Django’s permission system is very simple, it can grant permissions to users or users in groups.
Django admin backend uses this permission system, but it can also be used in your own code. A User Will '
' Get All Permissions Granted to Each of 'Their Groups. Ermissions = Models.manytomanyField (Permission,Verbose_name = _ ('User permissions'), blank=True,
help_text=_('Specific permissions for this user.'), related_name="user_set", related_query_name="user")
You can access them like other django Models:
myuser.groups = [group_list]
myuser.groups.add(group, group, ...)
myuser.groups.remove(group, group, ...)
myuser.groups.clear()
myuser. user_permissions = [permission_list]
myuser.user_permissions.remove(permission, permission, ...)
myuser.user_permissions.clear()
Permissions
Permission exists as a Model. To establish a permission is to create an instance of the Permission Model.
@python_2_unicode_compatible
class Permission(models.Model):
"""
users and groups of users.
The permissions system is used by the Django admin site, but may also be
useful in your own code. The Django admin site uses permissions as follows:
- The "add" permission limits the user's ability to view the "add" form
and add an object.
- The "change" permission limits a user's ability to view the change
list, view the "change" form and change an object.
- The "delete" permission limits the ability to delete an object.
Permissions are set globally per type of object, not per specific object
instance. It is possible to say "Mary may change news stories," but it's
not currently possible to say "Mary may change news stories, but only the
ones she created herself" or "Mary may only change news stories that have a
certain status or publication date."
Three basic permissions -- add, change and delete -- are automatically
created for each Django model.
"""
name = models.CharField(_('name '), max_length=255)
content_type = models.ForeignKey(ContentType)
codename = models.CharField(_('codename'), max_length=100)
objects = PermissionManager()
class Meta:
verbose_name = _( 'permission')
verbose_name_plural = _('permissions')
unique_together = (('content_type', 'codename'),)
ordering = ('content_type__app_label', 'content_type__model',
'codename')
def __str__( self):
using using through through ’s ’ s ’ through ‐ ‐ ‐ off to )
def natural_key(self):
return (self.codename,) + self.content_type.natural_key()
natural_key.dependencies = ['contenttypes.contenttype']
fields fields
name: required. 50 characters or less, for example, 'Can Vote'
content_type: Required, a reference to the django_content_type database table, which contains records for each Model in the application.
codename: required, 100 characters or less, e.g., 'can_vote'.
If you want to create permissions for a Model:
from django.db import models
class Vote(models.Model):
...
class Meta:
permissions = (("can_vote", "Can Vote "),)
If this Model is in the application foo, the permission is expressed as 'foo.can_vote', check whether a user has the permission myuser.has_perm('foo.can_vote')
default permissions
If django.contrib.auth has been configured in INSTALLED_APPS, it will ensure that 3 default permissions are created for each Django Model in installed applications: add, change and delete.
These permissions will be created the first time you run manage.py migrate (syncdb before 1.7). At that time, all models will have permissions established. New models created after this will have these default permissions created when manage.py migrate is run again. These permissions correspond to the creation, deletion, and modification behaviors in the admin management interface.
Suppose you have an application foo with a model Bar, you can use the following method to test basic permissions:
add: user.has_perm('foo.add_bar')
change: user.has_perm('foo. change_bar')
delete: user.has_perm('foo.delete_bar')
Permission model (Permission model) is generally not used directly.
Groups
Groups also exist as Models:
@python_2_unicode_compatible
class Group(models.Model):
"""
Groups are a generic way of categorizing users to apply permissions, or
some other label, to those users. A user can belong to any number of
groups.
A user in a group automatically has all the permissions granted to that
group. group will have that permission.
Beyond permissions, groups are a convenient way to categorize users to
apply some label, or extended functionality, to them. For example, you
could create a group 'Special users', and you could write code that would
do special things to those users -- such as giving them access to a
members-only portion of your site, or sending them members-only email
messages.
