 Backend Development
Backend Development PHP Tutorial
PHP Tutorial The Attack and Defense of Voting and Voting Brushing - How to Prevent Voting Brushing
The Attack and Defense of Voting and Voting Brushing - How to Prevent Voting BrushingIn the project, voting is a very widely used function, and it also spawns a lot of vote-swiping behaviors. How to prevent ticket fraud has become a very important issue. This article hopes to be helpful to everyone by sharing some ideas on preventing ticket fraud.
1. IP restriction
This is the most commonly used, most widespread, and indispensable ticket brushing restriction. And since the topics do not have user modules, this method has almost become the only feasible method. This method limits the number of tickets that visitors can use within a period of time by obtaining their IP addresses. Of course, visitors who normally visit the page to vote will definitely be restricted by this method. However, various voting activities and special topics, as well as generous prizes, make some people try every means to swipe their votes.
ADSL users can change their IP address by disconnecting and redialing.
We cannot obtain the real IP address of users who use proxy access.
There are also unknown vote brushing tools.
The above are all problems that we have no way to overcome, and for Internet cafe/intranet users, such a setting will also seem unfair.
2. Cookies verification
This is also a method commonly used on the Internet. However, all information and content from the client are unreliable. People who are familiar with the principles of cookies can easily bypass restrictions.
Cookies can be disabled.
We cannot obtain the real IP address of users who use proxy access.
Cookies can be cleared and modified at will.
3. Session verification
session will assign a unique sessionID to all visitors. This seems to have some effect on preventing ticket fraud. Unfortunately, session has fatal shortcomings.
Close the browser and the session will be destroyed.
If the client disables cookies, the session will also become invalid.
4. Verification code
Register, log in, reply, post... Verification codes are used in a wide range of applications. Unfortunately, as for the specific effect, over time, it was found that this method only made it more difficult for ordinary tourists to vote, and the frequent access to verification codes for swiping votes also greatly increased the burden on the server.
There is a kind of verification code that is feasible. The graphical verification code launched by Google is designed to allow users to flip the picture to the correct direction to complete the verification. There must be very few software or computer operations that can bypass such a verification code very well. However, the disadvantage is that it is very difficult to implement.
5. MAC address restriction
As a web program, it is difficult to obtain the real Mac address (I experimented with php/js and did not successfully obtain the Mac address). When we read the client's Mac address, we also read information stored in the registry, which can also be modified.
6. User module
This should be considered a very useful method. Each visitor must register an account to vote. Voting can be restricted by limiting the account ID, and the initial registered user can be restricted from participating in voting for a period of time. Moreover, if there is a large influx of registered users, it can also increase the traffic of the website. However, for websites in small areas, this will make netizens find it very troublesome and may give up voting, thereby possibly losing users of the website.
7. Behavior Record
In fact, we cannot restrict many ticket fraud behaviors. But sometimes, we can record it very well. And when abnormal voting is detected, the number of votes will be automatically raised, or the illusion of successful voting will be returned, which can also effectively limit vote manipulation.
The disadvantage is that recording too much data will put a lot of pressure on the server. Moreover, if there are not enough recording points to record the behavior, and it is not complex enough, it may also be penetrated by professional users who use ticket fraud.
8. Answer the question
The first time we used this method to limit ticket fraud, we were very pleased to see good results. Unfortunately, if there is not a large enough question bank, the content and answers of the questions will soon be collected. On the contrary, users who normally vote will find voting disgusting, troublesome, and disgusted. Gradually we were abandoned.
9. Random voting address
This method allows each user who visits the page to get a random and unique KEY. Through this KEY, a voting address is generated. This address can only Visit once and become invalid after use.
Unfortunately, for the content of the specified KEY, I currently use the MD5 code generated by sessionid+ip+random number, and sessionid and IP are mentioned in the above content and can be destroyed and tampered with. This method is nothing more than a desperate struggle when IP restrictions and session restrictions are invalid.
10. Fill in the information
When voting, let visitors fill in information such as ID card, name, mobile phone number, etc. that can represent a person's identity for uniqueness verification. However, if you know the format of the ID card, you can fill in your name and mobile phone number as you like, and there is no restriction. On the contrary, it makes people who vote normally feel troublesome.
11. Voting code/numbering system
Before voting, users need to obtain a unique voting code/volume from other pages/mailboxes, which will be invalidated once used. However, how to verify the uniqueness of a 'person'? If there is a user with enough mailboxes, can he get unlimited voting codes?
right! Therefore, this is only a temporary solution rather than a permanent solution. However, at least this method will make ticket swiping people feel troublesome. But at the same time, it will also make people who vote normally feel inconvenient. However, it can be considered useful if it can make the vote-swiping party not so happy.
12. RMB voting
Tiger, this is the best, whether it is texting, calling, or Alipay, one yuan per vote, if you are willing enough, of course, whatever You vote and swipe as you wish, and we're happy not to. Through the combination of payment interfaces, cheating is quite difficult.
However, fairness needs to be considered. After all, not all supporters have money and are willing to spend money. Good works may not get votes because they are "poor". This is fair and In a democratic society, this is not recommended!
Okay, that’s almost all the above methods. To quote a netizen’s original text: “To completely put an end to ticket fraud, we basically have to rely on people.”
Thinking about it:
Flash vote, but I don’t know the principle very well. I will put it into testing when I have time.
