Home >Operation and Maintenance >CentOS >About TCP Wrappers access control in CentOS
About TCP Wrappers access control in CentOS
- 藏色散人forward
- 2020-10-16 14:06:182167browse
The following column of centos Getting Started Tutorial will introduce to you about TCP Wrappers access control in CentOS. I hope it will be helpful to friends who need it. Helped!

TCP Wrappers access control in CentOS
1. Overview of TCP Wrappers
TCP Wrappers "wrap" the TCP service program and Listening to the port of the TCP service program adds a security detection process. External connection requests must first pass this layer of security detection and obtain permission before they can access the real service program. As shown in the figure below, TCP Wrappers can also record all attempts to access the Protect the behavior of services and provide administrators with rich security analysis information.
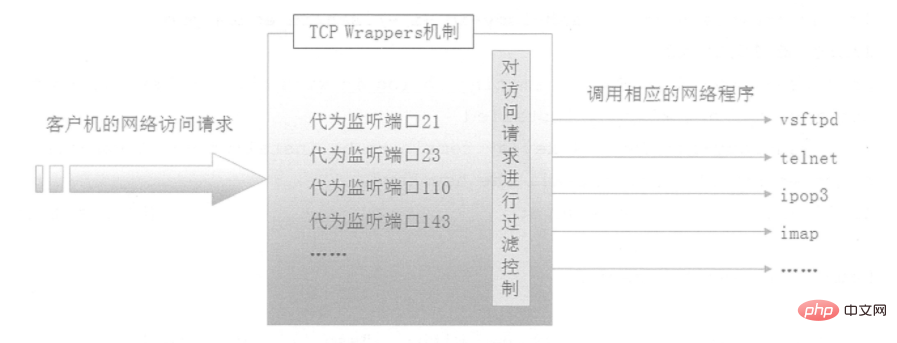
2. Access policy of TCP Wrappers
The protection objects of the TCP Wrappers mechanism are various network service programs, and are accessed based on the client address of the access service control. The two corresponding policy files are /etc/hosts.allow and /etc/hosts.deny, which are used to set allow and deny policies respectively.
1. Policy configuration format
The two policy files have opposite functions, but the format of the configuration record is the same, as shown below:
The service program list and client address list are separated by colons, and multiple items in each list are separated by commas.
1) Service program list
ALL: represents all services;
Single service program: such as "vsftpd";
Composed of multiple service programs List: such as "vsftpd.sshd";
2) Client address list
ALL: represents any client address;
LOCAL: represents the local address;
Single IP address: such as "192.1668.10.1";
Network segment address: such as "192.168.10.0/255.255.255.0";
Domain name starting with "." : For example, "benet.com" matches all hosts in the benet.com domain;
Network addresses ending with ".": For example, "192.168.10." matches the entire 192.168.10.0/24 network segment;
Embedded wildcard characters """?": The former represents any length of characters, and the latter represents only one character. For example, "192.168.10.1" matches all IP addresses starting with 192.168.10.1. Cannot be mixed with patterns starting or ending with ".";
A list of multiple client addresses: such as "192.168.1., 172.16.16., .benet.com";
2. Basic principles of access control
Regarding the access policy of the TCP Wrappers mechanism, follow the following order and principles when applying it: first check the /etc/hosts.allow file, and if a matching policy is found, allow it Access; otherwise, continue to check the /etc/hosts.deny file. If a matching policy is found, access is denied; if no matching policy is found by checking the above two files, access is allowed.
3. TCP Wrappers configuration example
When actually using the TCP Wrappers mechanism, the looser policy can be "allow all, deny some", and the stricter policy is "allow some, deny all ". The former only needs to add the corresponding deny policy in the hosts.deny file; the latter, in addition to adding the allow policy in host.allow, also needs to set the "ALL: ALL" deny policy in the hosts.deny file. .
The example is as follows:
Now we only want to access the sshd service from the host with the IP address 192.168.10.1 or the host located in the 172.16.16 network segment. Other addresses are denied. You can perform the following operations:
[root@CentOS01 ~]# vim /etc/hosts.allow sshd:192.168.10.1 172.16.16.* [root@centos01 ~]# vim /etc/hosts.deny sshd:ALL
The above is the detailed content of About TCP Wrappers access control in CentOS. For more information, please follow other related articles on the PHP Chinese website!

