 Backend Development
Backend Development PHP Tutorial
PHP Tutorial The problem of openssl rsa key format solves the key format problem of collaborative development of php and c++
The problem of openssl rsa key format solves the key format problem of collaborative development of php and c++OpenSSL Programming - Detailed Explanation of RSA Programming
This article was published by Da Tong on June 26, 2014, viewed: 1,954 times, comments: 0
1. RSA PEM file format
1. PEM private key format file
-- ---BEGIN RSA PRIVATE KEY-----
-----END RSA PRIVATE KEY-----
2. PEM public key format file
-----BEGIN PUBLIC KEY-----
-----END PUBLIC KEY-----
3. PEM RSAPublicKey public key format file
-----BEGIN RSA PUBLIC KEY-----
-----END RSA PUBLIC KEY- ----
2. OpenSSL key related commands
1. Generate key
openssl genrsa -out key.pem 1024
-out specifies the generated file. This file contains the public key and the private key, so you can Encryption and decryption
1024 The length of the generated key
2. Extract the PEM format public key
openssl rsa -in key.pem -pubout -out pubkey.pem
-in specifies the input key file
-out specifies the extraction Generate a public key file (PEM public key format)
3. Extract the PEM RSAPublicKey format public key
openssl rsa -in key.pem -RSAPublicKey_out -out pubkey.pem
-in specifies the input key file
-out specifies the extraction Generate public key file (PEM RSAPublicKey format)
4. Public key encryption file
openssl rsautl -encrypt -in input.file -inkey pubkey.pem -pubin -out output.file
-in Specify the encrypted file
- inkey specifies the encrypted public key file
-pubin The surface is encrypted with a pure public key file
-out specifies the encrypted file
