Since the ports on your computer are where information is sent and received, port scanning is similar to knocking on the door to see if anyone is home. Now let’s take you through port scanning, hoping it will be helpful to you.

Port scanning
Port scanning is used to identify open ports and services available on network hosts The name of a technology that checks all ports on an IP address to see if they are open or closed.
Security technicians sometimes use it to audit computers for vulnerabilities, but hackers also use it to attack their victims. It is considered an open hacking technique where hackers perform port scanning techniques to find vulnerabilities within specific computer ports. To an intruder, these weaknesses represent opportunities for attack.
There are 65,535 ports in each IP address, and hackers may scan each port to find any unsecured ports.
How does port scanning work?
Port scanning is very simple: send a request to connect to the target computer, and then keep track of which ports appear to be open or which respond to the request.

There are three possible responses:
1. Open, Accept: The computer responds and asks if there is anything it can do for you. things.
2. Closed, not listening: The computer responds "This port is currently in use and unavailable at this time."
3. Filter, discard, block: The computer doesn't even bother to respond, it doesn't have time for pranks.
Types of port scans
Ping scan:
The simplest port Scanning technology used to scan entire network blocks or individual targets to identify which computers on the network are active. It sends an ICMP echo request to the target, and if the response is an ICMP reply, it means the target is active.
vanilla scan:
The most basic type of scan, the scanner will try to connect to all 65,535 ports. It is a full connection scan, which sends the SYN flag (requesting a connection), and after receiving the SYN-ACK (connection confirmation) response, sends back the ACK flag. Full connection scans are accurate but very easy to detect because the firewall always logs full connections.
