In nodejs, the full name of jwt is Json web token, which is an open standard based on JSON implemented to transfer statements between network application environments. JWT claims are generally used to pass authenticated user identity information between identity providers and service providers in order to obtain resources from resource servers.

The operating environment of this tutorial: windows7 system, nodejs version 12.19.0, DELL G3 computer.
What is JWT in nodejs
Json web token (JWT) is a type of execution that is used to transfer claims between network application environments Based on the JSON open standard (RFC 7519). The token is designed to be compact and secure, especially suitable for single sign-on (SSO) scenarios on distributed sites.
JWT claims are generally used in The authenticated user identity information is passed between the identity provider and the service provider in order to obtain resources from the resource server. Some additional declaration information necessary for other business logic can also be added. The token can also be used directly for authentication, or Can be encrypted.
JWT, performs identity authentication during HTTP communication.
We know that HTTP communication is stateless, so the client’s request After the server is processed, it cannot be returned to the original client. Therefore, the accessed client needs to be identified. The common method is through the session mechanism: after the client successfully logs in to the server, the server will generate a sessionID and return To the client, the client saves the session ID in the cookie. When making a request again, it carries the session ID in the cookie to the server. The server will cache the session. When the client request comes, the server will know Which user's request is it, and the processing result is returned to the client to complete the communication.
Through the above analysis, we can know that the session has the following problems:
1. The session is saved on the server side , when the number of customer visits increases, the server needs to store a large number of sessions, which is a great test for the server;
2. When the server is a cluster, and the user logs in to one of the servers, the server will be The session is saved in the memory of the server, but when the user accesses other servers, it will be inaccessible. Cache consistency technology is usually used to ensure that it can be shared, or a third-party cache is used to save the session, which is inconvenient.
How is Json Web Token made?
1. The client logs in to the server through user name and password;
2. The server The client's identity is verified;
3. The server generates a Token for the user and returns it to the client;
4. The client saves the Token to the local browser, usually in a cookie ;
5. When the client initiates a request, it needs to carry the Token;
6. After the server receives the request, it first verifies the Token and then returns the data.
Server There is no need to save the Token, only the information carried in the Token needs to be verified;
No matter which server the client accesses in the background, as long as the user information can be verified.
What does Json Web Token look like?
You can tell from the name that it is a json.
is composed of three parts:
Header (header), generally use the default one with few changes:
{
‘typ’:‘JWT’,
‘alg’:‘HS256’
}(playload), everything is Installed here, the default content is:
{
‘iss’:‘签发者’,
‘sub’:‘面向的用户’,
‘aud’:‘接收方’,
‘exp’: 过期时间,
‘iat’: 创建时间,
‘nbf’: 在什么时间之前,该Token不可用,
‘jti’:‘Token唯一标识’
}Users can define it according to their needs. The content transmitted in the Token will generally put the user name, role and other information into the Token.
(signature), after the first two parts are converted into strings, use base64 encoding, and then encrypt to obtain a string.
Token = header (base64) payload (base64) signature;

Implementation process
–> When the user logs in, the server generates a token (encrypted string) and sends it to the front end.