5. Private key decryption file
openssl rsautl -decrypt -in input.file -inkey key.pem -out output.file
-in specifies the file to be decrypted
-inkey specifies the private key file
-out specifies the decrypted file
3. RSA related API
1. Basic data structure
struct {
BIGNUM *n; public modulus
BIGNUM *e; // public exponent
BIGNUM *d; // private exponent
BIGNUM *p; // secret prime factor
BIGNUM *dmp1; // d mod ( p-1)
BIGNUM *dmq1; // d mod (q-1)
BIGNUM *iqmp; Function
//Generate a new BIGNUM structure
BIGNUM *BN_new(void);
void BN_free(BIGNUM *a);
//Initialize all items is 0, usually BN_ init(&c)
void BN_init(BIGNUM *);
//Assign all items in a to 0, but the memory is not released
void BN_clear(BIGNUM *a);
// It is equivalent to combining BN_free and BN_clear, either assigning a value of 0 or releasing space.
void BN_clear_free(BIGNUM *a);
//Set the large number a to an integer w
int BN_set_word(BIGNUM *a, unsigned long w);
//If the large number a can be expressed as a long type, then return a long type number
unsigned long BN_get_word(BIGNUM *a);
//Generate a pseudo-random number with strong bits for encryption
//If top=-1, the highest bit is 0, top=0, the highest bit is 1 ,top=1, the highest and second highest bits are 1, bottom is true, and the random number is an even number
//Convert a into a string for storage Enter to, the space of to must be larger than BN_num_bytes(a)
//Convert the len-digit positive integer in s into a large number
BIGNUM *BN_bin2bn(const unsigned char *s, int len, BIGNUM *ret);
//Convert large numbers to hexadecimal strings
char *BN_bn2hex(const BIGNUM *a);
//Convert large numbers to decimal String
