Home >Operation and Maintenance >Safety >AWS S3 bucket misconfiguration - millions of personal information exposed
AWS S3 bucket misconfiguration - millions of personal information exposed
- 王林forward
- 2019-12-16 17:56:343412browse

1. The misconfiguration of AWS S3 bucket caused millions of personal information (PII) to be obtained
At first, when I tested the target website, I did not find it For any high-risk vulnerabilities, after nearly an hour of detection and analysis, I found that there are some insignificant IDOR and XSS vulnerabilities, but no high-risk vulnerabilities. Just when I was about to give up, I discovered that the target website used the Amazon Cloudfront service to store public images, and its storage URL link looked like the following:
https://d3ez8in977xyz.cloudfront.net/avatars /009afs8253c47248886d8ba021fd411f.jpg
At first, I thought this was just an open online data service. I casually visited the https://d3ez8in977xyz.cloudfront.net website and found that it Some public picture files were stored, but..., I was surprised to find that in addition to these picture files, some sensitive personal data information was also stored, such as: voice chat content, audio call content, text message content and other users Privacy document.
What’s terrible is that the contents stored in these sensitive files are almost all conversational information between patients and doctors.
Since different domain names of the company correspond to different AWS buckets, I turned to discover the public image storage of other domain names. Sure enough, each of its corresponding buckets stored thousands of personal data information. , I didn’t do any specific calculations at the time, but later I learned that the company’s customers numbered in the millions. The following is an illustration containing personal information:
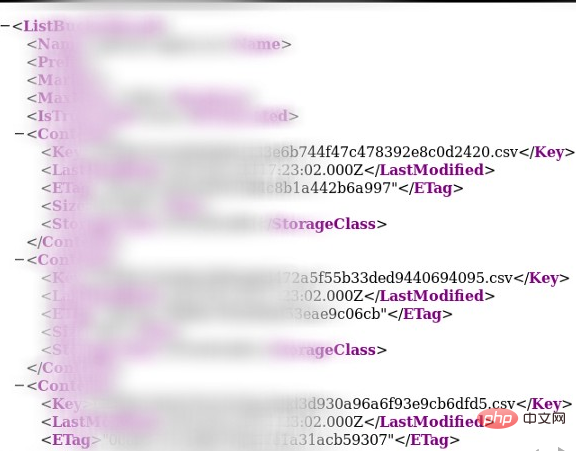
After I reported it to the target company in time, they promptly repaired it within an hour and rewarded me Got me a reward of $2500 and $500.
2. The administrator account with login access led to the leakage of business partner company details
This is a multinational company's website, and there is a stored XSS in it, so I obtained the website's Administrator account token and in-depth testing obtained detailed information of the company's partner companies.
I discovered a stored XSS vulnerability in the data format page of the company's website. The formatted data was stored in the local administrator account, so I used XSSHunter's built-in payload to trigger a rebound. After the operator triggered the Payload, he would send me the data I wanted:
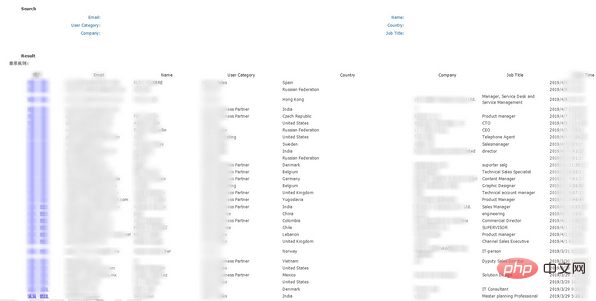
After reporting the vulnerability, I received a $1,250 reward.
Recommended related articles and tutorials: Web server security
The above is the detailed content of AWS S3 bucket misconfiguration - millions of personal information exposed. For more information, please follow other related articles on the PHP Chinese website!
Related articles
See more- Win2008 R2 WEB Server Security Settings Guide: Detailed introduction to disabling unnecessary services and closing ports
- Win2008 R2 WEB Server Security Settings Guide - Folder Permission Setting Tips
- Detailed explanation of group policy and user settings in win2008 R2 WEB server security settings guide (picture)
- Win2008 R2 WEB Server Security Settings Guide - Detailed explanation on how to modify port 3389 and update patches