"""
name = models.CharField(_ ('name'), max_length=80, unique=True)
permissions = models.ManyToManyField(Permission,
) verbose_name=_('permissions'), blank=True)
objects = GroupManager()
class Meta:
Verbose_name = _ ('Group')
Verbose_name_plural = _ ('Groups')
DEF __Str __ (Self):
Return Self.name
Def Nature_key (Sel):
Return (SELN f.Name,) 段 field fields:
name: required, 80 characters or less, e.g., 'Awesome Users'.
permissions: ManyToManyField to Permission
group.permissions = [permission_list]
group.permissions.add(permission, permission, ...)group.permissions.remove(permission, permission, ...)
group.permissions .clear()
Programmatically creating permissions
In addition to using Model meta to create permissions, you can also create them directly with code.
For example, create a can_publish permission for the BlogPost model in the myapp application:
from myapp.models import BlogPost
from django.contrib.auth.models import Group, Permissionfrom django.contrib.contenttypes.models import ContentType
content_type = ContentType.objects.get_for_model(BlogPost)
permission = Permission.objects.create(codename='can_publish',
name='Can Publish Posts',
content_type=content_type)
Permissions can be given to a User object through Its user_permissions attribute or assigned to a Group through its permissions attribute.
Permission caching
User's permissions can be cached when checked. If a new permission is given to a User, it will not be checked if it is checked immediately. The easiest way is to re-fetch the User object.
from django.contrib.auth.models import Permission, User
from django.shortcuts import get_object_or_404
def user_gains_perms(request, user_id):
user = get_object_or_404(User, pk=user_id)
#Permission check will cache the current permissions Set
user.has_perm('myapp.change_bar')
permission = Permission.objects.get(codename='change_bar')
user.user_permissions.add(permission)
# Check permission cache set
user.has_perm(' myapp.change_bar') # False
# Request a new instance
user = get_object_or_404(User, pk=user_id)
# Permission cache is repopulated from the database
user.has_perm('myapp.change_bar') # True
. ..
Permission decorator
permission_required(perm[, login_url=None, raise_exception=False])
Check whether the user has a certain permission, similar to @login_required()
from django.contrib.auth.decorators import permission_required
@permission_required('polls.can_vote', login_url='/loginpage/')
def my_view(request):
...
Permissions in the template
user's permissions are stored in template variables { { perms }} is the django.contrib.auth.context_processors.PermWrapper instance.
{{ perms.foo }}
The single attribute above is the proxy of User.has_module_perms. If the user has any permission in foo, it is True
{{ perms.foo.can_vote }}
The above two-level attribute query is a proxy of User.has_perm, if the user has the foo.can_vote permission, it is True .
