keys. A commonly used method for passive testing is side channel attack, which includes analyzing signal characteristics such as timing, power, and electromagnetic radiation of the chip.
Chip security testing requires professional equipment and professionals. Test execution methods mainly include non-invasive, semi-invasive and intrusive. For details, see Table 4:

Table 4 Security Chip Security Test Method
The above is the detailed content of Understand car-grade security chips and chip security testing technology in one article. For more information, please follow other related articles on the PHP Chinese website!
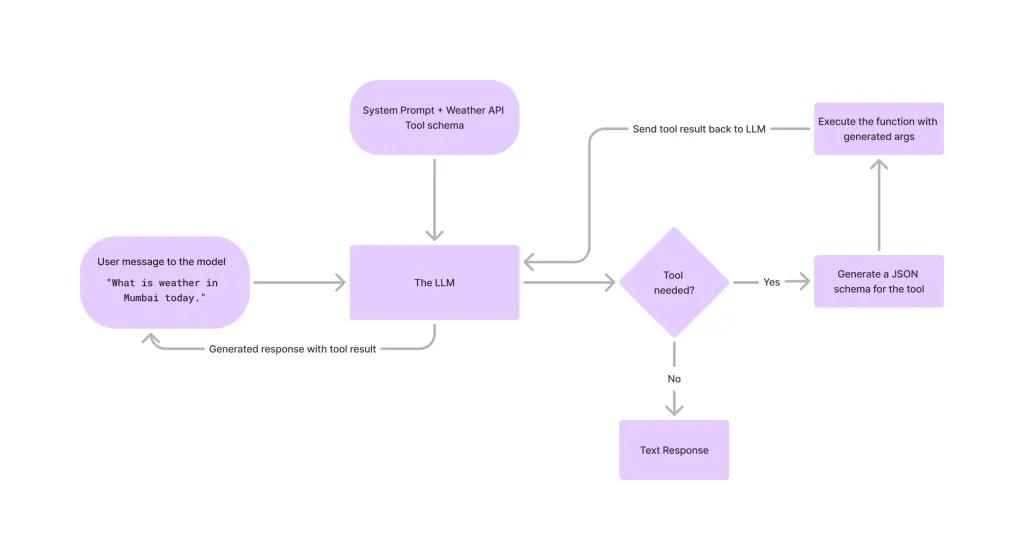 Tool Calling in LLMsApr 14, 2025 am 11:28 AM
Tool Calling in LLMsApr 14, 2025 am 11:28 AMLarge language models (LLMs) have surged in popularity, with the tool-calling feature dramatically expanding their capabilities beyond simple text generation. Now, LLMs can handle complex automation tasks such as dynamic UI creation and autonomous a
 How ADHD Games, Health Tools & AI Chatbots Are Transforming Global HealthApr 14, 2025 am 11:27 AM
How ADHD Games, Health Tools & AI Chatbots Are Transforming Global HealthApr 14, 2025 am 11:27 AMCan a video game ease anxiety, build focus, or support a child with ADHD? As healthcare challenges surge globally — especially among youth — innovators are turning to an unlikely tool: video games. Now one of the world’s largest entertainment indus
 UN Input On AI: Winners, Losers, And OpportunitiesApr 14, 2025 am 11:25 AM
UN Input On AI: Winners, Losers, And OpportunitiesApr 14, 2025 am 11:25 AM“History has shown that while technological progress drives economic growth, it does not on its own ensure equitable income distribution or promote inclusive human development,” writes Rebeca Grynspan, Secretary-General of UNCTAD, in the preamble.
 Learning Negotiation Skills Via Generative AIApr 14, 2025 am 11:23 AM
Learning Negotiation Skills Via Generative AIApr 14, 2025 am 11:23 AMEasy-peasy, use generative AI as your negotiation tutor and sparring partner. Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining
 TED Reveals From OpenAI, Google, Meta Heads To Court, Selfie With MyselfApr 14, 2025 am 11:22 AM
TED Reveals From OpenAI, Google, Meta Heads To Court, Selfie With MyselfApr 14, 2025 am 11:22 AMThe TED2025 Conference, held in Vancouver, wrapped its 36th edition yesterday, April 11. It featured 80 speakers from more than 60 countries, including Sam Altman, Eric Schmidt, and Palmer Luckey. TED’s theme, “humanity reimagined,” was tailor made
 Joseph Stiglitz Warns Of The Looming Inequality Amid AI Monopoly PowerApr 14, 2025 am 11:21 AM
Joseph Stiglitz Warns Of The Looming Inequality Amid AI Monopoly PowerApr 14, 2025 am 11:21 AMJoseph Stiglitz is renowned economist and recipient of the Nobel Prize in Economics in 2001. Stiglitz posits that AI can worsen existing inequalities and consolidated power in the hands of a few dominant corporations, ultimately undermining economic
 What is Graph Database?Apr 14, 2025 am 11:19 AM
What is Graph Database?Apr 14, 2025 am 11:19 AMGraph Databases: Revolutionizing Data Management Through Relationships As data expands and its characteristics evolve across various fields, graph databases are emerging as transformative solutions for managing interconnected data. Unlike traditional
 LLM Routing: Strategies, Techniques, and Python ImplementationApr 14, 2025 am 11:14 AM
LLM Routing: Strategies, Techniques, and Python ImplementationApr 14, 2025 am 11:14 AMLarge Language Model (LLM) Routing: Optimizing Performance Through Intelligent Task Distribution The rapidly evolving landscape of LLMs presents a diverse range of models, each with unique strengths and weaknesses. Some excel at creative content gen


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Linux new version
SublimeText3 Linux latest version

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.





