|
The operational security of the website is definitely an issue that every webmaster must consider. As we all know, most hackers attack websites by using sql injection. This is what we often say ?
The most original static website is the safest. Today we will talk about the security specifications of PHP injection to prevent your website from being injected by sql.
Today’s mainstream website development language is still php, so let’s start with how to prevent sqlinjection in php website:
Phpsecurity precautions for injection Through the above process, we We can understand the principles and methods of phpinjection. Of course, we can also develop corresponding prevention methods:
The first is the security settings of the server. Here are mainly the security settings of php+mysql and Security settings for linux host . To prevent php+mysql injection, first set magic_quotes_gpc to On, display_errs to Off, if the id type, we use intval() to convert it into an integer Type, such as code:
$idintval($id);
mysql_query"*fromexamplewherearticieid'$id'";or write like this: mysql_query("SEL ECT*FROMarticleWHEREarticleid ".intval($id)."")
If it is a character type, use addslashes() to filter it, and then filter "%" and "_" such as:
$searchaddslashes($search);
$searchstr_replace(“_”,”_”,$search);
$searchstr_replace(“%”,”%”,$search);
Of course you can also add php Universal anti-injection code:
/***************************
PHPUniversal anti-injection security code
Instructions:
Determine whether the passed variables contain illegal Characters
such as $_POST, $_GET
Function:
anti-injection
****************** ********/
//Illegal characters to be filtered
$ArrFiltratearray("'",";","union");
// The url to be redirected after an error, If not filled in, the previous page will be defaulted
$StrGoUrl"";
//Whether there is a value in the array
functionFunStringExist($StrFiltrate,$ArrFiltrate){ feach($ArrFiltrateas$key>$value){
if(eregi($value,$StrFiltrate)){
returntrue;
}
}
returnfalse;
}
//merge $_POST and $_GET
if(function_exists(array_merge)){
$ArrPostAndGetarray_merge($HTTP_POST_VARS,$HTTP_GET_VARS);
}else{
feach($HTTP_POST_VARSas$key>$value){
$ ArrPostAndGet[]$value;
}
feach($HTTP_GET_VARSas$key>$value){
$ArrPostAndGet[]$value;
}
}
//Verification starts
feach($ ArrPostAndGetas$key>$value){
if(FunStringExist($value,$ArrFiltrate)){
echo"alert(/"NeeaoPrompt, illegal characters /");";
if(empty($StrGoUrl)){
echo "histy.go(-1) ;";
}else{
echo "window.location/"".$StrGoUrl."/";";
}
exit;
}
}
?>
/* **************************
Save as checkpostget.php
Then add in front of each php file include(“checkpostget.php“);That’s it
*****************************/
In addition, the administrator username and password are md5encrypted, which can effectively prevent the injection of php.
The server and mysql also need to strengthen some security precautions.
For the security settings of the linux server:
encrypt the password, use the "/usr/sbin/authconfig" tool to turn on the shadow function of the password, and encrypt passwd.
Disable access to important files, enter the linux command interface, and enter at the prompt:
#chmod600/etc/inetd.conf//Change the file attributes to 600
#chattr+I /etc /inetd.conf // Ensure that the owner of the file is root
#chattr–I /etc/inetd.conf //Restrict changes to the file
prohibit any user from passing the su command Change to rootuser
Add the following two lines:Auth sufficient /lib/security/pam_rootok.sodebug Auth required /lib/security/pam_whell.sogroupwheel
Delete all special accounts
#userdel lp etc. Delete users
#groupdellp etc. Delete groups
Prohibit unused suid/ sgid program
#find/-typef(-perm-04000 -o–perm-02000)-execls–lg{};
Receive Brothers PHP original video tutorial CD for free, please contact the official website customer service for details:
http://www.lampbrother.net |
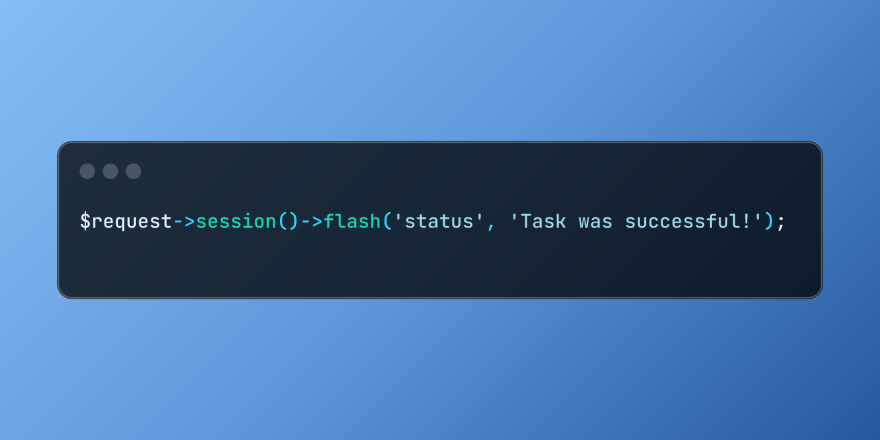 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
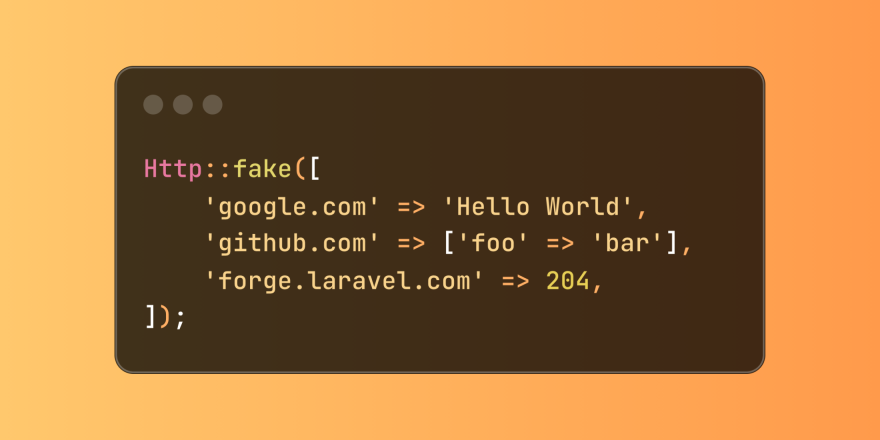 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version






