
During the PHP programmer interview, we may also encounter interview questions about redis. This article mainly shares with you the most common interview questions in Redis, hoping to help everyone.
Special topic recommendation: 2020 redis interview questions (latest)
2. Characteristics of Reids
Redis is essentially a Key-Value type in-memory database, much like memcached. The entire database is loaded into the memory for operation, and the database data is flushed to the hard disk for storage through asynchronous operations on a regular basis. Because it is a pure memory operation, Redis has excellent performance and can handle more than 100,000 read and write operations per second. It is the fastest Key-Value DB with known performance.
The excellence of Redis is not only its performance. The biggest charm of Redis is that it supports saving a variety of data structures. In addition, the maximum limit of a single value is 1GB. Unlike memcached, which can only save 1MB of data, Redis can It is used to implement many useful functions, such as using its List to make a FIFO doubly linked list, implementing a lightweight high-performance message queue service, and using its Set to make a high-performance tag system, etc. In addition, Redis can also set the expire time for the stored Key-Value, so it can also be used as an enhanced version of memcached.
The main disadvantage of Redis is that the database capacity is limited by physical memory and cannot be used for high-performance reading and writing of massive data. Therefore, the scenarios suitable for Redis are mainly limited to high-performance operations and calculations of smaller amounts of data.
3. What are the benefits of using redis?
(1) It is fast because the data is stored in memory, similar to HashMap. The advantage of HashMap is that the time complexity of search and operation is O(1)
(2) It supports rich data types, Supports string, list, set, sorted set, hash (3) Supports transactions, operations are atomic. The so-called atomicity means that all changes to the data are either executed or not executed
(4) Rich Features: Can be used for caching, messages, set expiration time by key, and will be automatically deleted after expiration
(1) All values in memcached are simple strings. As its replacement, redis supports richer data types. 3) redis can persist its data
5. What are the differences between Memcache and Redis?
1). Storage method Memecache stores all data in the memory. It will hang up after a power outage. The data cannot exceed the memory size. Part of Redis is stored on the hard disk, which ensures data persistence. 2) Data support types Memcache supports relatively simple data types. Redis has complex data types.
3). The underlying models used are different. The underlying implementation methods and the application protocols for communication with the client are different. Redis directly built its own VM mechanism, because if the general system calls system functions, it will waste a certain amount of time to move and request.
6.Redis common performance problems and solutions:
1).Master writes memory snapshots, and the save command schedules the rdbSave function, which will block the work of the main thread. When the snapshot is relatively large, it will have a great impact on performance, and the service will be suspended intermittently, so it is best not for the Master to write memory snapshots.
2) Master AOF persistence. If the AOF file is not rewritten, this persistence method will have the smallest impact on performance, but the AOF file will continue to grow. If the AOF file is too large, it will affect the recovery of the Master restart. speed. It is best not to do any persistence work on the Master, including memory snapshots and AOF log files. In particular, do not enable memory snapshots for persistence. If the data is critical, a Slave should enable AOF backup data. The strategy is to Synchronize once every second. 3).Master calls BGREWRITEAOF to rewrite the AOF file. AOF will occupy a large amount of CPU and memory resources during rewriting, resulting in excessive service load and brief service suspension. 4). Redis master-slave replication performance issues, for the speed of master-slave replication and the stability of the connection, it is best for the Slave and the Master to be in the same LAN7. There are 20 million data in mySQL, but only 20 million data are stored in redis. How to ensure that the data in redis are hot data
Related knowledge: When the size of the redis memory data set increases to a certain size, the data elimination strategy (recycling strategy) will be implemented. redis provides 6 data elimination strategies:
volatile-lru: Select the least recently used data from the data set (server.db[i].expires) with an expiration time set for elimination.
volatile-ttl: Select the data that will expire from the data set (server.db[i].expires) that has set expiration time to eliminate
-
volatile-random: Randomly select data for elimination from the data set (server.db[i].expires) with expiration time set
allkeys-lru: From the data set (server.db[i].expires) Select the least recently used data from server.db[i].dict) to eliminate
allkeys-random: Select data arbitrarily from the data set (server.db[i].dict) Eliminate
no-enviction (eviction): prohibit eviction data
8. Please use Redis and any language to implement a malicious login Protected code, limits each user ID to a maximum of 5 logins within 1 hour. For specific login functions or functions, just use an empty function and there is no need to write them out in detail.
