Home >Common Problem >Which layer does the IP protocol belong to?
Which layer does the IP protocol belong to?
- 青灯夜游Original
- 2022-11-23 11:11:4915903browse
The IP protocol belongs to the network layer. IP refers to Internet Protocol, the abbreviation of Internet Protocol. It is a network layer protocol in the TCP/IP system (equivalent to the network layer of the OSI model). It can provide various protocol information to the transport layer, such as TCP, UDP, etc.; Next, IP information packets can be placed at the link layer and transmitted through various technologies such as Ethernet and Token Ring networks.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
IP refers to Internet Protocol, the abbreviation of Internet Protocol, which is the network layer protocol in the TCP/IP system. The purpose of designing IP is to improve the scalability of the network: first, to solve Internet problems and realize the interconnection of large-scale and heterogeneous networks; second, to separate the coupling relationship between top-level network applications and underlying network technologies to facilitate the two. Develop independently. According to the end-to-end design principle, IP only provides a connectionless, unreliable, best-effort packet transmission service to the host.

IP is the core of the entire TCP/IP protocol suite and the foundation of the Internet. IP is located in the network layer of the TCP/IP model (equivalent to the network layer of the OSI model). It can provide various protocol information to the transport layer, such as TCP, UDP, etc.; IP information packets can be placed in the link layer. Transmitted through various technologies such as Ethernet and Token Ring networks.
In order to adapt to heterogeneous networks, IP emphasizes adaptability, simplicity and operability, and makes certain sacrifices in reliability. IP does not guarantee the delivery time and reliability of packets. The transmitted packets may be lost, duplicated, delayed or out of order.
The main content of ip protocol
IP mainly includes three aspects: IP addressing scheme, packet encapsulation format and packet forwarding rules.
Forwarding rules of IP packets
The router forwards only based on the network address. When an IP data packet is forwarded via a router, if the target network is directly connected to the local router, the data packet is delivered directly to the target host, which is called direct delivery; otherwise, the router looks up the routing information through the routing table and transfers the data packet to Specified next-hop router, this is called indirect delivery. In indirect delivery, if the router has a route to the target network in the routing table, it will deliver the data packet to the next-hop router specified in the routing table; if there is no route but there is a default route in the routing table, it will deliver the data packet. Gives the specified default router; if neither is present, the packet is dropped and an error is reported.
IP Fragmentation
An IP packet may need to pass through multiple different physical networks to be transmitted from the source host to the destination host. Since the data frames of various networks have a maximum transmission unit (MTU) limit, for example, the MTU of an Ethernet frame is 1500; therefore, when the router is forwarding IP packets, if the size of the data packet exceeds the maximum size of the egress link, When transmitting units, the IP packet will be broken down into many fragments that are small enough to be transmitted on the target link. These IP fragments re-encapsulate an IP packet for independent transmission and are reassembled when it reaches the destination host.
IP packet structure
An IP packet consists of header and data. The first 20 bytes of the header are required by all IP packets and are also called fixed headers. Following the fixed part of the header are some optional fields, the length of which is variable.
IP packet structure
IP datagram header diagram
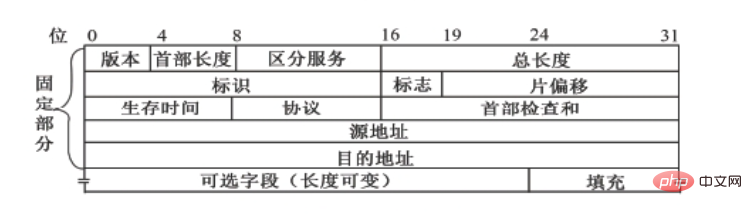
IP datagram header The meaning of the field
ip protocol version
IPv4 protocol
Internet Protocol version 4 ( Internet Protocol version 4 (IPv4) is the datagram transmission mechanism used by the TCP/IP protocol. A datagram is a variable-length packet consisting of two parts: header and data. The header length can consist of 20~60 bytes, and this part contains important information related to routing and transmission. The meaning of each field in the header is as follows in order: [3]
(1) Version (4 bits): This field defines the IP protocol version and is responsible for indicating to the IP software running on the processor which IP datagram it is. Version, all fields are to be interpreted according to this version's protocol. If the computer uses a different version, the datagram is discarded.
(2) Header length (4 bits): This field defines the length of the datagram protocol header, indicating the number of 32-bit word lengths in the protocol header. The minimum value of the protocol header is 5 and the maximum value is 15.
(3) Service (8 bits): This field defines the service quality expected by the upper layer protocol for processing the current datagram, and allocates the datagram according to the importance level. The first 3 bits become the priority bits, the last 4 bits become the service type, and the last 1 bit is not defined. These 8-bit fields are used to assign priority, latency, throughput, and reliability.
