If the client makes a request to the server interface, if the request information is encrypted and the request package is intercepted by a third party, although the third party cannot decrypt and obtain the data, it can use the request package for repeated processing. Request action. If the server does not prevent replay attacks, the pressure on the server will increase and the data will be disordered. This problem can be solved by adding a timestamp.
private readonly string TimeStamp = ConfigurationManager.AppSettings["TimeStamp"];//配置时间戳
[HttpPost]
public ActionResult TestApi()
{
string RequestTime = Request["rtime"]; //请求时间经过RSA签名
try
{
//请求时间RSA解密后加上时间戳的时间即该请求的有效时间
DateTime Requestdt = DateTime.Parse(RSACryptoProvider.Decrypt(RequestTime, RSA_Keys.Private)).AddMinutes(int.Parse(TimeStamp));
DateTime Newdt = DateTime.Now; //服务器接收请求的当前时间
//if 请求的有效时间 < 现在服务器接受请求的时间 即该请求失效
if (Requestdt < Newdt)
{
return Json(new { success = false, message = "该请求已经失效" });
}
else
{
//进行其他操作
}
}
catch (Exception ex)
{
return Json(new { success = false, message = "请求参数不和要求" });
}
}The above is the content of .NET adding timestamp to prevent replay attacks. For more related content, please pay attention to the PHP Chinese website (www .php.cn)!
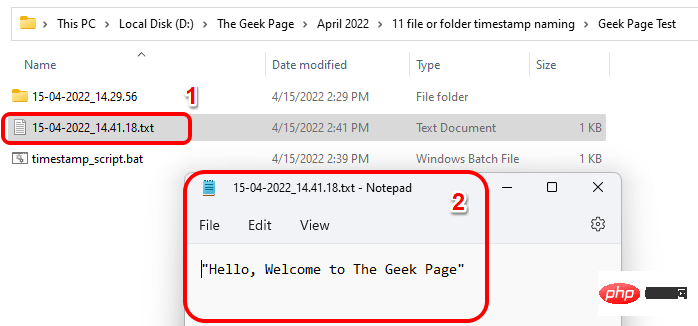 如何根据当前时间戳创建文件/文件夹并为其命名Apr 27, 2023 pm 11:07 PM
如何根据当前时间戳创建文件/文件夹并为其命名Apr 27, 2023 pm 11:07 PM如果您正在寻找根据系统时间戳自动创建文件和文件夹并为其命名的方法,那么您来对地方了。有一种超级简单的方法可以用来完成这项任务。然后,创建的文件夹或文件可用于各种目的,例如存储文件备份、根据日期对文件进行排序等。在本文中,我们将通过一些非常简单的步骤解释如何在Windows11/10中自动创建文件和文件夹,并根据系统的时间戳对其进行命名。使用的方法是批处理脚本,非常简单。希望你喜欢阅读这篇文章。第1节:如何根据系统当前时间戳自动创建文件夹并命名第1步:首先,导航到要在其中创建文件夹的父文件夹,
 Golang时间处理:如何在Golang中将时间戳转换为字符串Feb 24, 2024 pm 10:42 PM
Golang时间处理:如何在Golang中将时间戳转换为字符串Feb 24, 2024 pm 10:42 PMGolang时间转换:如何将时间戳转换为字符串在Golang中,时间操作是非常常见的操作之一。有时候我们需要将时间戳转换为字符串,以便于展示或者存储。本文将介绍如何使用Golang将时间戳转换为字符串,并提供具体的代码示例。1.时间戳和字符串的转换在Golang中,时间戳通常是以整型数字的形式表示的,表示的是从1970年1月1日至当前时间的秒数。而字符串则
