The role of encryption on the Internet is to prevent useful or private information from being intercepted and stolen on the Internet. The encrypted password is unreadable even if it is obtained by a hacker. The encrypted bidding document cannot be decrypted without the recipient's private key. The bidding document becomes a lot of garbled code without any practical meaning, so even if it is stolen, there will be no trace. loss; so encryption is very important to protect files.

The operating environment of this tutorial: Windows 7 system, Dell G3 computer.
The rapid development of network technology has facilitated our daily lives, accelerated work efficiency, and enhanced communication. The emergence of the Internet has indeed brought us a lot of convenience, but network security issues have always troubled us. Viruses and hackers are rampant, and various threats are constantly coming out. Network security issues have also become a concern of society. Key issues. File transmission security is one of the security issues of public concern. A file may contain many secrets. Once stolen by hackers, the loss will be unimaginable.
What is file encryption:
File encryption is simply to process the original plaintext file according to a certain algorithm to make it an unreadable piece of code. , often called "ciphertext". The original content can only be displayed after entering the corresponding key. In this way, the purpose of protecting the data from being illegally stolen and read is achieved. The reverse of this process is decryption, the process of converting the encoded information into its original data.
Why should we encrypt files:
We know that there are many unsafe factors in file transfer and email business transactions on the Internet, especially for some large companies and Some confidential documents are transmitted over the network. And this insecurity is inherent in the TCP/IP protocol, the foundation of the Internet, including some TCP/IP-based services; so in order to ensure security, we must encrypt files.
The role of encryption on the Internet is to prevent useful or private information from being intercepted and stolen on the Internet. A simple example is the transmission of passwords. Computer passwords are extremely important. Many security protection systems are based on passwords. In a sense, the leakage of passwords means the complete collapse of their security systems. When logging in through the network, the typed password is transmitted to the server in clear text, and eavesdropping on the network is extremely easy, so it is very likely that hackers will steal the user's password. If the user is a Root user or Administrator users, the consequences will be extremely serious.
The solution to the above problem is encryption. The encrypted password is unreadable even if it is obtained by a hacker. The encrypted bidding document cannot be decrypted without the recipient's private key. The bidding document becomes a large pile of unreadable documents. Any garbled code in any practical sense, so there will be no loss even if it is stolen. So encryption is very important to protect files.
Encryption Types
Encryption is based on mathematical encoding and decoding of information. There are two types of encryption, symmetric encryption and asymmetric encryption. Both parties of symmetric encryption use a common key (of course, this key needs to be kept secret).
Here we talk about asymmetric encryption. There are two keys in this encryption method. The key - one is the public key (as the name suggests, this is a public key value), and the other is the public key. The first is the private key (secret to the outside world). When you send information to us, it is encrypted using a public key. Once we receive your encrypted message, we use your private key to decrypt the message (message encrypted by our public key can only be decrypted by our private key), thus technically ensuring that only we can decrypt the message. Interpretation - because others do not have our private key). Information encrypted using the private key can only be decrypted using the public key (this function is applied in the field of digital signatures. The data encrypted by my private key can only be decrypted by my public key. For details, please refer to the information on digital signatures) and vice versa. to ensure the security of your information.
Encryption Tips
The following tips can enhance the security of encryption:
1. Do not use old encryption algorithms
Businesses should stop using older encryption algorithms like DES and its relative 3DES (Triple Data Encryption Standard).
2. Use the longest encryption key supported by the enterprise
It is recommended that enterprises use the largest length key possible, which can make it difficult for those enterprises without access to backdoors to crack the enterprise's encryption. AES 128 is pretty robust these days, but if possible, use AES 512 or longer keys.
3. Multi-layer encryption
It is recommended that enterprises utilize multi-layer encryption as much as possible, which can increase the difficulty for attackers. If possible, encrypt every field, every table, and the entire database.