(4) Total length (16 bits): This field defines the byte length of the entire IP datagram, including protocol header and data. Its maximum value is 65535 bytes. The Ethernet protocol has minimum and maximum limits (46~1500 bytes) on the data that can be encapsulated in a frame.
(5) Identification (16 bits): This field contains an integer used to identify the current datagram. When a datagram is fragmented, the value of the identification field is copied to all fragments. This field is allocated by the sender to help the receiver focus on datagram fragmentation.
(6) Flag (3 bits): This field consists of a 3-bit field, of which the lowest bit (MF) controls segmentation. If there is a next segment, it is set to 1, otherwise it is set to 0 to indicate that the segment is The last segment. The middle bit (DF) indicates whether the datagram can be fragmented. If it is 1, the machine cannot fragment the datagram. The third bit, the highest bit, is reserved unused and has a value of 0.
(7) Segmentation offset (13 bits): This field indicates the relative position of the segmented data in the source datagram, supporting the target IP to properly reconstruct the source data.
(8) Lifetime (8 bits): This field is a counter, and the value is decremented by 1 at each point of discarding the datagram until it is reduced to 0. This ensures that the datagram has a limited loop process (ie TTL), limiting the life of the datagram.
(9) Protocol (8 bits): This field indicates which upper-layer protocol receives the incoming datagram after the IP processing is completed. The value of this field is helpful for the receiving network layer to know which protocol the data belongs to.
(10) Header checksum (16 bits): This field helps ensure the integrity of the IP protocol header. Due to changes in some protocol header fields, this requires recalculation and verification for each point. The calculation process is to first set the checksum field to 0, then divide the entire header into parts every 16 bits, add the parts, and then take the complement of the calculation result and insert it into the checksum field.
(11) Source address (32 bits): Source host IP address. This field must remain unchanged during the transmission of IPv4 datagrams from the source host to the destination host.
(12) Destination address (32 bits): IP address of the destination host. This field must also remain unchanged during the transmission of the IPv4 datagram from the source host to the destination host.
IPv6 protocol
Since the advent of IPv4 in the 1970s, data communication technology has developed rapidly. Although IPv4 is well designed, its shortcomings are gradually revealed: ① Although the efficiency of IP address usage can be improved with the help of subnetting, classless addressing and NAT technology, the exhaustion of IP addresses in the Internet is still a problem that has not been completely solved Problems; ② IPv4 does not provide support for policies and reserved resources that require minimum transmission delay for real-time audio and video transmission; ③ IPv4 cannot provide support for certain applications that require data encryption and authentication. In order to overcome these shortcomings, IPv6 (Internet working Protocol version 6) was proposed. In IPv6, the IP address format and packet length as well as the format of the packet have changed. Each IPv6 packet consists of a necessary basic header followed by a payload. The payload consists of optional extension headers and data from upper layers. The basic header occupies 40 bytes and the payload can contain 65535 bytes of data. The meaning of each field in the IPv6 header is as follows in order:
(1) Version (4 bits): This field defines the IPv6 protocol version, its value is 6, and is responsible for indicating this IP data to the IP software running on the processor The reported version is IPv6.
(2) Priority (4 bits): This field defines the priority of the packet when communication congestion occurs.
(3) Stream label (24 bits): This field is used to provide specialized processing for special data streams.
(4) Payload length (16 bits): This field defines the byte length of the entire IPv6 datagram, including the basic header and payload. Its maximum value is 65,535 bytes.
(5) Next header (8 bits): This field defines the header that follows the basic header in the datagram. The next header can be an optional extension header used by IP, or a header from an upper layer protocol.
(6) Number of entries limit (8 bits): This field is a counter like the Time to Live (TTL) field in IPv4. At each point when the datagram is discarded, the value is decremented by 1 until it is reduced to 0. .
(7) Source address (128 bits): Source host IP address. This field must remain unchanged during the transmission of IPv4 datagrams from the source host to the destination host.
(8) Destination address (128 bits): IP address of the destination host. This field must also remain unchanged during the transmission of the IPv4 datagram from the source host to the destination host.
(9) Extension header: This field contains 6 optional types, including hop-by-hop options, source routing, segmentation, authentication, encrypted security payload, and destination options.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of Which layer does the IP protocol belong to?. For more information, please follow other related articles on the PHP Chinese website!
Related articles
See more- In the IP protocol, IP addresses are divided into several categories:
- What layers does the tcp/ip protocol contain?
- What are the four protocols used in conjunction with the IP protocol?
- In the tcp/ip protocol, what kind of protocol is the udp protocol?
- What is the IP protocol used for?
- What layers does the tcp/ip protocol contain?