char *BN_bn2dec(const BIGNUM *a);
//Convert hexadecimal string to large number
int BN_hex2bn(BIGNUM **a, const char *str);
//Convert decimal Pass the string into a large number
int BN_dec2bn(BIGNUM **a, const char *str);
3. RSA series functions
//Initialize an RSA structure
//Release an RSA Structure
void RSA_free(RSA *rsa);
//RSA private key generation function
//Generate a key pair modulo num bits, e is the public encryption index, generally 65537 (0x10001)
RSA *RSA_generate_key (int num, unsigned long e,void (*callback)(int,int,void *), void *cb_arg);
//Judge the number of digits function, return the number of digits in the RSA module
int RSA_size(const RSA *rsa);
//Test whether p and q are prime numbers
int RSA_check_key(RSA *rsa);
4. PEM series Function
//Load the RSAPublicKey format public key certificate from the file
RSA *PEM_read_RSAPublicKey(FILE *fp, RSA **x, pem_password_cb *cb, void *u);
//Reload the RSAPublicKey format public key certificate from the BIO
RSA *PEM_read_bio_RSAPublicKey(BIO *bp, RSA **x, pem_password_cb *cb, void *u);
//Output the RSAPublicKey public key certificate to the file
int PEM_write_RSAPublicKey(FILE *fp, RSA *x);
// Output the RSAPublicKey public key certificate to BIO
int PEM_write_bio_RSAPublicKey(BIO *bp, RSA *x);
5. RSA encryption API
int RSA_public_encrypt(int flen, unsigned char *from, unsigned char *to, RSA *rsa, int padding );
Parameter description:
flen: the length of the information to be encrypted
from: the information to be encrypted
to: the encrypted information
padding: the encryption scheme adopted, divided into: RSA_PKCS1_PADDING, RSA_PKCS1_OAEP_PADDING, RSA_SSLV23_PADDING, RSA_NO_PADDING
6.RSA Decryption API