4. Secure storage of encryption keys
The biggest problem facing enterprises may not be that the encryption algorithm has been left with a backdoor by the US National Security Agency, but that the password itself is only part of the encryption scheme. Other elements of the infrastructure, such as key management systems, must also be secured. Attackers are willing to target the weakest link in a security system. If an attacker can easily steal the key, why go to the trouble of cracking the encryption algorithm?
Some enterprises give the keys to protect their data to third parties, especially when the enterprise stores the data in a public cloud and is encrypted and protected by the cloud provider. The problem here is that the enterprise has no control over the keys and must instead trust the cloud provider's employees to keep the keys securely.
It would be much more secure if businesses could implement an encryption system that controlled the keys in the cloud. Cloud encryption gateways that automatically handle encryption can help companies achieve this security.
5. Ensure encryption is implemented correctly
In fact, implementing an encryption system is not an easy task because it has many dynamic parts, any one of which may become a weak link. You have to do a lot of research to make sure encryption is implemented correctly.
What areas are prone to errors when implementing encryption? In addition to the keys being vulnerable, there is also the implementation of CBC (Cryptoblock Chaining). Using CBC, plain text can be Then, the previously generated ciphertext block is used as an initialization vector to perform an XOR operation on the next plain text block.
Correct implementation of CBC requires that each process be started with a new initialization vector. A common mistake is to implement CBC with a static initialization vector that does not change. If CBC is implemented correctly, then if we encrypt a block of text on two different occasions, the resulting ciphertext block will not be the same.
