How to integrate facial recognition technology in mobile apps

Facial Recognition Technology is a technology used to recognize faces and compare and match them with pre-stored face images . Facial recognition technology mainly uses computer vision and pattern recognition technology to identify faces, and its main purpose is to ensure security and facilitate identity authentication.
Face recognition technology usually includes the following steps: collecting images, detecting faces, extracting facial features, comparison, recognition and authentication.
When collecting images, you can use cameras, scanners and other equipment and transfer them to computers or other devices for processing. Subsequently, facial recognition technology is used to detect the face in the image and extract it from the image. At the same time, the feature points, texture and other features of the face are extracted to form a face feature vector. Finally, these feature vectors are compared and matched with known face feature vectors stored in the database to identify or verify the identity of the face.
Face recognition technology has a wide range of applications, such as security monitoring, identity authentication, access control, electronic payment, personal device locking, etc. However, face recognition technology also faces some challenges, such as misidentification, privacy protection and other issues.
A technology invented in 1967 has now entered our daily use equipment-mobile phones. We are talking about Facial Recognition Technology (FRT). While originally used for regulation, prevention and security, we can now unlock our phones and even apps through FRT.
It uses a combination of artificial intelligence and biometric technology to recognize faces. FRT technology replaces long and complex passwords, allowing users to easily access applications. This technology adds another layer of security, keeping user data safe.
Do you have an app without facial recognition technology? Then you must know that the global FRT market is expected to grow to USD 9,523.15 million by 2025. The reasons are system security, user safety and better user engagement. Therefore, it is very important to integrate it into mobile applications.
How does facial recognition technology work?
Facial recognition technology uses algorithms to analyze facial images or video frames and compare them to a database of known faces to try to identify an individual. Here's a general overview of how the process works:
- Detection: The first step is to detect a face in an image or video frame. It can be done using various techniques such as Haar cascade, which is a classifier that detects the exact location of an object in an image based on its characteristics.
- Alignment: After a face is detected, the algorithm attempts to align it into standard positions by locating key facial features such as eyes, nose, and mouth.
- Feature Extraction: The algorithm then extracts various features from the face, such as the distance between the eyes, the shape of the chin, and the curvature of the lips. These features are used to create a digital representation of the face, called a facial imprint or facial template.
- Comparison: The facial print is then compared to a database of known facial prints to try to identify the individual. This can be done using various techniques, such as Euclidean distance, which measures the similarity between two facial prints by calculating the distance between them in a high-dimensional space.
- Verification or identification: Depending on the intended use case, the algorithm can verify that an individual is who they claim to be (e.g., at a security checkpoint) or attempt to identify an individual based solely on their face ( For example, in criminal) investigation).
It is worth noting that facial recognition technology has various challenges and limitations, such as changes in lighting and posture, as well as potential bias and privacy issues.
How to implement FRT in your app
The big question when applying face recognition in a mobile app is, which method to use? There are multiple ways to implement it, these are:
1.OpenCV and Python
OpenCV is an open source computer vision library and Python is a popular ML programming language. You can use OpenCV with Python to implement face recognition in your application. Here are the basic steps:
- Capture images from camera using OpenCV.
- Preprocess images to extract facial features and align faces.
- Train the model on preprocessed data using a machine learning algorithm such as a support vector machine or convolutional neural network.
- Integrate the model into your application so that it can recognize faces in real time.
2. Native API
One of the easiest ways to create facial recognition software for Android and iOS is with the help of native APIs from Google and Apple. These are affordable, easy to implement, and require no additional cost or effort. Integrate the API in your application and ensure reliable image detection and recognition capabilities.
3. Microsoft Azure Cognitive Services
Microsoft Azure provides a set of pre-built APIs that you can use to add facial recognition to your applications. Here's how to use the Azure Face API:
- Send images to the Face API to detect and recognize faces.