int RSA_private_decrypt(int flen, unsigned char *from, unsigned char *to, RSA *rsa, int padding);
Parameter description:
flen: length of information to be decrypted
from: information to be decrypted
to: Decrypted information
padding: Decryption scheme adopted
IV. RSA programming example
1. Data encryption, encryption and decryption example
#include
#include
#include
#include
#include
#include
#define PRIKEY "prikey.pem"
#define PUBKEY "pubkey.pem "
#define BUFFSIZE 4096
/***************************************************** ************************
* RSA encryption and decryption function
*
* file: test_rsa_encdec.c
* gcc -Wall -O2 -o test_rsa_encdec test_rsa_encdec.c -lcrypto -lssl
*
* author: tonglulin@gmail.com by
www.qmailer.net
************************************************ ****************************/
char *my_encrypt(char *str, char *pubkey_path)
{
RSA *rsa = NULL;
FILE *fp = NULL;
char *en = NULL;
int len = 0;
int rsa_len = 0;
if ((fp = fopen(pubkey_path, "r")) == NULL) {
return NULL;
}
/* Read the public key PEM, PUBKEY format PEM uses the PEM_read_RSA_PUBKEY function */
if ((rsa = PEM_read_RSAPublicKey(fp, NULL, NULL, NULL)) == NULL) {
return NULL;
}
RSA_print_fp(stdout, rsa, 0);
len = strlen(str);
rsa_len = RSA_size(rsa);
en = (char *)malloc(rsa_len + 1);
memset(en, 0, rsa_len + 1);
if (RSA_public_encrypt(rsa_len , (unsigned char *)str, (unsigned char*)en, rsa, RSA_NO_PADDING) return NULL;
{
RSA *rsa = NULL;
char *de = NULL;
int rsa_len = 0;
if ((fp = fopen(prikey_path, "r")) == NULL) {
""""""
RSA_print_fp(stdout, rsa, 0);
rsa_len = RSA_size(rsa);
de = (char *)malloc(rsa_len + 1);
if (RSA_private_ decrypt (rsa_len, (unsigned char *)str, (unsigned char*)de, rsa, RSA_NO_PADDING) return NULL;
