Warning! ! ! PHP remote code execution vulnerability
- 爱喝马黛茶的安东尼forward
- 2019-10-24 10:38:584393browse

1. Foreword
On October 22, 2019, a remote code execution vulnerability in PHP was disclosed on github.
Douxiang Intelligent Security CRS product has fully supported the detection and verification of this vulnerability. Users can directly log in to www.riskivy.com for verification.
2. Vulnerability Introduction
This vulnerability is caused by incorrect Nginx php-fpm configuration causing the server to be processed There is an incorrect parsing method that may lead to arbitrary code execution.
3. Vulnerability hazards
After analysis by Douxiang Security Emergency Response Team, attackers can execute remote code on misconfigured PHP servers through carefully constructed request packets. implement.
Related recommendations: "php Getting Started Tutorial"
4. Scope of Influence
Product
PHP
Version
5.6-7.x
Component
PHP
5. Vulnerability Recurrence
Confirmed by the Douxiang Security Emergency Response Team, the vulnerability does exist. Crash for version 5.6 or above, RCE for version 7.X
Write logs through request packets
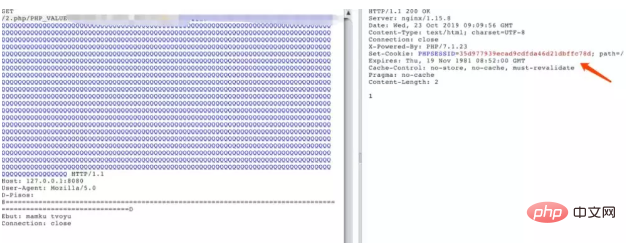
View phpinfo and you will find that
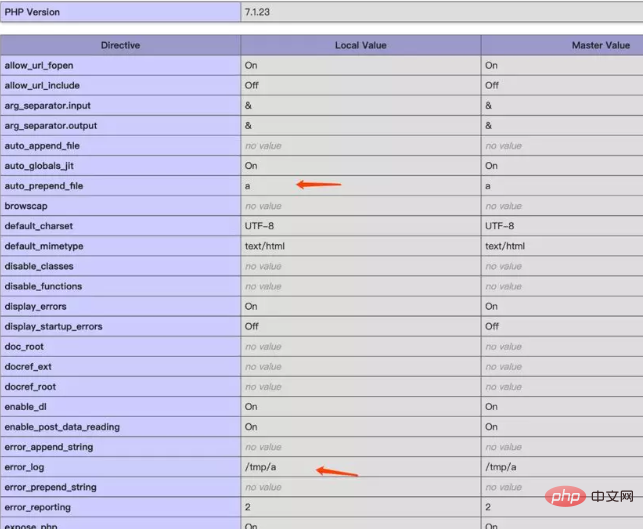
View /tmp/a
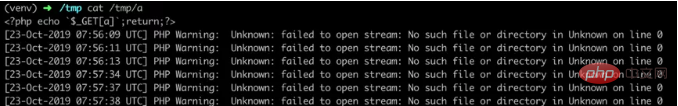
Remote code execution can be achieved by accessing 2.php

6. Repair plan
1. Please combine the actual business scenario and delete the following configuration in the Nginx configuration file without affecting normal business:
fastcgi_split_path_info ^(.+?\.php)(/.*)$; fastcgi_param PATH_INFO $fastcgi_path_info;
7. Reference
https://github.com/neex/phuip-fpizdam

