Home >PHP Framework >Swoole >Organize swoole knowledge points in detail (summary sharing)
Organize swoole knowledge points in detail (summary sharing)
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBforward
- 2022-02-28 18:13:523673browse
This article brings you relevant knowledge about swoole, including fastcgi requesting to the swoole master process to distribute to child processes, but it will not be like the php-fpm child process that exits after use and other related issues. I hope everyone has to help.

Recommended learning: swoole video tutorial
##swooleChat room process explanation
##The entire chat room process is:
- User http interface login is authorized
- Get the friend list, the last unread message of different friends and the number of unread messages (for homepage display) through authorized request http interface
- Obtain the group list through authorization request (group messages are not read or unread to save storage space)
- Create ws link
-Register the disconnection and reconnection mechanism. When the close event is triggered, reconnect ws
- Set up a ping timer and ping every 30 seconds
##- Through the ws interface, all unread messages are obtained, processed by the client, and pushed to the notification bar, etc.
##- Receive new message push and display it in the message list- When you click into a group/friend message interface, you will automatically get the latest n messages, the user will continue to obtain n messages when pulling up
## Run mode operation
cgi protocol mode
cgi mode Common Gateway Interface (Common Gateway Interface), which allows the web server to pass a specific protocol To communicate with the application, the calling principle is roughly:
User request->Web server receives request->fork child process
Call the program/execute the program->The program returns the content/The program call ends->The web server receives the content->Return to the user
Since each user request has to fork to create a process, call the program once, and then destroy the process, so the performance is low
fast-cgi protocol mode
##fast-cgi is an upgraded version of cgi mode, it is like It is a resident cgi. As long as it is turned on, it can always process requests without ending the process. The calling principle is roughly:
Web server fast-cgi process manager initialization->fork n processes in advance
User request->web server receives request->hands it to fast-cgi process manager->fast-cgi process management area receives it and gives it to one of the free fast-cgi Process processing->The processing is completed, the fast-cgi process becomes idle, waiting for the next request->The web server receives the content->Returns to the userModule mode When apache php is running, the module mode is used by default, which uses php as apache The module is started when apache is started. When a user request is received, it is processed directly by calling the mod_php module. The details can be found on Baidu ##php-cli mode belongs to the command line mode. It is the most suitable for many developers who have just started learning PHP and started wamp and wnmp. An unfamiliar operating mode This mode does not require the use of other programs, you can directly enter php xx.php to execute the php code The command line mode is obviously different from the regular web mode in: * None Timeout * Buffer buffering is turned off by default * Use of STDIN and STDOUT standard input/output/error * echo var_dump, phpinfo and other outputs are output directly Go to the console * The classes/functions that can be used are different * Differences in php.ini configuration
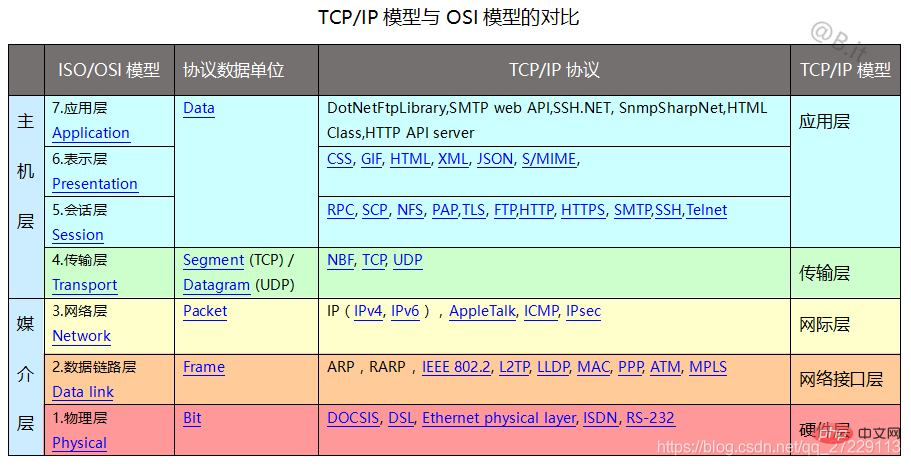
The network protocol is divided into seven levels according to the steps of communication. From top to bottom: ##Application layer
Presentation layer
Session Layer
Transport layer
Network layer
data link layer
Physical layer
IP protocol is the basic protocol of the Internet. It is currently the most popular network protocol The responsibility of IP is to transmit data from source to destination. It is not responsible for ensuring delivery reliability, flow control, packet ordering, and other services common to host-to-host protocols. This protocol is called by the host-to-host protocol, and this protocol is responsible for calling the local network protocol to transmit the data packet to the next gateway or destination host. For example, TCP can call the IP protocol, passing the destination address and source address as parameters when calling. IP forms a data packet and calls the local network (protocol) interface