For example:
{% if perms.foo %}
You have permission to do something in the You can vote! else %}
You don't have permission to do anything in the foo app.
{% endif %}
or:
{% if 'foo' in perms %}
{% if 'foo.can_vote' in perms %}
For more related content, please pay attention to the PHP Chinese website (www.php.cn)!
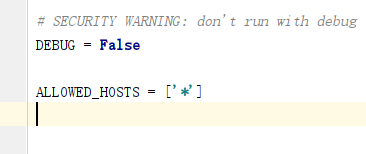 怎么将Django项目迁移到linux系统中Jun 01, 2023 pm 01:07 PM
怎么将Django项目迁移到linux系统中Jun 01, 2023 pm 01:07 PMDjango项目配置修改我们需要把原先的Django项目进行修改才能更好地进行项目迁移工作,首先需要修改的是settings.py文件。由于项目上线之后不能让用户看到后台的运行逻辑,所以我们要把DEBUG改成False,把ALLOWED_HOSTS写成‘*’,这样是为了允许从不同主机进行访问。由于linux中如果不加这句可能会出现文件找不到的情况,所以我们要把模板的路径进行拼接。由于做Django项目肯定进行过数据库的同步,所以我们要把migrations
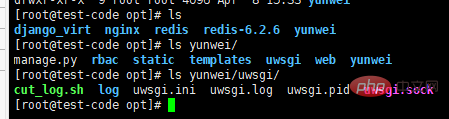 centos+nginx+uwsgi部署django项目上线的方法May 15, 2023 am 08:13 AM
centos+nginx+uwsgi部署django项目上线的方法May 15, 2023 am 08:13 AM我django项目叫yunwei,主要app是rabc和web,整个项目放/opt/下如下:[root@test-codeopt]#lsdjango_virtnginxredisredis-6.2.6yunwei[root@test-codeopt]#lsyunwei/manage.pyrbacstatictemplatesuwsgiwebyunwei[root@test-codeopt]#lsyunwei/uwsgi/cut_log.shloguwsgi.iniuwsgi.loguwsgi.p
 Django框架中的数据库迁移技巧Jun 17, 2023 pm 01:10 PM
Django框架中的数据库迁移技巧Jun 17, 2023 pm 01:10 PMDjango是一个使用Python语言编写的Web开发框架,其提供了许多方便的工具和模块来帮助开发人员快速地搭建网站和应用程序。其中最重要的一个特性就是数据库迁移功能,它可以帮助我们简单地管理数据库模式的变化。在本文中,我们将会介绍一些在Django中使用数据库迁移的技巧,包括如何开始一个新的数据库迁移、如何检测数据库迁移冲突、如何查看历史数据库迁移记录等等
 Django框架中的文件上传技巧Jun 18, 2023 am 08:24 AM
Django框架中的文件上传技巧Jun 18, 2023 am 08:24 AM近年来,Web应用程序逐渐流行,而其中许多应用程序都需要文件上传功能。在Django框架中,实现上传文件功能并不困难,但是在实际开发中,我们还需要处理上传的文件,其他操作包括更改文件名、限制文件大小等问题。本文将分享一些Django框架中的文件上传技巧。一、配置文件上传项在Django项目中,要配置文件上传需要在settings.py文件中进
 如何用nginx+uwsgi部署自己的django项目May 12, 2023 pm 10:10 PM
如何用nginx+uwsgi部署自己的django项目May 12, 2023 pm 10:10 PM第一步:换源输入命令换掉Ubuntu的下载源sudonano/etc/apt/sources.list将以下全部替换掉原文件,我这里用的是阿里的源,你也可以换其他的。debhttp://mirrors.aliyun.com/ubuntu/bionicmainrestricteddebhttp://mirrors.aliyun.com/ubuntu/bionic-updatesmainrestricteddebhttp://mirrors.aliyun.com/ubuntu/bionicunive
 使用Django构建RESTful APIJun 17, 2023 pm 09:29 PM
使用Django构建RESTful APIJun 17, 2023 pm 09:29 PMDjango是一个Web框架,可以轻松地构建RESTfulAPI。RESTfulAPI是一种基于Web的架构,可以通过HTTP协议访问。在这篇文章中,我们将介绍如何使用Django来构建RESTfulAPI,包括如何使用DjangoREST框架来简化开发过程。安装Django首先,我们需要在本地安装Django。可以使用pip来安装Django,具体
 使用Python Django框架构建博客网站Jun 17, 2023 pm 03:37 PM
使用Python Django框架构建博客网站Jun 17, 2023 pm 03:37 PM随着互联网的普及,博客在信息传播和交流方面扮演着越来越重要的角色。在此背景下,越来越多的人开始构建自己的博客网站。本文将介绍如何使用PythonDjango框架来构建自己的博客网站。一、PythonDjango框架简介PythonDjango是一个免费的开源Web框架,可用于快速开发Web应用程序。该框架为开发人员提供了强大的工具,可帮助他们构建功能丰
 Django+Bootstrap构建响应式管理后台系统Jun 17, 2023 pm 05:27 PM
Django+Bootstrap构建响应式管理后台系统Jun 17, 2023 pm 05:27 PM随着互联网技术的快速发展和企业业务的不断扩展,越来越多的企业需要建立自己的管理后台系统,以便于更好地管理业务和数据。而现在,使用Django框架和Bootstrap前端库构建响应式管理后台系统的趋势也越来越明显。本文将介绍如何利用Django和Bootstrap构建一个响应式的管理后台系统。Django是一种基于Python语言的Web框架,它提供了丰富的功


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version