int main(int argc, char *argv[])
{
char *en = NULL;
char *de = NULL;
printf("src is: %sn", src);
en = my_encrypt(src, PUBKEY);
printf("enc is: %sn", en);
de= my_decrypt(en, PRIKEY);
printf("dec is: %sn", de);
if (en != NULL) {
free(en);
}
if (de != NULL) {
free(de);
}
return 0;
}
2. PEM/BIGNUM公钥转换示例
#include
#include
#include
#include
/***************************************************** **********************
* RSA PEM/BIGNUM public key conversion function
*
* file: test_rsa_pubkey.c
* gcc -Wall -O2 -o test_rsa_pubkey test_rsa_pubkey .c -lcrypto -lssl
*
* author: tonglulin@gmail.com by
www.qmailer.net
************************************************ ****************************/
const char *n = "C7301B330C4E123E4FA9F54F49121E8CE07974D8BFEF1D39EC9245D573D66E7FAC258F86E2B0816C6BA875F10673E655E6A8DF48DEFDDB655E253ED5A4A0FBAD50D68E91D0459F9F2377BB8CA1583E3F83C06343A5A1177C903F498A6D14015CC975522BE4446CD1EB87E88EF05A863AF0DD7C4D413CF603EDF4893EEC063BE3";
const char *pubkey = "-----BEGIN RSA PUBLIC KEY-----nMIGJAoGBAMcwGzMMThI+T6n1T0kSHozgeXTYv+8dOeySRdVz1m5/rCWPhuKwgWxrnqHXxBnPmVeao30je/dtlXiU+1aSg+61Q1o6R0EWfnyN3u4yhWD4/g8BjQ6WhF3yQnP0mKbRQBXMl1UivkRGzR64fojvBahjrw3XxNQTz2A+30iT7sBjvjAgMBAAE=n-----END RSA PUBLIC KEY-----";
int main(int argc, char *argv[])
{
RSA *rsa = NULL;
BIO *bio = NULL;
BIGNUM *bne = NULL;
BIGNUM *bnn = NULL;
FILE *fp = NULL;
unsigned long e = 65537;
if (argc printf("%s pem|bignum argsn", argv[0]);
return -1;
}
/* 将PEM转换为大数字符串 */
if (strcasecmp(argv[1], "bignum") == 0) {
if (argc == 3) {
/* 从外部文件读 */
fp = fopen(argv[2], "r");
if (fp == NULL) {
return -1;
}
rsa = PEM_read_RSAPublicKey(fp, &rsa, NULL, NULL);