to transmit the data packet. IP implements two basic functions: addressing and segmentation. IP can transmit the data packet to the destination address according to the destination address included in the data packet header. In this process, IP is responsible for selecting the transmission path. This path selection is called the routing function. If some networks can only transmit small data packets, IP can reassemble the data packets and indicate this in the header field. These basic functions are included in the IP module, which exists on every host and gateway in the network, and these modules (especially on the gateway) have routing and other service functions. For IP, there is no connection between data packets, and it is difficult to say anything about connections or logical links for IP. IP uses four key technologies to provide services: service type, time to live, options, and header check codes. Service type refers to the quality of service expected. A service type is a set of parameters that represent the services that the Internet can provide. This service type is used by gateways to select the actual delivery parameters on a specific network, or on the next network to pass through, or the next gateway to route this packet. Time-to-live is the upper limit on how long a packet can live. It is set by the sender and processed by the route. If the time-to-live is zero when not arriving, discard the packet. The option is important for control functions, but for normal communication its presence is not necessary. Options include timestamps, security and special routing. The header check code ensures the correct transmission of data. If the check fails, the entire packet is discarded. When transmitting data from source to destination, an IP address is required for transmission. Now IP addresses are divided into two types: IPv4 and IPv6. The most common one now is IPv4 address, such as 127.0.0.1 (this machine Address) 119.75.217.109 (Baidu ip) ip transmission must have a clear ip address before data can be sent ##TCP (Transmission Control Protocol) It is a connection-oriented, reliable, byte stream-based transport layer communication protocol, defined by IETF's RFC 793. In the simplified computer network OSI model, it completes the functions specified by the fourth layer transport layer. User Datagram Protocol (UDP) is another important transport protocol within the same layer. In the Internet protocol suite, the TCP layer is an intermediate layer located above the IP layer and below the application layer. Reliable, pipe-like connections are often required between application layers of different hosts, but the IP layer does not provide such a flow mechanism, but provides unreliable packet switching. The application layer sends a data stream represented by 8-bit bytes for inter-network transmission to the TCP layer, and then TCP The data stream is partitioned into segments of appropriate length (usually limited by the maximum transmission unit (MTU) of the data link layer of the network to which the computer is connected). TCP then passes the resulting packet to the IP layer, which delivers the packet through the network to the TCP layer of the receiving entity. In order to ensure that packet loss does not occur, TCP gives each packet a sequence number. At the same time, the sequence number also ensures that the packets transmitted to the receiving end entity are received in order. The receiving entity then sends back a corresponding acknowledgment (ACK) for the successfully received packet; if the sending entity does not receive an acknowledgment within a reasonable round trip delay (RTT), the corresponding data packet is assumed to have been received. Lost data will be retransmitted. TCP uses a checksum function to check whether the data has errors; checksums are calculated both when sending and receiving. TCP is the transport layer protocol in the Internet, which uses a three-way handshake protocol to establish a connection. After the active party sends a SYN connection request, it waits for the other party to respond with SYN ACK, and finally performs ACK confirmation on the other party's SYN. This method of establishing a connection can prevent erroneous connections. The flow control protocol used by TCP is a variable-size sliding window protocol. The process of TCP three-way handshake is as follows: The client sends a SYN (SEQ=x) message to the server and enters the SYN_SEND state.
#The server receives the SYN message, responds with a SYN (SEQ=y) ACK (ACK=x 1) message, and enters the SYN_RECV state.
