Solution to illegal input values in Excel: First find the "Data Verification" button under the "Data" label; then click this option and click Next; finally, after setting up, continue to click the OK button. .

The operating environment of this article: Windows 7 system, Microsoft Office Excel 2010 version, Dell G3 computer.
Solution to illegal input value in excel:
1. First, take a look at the high-definition picture of the crime scene: When we want to enter in cell C1, Once you enter, you will see the above prompt.

2. After canceling, return to the spreadsheet page and select cell C1. At this time, some people may find that there is a small drop-down triangle symbol in the lower right corner of cell C1. , as shown in the figure, actually the problem lies here.

3. When we click the drop-down arrow, we will find that a content list pops up. At this time, we understand that cell C1 is restricted to only input the content in the list. .

4. At this time, you will find the "Data Verification" button under the "Data" label, click this option, and then continue to the next step.
#5. After setting, continue to click the OK button and return to the interface again. At this time, you can enter any content in cell C1.

The above is the detailed content of What to do if the input value in Excel is illegal. For more information, please follow other related articles on the PHP Chinese website!
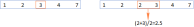 MEDIAN formula in Excel - practical examplesApr 11, 2025 pm 12:08 PM
MEDIAN formula in Excel - practical examplesApr 11, 2025 pm 12:08 PMThis tutorial explains how to calculate the median of numerical data in Excel using the MEDIAN function. The median, a key measure of central tendency, identifies the middle value in a dataset, offering a more robust representation of central tenden
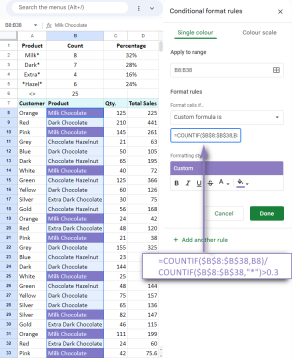 Google Spreadsheet COUNTIF function with formula examplesApr 11, 2025 pm 12:03 PM
Google Spreadsheet COUNTIF function with formula examplesApr 11, 2025 pm 12:03 PMMaster Google Sheets COUNTIF: A Comprehensive Guide This guide explores the versatile COUNTIF function in Google Sheets, demonstrating its applications beyond simple cell counting. We'll cover various scenarios, from exact and partial matches to han
 Excel shared workbook: How to share Excel file for multiple usersApr 11, 2025 am 11:58 AM
Excel shared workbook: How to share Excel file for multiple usersApr 11, 2025 am 11:58 AMThis tutorial provides a comprehensive guide to sharing Excel workbooks, covering various methods, access control, and conflict resolution. Modern Excel versions (2010, 2013, 2016, and later) simplify collaborative editing, eliminating the need to m
 How to convert Excel to JPG - save .xls or .xlsx as image fileApr 11, 2025 am 11:31 AM
How to convert Excel to JPG - save .xls or .xlsx as image fileApr 11, 2025 am 11:31 AMThis tutorial explores various methods for converting .xls files to .jpg images, encompassing both built-in Windows tools and free online converters. Need to create a presentation, share spreadsheet data securely, or design a document? Converting yo
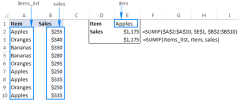 Excel names and named ranges: how to define and use in formulasApr 11, 2025 am 11:13 AM
Excel names and named ranges: how to define and use in formulasApr 11, 2025 am 11:13 AMThis tutorial clarifies the function of Excel names and demonstrates how to define names for cells, ranges, constants, or formulas. It also covers editing, filtering, and deleting defined names. Excel names, while incredibly useful, are often overlo
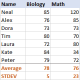 Standard deviation Excel: functions and formula examplesApr 11, 2025 am 11:01 AM
Standard deviation Excel: functions and formula examplesApr 11, 2025 am 11:01 AMThis tutorial clarifies the distinction between standard deviation and standard error of the mean, guiding you on the optimal Excel functions for standard deviation calculations. In descriptive statistics, the mean and standard deviation are intrinsi
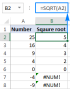 Square root in Excel: SQRT function and other waysApr 11, 2025 am 10:34 AM
Square root in Excel: SQRT function and other waysApr 11, 2025 am 10:34 AMThis Excel tutorial demonstrates how to calculate square roots and nth roots. Finding the square root is a common mathematical operation, and Excel offers several methods. Methods for Calculating Square Roots in Excel: Using the SQRT Function: The
 Google Sheets basics: Learn how to work with Google SpreadsheetsApr 11, 2025 am 10:23 AM
Google Sheets basics: Learn how to work with Google SpreadsheetsApr 11, 2025 am 10:23 AMUnlock the Power of Google Sheets: A Beginner's Guide This tutorial introduces the fundamentals of Google Sheets, a powerful and versatile alternative to MS Excel. Learn how to effortlessly manage spreadsheets, leverage key features, and collaborate


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

Atom editor mac version download
The most popular open source editor

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Zend Studio 13.0.1
Powerful PHP integrated development environment

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function






