 Backend Development
Backend Development PHP Tutorial
PHP Tutorial PHP Core Technology and Best Practices Hash Table Conflict_PHP Tutorial
PHP Core Technology and Best Practices Hash Table Conflict_PHP TutorialHash table conflict between PHP core technology and best practices
Hash table conflict between PHP core technology and best practices
Following the previous article, after testing, output value1value2. When
$ht->insert(‘key12’,’value12’);
Echo $ht ->find(‘key12’);,
Found the output value12value12. What is the reason for this?
This problem is called a Hash table conflict. Since the insert is a string, the algorithm used is to add the ASIIC codes of the string. According to this method, a conflict occurs. By printing the Hash values of key12 and key1, we find that they are both 8. In other words, value1 and value12 are stored at the 9th position of the Hash table at the same time (the index starts from 0), so the value of value1 is overwritten by value12. .
Commonly used methods to resolve conflicts are: open addressing method and zipper method. Because zippers are easy to understand, this article uses the zipper method to solve conflict problems.
Zipper method to resolve conflicts:
The approach is to link all key nodes with the same Hash value in the same linked list.
The zipper method connects key nodes with the same hash value in a linked list. Then when looking for elements, you must traverse the linked list and compare whether the keyword of each element in the linked list is equal to the searched keyword. If they are equal, This is the element we are looking for.
Because nodes need to save keywords (key) and data (value), and also record nodes with the same hash value. So create a HashNode class to store this information.
The structure of HashNode is as follows:
<!--?PHP
Class HashNode{
Public $key;
Public $value;
Public $nextNode;
Public function__construct($key,$value,$nextNode = null){
$this --->key = $key;
$this ->value = $value;
$this ->nextNode = $nextNode;
}
}
?>
HashNode has 3 attributes: $key, $value, and $nextNode. $key is the key of the node, $value is the value of the node, and $nextNode is the pointer to the node with the same Hash value. Now modify the insertion method as follows:
Public function insert($key,$value){
$index= $this -> hashfunc($key);
//新建一个节点
if(isset($this->buckets[$index])){
$newNode = new HashNode($key,$value,$this->buckets[$index])
}else{
$newNode = newHashNode($key,$value,null);
}
$this -> buckets[$index] = $newNode;//保存新节点
}
The modified insertion algorithm flow is as follows:
1) Use the Hash function to calculate the Hash value of the keyword, and locate the specified position in the Hash table through the Hash value.
2) If this position is already occupied by other nodes, point the new node's $nextNode to this node, otherwise set the new node's $nextNode to null.
3) Save the new node to the current location of the Hash table.
After these three steps, nodes with the same Hash value will be connected to the same linked list.
The search algorithm is correspondingly modified into the following format:
Public functionfind($key){
$index = $this ->hashfunc($key);
$current =$this->buckets[$index];
while(isset($current)){//遍历当前链表
if($current->key== $key){ //比较当前节点的关键字
return$current -> value;//查找成功
}
$current =$current ->nextNode; //比较下一个节点
}
Return null; //查找失败
}
The modified search algorithm process is as follows:
1) Use the Hash function to calculate the Hash value of the keyword, and locate the specified position in the Hash table through the Hash value.
2) Traverse the current linked list and compare whether the key of each node in the linked list is equal to the search key. If they are equal, the search is successful.
3) If there is no keyword to be found in the entire linked list, the search fails.
After testing, the conflict problem was solved using the zipper method.