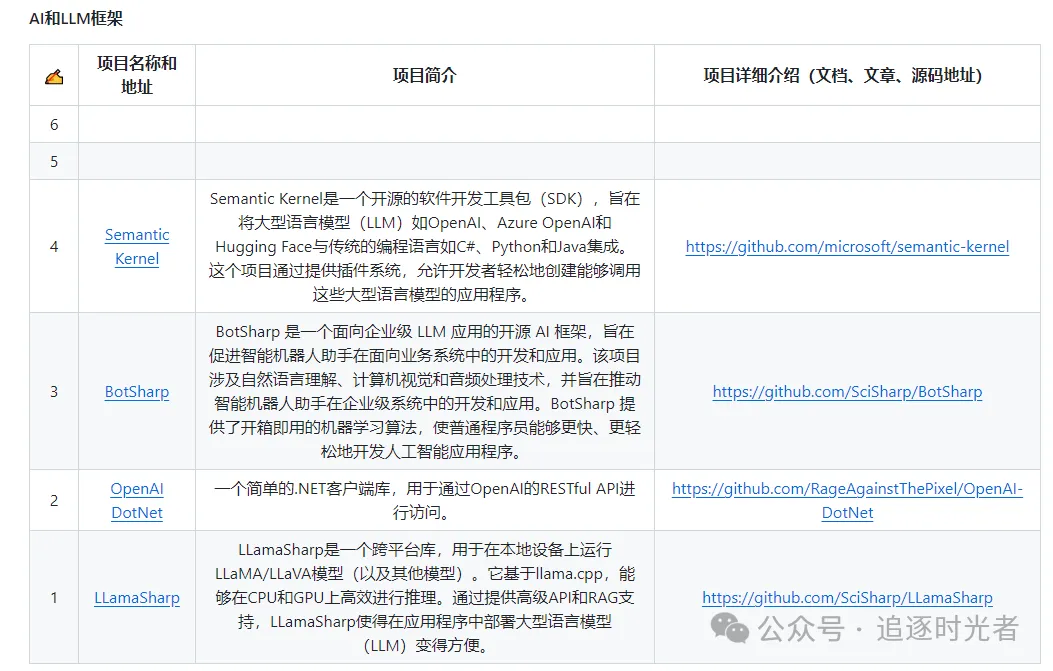 分享几个.NET开源的AI和LLM相关项目框架May 06, 2024 pm 04:43 PM
分享几个.NET开源的AI和LLM相关项目框架May 06, 2024 pm 04:43 PM当今人工智能(AI)技术的发展如火如荼,它们在各个领域都展现出了巨大的潜力和影响力。今天大姚给大家分享4个.NET开源的AI模型LLM相关的项目框架,希望能为大家提供一些参考。https://github.com/YSGStudyHards/DotNetGuide/blob/main/docs/DotNet/DotNetProjectPicks.mdSemanticKernelSemanticKernel是一种开源的软件开发工具包(SDK),旨在将大型语言模型(LLM)如OpenAI、Azure
 时间戳获取的最佳实践:Golang编程中的强大工具Dec 29, 2023 am 08:28 AM
时间戳获取的最佳实践:Golang编程中的强大工具Dec 29, 2023 am 08:28 AMGolang编程利器:时间戳获取的最佳实践引言:在软件开发中,时间戳是一个非常常见的概念。它是一个标识特定事件发生的数字值,通常表示自从某个参考时间点开始的毫秒数或纳秒数。在Golang中,处理时间戳的操作非常简单且高效。本文将介绍Golang中获取时间戳的最佳实践,并提供具体的代码示例。正文:获取当前时间戳在Golang中,获取当前时间戳非常简单。我们可以
 Java文档解读:System类的currentTimeMillis()方法用法解析Nov 03, 2023 am 09:30 AM
Java文档解读:System类的currentTimeMillis()方法用法解析Nov 03, 2023 am 09:30 AMJava文档解读:System类的currentTimeMillis()方法用法解析,需要具体代码示例在Java编程中,System类是一个非常重要的类,其封装了与系统相关的一些属性和操作。其中,currentTimeMillis方法是System类中非常常用的一个方法,本文将对该方法做详细解读并提供代码示例。一.currentTimeMillis方法概述
 如何从Excel中的日期中删除时间May 17, 2023 am 11:22 AM
如何从Excel中的日期中删除时间May 17, 2023 am 11:22 AM使用数字格式更改Excel中的日期格式在Excel中从日期中删除时间的最简单方法是更改数字格式。这不会从时间戳中删除时间——它只是阻止它在您的单元格中显示。如果您在计算中使用这些单元格,时间和日期仍然包括在内。要使用数字格式更改Excel中的日期格式:打开您的Excel电子表格。选择包含您的时间戳的单元格。在主菜单中,选择数字格式框末尾的向下箭头。选择一种日期格式。更改格式后,时间将停止出现在您的单元格中。如果单击其中一个单元格,则时间格式在编辑栏中仍然可见。使用单元格格式更
 PHP中的时间戳处理:如何使用strftime函数格式化时间戳为本地化的日期时间Jul 30, 2023 am 09:15 AM
PHP中的时间戳处理:如何使用strftime函数格式化时间戳为本地化的日期时间Jul 30, 2023 am 09:15 AMPHP中的时间戳处理:如何使用strftime函数格式化时间戳为本地化的日期时间在开发PHP应用程序时,我们经常需要处理日期和时间。PHP提供了强大的日期和时间处理函数,其中strftime函数允许我们将时间戳格式化为本地化的日期时间。strftime函数具有以下语法:strftime(string$format[,int$timestamp=ti


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Atom editor mac version download
The most popular open source editor

Dreamweaver Mac version
Visual web development tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 English version
Recommended: Win version, supports code prompts!