if (rsa == NULL) {
return -1;
}
}
else {
/* 从内存数据读 */
bio = BIO_new(BIO_s_mem());
BIO_puts(bio, pubkey);
rsa = PEM_read_bio_RSAPublicKey(bio, &rsa, NULL, NULL);
if (rsa == NULL) {
return -1;
}
}
RSA_print_fp(stdout, rsa, 0);
printf("%sn", BN_bn2hex(rsa->n));
printf("%sn", BN_bn2hex(rsa->e));
rsa);
}
/* Convert large number string to PEM file*/
else if (strcasecmp(argv[1], "pem") == 0) {
bne = BN_new();
if (bne == NULL) {
return -1;
}
ULL) {
BN_free(bnn);
BN_free( bne);
BN_set_word(bne, e);
BN_hex2bn(&bnn, argv[2]);
PEM_write_RSAPublicKey(stdout, rsa);
RSA_free(rsa);
}
""""""""""""""" """"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""" ;
#include
#include
#include
/***************************************************** ************************
*
* file: test_rsa_genkey.c
*
* author: tonglulin@gmail.com by
www.qmailer.net
************************************************ ****************************/
int main(int argc , char *argv[])
{
/* Generate RSA key*/
RSA *rsa = RSA_generate_key(1024, 65537, NULL, NULL);
printf("PRIKEY:n");
PEM_write_RSAPrivateKey(stdout, rsa, NULL, NULL, 0, NULL, NULL);
/* Extract public key* /
unsigned char *n_b = (unsigned char *)calloc(RSA_size(rsa), sizeof(unsigned char));
int n_size = BN_bn2bin(rsa->n, n_b);
int b_size = BN_bn2bin(rsa->e, e_b);
RSA *pubrsa = RSA_new();
pubrsa->n = BN_bin2bn (n_b, n_size, NULL);
pubrsa->e = BN_bin2bn(e_b, b_size, NULL);
printf("PUBKEY: n");
PEM_write_RSAPublicKey(stdout, pubrsa);
RSA_free(rsa);
RSA_free(pubrsa);
return 0;
}
The above introduces the problem of openssl rsa key format, solves the key format problem of collaborative development of PHP and C++, including aspects of the content, I hope it will be helpful to friends who are interested in PHP tutorials.