Use a list to implement: Each element in the list represents the login time. As long as the difference between the last 5th login time and the current time is not more than 1 hour, login is prohibited. The code written in Python is as follows:
#!/usr/bin/env python3 import redis import sys import time r = redis.StrictRedis(host=’127.0.0.1′, port=6379, db=0) try: id = sys.argv[1] except: print(‘input argument error’) sys.exit(0) if r.llen(id) >= 5 and time.time() – float(r.lindex(id, 4)) <p><strong>9. Why does redis need to put all data into memory? </strong><br></p><p style="text-align: left;"> In order to achieve the fastest reading and writing speed, Redis reads all data into memory and uses asynchronous way to write data to disk. So redis has the characteristics of fast speed and data persistence. If the data is not placed in memory, disk I/O speed will seriously affect the performance of redis. Today, when memory is getting cheaper and cheaper, redis will become more and more popular. </p><p style="text-align: left;"> If the maximum memory used is set, new values cannot be inserted after the number of data records reaches the memory limit. </p><p style="text-align: left;"><strong>10.Redis is a single process and single thread</strong></p><p style="text-align: left;"> Redis uses queue technology to turn concurrent access into serial access, eliminating the overhead of traditional database serial control</p><p style="text-align: left;"><strong>11. How to solve the concurrency competition problem of redis?</strong></p><p style="text-align: left;"> Redis is a single-process single-thread mode and uses queue mode to turn concurrent access into serial access. Redis itself has no concept of locks. Redis does not compete for multiple client connections. However, when the Jedis client concurrently accesses Redis, problems such as connection timeout, data conversion errors, blocking, and client closing the connection may occur. These problems They are all </p><p style="text-align: left;"> caused by client connection confusion. There are 2 solutions to this: </p><p style="text-align: left;"> 1. From the client perspective, in order to ensure that each client communicates with Redis in a normal and orderly manner, the connections are pooled, and at the same time, the client reads and writes Redis operations. The internal lock is synchronized. </p><p style="text-align: left;"> 2. From the server perspective, use setnx to implement locking. <br> Note: For the first type, the application needs to handle the synchronization of resources by itself. The methods that can be used are relatively common, you can use synchronized or lock; the second type requires the use of the setnx command of Redis, but you need to pay attention to some issues. . </p><p style="text-align: left;"><strong>12. Understanding of redis things CAS (check-and-set operation to achieve optimistic locking)?</strong></p><p style="text-align: left;"> Like many other databases, Redis also provides a NoSQL database transaction mechanism. In Redis, the four commands MULTI/EXEC/DISCARD/WATCH are the cornerstone of our transaction implementation. I believe that this concept is not unfamiliar to developers who have experience in relational database development. Even so, we will briefly list the implementation characteristics of </p><p style="text-align: left;"> transactions in Redis:</p> 1). All commands in the transaction will be executed serially and sequentially. During the execution of the transaction, Redis will no longer provide any services for other client requests, thus ensuring that all commands in the transaction are executed atomically. implement. <p style="text-align: left;"> 2). Compared with transactions in relational databases, if a command fails to execute in a Redis transaction, subsequent commands will continue to be executed. <br> 3). We can start a transaction through the MULTI command, which people with experience in relational database development can understand as the "BEGIN TRANSACTION" statement. The commands executed after this statement will be regarded as operations within the transaction. Finally, we can commit/rollback all operations within the transaction by executing the EXEC/DISCARD command. These two<br></p><p style="text-align: left;"> A Redis command can be regarded as equivalent to the COMMIT/ROLLBACK statement in a relational database. <br> 4). Before the transaction is started, if there is a communication failure between the client and the server and the network is disconnected, all subsequent statements to be executed will not be executed by the server. However, if the network interruption event occurs after the client executes the EXEC command, then all commands in the transaction will be executed by the server. <br> 5). When using the Append-Only mode, Redis will write all write operations in the transaction to the disk in this call by calling the system function write. However, if a system crash occurs during the writing process, such as a downtime caused by a power failure, then only part of the data may be written to the disk at this time, while other part of the data has been lost. </p><p style="text-align: left;"> The Redis server will perform a series of necessary consistency checks when restarting. Once a similar problem is found, it will exit immediately and give a corresponding error prompt. At this time, we must make full use of the redis-check-aof tool provided in the Redis toolkit. This tool can help us locate data inconsistency errors and return part of the data that has been written.