The client receives the SYN message from the server, responds with an ACK (ACK=y 1) message, and enters the Established state.
After the connection is successful, both parties can transmit byte streams to each other, and the connection can be closed at any time. The transmitted data has the following characteristics The transmitted data is divided by tcp into data blocks most suitable for sending and passed to the ip protocol. This sending data is called a message segment or segment
tcp is a reliable connection. Each time a data segment is sent, a timer will be started. Each time a data segment is received, a confirmation will be sent. If the timer does not receive the data in time, When confirmed, the data will be resent
TCP will maintain a checksum of its header and data. This is an end-to-end checksum designed to detect any changes in the data during transmission. If there is an error in the checksum of a received segment, TCP will discard the segment and not acknowledge receipt of the segment (hoping that the sender will time out and resend).
#Two applications exchange a byte stream of 8-bit bytes through a TCP connection. TCP does not insert record identifiers into the byte stream. We call this bytestream service. If one party's application first transmits 10 bytes, then 20 bytes, and then 50 bytes, the other party of the connection will not be able to understand how many bytes the sender sent each time. As long as its own receive buffer is not full, the TCP receiver will receive as many as it can receive. One end puts a stream of bytes onto a TCP connection, and the same stream of bytes will appear on the other end of the TCP connection.
Establishing a connection requires three handshakes, and terminating a connection requires four waves. This is caused by TCP's half-close. The specific process is as follows. An application process first calls close, which is said to perform an "active close". The TCP on that end then sends a FIN segment to indicate that the data has been sent.
The peer that receives this FIN performs a "passive close" (passive close), and this FIN is confirmed by TCP.
Note: The reception of FIN is also passed to the receiving application process as an end-of-file, and is placed in the queue waiting for the application process to receive it. After any other data, because the reception of FIN means that the receiving application process has no additional data to receive on the corresponding connection.
#After a while, the application process that receives this end-of-file character will call close to close its socket. This causes its TCP to also send a FIN.
The original sending end TCP that receives this final FIN (that is, the end that performs active shutdown) confirms this FIN. Since each direction requires a FIN and an ACK, 4 segments are usually required.
"Usually" means that in some cases, the FIN of step 1 is sent together with the data. In addition, the segments sent in steps 2 and 3 are both From the side that performs passive shutdown, it is possible to be merged into a section. Between steps 2 and 3, it is possible to flow data from the side that performs passive shutdown to the side that performs active shutdown. This is called "half-close". When a Unix process terminates, either voluntarily (calling exit or returning from the main function) or involuntarily (receiving a signal that terminates the process), all open descriptors are closed, which also results in any TCP still open A FIN is also issued on the connection. Either client or server can perform an active shutdown. Typically, the client performs an active shutdown, but some protocols, such as HTTP/1.0, have the server perform an active shutdown. php can be accessed through socket Function, swoole extension, stream flow function creates a socket of the tcp protocol, binds the network card port, and performs tcp server/client operations. In php, we do not need to know the tcp handshake/waving, we only need to know the ip:port Just be able to connect/create a tcp server/client Using PHP's socket, we can directly send strings and receive strings. Everything else is language and what the operating system needs to do. , We only need to handle the integrity of the string. For example, we use php as the tcp server After the client connects successfully, it sends a "easyswoole is a very good swoole framework" string
#The server only receives 9 bytes each time, so the first acquisition will only receive the incomplete string of "easyswool", and you need to continue to obtain data The process of a http request is roughly as follows: in the browser
www.easyswoole.com
The browser receives the response data, parses the response text type, parses the data, and disconnects
In the https protocol, there is an additional layer of tls and ssl encryption and decryption protocols in the request and response. The default port has changed from 80 to 443
in phper due to Most of the time, PHP is used for web servers, so the protocol that PHP developers are most exposed to is the HTTP protocol based on the TCP/IP protocol. Among junior PHP programmers, there is actually no detailed understanding of HTTP. protocol, but you can use the browser's f12->network to view the specific request headers of the http protocol and the response headers sent by the server Before there was the WebSocket protocol, in a web page, the only way to implement a chat room was to use ajax to continuously poll and request whether the server had data generated, and such an implementation method would cause a series of problems: If the polling interval is too short, the client and server will continue to perform http tcp handshakes within a period of time. /Waving motion and the transmission of http request headers and response headers consume a lot of server resources. If there are a large number of users, the server will be busy and even down.