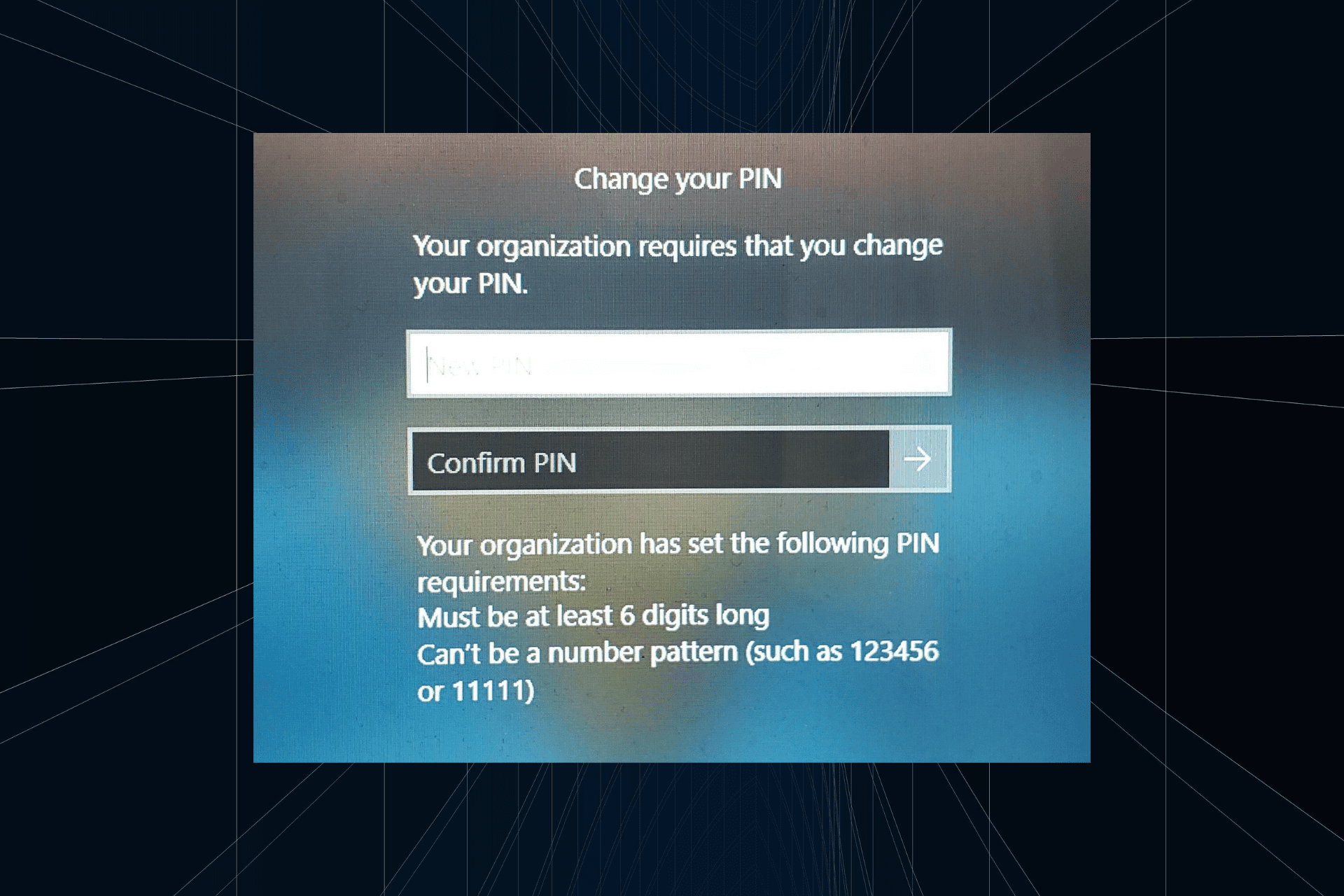 解决方法:您的组织要求您更改 PIN 码Oct 04, 2023 pm 05:45 PM
解决方法:您的组织要求您更改 PIN 码Oct 04, 2023 pm 05:45 PM“你的组织要求你更改PIN消息”将显示在登录屏幕上。当在使用基于组织的帐户设置的电脑上达到PIN过期限制时,就会发生这种情况,在该电脑上,他们可以控制个人设备。但是,如果您使用个人帐户设置了Windows,则理想情况下不应显示错误消息。虽然情况并非总是如此。大多数遇到错误的用户使用个人帐户报告。为什么我的组织要求我在Windows11上更改我的PIN?可能是您的帐户与组织相关联,您的主要方法应该是验证这一点。联系域管理员会有所帮助!此外,配置错误的本地策略设置或不正确的注册表项也可能导致错误。即
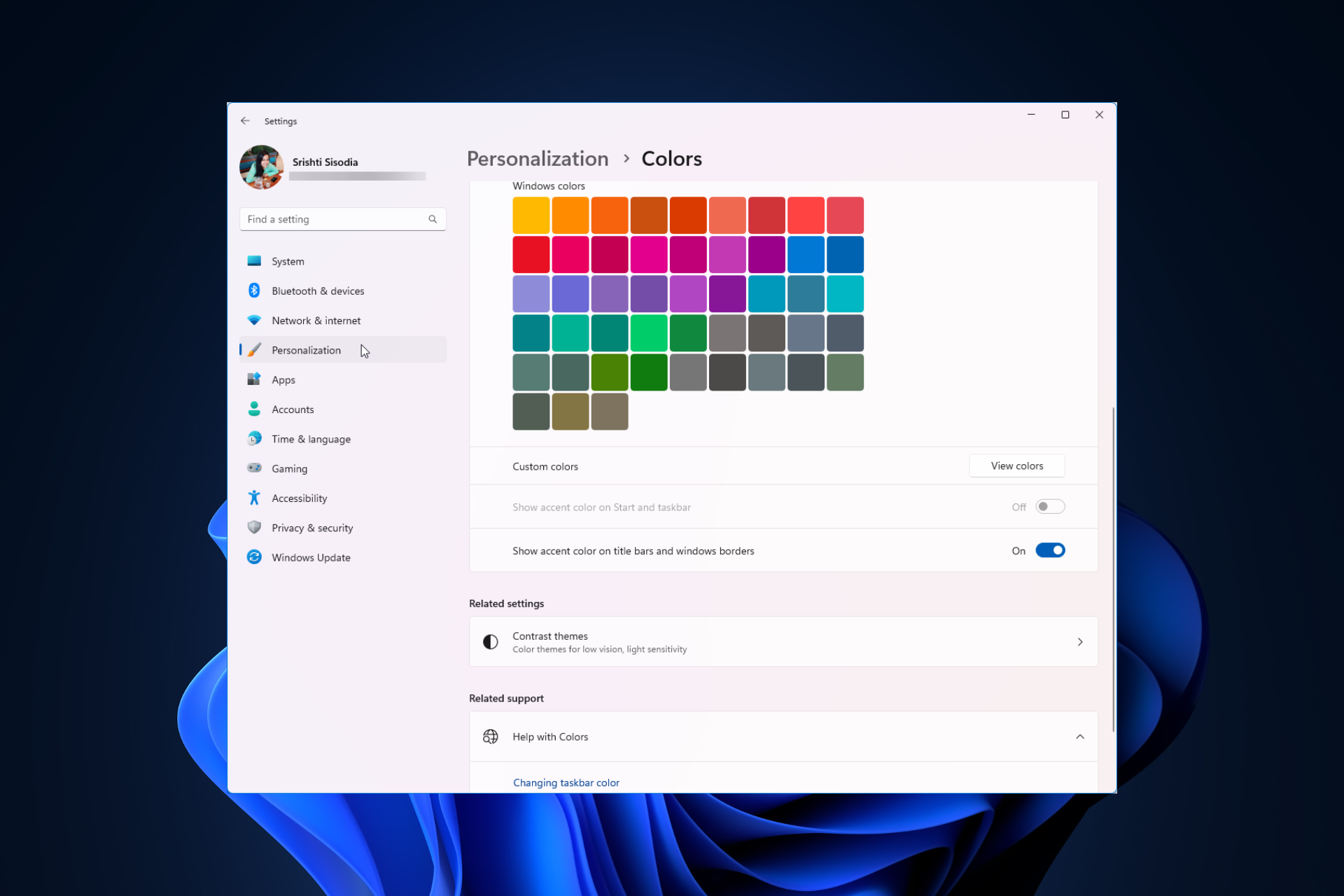 Windows 11 上调整窗口边框设置的方法:更改颜色和大小Sep 22, 2023 am 11:37 AM
Windows 11 上调整窗口边框设置的方法:更改颜色和大小Sep 22, 2023 am 11:37 AMWindows11将清新优雅的设计带到了最前沿;现代界面允许您个性化和更改最精细的细节,例如窗口边框。在本指南中,我们将讨论分步说明,以帮助您在Windows操作系统中创建反映您的风格的环境。如何更改窗口边框设置?按+打开“设置”应用。WindowsI转到个性化,然后单击颜色设置。颜色更改窗口边框设置窗口11“宽度=”643“高度=”500“>找到在标题栏和窗口边框上显示强调色选项,然后切换它旁边的开关。若要在“开始”菜单和任务栏上显示主题色,请打开“在开始”菜单和任务栏上显示主题
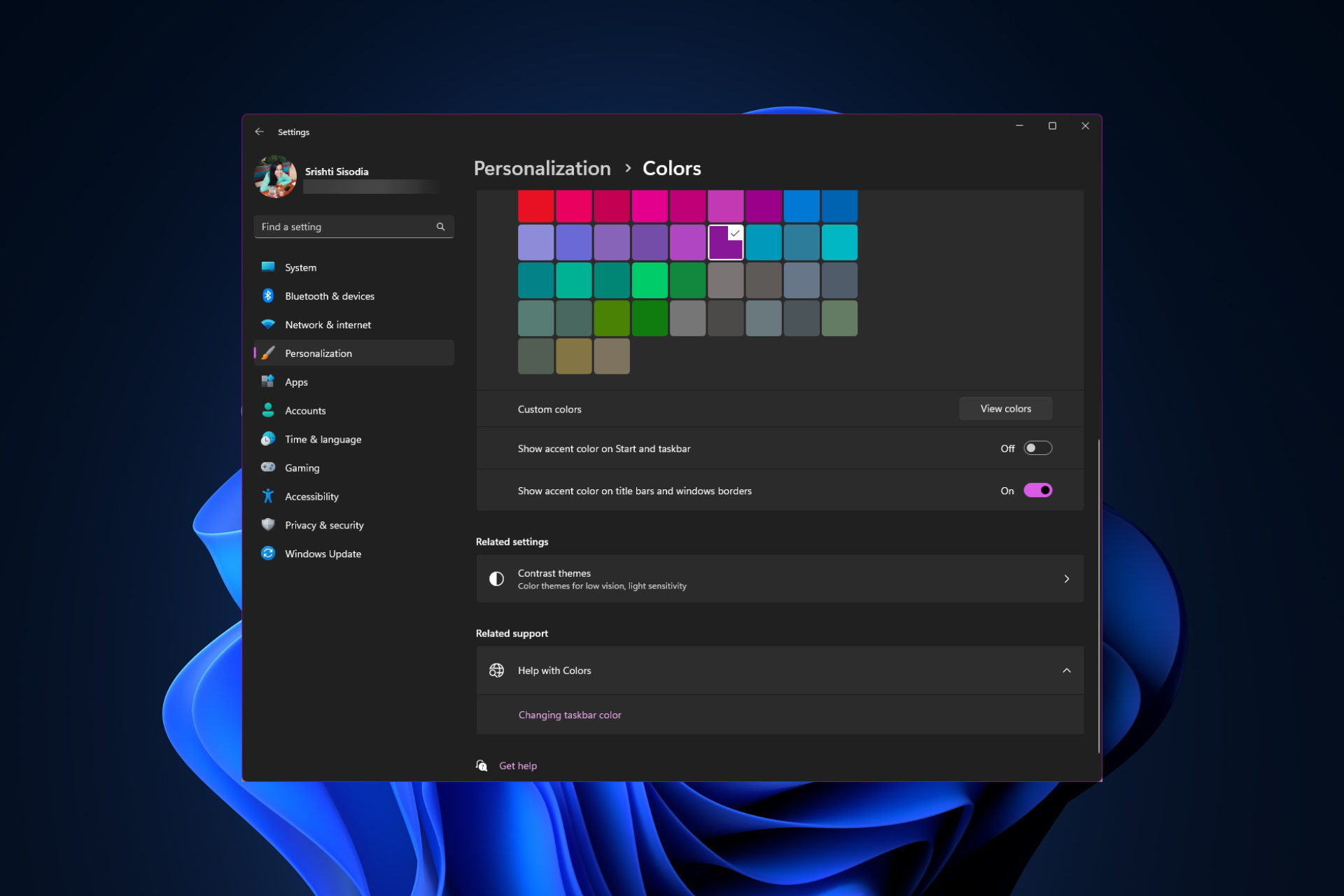 如何在 Windows 11 上更改标题栏颜色?Sep 14, 2023 pm 03:33 PM
如何在 Windows 11 上更改标题栏颜色?Sep 14, 2023 pm 03:33 PM默认情况下,Windows11上的标题栏颜色取决于您选择的深色/浅色主题。但是,您可以将其更改为所需的任何颜色。在本指南中,我们将讨论三种方法的分步说明,以更改它并个性化您的桌面体验,使其具有视觉吸引力。是否可以更改活动和非活动窗口的标题栏颜色?是的,您可以使用“设置”应用更改活动窗口的标题栏颜色,也可以使用注册表编辑器更改非活动窗口的标题栏颜色。若要了解这些步骤,请转到下一部分。如何在Windows11中更改标题栏的颜色?1.使用“设置”应用按+打开设置窗口。WindowsI前往“个性化”,然
 OOBELANGUAGE错误Windows 11 / 10修复中出现问题的问题Jul 16, 2023 pm 03:29 PM
OOBELANGUAGE错误Windows 11 / 10修复中出现问题的问题Jul 16, 2023 pm 03:29 PM您是否在Windows安装程序页面上看到“出现问题”以及“OOBELANGUAGE”语句?Windows的安装有时会因此类错误而停止。OOBE表示开箱即用的体验。正如错误提示所表示的那样,这是与OOBE语言选择相关的问题。没有什么可担心的,你可以通过OOBE屏幕本身的漂亮注册表编辑来解决这个问题。快速修复–1.单击OOBE应用底部的“重试”按钮。这将继续进行该过程,而不会再打嗝。2.使用电源按钮强制关闭系统。系统重新启动后,OOBE应继续。3.断开系统与互联网的连接。在脱机模式下完成OOBE的所