</p><p style="text-align: left;"> roll. After the repair, we can restart the Redis server again. </p><p style="text-align: left;"><strong>13.WATCH command and CAS-based optimistic locking: </strong></p><p style="text-align: left;"> In Redis transactions, the WATCH command can be used to provide CAS (check-and-set) function. Assume that we monitor multiple Keys through the WATCH command before the transaction is executed. If the value of any Key changes after WATCH, the transaction executed by the EXEC command will be abandoned and a Null multi-bulk response will be returned to notify the caller of the transaction. </p><p style="text-align: left;"> Execution failed. For example, we assume again that the incr command is not provided in Redis to complete the atomic increment of key values. If we want to implement this function, we can only write the corresponding code ourselves. The pseudo code is as follows: <br> val = GET mykey<br> val = val + 1<br> SET mykey $val<br> The above code can only guarantee that the execution result is correct in the case of a single connection, because if If multiple clients are executing this code at the same time, an error scenario that often occurs in multi-threaded programs will occur - a race condition. For example, both clients A and B read the original value of mykey at the same time. Assume that the value is 10. After that, both clients add one to the value and set it back to the Redis server. This will cause the value of mykey to be lost. The result is 11, not 12 as we thought. In order to solve similar problems, we need to use the help of the WATCH command, see the following code: <br> WATCH mykey<br> val = GET mykey<br> val = val + 1<br> MULTI<br> SET mykey $val<br> EXEC<br> Different from the previous code, the new code first monitors the key through the WATCH command before obtaining the value of mykey, and then surrounds the set command in the transaction, thus effectively ensuring that each connection is Before executing EXEC, if the value of mykey obtained by the current connection is modified by another connected client, the EXEC command of the current connection will fail to execute. In this way, the caller can know whether val has been successfully reset after judging the return value. </p><p style="text-align: left;"><strong>14. Several ways of redis persistence</strong></p><p style="text-align: left;">1. Snapshots<br> By default, Redis stores data snapshots on disk In the binary file, the file name is dump.rdb. You can configure the persistence strategy of Redis. For example, if there are more than M updates in the data set every N seconds, the data will be written to the disk; or you can manually call the command SAVE or BGSAVE. <br> working principle<br> . Redis forks.<br> . The child process starts writing data to the temporary RDB file. <br> . When the child process finishes writing the RDB file, replace the old file with the new file. <br> . This method allows Redis to use copy-on-write technology. <br>2. AOF<br> The snapshot mode is not very robust. When the system stops or Redis is accidentally killed, the last data written to Redis will be lost. This may not be a big problem for some applications, but for applications that require high reliability, <br> Redis is not a suitable choice. <br>Append-only file mode is another option. <br> You can turn on the AOF mode in the configuration file <br>3. Virtual memory mode <br> When your key is small and the value is large, the effect of using VM will be better because the memory saved in this way is relatively large. .<br> When your key is not small, you can consider using some extraordinary methods to turn a large key into a large value. For example, you can consider combining key and value into a new value.<br> vm-max The -threads parameter can set the number of threads that access the swap file. It is best not to exceed the number of cores of the machine. If it is set to 0, then all operations on the swap file will be serial. This may cause a long delay. , but there is a good guarantee for data integrity.</p><p style="text-align: left;"> When I tested it myself, I found that the performance of using virtual memory is also good. If the amount of data is large, you can consider distributed or other databases</p><p style="text-align: left;"><strong>15.redis’s cache invalidation strategy and primary key invalidation mechanism</strong></p><p style="text-align: left;"> As a cache system, it must be regularly cleaned and invalidated Data requires a primary key invalidation and elimination strategy.<br>In Redis, keys with a lifetime are called volatile. When creating a cache, set the lifetime for a given key. When the key expires (the lifetime is 0), it may be deleted. <br> 1. Some operations that affect the survival time <br> The survival time can be removed by using the DEL command to delete the entire key, or the original data can be overwritten by the SET and GETSET commands, that is, modify the value and value corresponding to the key. After overwriting with the same key and value, the survival time of the current data is different. <br>For example, executing the INCR command on a key, executing the LPUSH command on a list, or executing the HSET command on a hash table, these operations will not modify the survival time of the key itself. On the other hand, if you use RENAME to rename a key, the survival time of the renamed key will be the same as before the rename. <br> Another possibility of the RENAME command is to try to rename a key with a survival time to another_key with a survival time. At this time, the old another_key (and its survival time) will be deleted, and then the old key It will be renamed to another_key. Therefore, the survival time of the new another_key is the same as the original key. Use the PERSIST command to remove the key's lifetime without deleting the key, making the key a persistent key again. <br> 2. How to update the survival time<br> You can execute the EXPIRE command on a key that already has a survival time, and the newly specified survival time will replace the old survival time. The accuracy of the expiration time has been controlled within 1ms, and the time complexity of primary key failure is O(1). <br> Use the EXPIRE and TTL commands together. TTL can view the current survival time of the key. Returns 1 if the setting is successful; returns 0 when the key does not exist or the survival time cannot be set for the key. <br> Maximum cache configuration<br> In redis, users are allowed to set the maximum memory size<br> server.maxmemory<br> The default is 0, and the maximum cache is not specified. If new data is added and exceeds the maximum memory, then It will crash redis, so it must be set. When the size of the redis memory data set increases to a certain size, the data elimination strategy will be implemented. <br> Redis provides 6 data elimination strategies: <br> . volatile-lru: Select the least recently used data from the data set (server.db[i].expires) with an expiration time set for elimination<br> . volatile-ttl: Select the data that is about