SYN Scan: Also known as Half-Open Scan (TCP Half-Open)
This is a quick and sneaky scan that attempts to find potentially open scans on the target computer port. This scan is fast because it never completes the full TCP 3-way handshake. The scanner sends a SYN message and only records the SYN-ACK response. The scanner does not complete the connection by sending a final ACK: it leaves the target dangling.
strobe scan: A more focused scan that only looks for known developed services
UDP: The scanner looks for open UDP Port
FTP Bounce Scanning: The scanner masquerades the scan source through an FTP server, allowing packets to be bounced through the FTP server to masquerade the sender's location.
Stealth Scan: Used to collect information without being logged by the target system, the scanner prevents the scanned computer from logging port scan activity.
Summary: Port scanning is the first step in any vulnerability analysis or penetration testing; knowing which ports are open is the beginning of being able to actively communicate with the target. Port scanning itself does not constitute a crime. We can protect port scanning through the use of firewalls.
This article ends here. I hope it will be helpful to everyone's study. For more exciting content, you can pay attention to the relevant tutorial columns of the PHP Chinese website! ! !
The above is the detailed content of What does port scanning mean?. For more information, please follow other related articles on the PHP Chinese website!
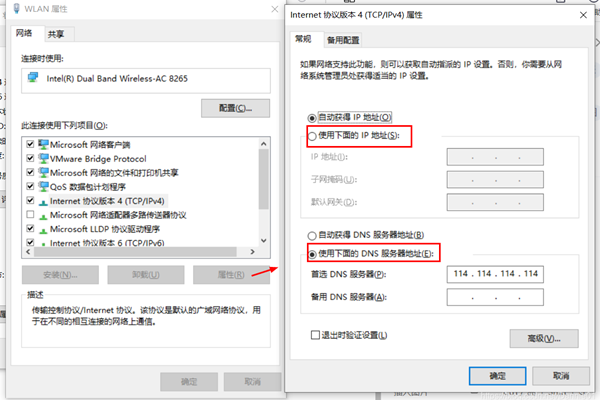 win10如何重置tcp/ip协议?windows10重置tcp/ip协议栈的方法Mar 16, 2024 am 11:07 AM
win10如何重置tcp/ip协议?windows10重置tcp/ip协议栈的方法Mar 16, 2024 am 11:07 AMwin10如何重置tcp/ip协议?其实方法很简单的,用户们可以直接的进入到命令提示符,然后按下ctrl+shift+enter的组合键来进行操作就可以了或者是直接的执行重置命令来进行设置,下面就让本站来为用户们来仔细的介绍一下windows10重置tcp/ip协议栈的方法吧。windows10重置tcp/ip协议栈的方法一、管理员权限1、我们使用快捷键win+R直接打开运行窗口,然后输入cmd并按住ctrl+shift+enter的组合键。2、或者我们可以直接在开始菜单中搜索命令提示符,右键点
 Java API 开发中使用 Netty4 进行 TCP 通信Jun 17, 2023 pm 11:18 PM