6. Don’t ignore external factors
External factors that a company has little control over have the potential to undermine the security of an encryption system. For example, SSL relies on digital certificates, and these factors rely on the integrity of the root certificate authority embedded in the browser (such as IE, Firefox, Chrome, etc.). But how do we know if they are trustworthy, or if these certificate authorities are not a front for some foreign intelligence agency? If you think this sounds far-fetched, it could be true.
In addition, DNS is also a weakness that must be taken seriously. Once the DNS is compromised, attackers can use phishing techniques to bypass encryption.
Of course, the emphasis here is on the various possibilities of encryption issues. A properly implemented encryption system can only be broken under one condition, namely by testing the key. It is not impossible to guess the key in a short time, but it is extremely unlikely.
For more related knowledge, please visit the FAQ column!
The above is the detailed content of What is the role of encryption on the Internet?. For more information, please follow other related articles on the PHP Chinese website!
 Redis作为缓存数据库的数据压缩与加密方案Jun 21, 2023 am 08:48 AM
Redis作为缓存数据库的数据压缩与加密方案Jun 21, 2023 am 08:48 AMRedis作为一款开源的内存缓存数据库,在应用开发中极度广泛。其强大、高效的性能优势,使得其成为了最常用的缓存数据库之一。然而,在某些特殊场景下,由于数据量过大或安全性需要,我们需要对Redis数据进行压缩和加密处理。本文将从Redis的数据压缩和加密两方面入手,探讨Redis作为缓存数据库在实际应用中的数据压缩与加密方案。一、Redis数据压缩方案Re
 如何使用PHP ZipArchive实现对压缩包的文件内容加密和解密?Jul 21, 2023 pm 06:44 PM
如何使用PHP ZipArchive实现对压缩包的文件内容加密和解密?Jul 21, 2023 pm 06:44 PM如何使用PHPZipArchive实现对压缩包的文件内容加密和解密?在进行文件传输或存储时,保护数据安全是非常重要的。使用密码对压缩包的文件内容进行加密和解密可以有效地避免数据泄漏的风险。PHP提供了一个名为ZipArchive的类,它可以用来创建和操作ZIP格式的压缩包。本文将介绍如何使用PHPZipArchive类实现对压缩包的文件内容加密和解密。创