to expire from the data set (server.db[i].expires) with an expiration time set for elimination<br> . volatile-random: Randomly select data for elimination from the data set (server.db[i].expires) that has set expiration time<br> . allkeys-lru: Select the least recently used data from the data set (server.db[i].dict) to eliminate<br> . allkeys-random: Randomly select data from the data set (server.db[i].dict) for elimination<br> . no-enviction (eviction): prohibit eviction of data<br> Note the 6 mechanisms here. Volatile and allkeys specify whether to eliminate data from the data set with an expiration time or from all data sets. The following lru, ttl and Random is three different elimination strategies, plus a no-enviction strategy that never recycles. <br> Usage policy rules: <br> 1. If the data shows a power law distribution, that is, some data have high access frequency and some data have low access frequency, then use allkeys-lru<br> 2. If the data shows equal distribution, also That is, all data access frequencies are the same, then use allkeys-random<br> Three data elimination strategies: <br> ttl and random are easier to understand and easier to implement. The main reason is that Lru has used the elimination strategy at least recently. The design will sort the keys according to the expiration time, and then eliminate the key that expires first</p><p style="text-align: left;"><strong>16. The most suitable scenario for redis</strong></p> <p style="text-align: left;">Redis is most suitable for all data in-momory scenarios. Although Redis also provides persistence function, it is actually more of a disk-backed function, which is quite different from persistence in the traditional sense. Then it may Everyone will have questions. It seems that Redis is more like an enhanced version of Memcached, so when to use Memcached and when to use Redis? <br>If you simply compare the differences between Redis and Memcached, most people will get the following opinions: <br> 1. Redis not only supports simple k/v type data, but also provides storage of data structures such as list, set, zset, and hash. <br> 2. Redis supports data backup, that is, data backup in master-slave mode. <br> 3. Redis supports data persistence, which can keep the data in the memory on the disk and can be loaded again for use when restarting. <br>(1), Session Cache</p><p style="text-align: left;"> One of the most commonly used scenarios for using Redis is session cache. The advantage of using Redis to cache sessions over other storage (such as Memcached) is that Redis provides persistence. When maintaining a cache that does not strictly require consistency, most people will be unhappy if all the user's shopping cart information is lost. Now, </p><p style="text-align: left;"> Will they still be like this? </p><p style="text-align: left;"> Fortunately, as Redis has improved over the years, it is easy to figure out how to properly use Redis to cache session documents. Even the well-known commercial platform Magento provides Redis plug-ins. </p><p style="text-align: left;">(2), Full Page Cache (FPC)<br> In addition to the basic session token, Redis also provides a very simple FPC platform. Back to the consistency issue, even if the Redis instance is restarted, users will not see a decrease in page loading speed because of disk persistence. This is a great improvement, similar to PHP local FPC. <br> Taking Magento as an example again, Magento provides a plug-in to use Redis as a full-page cache backend. <br> In addition, for WordPress users, Pantheon has a very good plug-in wp-redis, which can help you load the pages you have browsed as quickly as possible. <br>(3), Queue<br> One of the great advantages of Redis in the field of memory storage engines is that it provides list and set operations, which allows Redis to be used as a good message queue platform. The operations used by Redis as a queue are similar to the push/pop operations of list in local programming languages (such as Python). <br> If you quickly search "Redis queues" in Google, you will immediately find a large number of open source projects. The purpose of these projects is to use Redis to create very good back-end tools to meet various queue needs. For example, Celery has a backend that uses Redis as the broker. You can view it from here. <br>(4), Ranking/Counter<br> Redis implements the operation of incrementing or decrementing numbers in memory very well. Sets and Sorted Sets also make it very simple for us to perform these operations. Redis just provides these two data structures. So, we want to get the top 10 users from the sorted set - we </p><p style="text-align: left;"> We call it "user_scores", we just need to execute it like the following: <br> Of course, this is Suppose you are sorting in ascending order based on your users' scores. If you want to return the user and the user's score, you need to execute it like this: <br> ZRANGE user_scores 0 10 WITHSCORES<br> <br> Agora Games is a good example, implemented in Ruby, and its ranking list uses Redis To store data, you can see it here. <br>(5), Publish/Subscribe<br> Last (but certainly not least) is the publish/subscribe function of Redis. There are indeed many use cases for publish/subscribe. I've seen people use it in social network connections, as triggers for publish/subscribe based scripts, and even to build chat systems using Redis' publish/subscribe functionality! (No, this is true, you can check it</p><p style="text-align: left;"> ). <br> Among all the features provided by Redis, I feel that this is the one that people like the least, although it provides users with this multi-function. </p><p style="text-align: left;">Related recommendations: </p><p style="text-align: left;"><a href="http://www.php.cn/php-weizijiaocheng-389606.html" target="_self">Detailed explanation of redis in php</a></p><p style="text-align: left;"><a href="http://www.php.cn/php-weizijiaocheng-389163.html" target="_self">Application examples of redis in php</a></p><p style="text-align: left;"><a href="http://www.php.cn/php-weizijiaocheng-387976.html" target="_self">Redis common usage scenarios sharing</a></p>
The above is the detailed content of The most common interview questions in Redis. For more information, please follow other related articles on the PHP Chinese website!