Java API 开发中使用 Netty4 进行 TCP 通信Jun 17, 2023 pm 11:18 PMTCP是计算机网络通信协议的一种,是一种面向连接的传输协议。在Java应用开发中,TCP通信被广泛应用于各种场景,比如客户端和服务器之间的数据传输、音视频实时传输等等。Netty4是一个高性能、高可扩展性、高性能的网络编程框架,能够优化服务器和客户端之间的数据交换过程,使其更加高效可靠。使用Netty4进行TCP通信的具体实现步骤如下:引入
 python中怎么使用TCP实现对话客户端和服务器May 17, 2023 pm 03:40 PM
python中怎么使用TCP实现对话客户端和服务器May 17, 2023 pm 03:40 PMTCP客户端一个使用TCP协议实现可连续对话的客户端示例代码:importsocket#客户端配置HOST='localhost'PORT=12345#创建TCP套接字并连接服务器client_socket=socket.socket(socket.AF_INET,socket.SOCK_STREAM)client_socket.connect((HOST,PORT))whileTrue:#获取用户输入message=input("请输入要发送的消息:&
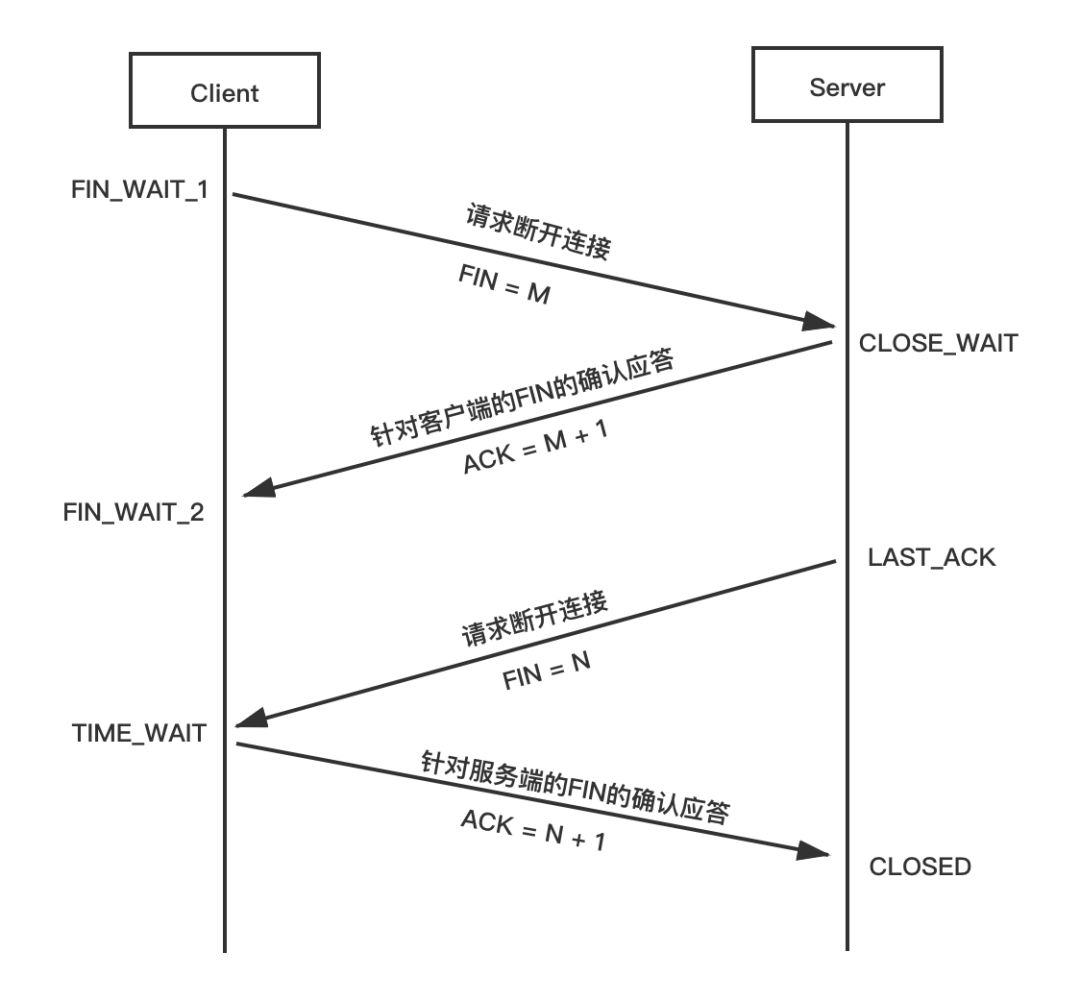
 活久见!TCP两次挥手,你见过吗?那四次握手呢?Jul 24, 2023 pm 05:18 PM
活久见!TCP两次挥手,你见过吗?那四次握手呢?Jul 24, 2023 pm 05:18 PM那这里面提到的"面向连接",意味着需要 建立连接,使用连接,释放连接。建立连接是指我们熟知的TCP三次握手。而使用连接,则是通过一发送、一确认的形式,进行数据传输。还有就是释放连接,也就是我们常见的TCP四次挥手。
 如何在Java中使用单个TCP连接发送多个文件?Apr 27, 2023 am 08:49 AM
如何在Java中使用单个TCP连接发送多个文件?Apr 27, 2023 am 08:49 AM使用一个TCP连接发送多个文件为什么会有这篇博客?最近在看一些相关方面的东西,简单的使用一下Socket进行编程是没有的问题的,但是这样只是建立了一些基本概念。对于真正的问题,还是无能为力。当我需要进行文件的传输时,我发现我好像只是发送过去了数据(二进制数据),但是关于文件的一些信息却丢失了(文件的扩展名)。而且每次我只能使用一个Socket发送一个文件,没有办法做到连续发送文件(因为我是依靠关闭流来完成发送文件的,也就是说我其实是不知道文件的长度,所以只能以一个Socket连接代表一个文件)。
 Linux SIGPIPE信号Feb 19, 2024 pm 04:00 PM
Linux SIGPIPE信号Feb 19, 2024 pm 04:00 PM在TCP通信双方中,为了描述方便,以下将通信双方用A和B代替。根据TCP协议规定,如果A关闭连接后B继续发送数据,B会收到A的RST响应。若B继续发送数据,系统会发出SIGPIPE信号告知连接已断开,停止发送。系统对SIGPIPE信号的默认处理行为是让B进程退出。操作系统对SIGPIPE信号的这种默认处理行为非常不友好,让我们来分析一下。TCP通信是全双工信道,相当于两条单工信道,连接两端各负责一条。当对端“关闭”时,虽然本意是关闭整个两条信道,但本端只是收到FIN包。根据TCP协议的规定,当一
 tcp和ip的区别是什么Sep 04, 2023 pm 02:19 PM
tcp和ip的区别是什么Sep 04, 2023 pm 02:19 PMTCP和IP是互联网中两个不同的协议:1、TCP是一种运输层协议,而IP是一种网络层协议;2、TCP提供了数据包的分段、排序、确认和重传等功能,而IP协议负责为数据包提供源和目标地址;3、TCP是面向连接的协议,而IP协议是无连接的;4、TCP还提供流量控制和拥塞控制。
 如何使用Nginx防范端口扫描攻击Jun 10, 2023 pm 12:18 PM
如何使用Nginx防范端口扫描攻击Jun 10, 2023 pm 12:18 PM在当前互联网环境下,安全性一直是网络管理员和网站开发者最为关注的问题之一。其中,端口扫描攻击是一种常见的安全漏洞,攻击者会对网站开放的端口进行扫描,以识别潜在的漏洞。为了避免端口扫描攻击带来的安全威胁,越来越多的企业和网站选择使用Nginx作为Web服务器。本文将介绍如何使用Nginx防范端口扫描攻击。一、什么是端口扫描攻击?端口扫描是指攻击者使用TCP或U


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Chinese version
Chinese version, very easy to use

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Mac version
God-level code editing software (SublimeText3)






