There are two sentences that say this:
1) Algorithms and data structures are an important part of programming. If you lose algorithms and data structures, you will lose everything.
2) Programming is algorithms and data structures. Algorithms and data structures are the soul of programming.
Note that this is not what I said. It was summed up by countless programmers. What I said is very practical and insightful. If you want long-term sustainable development, it is still necessary to study more algorithms. Today I will tell you about encryption algorithms. Symmetric encryption algorithm, and here we will teach you the programming and use of symmetric encryption algorithm. It includes the programming and use of three symmetric encryption algorithms: DES, 3DES and AES, and is full of useful information.

1.Symmetric cryptographic algorithm
Symmetric cryptographic algorithms are the most widely used and most frequently used encryption algorithms today. It is not only used in the software industry, but is also popular in the hardware industry. Whenever security requirements are involved in various infrastructures, symmetric encryption algorithms will be given priority.
The encryption key and decryption key of symmetric cryptographic algorithms are the same. For most symmetric cryptographic algorithms, the encryption and decryption processes are reversed.
(1) Encryption and decryption communication model

(2) Features: open algorithm, small amount of calculation, fast encryption speed, high encryption efficiency
(3) Weakness: Both parties use the same key, and security cannot be guaranteed
Symmetric ciphers include stream ciphers and block ciphers, but block ciphers are commonly used now:
(4) Block cipher working mode
1) ECB: Electronic codebook (the most commonly used, each encryption generates an independent ciphertext group, and will not affect other ciphertext groups, that is, the same plaintext will produce the same ciphertext after encryption)
2) CBC: Ciphertext link (commonly used, before plaintext encryption needs to be XORed with the previous ciphertext, that is, the same plaintext will produce different ciphertext after encryption)
3) CFB: ciphertext feedback
4) OFB: Output feedback
5) CTR: Counter
These five working modes are mainly used by algorithms in cryptography when performing derivation calculations.
6. Block cipher filling method
1) NoPadding: No padding
2) PKCS5Padding:
3) ISO10126Padding:
7. Commonly used symmetric passwords:
1) DES (Data Encryption Standard, Data Encryption Standard)
2) 3DES (Triple DES, DESede, triple DES encryption algorithm)
3) AES (Advanced Encryption Standard, advanced data encryption standard, AES algorithm can effectively resist the attack algorithm against DES)
Let’s first look at a simple comparison of these three algorithms:
| algorithm | Key length | Default key length | Operating mode | Filling method |
|---|---|---|---|---|
| DES | 56 | 56 | ECB, CBC, PCBC, CTR, CTS, CFB, CFB8-CFB128, OFB, OFB8-OFB128 | NoPadding、PKCS5Padding、ISO10126Padding |