- Use the Face API to identify facial features and attributes such as age, gender, and emotion.
- Integrate the API into your application to recognize faces and display relevant information.
4. Google Cloud Vision API
Google Cloud also provides a facial recognition API that you can use to add facial detection and recognition capabilities to your applications. Here's how you can use the Google Cloud Vision API:
- Send images to the Vision API to detect and recognize faces.
- Use the API to extract facial features such as eyes and nose.
- Integrate the API into your application to recognize faces and perform related tasks.
It’s important to remember that these are just some examples, there are many other techniques and frameworks that can be used to implement facial recognition in applications. Some other ways to integrate facial recognition technology into your applications include Amazon Rekognition, luxand.cloud API, and others. The choice of technology will depend on your specific use cases, requirements and expertise.
Summary
To successfully implement facial recognition, it is critical to evaluate factors such as the type of recognition algorithm used, data privacy and security issues, user experience, and hardware requirements. It’s also important to conduct thorough testing and user feedback to ensure the feature works effectively and meets user needs. With proper planning and execution, facial recognition can be a powerful addition to any application, providing users with a seamless and secure experience.
The above is the detailed content of How to integrate facial recognition technology in mobile apps. For more information, please follow other related articles on the PHP Chinese website!
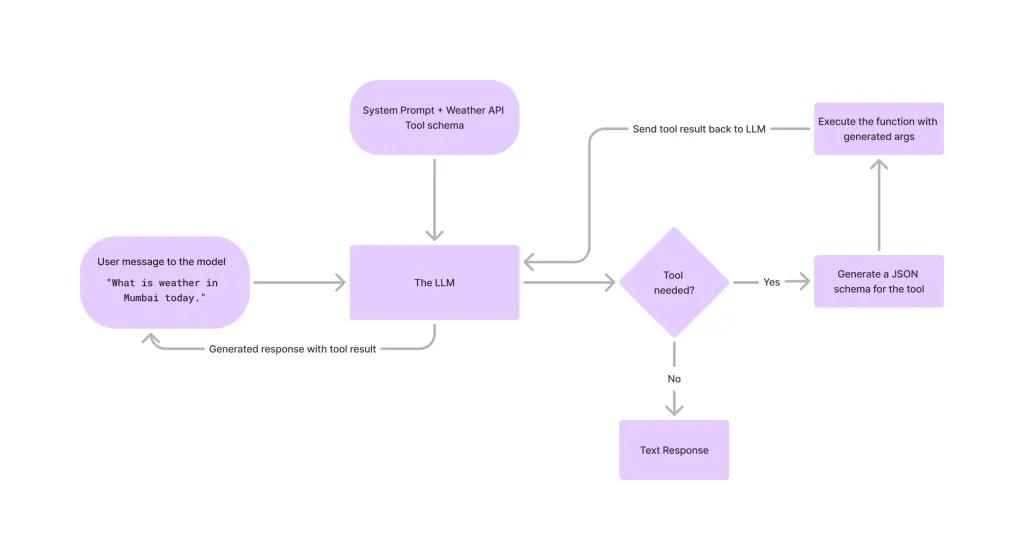 Tool Calling in LLMsApr 14, 2025 am 11:28 AM
Tool Calling in LLMsApr 14, 2025 am 11:28 AMLarge language models (LLMs) have surged in popularity, with the tool-calling feature dramatically expanding their capabilities beyond simple text generation. Now, LLMs can handle complex automation tasks such as dynamic UI creation and autonomous a
 How ADHD Games, Health Tools & AI Chatbots Are Transforming Global HealthApr 14, 2025 am 11:27 AM
How ADHD Games, Health Tools & AI Chatbots Are Transforming Global HealthApr 14, 2025 am 11:27 AMCan a video game ease anxiety, build focus, or support a child with ADHD? As healthcare challenges surge globally — especially among youth — innovators are turning to an unlikely tool: video games. Now one of the world’s largest entertainment indus
 UN Input On AI: Winners, Losers, And OpportunitiesApr 14, 2025 am 11:25 AM
UN Input On AI: Winners, Losers, And OpportunitiesApr 14, 2025 am 11:25 AM“History has shown that while technological progress drives economic growth, it does not on its own ensure equitable income distribution or promote inclusive human development,” writes Rebeca Grynspan, Secretary-General of UNCTAD, in the preamble.
 Learning Negotiation Skills Via Generative AIApr 14, 2025 am 11:23 AM
Learning Negotiation Skills Via Generative AIApr 14, 2025 am 11:23 AMEasy-peasy, use generative AI as your negotiation tutor and sparring partner. Let’s talk about it. This analysis of an innovative AI breakthrough is part of my ongoing Forbes column coverage on the latest in AI, including identifying and explaining
 TED Reveals From OpenAI, Google, Meta Heads To Court, Selfie With MyselfApr 14, 2025 am 11:22 AM
TED Reveals From OpenAI, Google, Meta Heads To Court, Selfie With MyselfApr 14, 2025 am 11:22 AMThe TED2025 Conference, held in Vancouver, wrapped its 36th edition yesterday, April 11. It featured 80 speakers from more than 60 countries, including Sam Altman, Eric Schmidt, and Palmer Luckey. TED’s theme, “humanity reimagined,” was tailor made
 Joseph Stiglitz Warns Of The Looming Inequality Amid AI Monopoly PowerApr 14, 2025 am 11:21 AM
Joseph Stiglitz Warns Of The Looming Inequality Amid AI Monopoly PowerApr 14, 2025 am 11:21 AMJoseph Stiglitz is renowned economist and recipient of the Nobel Prize in Economics in 2001. Stiglitz posits that AI can worsen existing inequalities and consolidated power in the hands of a few dominant corporations, ultimately undermining economic
 What is Graph Database?Apr 14, 2025 am 11:19 AM
What is Graph Database?Apr 14, 2025 am 11:19 AMGraph Databases: Revolutionizing Data Management Through Relationships As data expands and its characteristics evolve across various fields, graph databases are emerging as transformative solutions for managing interconnected data. Unlike traditional
 LLM Routing: Strategies, Techniques, and Python ImplementationApr 14, 2025 am 11:14 AM
LLM Routing: Strategies, Techniques, and Python ImplementationApr 14, 2025 am 11:14 AMLarge Language Model (LLM) Routing: Optimizing Performance Through Intelligent Task Distribution The rapidly evolving landscape of LLMs presents a diverse range of models, each with unique strengths and weaknesses. Some excel at creative content gen


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

Dreamweaver CS6
Visual web development tools

WebStorm Mac version
Useful JavaScript development tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Zend Studio 13.0.1
Powerful PHP integrated development environment