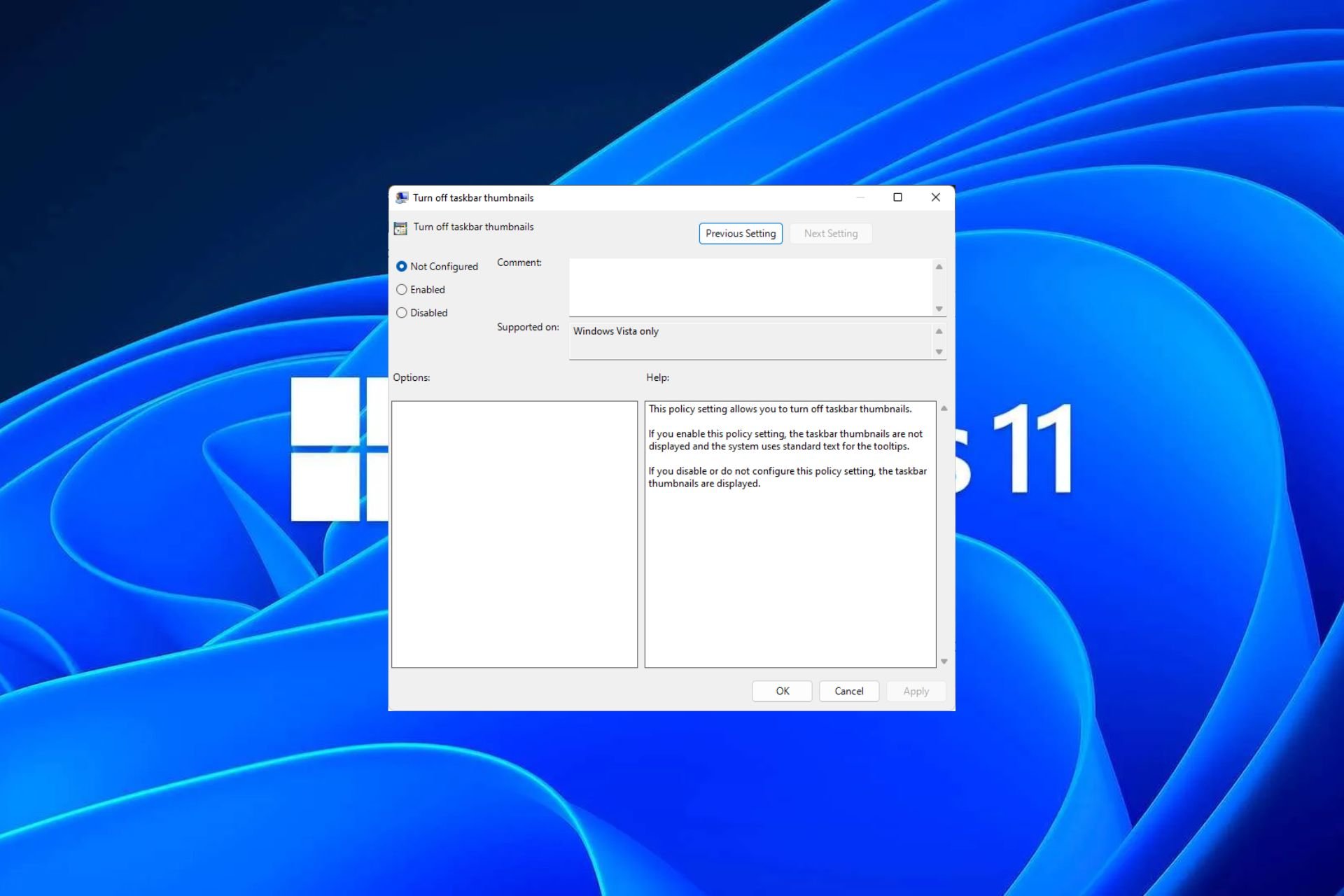 Windows 11 上启用或禁用任务栏缩略图预览的方法Sep 15, 2023 pm 03:57 PM
Windows 11 上启用或禁用任务栏缩略图预览的方法Sep 15, 2023 pm 03:57 PM任务栏缩略图可能很有趣,但它们也可能分散注意力或烦人。考虑到您将鼠标悬停在该区域的频率,您可能无意中关闭了重要窗口几次。另一个缺点是它使用更多的系统资源,因此,如果您一直在寻找一种提高资源效率的方法,我们将向您展示如何禁用它。不过,如果您的硬件规格可以处理它并且您喜欢预览版,则可以启用它。如何在Windows11中启用任务栏缩略图预览?1.使用“设置”应用点击键并单击设置。Windows单击系统,然后选择关于。点击高级系统设置。导航到“高级”选项卡,然后选择“性能”下的“设置”。在“视觉效果”选
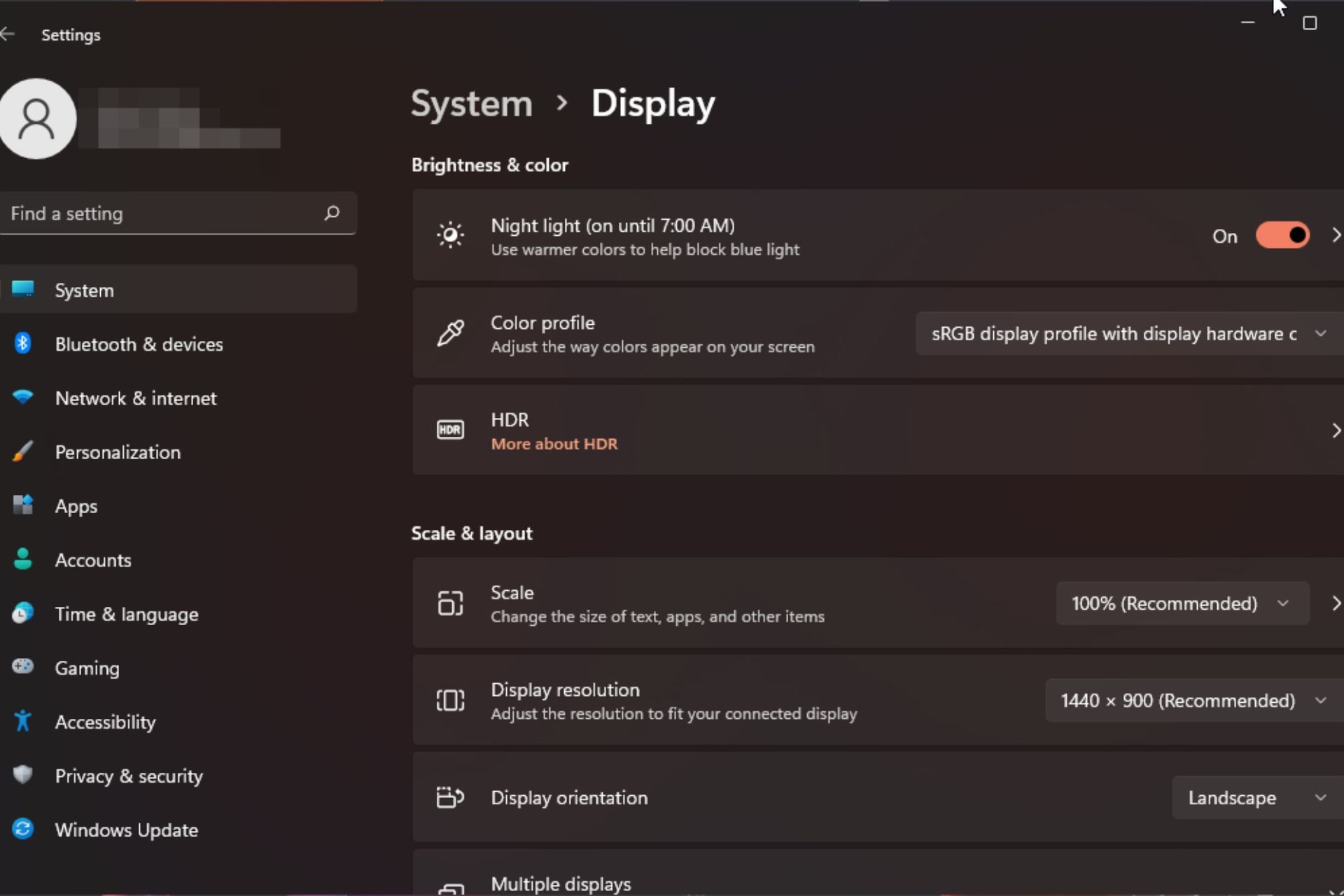 Windows 11 上的显示缩放比例调整指南Sep 19, 2023 pm 06:45 PM
Windows 11 上的显示缩放比例调整指南Sep 19, 2023 pm 06:45 PM在Windows11上的显示缩放方面,我们都有不同的偏好。有些人喜欢大图标,有些人喜欢小图标。但是,我们都同意拥有正确的缩放比例很重要。字体缩放不良或图像过度缩放可能是工作时真正的生产力杀手,因此您需要知道如何对其进行自定义以充分利用系统功能。自定义缩放的优点:对于难以阅读屏幕上的文本的人来说,这是一个有用的功能。它可以帮助您一次在屏幕上查看更多内容。您可以创建仅适用于某些监视器和应用程序的自定义扩展配置文件。可以帮助提高低端硬件的性能。它使您可以更好地控制屏幕上的内容。如何在Windows11
 10种在 Windows 11 上调整亮度的方法Dec 18, 2023 pm 02:21 PM
10种在 Windows 11 上调整亮度的方法Dec 18, 2023 pm 02:21 PM屏幕亮度是使用现代计算设备不可或缺的一部分,尤其是当您长时间注视屏幕时。它可以帮助您减轻眼睛疲劳,提高易读性,并轻松有效地查看内容。但是,根据您的设置,有时很难管理亮度,尤其是在具有新UI更改的Windows11上。如果您在调整亮度时遇到问题,以下是在Windows11上管理亮度的所有方法。如何在Windows11上更改亮度[10种方式解释]单显示器用户可以使用以下方法在Windows11上调整亮度。这包括使用单个显示器的台式机系统以及笔记本电脑。让我们开始吧。方法1:使用操作中心操作中心是访问
 如何在Safari中关闭iPhone的隐私浏览身份验证?Nov 29, 2023 pm 11:21 PM
如何在Safari中关闭iPhone的隐私浏览身份验证?Nov 29, 2023 pm 11:21 PM在iOS17中,Apple为其移动操作系统引入了几项新的隐私和安全功能,其中之一是能够要求对Safari中的隐私浏览选项卡进行二次身份验证。以下是它的工作原理以及如何将其关闭。在运行iOS17或iPadOS17的iPhone或iPad上,如果您在Safari浏览器中打开了任何“无痕浏览”标签页,然后退出会话或App,Apple的浏览器现在需要面容ID/触控ID认证或密码才能再次访问它们。换句话说,如果有人在解锁您的iPhone或iPad时拿到了它,他们仍然无法在不知道您的密码的情况下查看您的隐私


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Dreamweaver Mac version
Visual web development tools

Notepad++7.3.1
Easy-to-use and free code editor

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft





