The huge potential of facial recognition technology in various fields is almost unimaginable.
However, certain common mistakes in its functionality and some ethical issues need to be addressed before use.

Facial recognition systems use biometric technology to map facial features from photos or videos and then compare that information to a database of known faces to find a match. Facial recognition can help verify a person's identity, but it also raises privacy concerns.
As with other artificial intelligence technologies, there are some ethical principles that need to be followed when using facial recognition systems. These principles include:
1. Fairness of facial recognition
First of all, the development of facial recognition technology must ensure that the system can completely prevent or at least minimize discrimination based on race, gender, facial features, deformity, etc. or otherwise prejudice any person or group. There is now ample evidence that facial recognition systems are unlikely to be 100% fair in their operation. As a result, companies developing the technology often spend hundreds of hours removing all traces of bias found within it.
Organizations must redouble their efforts to eliminate bias in facial recognition systems, and to do so, the datasets used for machine learning and labeling must be diverse. Most importantly, the output quality of a fair facial recognition system will be very high, as it can work seamlessly anywhere in the world without any bias.
To ensure the fairness of facial recognition systems, developers can also involve end customers during the testing phase.
2. Openness in how AI operates
Organizations incorporating facial recognition systems into workplace and cybersecurity systems need to know everything about where the machine learning data is stored. Such organizations need to understand the limitations and capabilities of the technology before implementing it. Companies providing AI technology must be fully transparent with customers on these details. Additionally, service providers must ensure that their facial recognition systems can be used by customers from any location based on their convenience. And any updates in the system must be made after receiving valid approval from the customer.
3. Responsibilities of Stakeholders
As mentioned earlier, facial recognition systems are deployed in multiple fields. Organizations developing such systems must be held accountable for them, especially where the technology may directly impact any individual or group (law enforcement, surveillance). Liability in such systems is intended to prevent physical or health harm, financial misappropriation, or other problems caused by the system that may result. In order to introduce an element of control into the process, a qualified person needs to be put in charge of the systems in the organization to make sound decisions. Beyond this, organizations that incorporate facial recognition systems into their daily operations must immediately address customer dissatisfaction related to the technology.
4. Consent and notification before surveillance
Under normal circumstances, facial recognition systems may not be used to spy on individuals, groups or others without their consent. Some institutions, such as the European Union, have a standardized set of laws (GDPR) to prevent unauthorized organizations from monitoring individuals. Organizations with such systems must comply with all data protection and privacy regulations in the country.
5. Lawful surveillance to avoid human rights violations
Organizations cannot use facial recognition systems unless authorized by the state or government decision-making authority for purposes related to national security or other important circumstances. Monitor any individual or group. Basically, the use of this technology to violate the human rights and freedoms of victims is strictly prohibited.
6. Verification Error While Shopping
As mentioned earlier, facial recognition systems are incorporated into digital payment applications so that users can verify transactions using the technology. Using this technology to pay makes criminal activities such as facial identity theft and debit card fraud likely to occur. Customers choose facial recognition systems because of the great convenience it provides users. However, one error that can occur in such a system is that identical twins can use each other's bank accounts to make unauthorized payments.
7. Inaccurate Law Enforcement Applications
