 Technology peripherals
Technology peripherals AI
AI An article about the functional safety design of advanced autonomous driving domain controllers
An article about the functional safety design of advanced autonomous driving domain controllersAn article about the functional safety design of advanced autonomous driving domain controllers
The design process of the advanced autonomous driving central domain controller requires a full understanding of the security design principles, because in the early design, whether it is architecture, software, hardware or communication, it is necessary to fully understand its design rules in order to give full play to it. It provides corresponding advantages while avoiding certain design problems.
The high-end domain controller functional safety design we are talking about here mainly refers to the scenario analysis involved in expected functional safety in front-end development and all sub-items involved in back-end functional safety. . First, the basic level of hardware is used as the connection base point, and the entire system architecture communication and data stream transmission are realized through the data communication end. The software is burned into the hardware, using the hardware as the carrier, and the communication unit is responsible for calling modules between each other. So for the security design side of the domain controller. From the perspective of vehicle safety capability analysis, the main analysis process also includes the following three aspects: System Theoretic Analysis STPA (Systems Theoretic Process Analysis), Failure Mode and Effect Analysis FMEA, and Fault Tree Analysis (FTA).
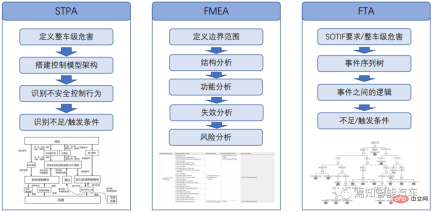
For the domain controller at the core of the architecture, a very strong functional security level is involved. We can generally divide it into three levels: data communication security, hardware basic security, and software basic security. The specific analysis process needs to fully consider several aspects including functional safety at the basic hardware level, functional safety at the basic software level, and data communication capabilities, and the analysis of each aspect needs to be comprehensive.
Data communication security
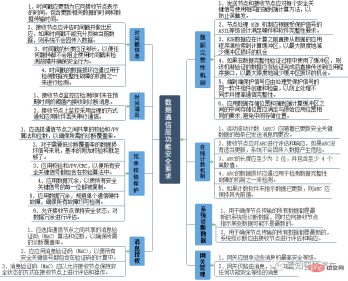
The communication end, as the connection and data inflow and outflow end, plays a decisive role in the entire system architecture communication. At the data communication level, its functional safety requirements mainly refer to the general data integrity mechanism, online counting mechanism (Rolling Counter), system diagnostic data refresh, timestamp information (Time Stamp), time overflow (CheckSum), management authorization code, data Redundancy, gateway and other major aspects. Among them, for data communication, such as online counting, diagnosis, time overflow verification, etc. are consistent with the traditional point-to-point Canbus signal, while for the next generation of autonomous driving, data redundancy, central gateway management optimization, and data authorization Access, etc. are areas that need to be focused on.
Their overall requirements for functional safety are as follows:
Hardware basic level
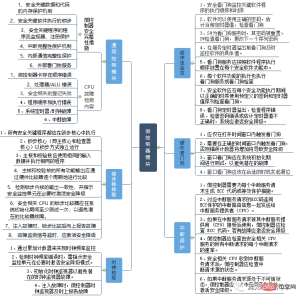
Functional safety requirements at the basic level of hardware mainly refer to several major modules such as microcontroller modules, storage modules, power supply support, and serial data communication.
Microcontroller module security
The microcontroller here is what we often call AI chip (SOC), floating point operation Chip (GPU) and logic computing chip (MCU) are the main computing units running on the vehicle-side domain controller. From the perspective of functional safety design, various types of microcontroller modules include general design modules, lock-step core verification (including lock-step core comparison, lock-step core self-test), clock verification (including clock comparison, clock Self-test), program flow monitoring, heartbeat monitoring, hardware watchdog function, interrupt protection, memory/flash/register monitoring/self-test, power supply monitoring and self-test, communication protection, etc.