#The client can only obtain whether the server has data to return by sending an http request each time, and the timeliness of the data cannot be guaranteed
. The two can directly transmit data to each other. In this WebSocket protocol, it brings two major benefits to us to achieve real-time service:
UDP is the abbreviation of User Datagram Protocol. The Chinese name is User Datagram Protocol. It is a connectionless transport layer protocol in the OSI (Open System Interconnection) reference model, providing a simple and unreliable transaction-oriented Message Transfer Service, IETF RFC 768 is the formal specification for UDP. The protocol number of UDP in IP packets is 17. The full name of UDP protocol is User Datagram Protocol. In the network, it is used to process data packets like the TCP protocol. It is a Connectionless protocol. In the OSI model, the fourth layer - the transport layer, is the upper layer of the IP protocol. UDP has the disadvantage of not providing data packet grouping, assembly, and inability to sort data packets. That is to say, after a message is sent, it is impossible to know whether it has arrived safely and completely. UDP is used to support network applications that need to transmit data between computers. Numerous client/server network applications, including network video conferencing systems, require the use of UDP protocol. The UDP protocol has been used for many years since its inception. Although its initial glory has been overshadowed by some similar protocols, UDP is still a very practical and feasible network transport layer protocol even today. Like the well-known TCP (Transmission Control Protocol) protocol, the UDP protocol is directly on top of the IP (Internet Protocol) protocol. According to the OSI (Open Systems Interconnection) reference model, both UDP and TCP are transport layer protocols. The main function of the UDP protocol is to compress network data traffic into data packets. A typical data packet is a transmission unit of binary data. The first 8 bytes of each data packet are used to contain header information, and the remaining bytes are used to contain specific transmission data. udp and tcp both belong to the transport layer protocol and are located on the top layer of the ip protocol. Their differences are: udp is a connectionless protocol and does not require a tcp handshake
The maximum length udp sends per time is 65535, while tcp can send continuously after the handshake
#The udp protocol uses the check value in the header to ensure data security. The check value is first calculated by a special algorithm at the data sender, and needs to be recalculated after it is passed to the receiver. If a datagram is tampered with by a third party during transmission or damaged due to line noise or other reasons, the checksum calculations of the sender and receiver will not match, so the UDP protocol can detect whether there is an error. This is different from the TCP protocol, which requires a check value.
Udp messages do not have reliability guarantee, sequence guarantee and flow control fields, etc., and their reliability is poor. However, precisely because the UDP protocol has fewer control options, the delay during data transmission is small, and the data transmission efficiency is high. It is suitable for applications that do not require high reliability, or applications that can guarantee reliability, such as DNS, TFTP, and SNMP. wait.
#In an environment where the network quality is very unsatisfactory, UDP protocol packet loss will be more serious. TCP will perform confirmation verification to ensure that the other party receives successfully
udp can broadcast to all hosts in the gateway At the php-fpm software level, multiple processes of fast-cgi will It belongs to multi-process processing, but when the user initiates a request and # is handed over by nginx to php-fpm for processing, at this level, each request actually only Occupy a php fast-cgi process for processing logic. The php process that runs business logic is actually a single process. Similarly, When we run a php file directly, by default only one php process is opened to run php code In the traditional web mode, PHP has always processed business logic in a single process. Only in PHP- In cli mode, it is used to handle asynchronous tasks. When serving as a network server, multi-process processing is possible. Therefore, most phpers are not familiar with the concept of php multi-process
Shared memory communication maps a section of memory that can be accessed by other processes. This shared memory is created by one process, but can be accessed by multiple processes.
Shared memory is the fastest IPC method. It is specially designed for the low operating efficiency of other inter-process communication methods.
#It is often used in conjunction with other communication mechanisms, such as signals, to achieve synchronization and communication between processes.