Facial recognition systems are used to identify criminals before they are captured. While the technology as a concept is undoubtedly useful in law enforcement, there are some glaring issues with its work, such as biased artificial intelligence that provides inaccurate results for law enforcement officers because sometimes systems fail to differentiate between people of color. Typically, such systems are trained on datasets containing images of white people. As a result, the system's work is riddled with errors when it comes to identifying people of other races.
As we have seen, the main problems and errors associated with facial recognition technology stem from a lack of advancement in the technology, a lack of diversity in the data sets, and inefficient handling of the system by organizations.
It is foreseeable that with the further advancement of technology in the future, technology-related problems will be solved; problems related to bias in artificial intelligence algorithms will eventually be eliminated. However, in order for the technology to work flawlessly without violating any ethical principles, organizations must maintain a strict level of governance for such systems.
The above is the detailed content of Ethical principles for facial recognition technology. For more information, please follow other related articles on the PHP Chinese website!
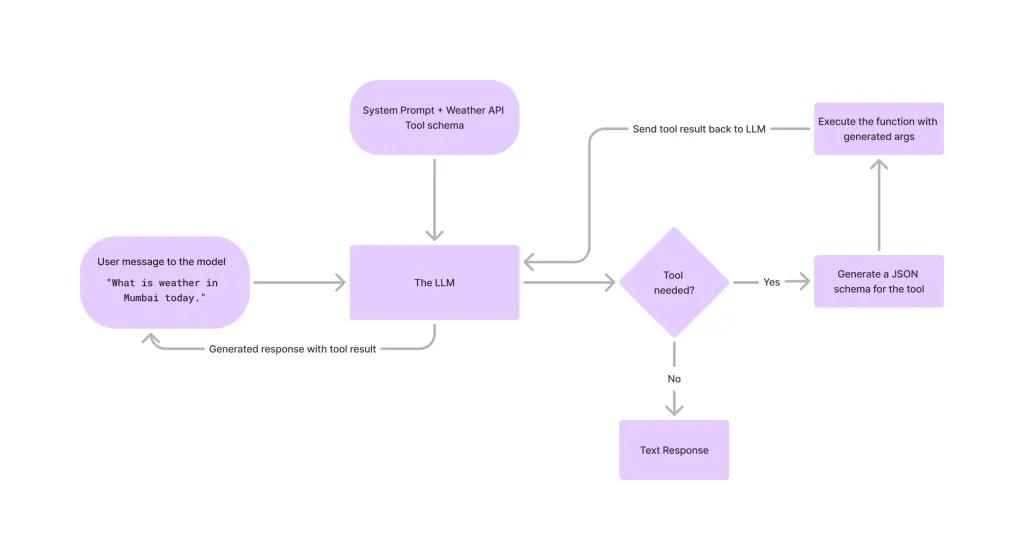 Tool Calling in LLMsApr 14, 2025 am 11:28 AM
Tool Calling in LLMsApr 14, 2025 am 11:28 AMLarge language models (LLMs) have surged in popularity, with the tool-calling feature dramatically expanding their capabilities beyond simple text generation. Now, LLMs can handle complex automation tasks such as dynamic UI creation and autonomous a
 How ADHD Games, Health Tools & AI Chatbots Are Transforming Global HealthApr 14, 2025 am 11:27 AM
How ADHD Games, Health Tools & AI Chatbots Are Transforming Global HealthApr 14, 2025 am 11:27 AMCan a video game ease anxiety, build focus, or support a child with ADHD? As healthcare challenges surge globally — especially among youth — innovators are turning to an unlikely tool: video games. Now one of the world’s largest entertainment indus
 UN Input On AI: Winners, Losers, And OpportunitiesApr 14, 2025 am 11:25 AM
UN Input On AI: Winners, Losers, And OpportunitiesApr 14, 2025 am 11:25 AM“History has shown that while technological progress drives economic growth, it does not on its own ensure equitable income distribution or promote inclusive human development,” writes Rebeca Grynspan, Secretary-General of UNCTAD, in the preamble.
 Learning Negotiation Skills Via Generative AIApr 14, 2025 am 11:23 AM
Learning Negotiation Skills Via Generative AIApr 14, 2025 am 11:23 AMEasy-peasy, use generative AI as your negotiation tutor and sparring partner. Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining
 TED Reveals From OpenAI, Google, Meta Heads To Court, Selfie With MyselfApr 14, 2025 am 11:22 AM
TED Reveals From OpenAI, Google, Meta Heads To Court, Selfie With MyselfApr 14, 2025 am 11:22 AMThe TED2025 Conference, held in Vancouver, wrapped its 36th edition yesterday, April 11. It featured 80 speakers from more than 60 countries, including Sam Altman, Eric Schmidt, and Palmer Luckey. TED’s theme, “humanity reimagined,” was tailor made
 Joseph Stiglitz Warns Of The Looming Inequality Amid AI Monopoly PowerApr 14, 2025 am 11:21 AM
Joseph Stiglitz Warns Of The Looming Inequality Amid AI Monopoly PowerApr 14, 2025 am 11:21 AMJoseph Stiglitz is renowned economist and recipient of the Nobel Prize in Economics in 2001. Stiglitz posits that AI can worsen existing inequalities and consolidated power in the hands of a few dominant corporations, ultimately undermining economic
 What is Graph Database?Apr 14, 2025 am 11:19 AM
What is Graph Database?Apr 14, 2025 am 11:19 AMGraph Databases: Revolutionizing Data Management Through Relationships As data expands and its characteristics evolve across various fields, graph databases are emerging as transformative solutions for managing interconnected data. Unlike traditional
 LLM Routing: Strategies, Techniques, and Python ImplementationApr 14, 2025 am 11:14 AM
LLM Routing: Strategies, Techniques, and Python ImplementationApr 14, 2025 am 11:14 AMLarge Language Model (LLM) Routing: Optimizing Performance Through Intelligent Task Distribution The rapidly evolving landscape of LLMs presents a diverse range of models, each with unique strengths and weaknesses. Some excel at creative content gen


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

SublimeText3 Linux new version
SublimeText3 Linux latest version

Atom editor mac version download
The most popular open source editor

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

SublimeText3 Mac version
God-level code editing software (SublimeText3)