It should be noted that the microcontroller should provide the "active heartbeat" periodic switching signal to the monitoring unit through hard wires. Switching signals should be managed by a security watchdog that also provides program flow monitoring capabilities. The security watchdog is only allowed to toggle the "active heartbeat" during the watchdog service. The microcontroller security software should then toggle the "active heartbeat" every time the internal security watchdog is serviced, which indicates to the monitoring unit that the microcontroller is running and the security watchdog timer is running. The system background should monitor the "active heartbeat" switching signal by checking that the times of signal switching and high and low states are within the valid range. Once an "active heartbeat" failure is detected, the SMU activates safety downgrade.
For watchdog programs, testing should be performed during system initialization to avoid potential failures. The following fault types should be tested during the process:
- Incorrect watchdog trigger time (triggered in closed window);
- There is no watchdog trigger;
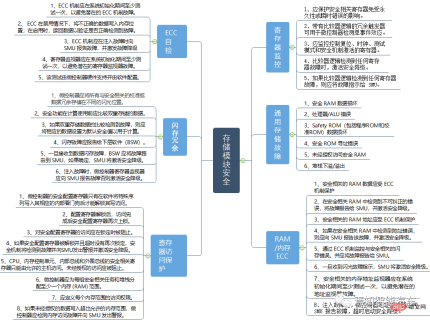
Storage module security
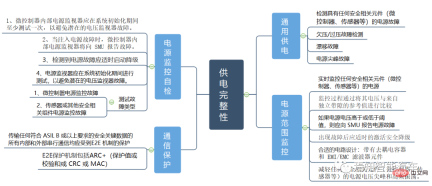
The storage module is an integral part of the entire domain control. During the entire chip operation process, it is mainly used for Temporary and commonly used file storage, as well as data exchange during the operation process. For example, our operating system startup program is stored in a SOC/MCU plug-in storage unit, and for example, our next-generation autonomous driving products must use driving/ Parking high-precision maps are usually stored in the storage unit plugged into the chip, and some diagnostic and log files in the underlying software are also stored in our plug-in chip. So what conditions need to be met for the entire storage unit to ensure appropriate functional safety conditions? See the figure below for detailed explanation.
The security of the entire storage unit mainly includes register monitoring, general storage unit, RAM/memory ECC, ECC self-test, flash redundancy, register write protection, range protection, register self-test, etc. Many aspects.
Power supply integrity
The power supply integrity safety method test is mainly through the entire power supply operating status. It is carried out through fault injection and real-time monitoring.
One example of a test approach is to configure a higher or lower monitoring threshold to force the monitor to detect an undervoltage or overvoltage fault and verify that the fault is correctly detected. When a fault is injected, the power monitor should activate the auxiliary shutdown path. The microcontroller should monitor the auxiliary shutdown path and only consider the test a "pass" if the auxiliary shutdown path behaves as expected in the test procedure, otherwise it will be considered a "fail". Once a failure is detected, the microcontroller activates safety degradation. This test is supported by a dedicated BIST function and must be configured by the microcontroller software according to a detailed procedure.
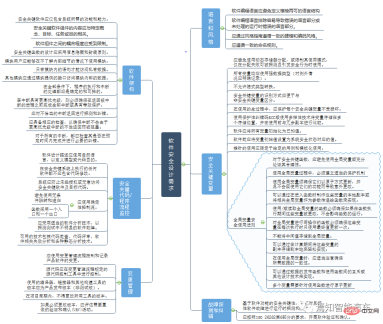
Software Basic Security
Design considerations regarding the basic software security level are mainly for vehicle-mounted Comprehensive consideration of possible software failures during the development of intelligent driving software. These include software document design, software language and style, safety-critical variables, fault detection and correction, software architecture, safety-critical code, program flow monitoring, change management and other major aspects. Software design descriptions at all levels should use natural language to define the purpose of the model or code. For example, when the independence between multiple variables is critical to the security of the system, these variables should not be combined into a single data element using the variable's public address. This can lead to common mode systematic failures involving all elements in the structure. If variables have been grouped, appropriate justification should be made for safety-critical functions.