 如何在 Windows 11、10 中启用或禁用核心隔离内存完整性Apr 27, 2023 pm 10:43 PM
如何在 Windows 11、10 中启用或禁用核心隔离内存完整性Apr 27, 2023 pm 10:43 PM如今,大多数Windows用户都使用虚拟机。当他们系统上的核心隔离被禁用时,安全风险和攻击是可以预料的。即使设置了核心隔离,如果用户升级了系统,也会禁用内存完整性。如果启用核心隔离,系统将免受攻击。对于经常使用虚拟计算机的人,强烈建议他们启用它。如果您正在寻求有关如何在任何Windows11系统上启用或禁用核心隔离内存完整性的说明,此页面可以提供帮助。如何使用Windows安全应用在Windows11中启用或禁用核心隔离内存完整性第1步:按Windows键并键入Windows安全
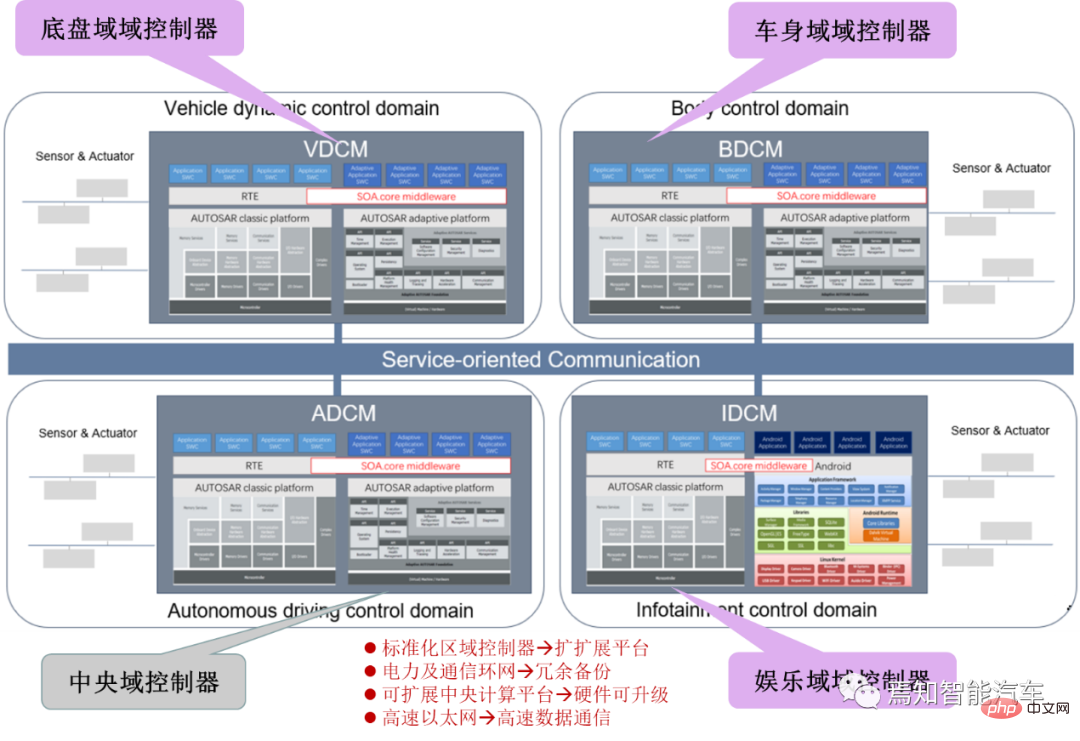 SOA中的软件架构设计及软硬件解耦方法论Apr 08, 2023 pm 11:21 PM
SOA中的软件架构设计及软硬件解耦方法论Apr 08, 2023 pm 11:21 PM对于下一代集中式电子电器架构而言,采用central+zonal 中央计算单元与区域控制器布局已经成为各主机厂或者tier1玩家的必争选项,关于中央计算单元的架构方式,有三种方式:分离SOC、硬件隔离、软件虚拟化。集中式中央计算单元将整合自动驾驶,智能座舱和车辆控制三大域的核心业务功能,标准化的区域控制器主要有三个职责:电力分配、数据服务、区域网关。因此,中央计算单元将会集成一个高吞吐量的以太网交换机。随着整车集成化的程度越来越高,越来越多ECU的功能将会慢慢的被吸收到区域控制器当中。而平台化
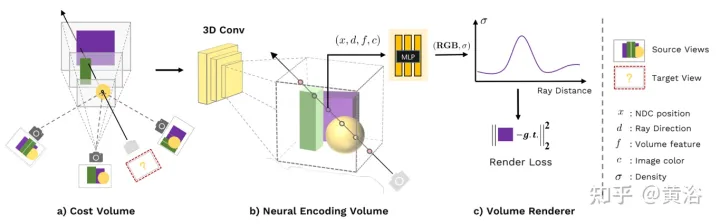 新视角图像生成:讨论基于NeRF的泛化方法Apr 09, 2023 pm 05:31 PM
新视角图像生成:讨论基于NeRF的泛化方法Apr 09, 2023 pm 05:31 PM新视角图像生成(NVS)是计算机视觉的一个应用领域,在1998年SuperBowl的比赛,CMU的RI曾展示过给定多摄像头立体视觉(MVS)的NVS,当时这个技术曾转让给美国一家体育电视台,但最终没有商业化;英国BBC广播公司为此做过研发投入,但是没有真正产品化。在基于图像渲染(IBR)领域,NVS应用有一个分支,即基于深度图像的渲染(DBIR)。另外,在2010年曾很火的3D TV,也是需要从单目视频中得到双目立体,但是由于技术的不成熟,最终没有流行起来。当时基于机器学习的方法已经开始研究,比
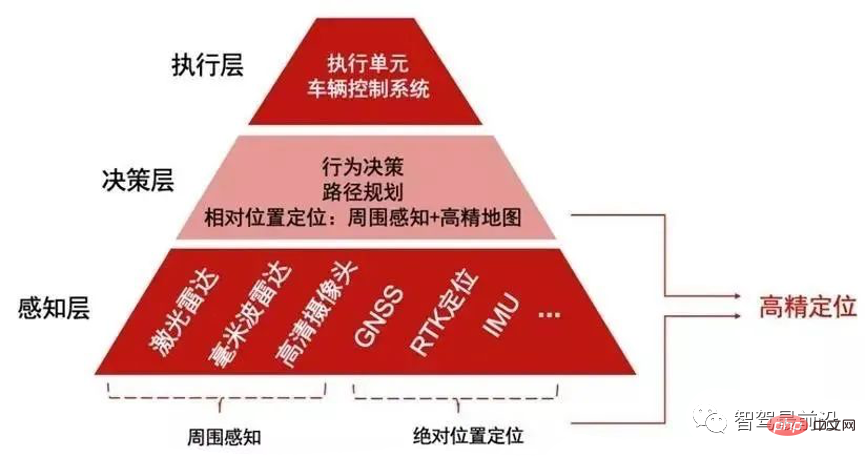 如何让自动驾驶汽车“认得路”Apr 09, 2023 pm 01:41 PM
如何让自动驾驶汽车“认得路”Apr 09, 2023 pm 01:41 PM与人类行走一样,自动驾驶汽车想要完成出行过程也需要有独立思考,可以对交通环境进行判断、决策的能力。随着高级辅助驾驶系统技术的提升,驾驶员驾驶汽车的安全性不断提高,驾驶员参与驾驶决策的程度也逐渐降低,自动驾驶离我们越来越近。自动驾驶汽车又称为无人驾驶车,其本质就是高智能机器人,可以仅需要驾驶员辅助或完全不需要驾驶员操作即可完成出行行为的高智能机器人。自动驾驶主要通过感知层、决策层及执行层来实现,作为自动化载具,自动驾驶汽车可以通过加装的雷达(毫米波雷达、激光雷达)、车载摄像头、全球导航卫星系统(G