| 3DES | 112, 168 | 168 | ECB, CBC, PCBC, CTR, CTS, CFB, CFB8-CFB128, OFB, OFB8-OFB128 | NoPadding、PKCS5Padding、ISO10126Padding |
| AES | 128, 192, 256 | 128 | ECB, CBC, PCBC, CTR, CTS, CFB, CFB8-CFB128, OFB, OFB8-OFB128 | NoPadding、PKCS5Padding、ISO10126Padding |
Let’s see how to use the three algorithms DES / 3DES / AES to implement symmetric encryption:
2.DES algorithm
1.DES: Data Encryption Standard, a typical algorithm in the field of symmetric encryption algorithms
2. Features: short key (56 bits), short life cycle (to avoid being cracked)
3.Java implementation
1) Generate key
KeyGenerator keyGen = KeyGenerator.getInstance("DES");//密钥生成器
keyGen.init(56);//初始化密钥生成器
SecretKey secretKey = keyGen.generateKey();//生成密钥
byte[] key = secretKey.getEncoded();//密钥字节数组
2) Encryption
SecretKey secretKey = new SecretKeySpec(key, "DES");//恢复密钥
Cipher cipher = Cipher.getInstance("DES");//Cipher完成加密或解密工作类
cipher.init(Cipher.ENCRYPT_MODE, secretKey);//对Cipher初始化,加密模式
byte[] cipherByte = cipher.doFinal(data);//加密data
3) Decryption
SecretKey secretKey = new SecretKeySpec(key, "DES");//恢复密钥
Cipher cipher = Cipher.getInstance("DES");//Cipher完成加密或解密工作类
cipher.init(Cipher.DECRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//解密data
We can find that we just set different modes for encryption and decryption.
3.3DES algorithm
1.3DES: Increase the key length to 112 or 168 bits to improve security by increasing the number of iterations
2. Disadvantages: slow processing speed, long key calculation time, low encryption efficiency
3.Java implementation
1) Generate key
KeyGenerator keyGen = KeyGenerator.getInstance("DESede");//密钥生成器
keyGen.init(168); //可指定密钥长度为112或168,默认为168
SecretKey secretKey = keyGen.generateKey();//生成密钥
byte[] key = secretKey.getEncoded();//密钥字节数组
2) 3DES encryption
SecretKey secretKey = new SecretKeySpec(key, "DESede");//恢复密钥
Cipher cipher = Cipher.getInstance("DESede");//Cipher完成加密或解密工作类
cipher.init(Cipher.ENCRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//加密data
3) 3DES decryption
SecretKey secretKey = new SecretKeySpec(key, "DESede");//恢复密钥
Cipher cipher = Cipher.getInstance("DESede");//Cipher完成加密或解密工作类
cipher.init(Cipher.DECRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//解密data
4.AES algorithm (recommended)
1.AES: Advanced Data Encryption Standard, which can effectively resist all known attacks against the DES algorithm
2. Features: short key establishment time, good sensitivity, low memory requirements, and high security
3.Java implementation
1) Generate key
KeyGenerator keyGen = KeyGenerator.getInstance("AES");//密钥生成器
keygen.init(128); //默认128,获得无政策权限后可为192或256
SecretKey secretKey = keyGen.generateKey();//生成密钥
byte[] key = secretKey.getEncoded();//密钥字节数组
2) AES encryption
SecretKey secretKey = new SecretKeySpec(key, "AES");//恢复密钥
Cipher cipher = Cipher.getInstance("AES");//Cipher完成加密或解密工作类
cipher.init(Cipher.ENCRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//加密data
3) AES decryption
SecretKey secretKey = new SecretKeySpec(key, "AES");//恢复密钥
Cipher cipher = Cipher.getInstance("AES");//Cipher完成加密或解密工作类
cipher.init(Cipher.DECRYPT_MODE, secretKey);//对Cipher初始化,解密模式
byte[] cipherByte = cipher.doFinal(data);//解密data
For ease of use, I wrote tool classes for the three algorithms DES/3DES/AES, address: https://github.com/smartbetter/Android-UtilsLibrary (new DES/3DES/AES tool class).
The above is the detailed content of Implementation of three symmetric encryption algorithms DES/3DES/AES in Java. For more information, please follow other related articles on the PHP Chinese website!
 如何在Java中进行AES加密和解密操作May 08, 2023 pm 10:34 PM
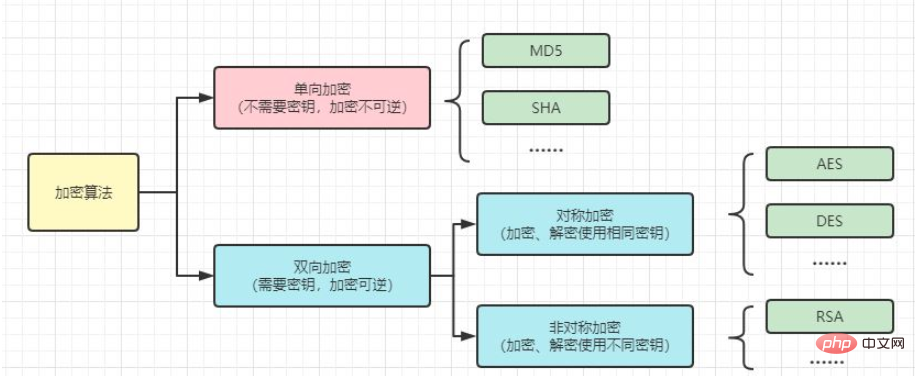
如何在Java中进行AES加密和解密操作May 08, 2023 pm 10:34 PM1.背景知识在密码学中,加密算法分为单向加密和双向加密。对称加密是指加密和解密使用相同的密钥,包括AES加密、DES加密等。非对称加密是指加密和解密使用不同的密钥,包括RSA加密等。单向加密包括MD5、SHA等摘要算法,它们是不可逆的。双向加密包括对称加密和非对称加密。双向加密是可逆的,存在密文的密钥。2.AES简介AES:高级加密标准(AdvancedEncryptionStandard)是美国联邦政府采用的一种区块加密标准,是目前最流行的一种对称加密算法。是用来替代DES的新一代分组加密算法
 PHP中的高速加密算法及其应用Jun 23, 2023 am 10:42 AM
PHP中的高速加密算法及其应用Jun 23, 2023 am 10:42 AM随着网络技术的不断发展,Web应用程序越来越普及,而Web应用程序中的信息安全也变得日益重要。为了解决Web应用程序中信息安全的问题,人们研究出了很多加密算法,其中最著名的当属RSA、DES等算法。不过,由于加密算法的解密需要大量计算和时间,会带来较大的系统负担,因此出现了一类能够在短时间内快速加密和解密的加密算法,这就是高速加密算法。本文将介绍PHP中的高
 SpringBoot如何实现RAS+AES自动接口解密May 20, 2023 pm 04:04 PM
SpringBoot如何实现RAS+AES自动接口解密May 20, 2023 pm 04:04 PM一、讲个事故接口安全老生常谈了过年之前做了过一款飞机大战的H5小游戏,里面无限模式-需要保存用户的积分,因为使用的Body传参,参数是可见的,为了接口安全我,我和前端约定了传递参数是:用户无限模式的积分+“我们约定的一个数字”+用户id的和,在用Base64加密,请求到服务器我再解密,出用户无限模式的积分;如下:{"integral":"MTExMTM0NzY5NQ==",}可是过年的时候,运营突然找我说无限模式积分排行榜分数不对:这就很诡异了,第二名才一
 PHP中如何进行对称和非对称加密?May 21, 2023 pm 03:10 PM
PHP中如何进行对称和非对称加密?May 21, 2023 pm 03:10 PM在网络安全领域,加密技术是一种非常重要的技术手段,其可以将数据进行加密和解密,从而确保数据的安全性。PHP作为一种流行的服务器端编程语言,也提供了对称和非对称加密的支持,以满足不同应用场景的需求。对称加密对称加密是指使用相同的密钥进行加密与解密的加密方法。对称加密算法有很多,比如DES、3DES、AES等。在PHP中,使用mcrypt扩展库提供的函数可以实现
 PHP中的AES256加密技术及其在框架中的应用方法详解Jun 09, 2023 pm 12:25 PM
PHP中的AES256加密技术及其在框架中的应用方法详解Jun 09, 2023 pm 12:25 PM随着互联网的发展和普及,数据的安全性越来越受到重视。在数据传输和存储过程中,加密技术是一种非常有效的手段,通过加密可以保证数据的机密性和完整性。而在PHP中,AES256加密技术是一种非常流行的加密方式,本文将详细介绍其在框架中的应用方法。AES256加密技术简介AES(AdvancedEncryptionStandard)即高级加密标准,是现代流行的对
 如何利用Python编写RSA加密算法?Sep 20, 2023 pm 01:21 PM
如何利用Python编写RSA加密算法?Sep 20, 2023 pm 01:21 PM如何利用Python编写RSA加密算法?引言:RSA是一种非对称加密算法,被广泛应用于信息安全领域。在现代通信中,RSA加密算法常用于加密和解密敏感数据。本文将介绍如何使用Python编写RSA加密算法,并提供具体的代码示例。安装Python库在开始编写RSA加密算法之前,需要安装Python的加密库。可以使用以下命令安装:pipinstallrsa生成
 PHP和Java des的加密解密实例分析Apr 29, 2023 am 09:40 AM
PHP和Java des的加密解密实例分析Apr 29, 2023 am 09:40 AMdes加密是对称加密中在互联网应用的比较多的一种加密方式,php通过mcrypt扩展库来支持des加密,要在Php中使用des加密,需要先安装mcrypt扩展库下面是加密解密的实例复制代码代码如下:$iv_size=mcrypt_get_iv_size(MCRYPT_RIJNDAEL_256,MCRYPT_MODE_ECB);$iv=mcrypt_create_iv($iv_size,MCRYPT_RAND);$key="Thisisaverysecretkey";//密钥$
 php加密算法有哪些Aug 31, 2023 pm 05:24 PM
php加密算法有哪些Aug 31, 2023 pm 05:24 PMphp加密算法有MD5算法、SHA算法、AES算法、RSA算法、Base64编码、DES算法、RC4算法、Blowfish算法等。详细介绍:1、MD5算法,用于将任意长度的数据转换为固定长度的哈希值,在PHP中可以使用md5()函数来计算字符串的MD5哈希值;2、SHA算法,包括SHA-1、SHA-256、SHA-512等,这些算法在PHP中都有对应的函数;3、AES算法等等。


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Atom editor mac version download
The most popular open source editor

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

Dreamweaver CS6
Visual web development tools