–> The front end saves the token (save it wherever you want) Which)
–> When the front end initiates a data request, it carries the token
–> The server verifies whether the token is legal, continues the operation if it is legal, and terminates the operation if it is illegal
token Usage scenarios: stateless request, maintaining user login status, third-party login (token auth2.0)
Support algorithm
| alg参数值 | 数字签名或MAC算法 |
|---|---|
| HS256 | 使用SHA-256哈希算法的HMAC |
| HS384 | 使用SHA-384哈希算法的HMAC |
| HS512 | 使用SHA-512哈希算法的HMAC |
| RS256 | 使用SHA-256哈希算法的RSASSA-PKCS1-v1_5 |
| RS384 | 使用SHA-384哈希算法的RSASSA-PKCS1-v1_5 |
| RS512 | 使用SHA-512哈希算法的RSASSA-PKCS1-v1_5 |
| PS256 | 使用SHA-256哈希算法的RSASSA-PSS(仅节点^ 6.12.0 OR> = 8.0.0) |
| PS384 | 使用SHA-384哈希算法的RSASSA-PSS(仅节点^ 6.12.0 OR> = 8.0.0) |
| PS512 | 使用SHA-512哈希算法的RSASSA-PSS(仅节点^ 6.12.0 OR> = 8.0.0) |
| ES256 | 使用P-256曲线和SHA-256哈希算法的ECDSA |
| ES384 | 使用P-384曲线和SHA-384哈希算法的ECDSA |
| ES512 | 使用P-521曲线和SHA-512哈希算法的ECDSA |
| 没有 | 不包含数字签名或MAC值 |
开发时使用
安装
npm install jsonwebtoken --save
使用
const jwt = require('jsonwebtoken');//加载包
//产生token默认算法hs256
let token=jwt.sign({user:'123'},'123114655sad46aa');//此方法接收两个参数,第一个是要加密保存的数据(一个对象,不要放隐秘性的数据,如密码),第二个是要加密的私钥(一个字符串,越乱越好)
console.log(token);//返回一个加密字符串
// 服务器签发的token
//eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyIjoiMTIzIiwiaWF0IjoxNTcwMDc2NjU5fQ.3FT6v8zVptdWGBILD1m1CRY6sCP1I3E947krUh_E3
//客户端请求数据的时候验证token
//客户端传递过来的token
let tokens=token;
jwt.verify(tokens,'123114655sad46aa',function (err,data) {
//verify接收两个参数,第一个参数是客户端传递过来的token,第二个参数是加密时的私钥;第三个参数是回调函数
console.log(err);//签名通过返回null,签名不通过返回err(JsonWebTokenError: invalid signature)
console.log(data);// 通过返回解密数据,失败返回unfinished
});更多node相关知识,请访问:nodejs 教程!!
The above is the detailed content of what is nodejs jwt. For more information, please follow other related articles on the PHP Chinese website!
 Vercel是什么?怎么部署Node服务?May 07, 2022 pm 09:34 PM
Vercel是什么?怎么部署Node服务?May 07, 2022 pm 09:34 PMVercel是什么?本篇文章带大家了解一下Vercel,并介绍一下在Vercel中部署 Node 服务的方法,希望对大家有所帮助!
 node.js gm是什么Jul 12, 2022 pm 06:28 PM
node.js gm是什么Jul 12, 2022 pm 06:28 PMgm是基于node.js的图片处理插件,它封装了图片处理工具GraphicsMagick(GM)和ImageMagick(IM),可使用spawn的方式调用。gm插件不是node默认安装的,需执行“npm install gm -S”进行安装才可使用。
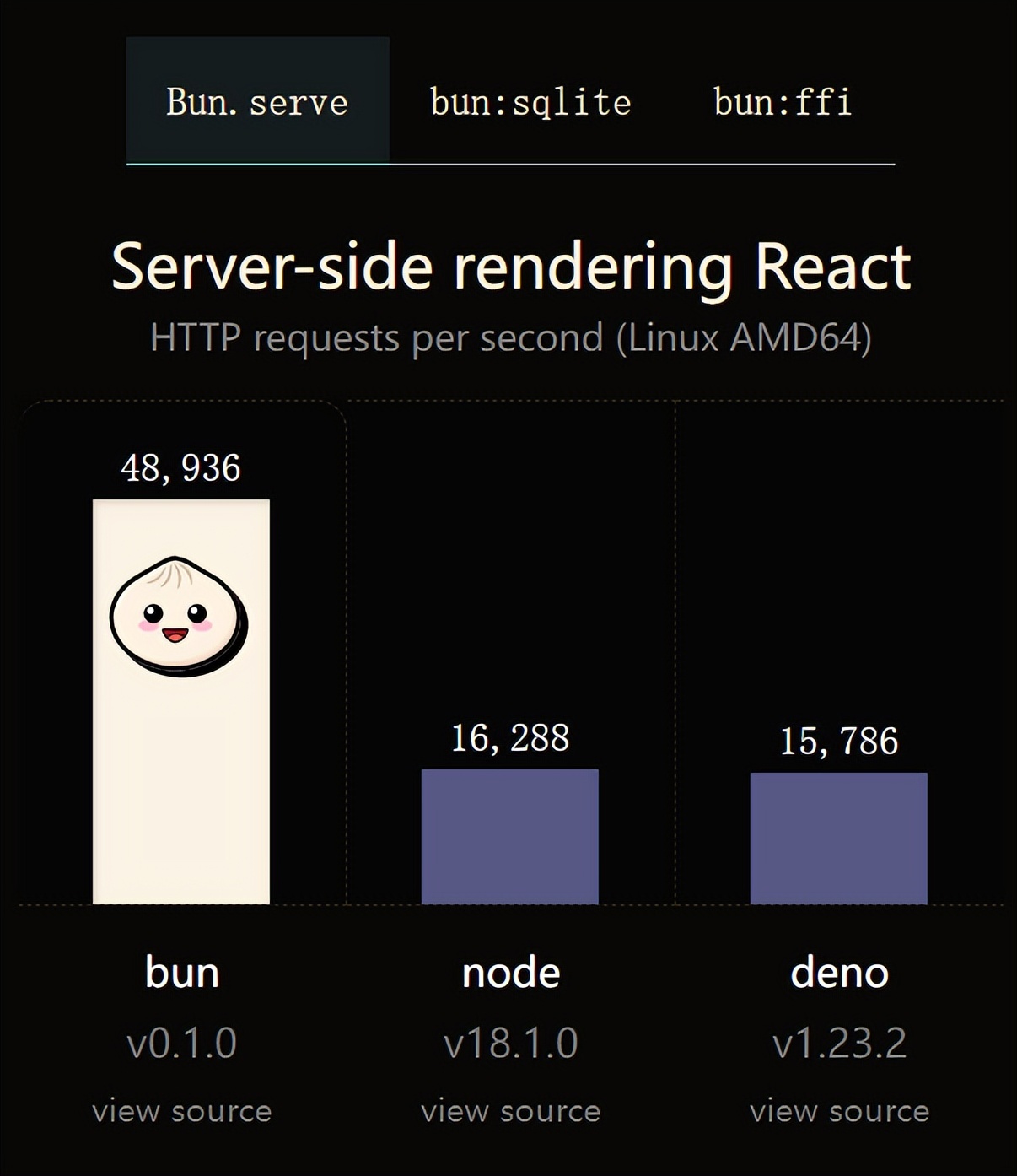 火了!新的JavaScript运行时:Bun,性能完爆NodeJul 15, 2022 pm 02:03 PM
火了!新的JavaScript运行时:Bun,性能完爆NodeJul 15, 2022 pm 02:03 PM今天跟大家介绍一个最新开源的 javaScript 运行时:Bun.js。比 Node.js 快三倍,新 JavaScript 运行时 Bun 火了!
 聊聊Node.js中的多进程和多线程Jul 25, 2022 pm 07:45 PM
聊聊Node.js中的多进程和多线程Jul 25, 2022 pm 07:45 PM大家都知道 Node.js 是单线程的,却不知它也提供了多进(线)程模块来加速处理一些特殊任务,本文便带领大家了解下 Node.js 的多进(线)程,希望对大家有所帮助!
 nodejs中lts是什么意思Jun 29, 2022 pm 03:30 PM
nodejs中lts是什么意思Jun 29, 2022 pm 03:30 PM在nodejs中,lts是长期支持的意思,是“Long Time Support”的缩写;Node有奇数版本和偶数版本两条发布流程线,当一个奇数版本发布后,最近的一个偶数版本会立即进入LTS维护计划,一直持续18个月,在之后会有12个月的延长维护期,lts期间可以支持“bug fix”变更。
 node爬取数据实例:聊聊怎么抓取小说章节May 02, 2022 am 10:00 AM
node爬取数据实例:聊聊怎么抓取小说章节May 02, 2022 am 10:00 AMnode怎么爬取数据?下面本篇文章给大家分享一个node爬虫实例,聊聊利用node抓取小说章节的方法,希望对大家有所帮助!


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Dreamweaver CS6
Visual web development tools

WebStorm Mac version
Useful JavaScript development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software