Socket communication
Third-party communication can also be achieved using file operations, mysql, redis and other methods Coroutine Coroutines are not processes or threads, and their execution process is more similar to subroutines, or function calls without return values. A program can contain multiple coroutines, which can be compared with a process containing multiple threads, so let’s compare coroutines and threads below. We know that multiple threads are relatively independent, have their own context, and switching is controlled by the system; and coroutines are also relatively independent, There are Its own context, but its switching is controlled by itself, and switching from the current coroutine to other coroutines is controlled by the current coroutine. From the code 2 in the above coroutine execution sequence, we can easily It was found that the coroutine is actually just a function running in a process, but this function will be switched to the next execution, so to speak: Coroutines are just a series of task codes running in the process, but these task codes can run cross-wise. Note that coroutines are not multi-tasks in parallel, they are multi-tasks serial. Each process only executes one task at a time Because the coroutine is in the process A string of task codes, so its global variables, static variables and other variables are all shared, including the global buffer of php. Therefore, during development, you need to pay special attention to the global variables in the coroutine , static variables, as long as one coroutine is modified, it will affect all coroutines. When using the ob buffer function to intercept, you must also consider whether it will be contaminated by the output of other coroutines. Use Coroutine execution sequence Code 2 explains that when task1 assigns a value of 1 to $_GET['name'], task2 reads $_GET['name'] and it will also be 1, task2 When $_GET['name'] is assigned a value of 2, task3 reads $_GET['name'] and it will also be 2 ##In the coroutine, special attention must be paid not to share an I/O connection, otherwise data will be Exception. Use the code 2 in coroutine execution sequence to explain that when the task1 and task2 functions share the mysql connection, they both perform queries. At this time, because the coroutines run cross-wise, task1 may obtain the data queried by task1 and task2, or part of the data may be lost and obtained by task2. Due to the cross-running mechanism of coroutines, the I/O connections of each coroutine must be independent, so we need to create a connection in each coroutine, but due to the limited number of mysql and redis connections, And the opening and closing of connections consumes a lot of resources, so we can use the connection pool solution to achieve shared connections (as long as only one coroutine is used for each connection at a time)Module mode
##php- cli mode
##php-fpmPHP-FPM (FastCGI Process Manager) is used to replace most of the additional functions of PHP FastCGI and is very useful for high-load websites.
Its functions include:
Advanced process management functions that support smooth stop/start;
Working principle:The approximate working principle Start for:
php-fpm->Generate n fast-cgi protocol processing processes->Listen to a port to wait for tasksUser requests->Web server receives requests-> The request is forwarded to php-fpm->php-fpm is handed over to an idle process for processing->The process processing is completed->php-fpm returns to the web server->the web server receives data-> Return to user
Network protocolNetwork protocol is a rule and standard established for data exchange in a computer network Or a set of agreements. All communications between computers/mobile phones and other network devices must comply with network protocols.
##ip protocol (network layer)
Scope
interface
operate
ip address
tcp (Transmission Layer)
Three-way handshake
connection succeeded
Wave four times
php in tcp
##http protocol
# #Process Analysis
http
##WebSocket Protocol
Background
Because of this situation, WebSocket appeared. It only requires one http handshake to maintain A long connection allows the server to actively send messages to the client, greatly reducing the consumption of the polling mechanism
##Implementation principle
In the process of implementing websocket connection, it is necessary to send a websocket connection request through the browser, and then the server sends a response. This process is usually called "Handshake"
udp(transport layer)
##udp and tcp
PHP multi-process
The concept of multi-process
As mentioned before, multi-process is mainly used to develop business logic level and process multiple tasks in parallel. What is the development of business logic level? We have mentioned above that php-fpm It is the process manager of fast-cgi. After startup, multiple fast-cgi processes will be started, waiting for task processing
more Process development scenario
##Use pcntl extension
##Process communication
Pipe communication is divided into named pipes, unnamed pipes, etc. You can search for details by yourself

Coroutines and processes
The scope of the coroutine
I in the coroutine /O connection
Recommended Learn:
The above is the detailed content of Organize swoole knowledge points in detail (summary sharing). For more information, please follow other related articles on the PHP Chinese website!