This article starts from the perspective of functional safety and analyzes in detail the comprehensive elements and processes of the entire autonomous driving domain controller design from different aspects. Among them, it includes various aspects such as hardware foundation, software methods, data communication and so on. These functional safety design capabilities focus on the entire architecture level while also paying full attention to the connections between its internal components to ensure the compliance and integrity of the design process and avoid unpredictable consequences in the later stages of the design. Therefore, as detailed safety design rules, it can provide necessary reference for development engineers.
The above is the detailed content of An article about the functional safety design of advanced autonomous driving domain controllers. For more information, please follow other related articles on the PHP Chinese website!
 Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AM
Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AMCyberattacks are evolving. Gone are the days of generic phishing emails. The future of cybercrime is hyper-personalized, leveraging readily available online data and AI to craft highly targeted attacks. Imagine a scammer who knows your job, your f
 Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AM
Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AMIn his inaugural address to the College of Cardinals, Chicago-born Robert Francis Prevost, the newly elected Pope Leo XIV, discussed the influence of his namesake, Pope Leo XIII, whose papacy (1878-1903) coincided with the dawn of the automobile and
 FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AM
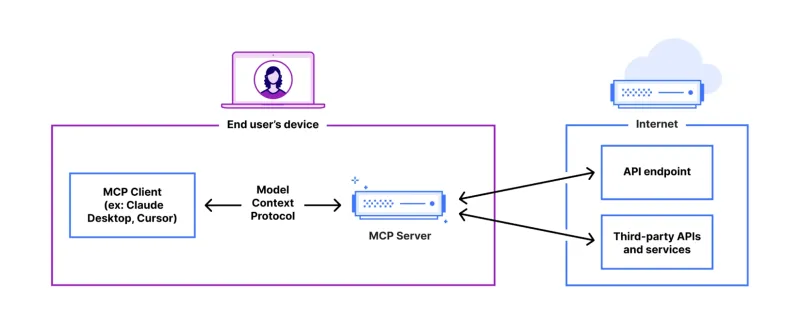
FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AMThis tutorial demonstrates how to integrate your Large Language Model (LLM) with external tools using the Model Context Protocol (MCP) and FastAPI. We'll build a simple web application using FastAPI and convert it into an MCP server, enabling your L
 Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AM
Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AMExplore Dia-1.6B: A groundbreaking text-to-speech model developed by two undergraduates with zero funding! This 1.6 billion parameter model generates remarkably realistic speech, including nonverbal cues like laughter and sneezes. This article guide
 3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AM
3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AMI wholeheartedly agree. My success is inextricably linked to the guidance of my mentors. Their insights, particularly regarding business management, formed the bedrock of my beliefs and practices. This experience underscores my commitment to mentor
 AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AM
AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AMAI Enhanced Mining Equipment The mining operation environment is harsh and dangerous. Artificial intelligence systems help improve overall efficiency and security by removing humans from the most dangerous environments and enhancing human capabilities. Artificial intelligence is increasingly used to power autonomous trucks, drills and loaders used in mining operations. These AI-powered vehicles can operate accurately in hazardous environments, thereby increasing safety and productivity. Some companies have developed autonomous mining vehicles for large-scale mining operations. Equipment operating in challenging environments requires ongoing maintenance. However, maintenance can keep critical devices offline and consume resources. More precise maintenance means increased uptime for expensive and necessary equipment and significant cost savings. AI-driven
 Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AM
Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AMMarc Benioff, Salesforce CEO, predicts a monumental workplace revolution driven by AI agents, a transformation already underway within Salesforce and its client base. He envisions a shift from traditional markets to a vastly larger market focused on
 AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AM
AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AMThe Rise of AI in HR: Navigating a Workforce with Robot Colleagues The integration of AI into human resources (HR) is no longer a futuristic concept; it's rapidly becoming the new reality. This shift impacts both HR professionals and employees, dem


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

SublimeText3 English version
Recommended: Win version, supports code prompts!

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

Dreamweaver Mac version
Visual web development tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.