Plug-in. Web plug-ins may require users to download and install them, which may be troublesome for ordinary users, and the feasibility remains to be studied.
Some interesting settings, for example, multiple votes in a short period of time may lead to a decrease in the number of votes; negative votes can be cast for a work, but there is a certain chance that it will be invalid or reflected to other works; similar to the 'stealing vegetables' on the farm, we You can vote and so on. Maybe it can add a little more playability, but fairness cannot be guaranteed.
Summary: Personally, I feel that the most effective method at present is RMB voting, which can effectively limit the behavior of vote fraud.
Related recommendations:
The above is the detailed content of The Attack and Defense of Voting and Voting Brushing - How to Prevent Voting Brushing. For more information, please follow other related articles on the PHP Chinese website!
 微信投票怎么发起Feb 23, 2024 pm 12:20 PM
微信投票怎么发起Feb 23, 2024 pm 12:20 PM微信投票怎么发起?在微信中是可以发起投票功能,但是多数的用户不知道微信中如何发起投票功能,接下来就是小编为用户带来的微信投票发起方法图文教程,感兴趣的用户快来一起看看吧!微信使用教程微信投票怎么发起1、首先打开微信APP,主页面最上方搜索框点击输入【投票】点击如下图所示的【群投票】;2、接着进入到群投票小程序页面,点击【+投票】服务按钮;3、最后在创建群投票页面编辑内容即可发起投票。
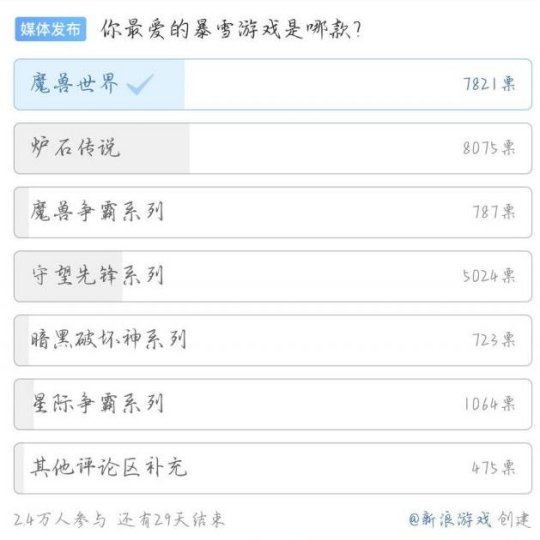 魔兽世界:多个媒体投票结果,玩家回归率惊人,点卡涨10倍也要玩Apr 15, 2024 pm 03:01 PM
魔兽世界:多个媒体投票结果,玩家回归率惊人,点卡涨10倍也要玩Apr 15, 2024 pm 03:01 PM国服官宣之后玩家的热情非常高,很多媒体也在公共平台发起了国服玩家回归意愿投票,下面我们来看看各项投票的数据。第一个投票是新浪科技发起的“你最爱的暴雪游戏是哪款”,本以为魔兽世界的玩家人数是最多的,结果炉石传说才是真正的王者。这也再一次证明了国服关闭之后的传言——炉石传说在国服的收益一直领先魔兽世界,直到怀旧服上线,魔兽世界才追了上来。第二个投票同样是新浪科技发起的“暴雪国服回归你还会玩吗?”结果只有40.6%的玩家选择了会继续玩,45.8%的玩家选择了不会继续玩,13.6%的玩家选择了不确定。要
 微博之夜怎么投票_微博之夜投票方法Mar 29, 2024 pm 06:12 PM
微博之夜怎么投票_微博之夜投票方法Mar 29, 2024 pm 06:12 PM1、打开手机上的微博最新版进入到里面。2、在里面输入微博之夜,找到官微进入。3、进入以后,置顶的微博打开,里面有向微博之夜出发,我们点击这个蓝字即可。4、进入主界面,往下拉就可以看到自己喜欢的明星,点击投票按钮。5、然后会显示他的简介,点击下面的投票按钮或者点击全部投给他。6、投完票以后界面就会提示我们投的票数了,自己坚持每天投票,后续会获得更多的票数。
 prompt攻防战!哥伦比亚大学提出BPE造词法,可绕过审核机制,DALL-E 2已中招Apr 12, 2023 am 10:31 AM
prompt攻防战!哥伦比亚大学提出BPE造词法,可绕过审核机制,DALL-E 2已中招Apr 12, 2023 am 10:31 AM2022年什么最值钱?prompt!基于文本的图像生成(text-guided image generation)模型,如DALL-E 2大火后,网友们也是乐此不疲地生成各种搞怪图像。 但想要让模型生成清晰、可用的目标图像,必须得掌握正确的「咒语」才行,也就是prompt须得精心设计之后才能用,甚至还有人架设网站卖起了prompt要是prompt是邪恶咒语,那生成的图片可能会「涉嫌违规」。虽然DALL-E 2发布之初就设立了各种机制来避免模型被滥用,比如从训练数据中删除暴力、仇恨或少儿不宜的图
 如何使用Webman框架实现在线调查和投票功能?Jul 08, 2023 am 08:05 AM
如何使用Webman框架实现在线调查和投票功能?Jul 08, 2023 am 08:05 AM如何使用Webman框架实现在线调查和投票功能?引言:随着互联网的快速发展,越来越多的人开始积极参与各种调查和投票活动。为了方便用户参与和管理这些活动,我们需要一个简单易用且功能强大的在线调查和投票系统。本文将介绍如何使用Webman框架来实现这一功能。一、Webman框架简介Webman是一个基于Python语言开发的轻量级Web框架,它提供了一套简单易用
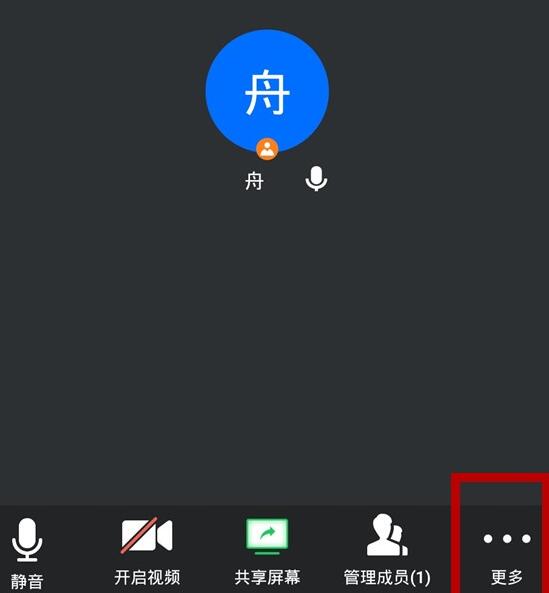 腾讯会议进行投票的简单教程Apr 02, 2024 pm 02:04 PM
腾讯会议进行投票的简单教程Apr 02, 2024 pm 02:04 PM1、点击会议右下角的【更多】。2、选择【聊天】。3、点击右上角齿轮设置图标。4、在对话框中选择【仅允许私聊主持人】。5、返回聊天界面,输入投票选项内容,选择发送给所有参会人员。
 使用JavaScript开发网页投票应用Aug 10, 2023 am 09:33 AM
使用JavaScript开发网页投票应用Aug 10, 2023 am 09:33 AM使用JavaScript开发网页投票应用随着互联网的发展,网上投票已经成为一种常见的方式来收集用户的意见和反馈。为了方便用户参与投票活动,开发一个简单的网页投票应用是非常有必要的。本文将介绍如何使用JavaScript开发一个网页投票应用,并附上相应的代码示例。准备工作首先,我们需要在网页中添加一个投票区域和一些选项按钮,用户可以在这里选择自己喜欢的选项进行
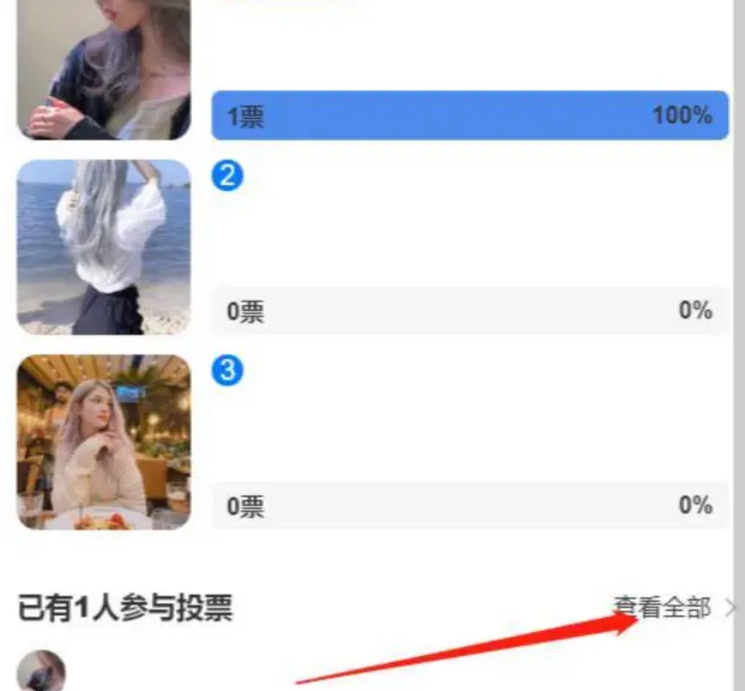 投票帮怎么看到投票的人Apr 01, 2024 pm 05:26 PM
投票帮怎么看到投票的人Apr 01, 2024 pm 05:26 PM投票是一种社会参与和意见表达的重要方式,通过投票,个体能够直接参与决策过程,影响公共事务的发展方向,而大家最常用的工具便是投票帮,所以小编本期就带来了查看投票帮活动投票记录明细流程,一起学习下吧。查看投票帮活动投票记录明细流程一、简易投票/群投票:这是一个简易投票系统,包括公开投票和群投票。参与投票活动后,点击投票页面底部的‘查看全部’按钮,即可查询投票明细。投票明细包括【所有投票者】的投票明细,还有【按选项查询】的单个选项的投票明细。注意:为保护匿名投票者的隐私,选择匿名投票的用户,只会统计票


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

SublimeText3 Linux new version
SublimeText3 Linux latest version

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment