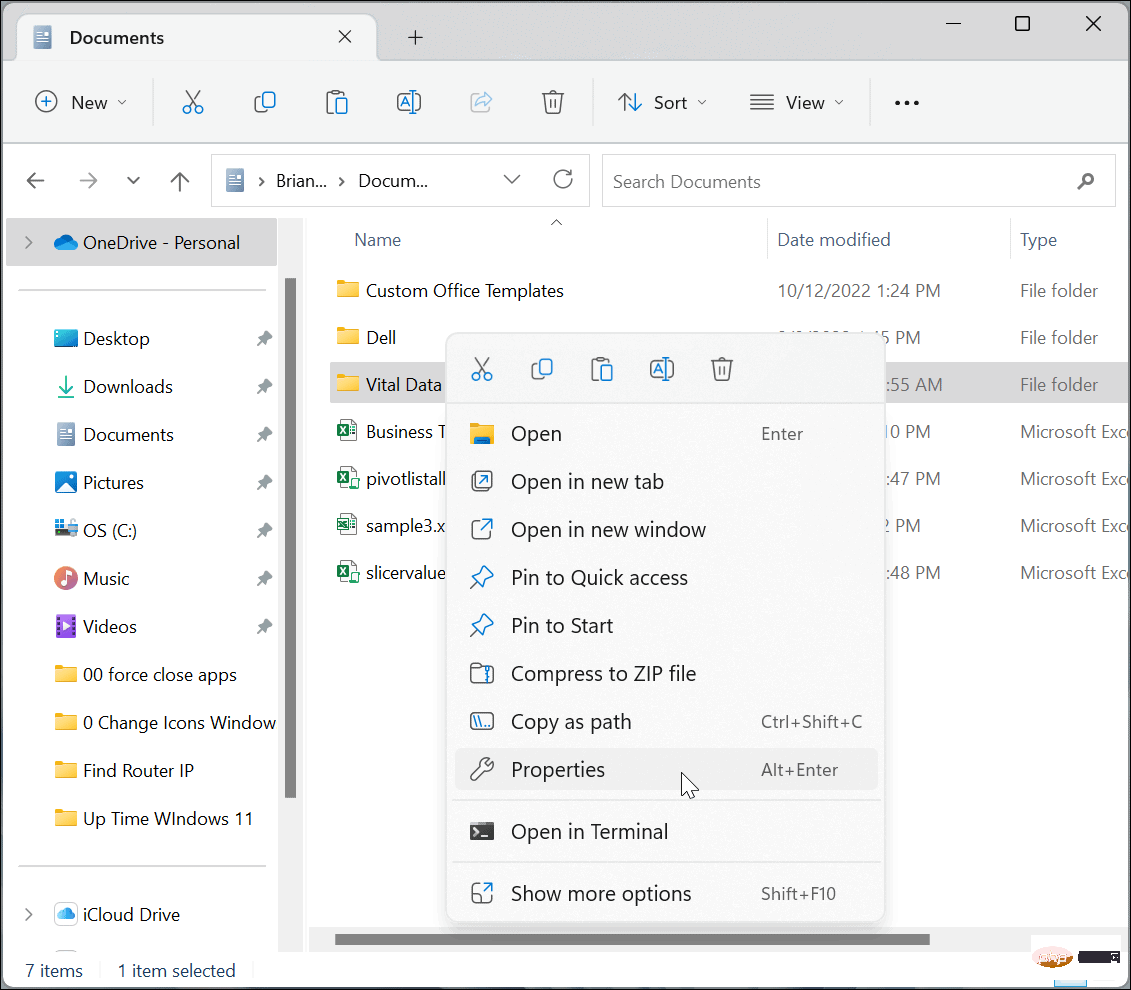 如何在 Windows 11 上加密文件和文件夹May 03, 2023 pm 06:46 PM
如何在 Windows 11 上加密文件和文件夹May 03, 2023 pm 06:46 PM在Windows11上加密文件和文件夹与WindowsBitLocker一样,EFS加密可用于加密您PC上最重要的文件。使用内置加密非常简单,而且触手可及。此外,由于EFS与您的用户帐户相关联,我们将向您展示如何将加密密钥备份到安全位置,这样您就永远不会失去对文件和文件夹的访问权限。注意:要使用EFS,您的PC必须运行Windows11专业版、企业版或教育版。EFS加密在Windows11家庭版上不可用。要加密充满文件的文件夹或单个文件,请使用以下步骤:
 PHP实现SHA加密技术Jun 18, 2023 pm 02:51 PM
PHP实现SHA加密技术Jun 18, 2023 pm 02:51 PMSHA(SecureHashAlgorithm)加密技术是一种常用的安全加密算法。在PHP开发中,SHA加密技术通常用于加密账户密码以及保护敏感数据。本文将介绍如何在PHP中实现SHA加密技术。SHA算法简介SHA算法是一种信息摘要算法,通常用于数据的完整性保护和身份验证。SHA算法的主要作用是将任意长度的消息转换为一个固定长度的消息摘要(即哈希值),通
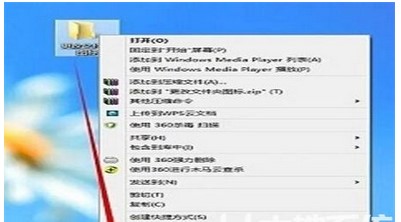 windows10家庭版如何加密文件夹Jul 12, 2023 pm 08:33 PM
windows10家庭版如何加密文件夹Jul 12, 2023 pm 08:33 PMwindows10家庭版如何加密文件夹呢,加密文件夹这个功能一般客户没有使用,但是如果想要设定的话也是可行的,首先在想要加密的文件夹中右键属性进到高级,然后选择缩小加密属性,加密内容维护数据,下面就是具体的windows10家庭版如何加密文件夹方式介绍,大家如果想要学会的话就接着往下看。windows10家庭版如何加密文件夹1.最先,先找到想要加密的文件夹,然后用鼠标右键文件夹,在弹出的菜单中选择底部的“属性”选项,点击查看;2.随后,将打开文件的属性窗口,点击窗口里的“高级”按键进到;3.接着
 PHP和XML:如何实现数据的加密和解密Aug 07, 2023 am 09:46 AM
PHP和XML:如何实现数据的加密和解密Aug 07, 2023 am 09:46 AMPHP和XML:如何实现数据的加密和解密引言:在现代的互联网时代,数据的安全性越来越受到重视。其中,对于敏感数据的加密和解密成为了保护数据安全的重要手段之一。本文将通过使用PHP和XML来实现数据的加密和解密,并提供相关的代码示例。加密数据的实现使用PHP的加密函数,可以轻松实现对数据的加密。下面是一个使用AES加密算法对数据进行加密的示例代码://待加密
 如何进行代码授权和加密保护?Jun 12, 2023 am 09:33 AM
如何进行代码授权和加密保护?Jun 12, 2023 am 09:33 AM在当前信息化时代,网络上存在着大量的软件、程序和代码文件,其中有不少代码是需要被保护的,以避免被盗版或恶意利用,同时也有些代码需要进行授权以获得经济收益。那么,问题就来了:如何进行代码授权和加密保护呢?一、代码授权代码授权是指在一定的条件下,授予使用或修改、发布软件或程序源代码的权利。此时,程序开发者作为版权人,需要明确在何种情况下允许其他人使用代码、以何
 如何通过PHP ZipArchive实现对压缩包的加密和解密操作?Jul 22, 2023 pm 04:36 PM
如何通过PHP ZipArchive实现对压缩包的加密和解密操作?Jul 22, 2023 pm 04:36 PM如何通过PHPZipArchive实现对压缩包的加密和解密操作?概述:PHPZipArchive是一种用于创建、打开和操作ZIP压缩文件的功能强大的类。尽管ZipArchive类本身并不直接提供加密和解密ZIP压缩文件的功能,但我们可以利用一些PHP扩展来实现对压缩包的加密和解密操作,如openssl扩展。在本文中,我们将介绍如何使用PHPZipArc

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),