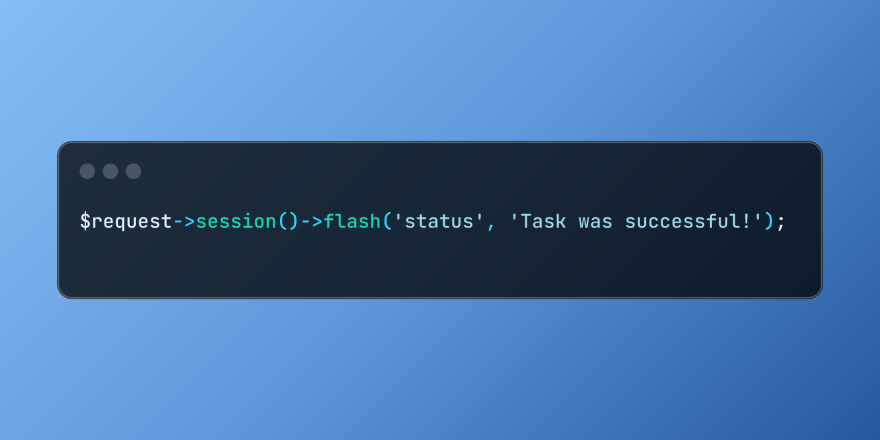 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
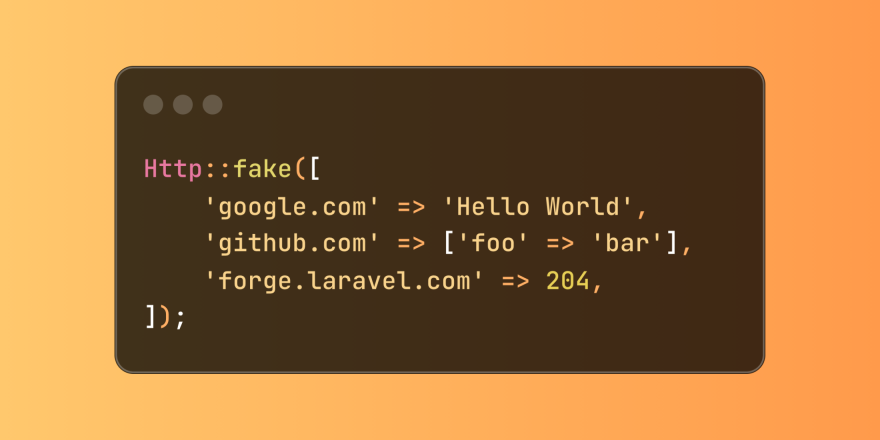 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot
 How to Register and Use Laravel Service ProvidersMar 07, 2025 am 01:18 AM
How to Register and Use Laravel Service ProvidersMar 07, 2025 am 01:18 AMLaravel's service container and service providers are fundamental to its architecture. This article explores service containers, details service provider creation, registration, and demonstrates practical usage with examples. We'll begin with an ove
 Customizing/Extending Frameworks: How to add custom functionality.Mar 28, 2025 pm 05:12 PM
Customizing/Extending Frameworks: How to add custom functionality.Mar 28, 2025 pm 05:12 PMThe article discusses adding custom functionality to frameworks, focusing on understanding architecture, identifying extension points, and best practices for integration and debugging.


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

SublimeText3 Chinese version
Chinese version, very easy to use

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.






