Home >Operation and Maintenance >Linux Operation and Maintenance >How to use access control RAM to authorize access to ECS instances and API authentication rules
How to use access control RAM to authorize access to ECS instances and API authentication rules
- 坏嘻嘻Original
- 2018-09-19 16:16:362280browse
The content of this article is about how to use access control RAM to authorize and access ECS instances. It has certain reference value. Friends in need can refer to it. I hope it will be helpful to you.
Authentication Rules
By default, you can use the ECS API to fully operate the ECS resources you create. However, when the sub-account is first created, it does not have permission to operate the resources of the main account, or when accessing ECS from other services, operation authorization issues will be involved. Therefore, before you operate certain ECS resources with permission control, the resource owner needs to authorize the target resource and target API behavior permissions. If you do not need cross-account authorization and access to ECS instance resources, you can skip this chapter.
Before learning how to use access control RAM to authorize and access ECS instances, make sure you have read the RAM product documentation and API documentation.
When other accounts access the ECS resources of the main account through the ECS API, we first initiate a permission check to RAM to ensure that the resource owner has indeed granted the relevant permissions of the relevant resources to the caller. Different ECS APIs determine which resource permissions need to be checked based on the resources involved and the API semantics. Specifically, the authentication rules for some APIs are as shown in the table below.
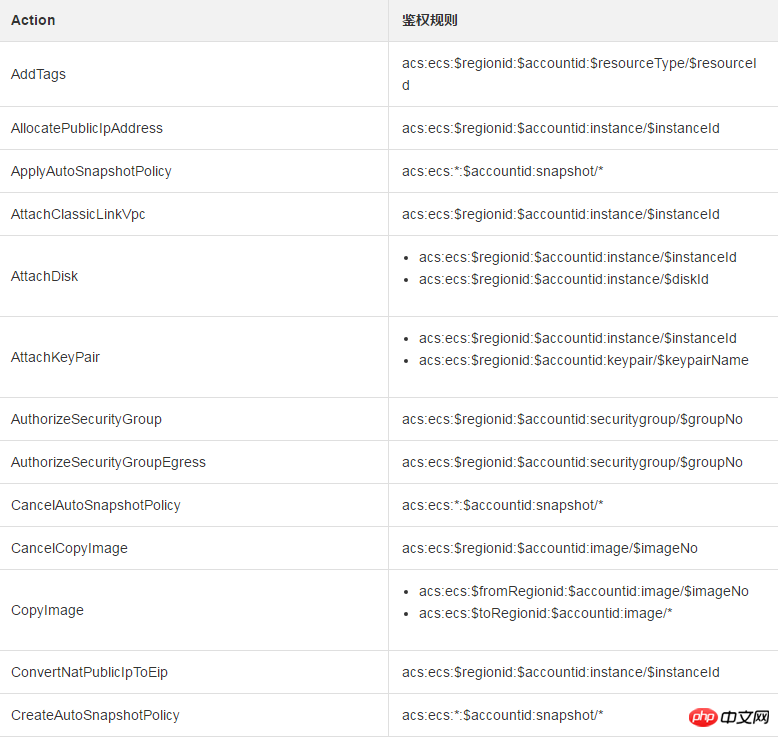
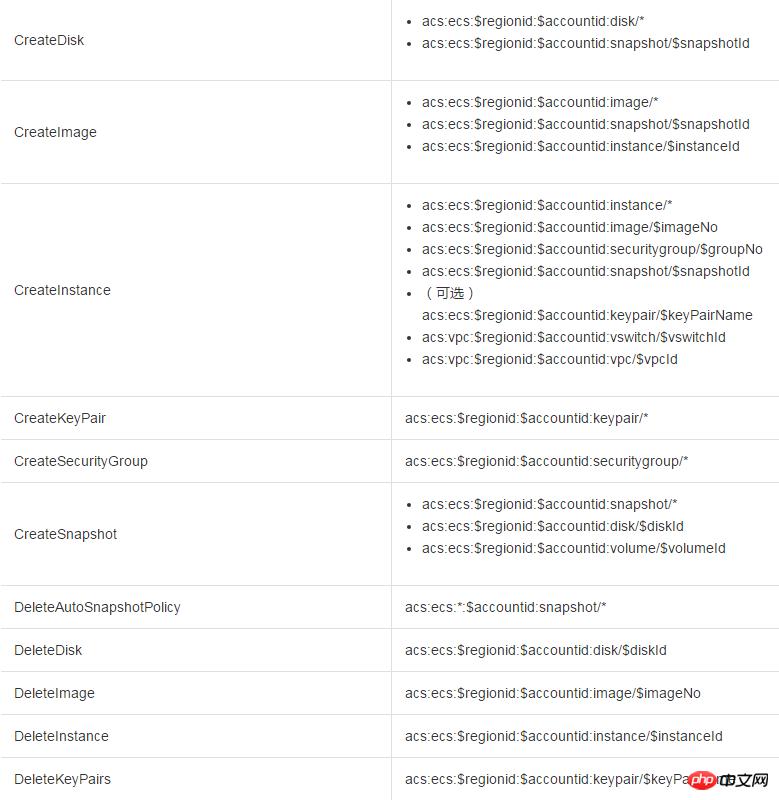
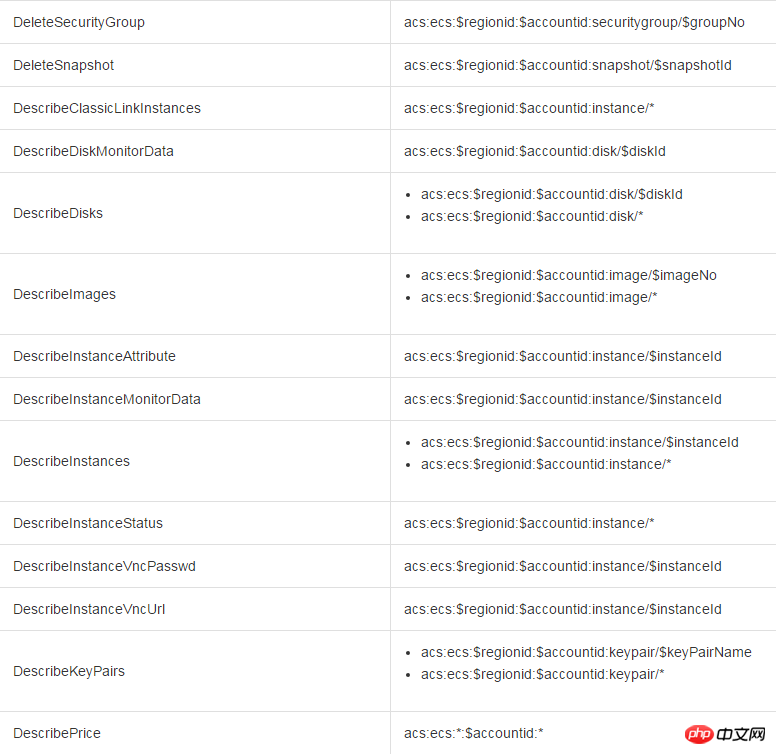
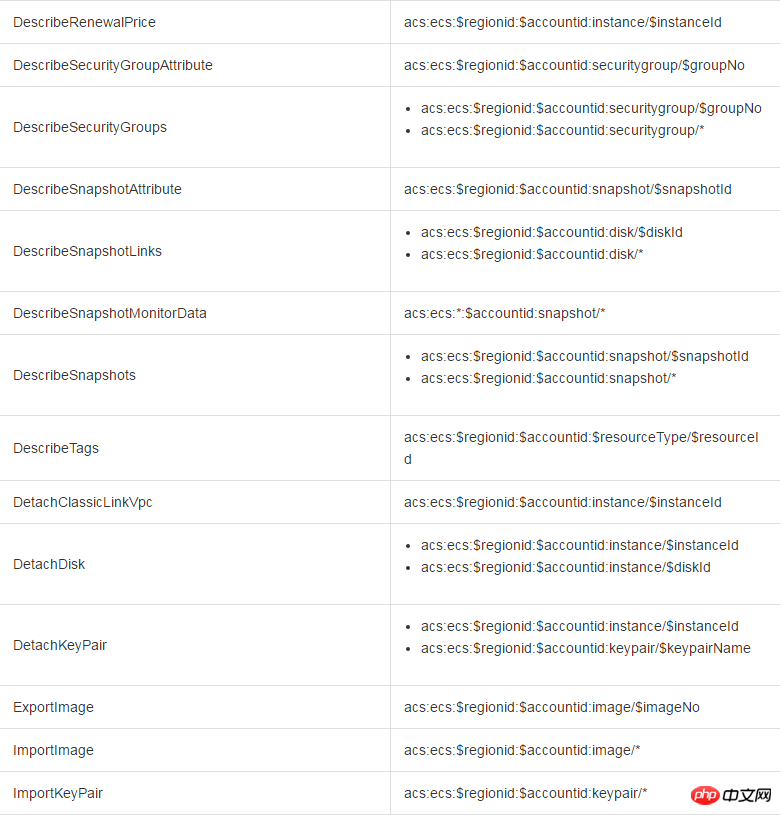
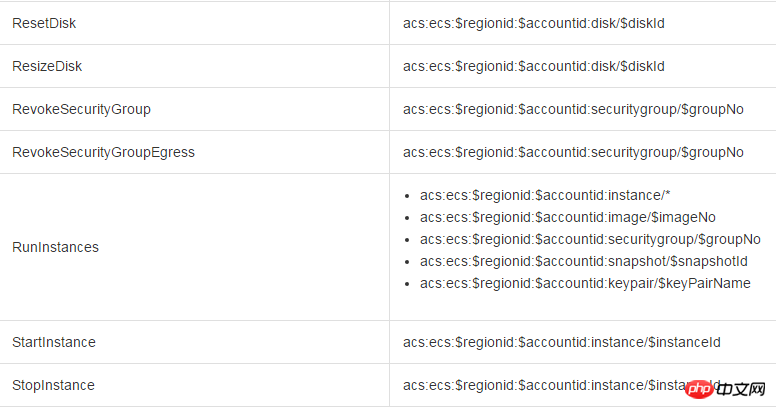 ##
##
The above is the detailed content of How to use access control RAM to authorize access to ECS instances and API authentication rules. For more information, please follow other related articles on the PHP Chinese website!