 多无人机协同3D打印盖房子,研究登上Nature封面Apr 09, 2023 am 11:51 AM
多无人机协同3D打印盖房子,研究登上Nature封面Apr 09, 2023 am 11:51 AM我们经常可以看到蜜蜂、蚂蚁等各种动物忙碌地筑巢。经过自然选择,它们的工作效率高到叹为观止这些动物的分工合作能力已经「传给」了无人机,来自英国帝国理工学院的一项研究向我们展示了未来的方向,就像这样:无人机 3D 打灰:本周三,这一研究成果登上了《自然》封面。论文地址:https://www.nature.com/articles/s41586-022-04988-4为了展示无人机的能力,研究人员使用泡沫和一种特殊的轻质水泥材料,建造了高度从 0.18 米到 2.05 米不等的结构。与预想的原始蓝图
 苹果M3 Ultra推出全新版本,新增32个CPU核心和80个GPU核心Nov 13, 2023 pm 11:13 PM
苹果M3 Ultra推出全新版本,新增32个CPU核心和80个GPU核心Nov 13, 2023 pm 11:13 PM这款芯片可能会搭载高达80个GPU核心,进而成为M3系列中性能最强大的产品。Max两倍核心数量从M1与M2系列的发展模式来看,苹果的「Ultra」版芯片基本上是「Max」版本的两倍核心数量,这是因为苹果实际上将两颗Max芯片透过内部连接技术结合起来,形成了M1Ultra与M2Ultra。80个GPU核心M3Ultra可能拥有「高达80个图形处理核心」。这一预测基于苹果芯片的发展路径:从基础版到「Pro」版,再到图形核心数量翻倍的「Max」版,以及CPU和GPU核心都翻倍的「Ultra」版。举例来
 超逼真渲染!虚幻引擎技术大牛解读全局光照系统LumenApr 08, 2023 pm 10:21 PM
超逼真渲染!虚幻引擎技术大牛解读全局光照系统LumenApr 08, 2023 pm 10:21 PM实时全局光照(Real-time GI)一直是计算机图形学的圣杯。多年来,业界也提出多种方法来解决这个问题。常用的方法包通过利用某些假设来约束问题域,比如静态几何,粗糙的场景表示或者追踪粗糙探针,以及在两者之间插值照明。在虚幻引擎中,全局光照和反射系统Lumen这一技术便是由Krzysztof Narkowicz和Daniel Wright一起创立的。目标是构建一个与前人不同的方案,能够实现统一照明,以及类似烘烤一样的照明质量。近期,在SIGGRAPH 2022上,Krzysztof Narko
 internet的基本结构与技术起源于什么Dec 15, 2020 pm 04:48 PM
internet的基本结构与技术起源于什么Dec 15, 2020 pm 04:48 PMinternet的基本结构与技术起源于ARPANET。ARPANET是计算机网络技术发展中的一个里程碑,它的研究成果对促进网络技术的发展起到了重要的作用,并未internet的形成奠定了基础。arpanet(阿帕网)为美国国防部高级研究计划署开发的世界上第一个运营的封包交换网络,它是全球互联网的始祖。


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 English version
Recommended: Win version, supports code prompts!

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools





