Leak Monitor
When leaving http://script.aculo.us/
This is probably my most common leak prototype.js, line 74:3
A serious leak, two windows popped up at once (pay attention to the scroll bar!).
This is even more outrageous. Every time I finish writing Word press, it will appear!
Visit general sites and you will find that most sites will have this kind of problem. Indeed, it can be a bit of a shock if some websites have not gone through such testing - a few minor changes could have ensured that this problem would not occur.
Although this website (Jack'sBlog, examples) is all JavaScript, you don't have to worry about any risk of leakage.
Here are three simple steps:
1. When you are done, set your XMLHttpRequest onreadystatechange handlers to null,
I use YAHOO.util.Connect for XHR linking because it uses polling mechanism instead of readstate, so I don't have to set null manually. I recommend that you, where possible, use YAHOO.util.Connect (or YAHOO.ext.UpdateManager built on top of it).
2. Clear all DOM event handlers objects in the unload event, if they have a chance to reference (Refence).
If you can ask Library to do it, don’t do it your own way! For the event mechanism, I use YAHOO.util.Event to handle it. Other libraries (prototype, dojo, etc) also have their own corresponding mechanisms to handle it. --Though I don't know how efficiently they go there. If you look at the screenshot above carefully, you will find that the leaked code above will be associated with these libraries (use facts to prove the source of the accident, Frank's note)
3. In addition to some basic types of data primitive value (String , Number), never put anything else in the DOM expando or property. Of course, there is an exception if you can ensure that you clear it in time.
This is the most important golden rule. You may find it convenient to put something in the DOM expando, and then use $() to get it, but never do this. Really, I know what you are thinking. Now I have admitted to being wired and paranoid. Yes, JS objects are put into DOM expando on many occasions, and nothing happens, but there are many. . . . This situation is not easy to detect! (For example: closure closure). So to avoid any possible occurrence, I will only follow this rule.
It’s not too difficult to solve this problem. It requires no skills or experience. As long as you pay attention to the above points, a novice novice will also know how to avoid leaks.
Please please take some time and effort from some of the big sites (including the new Yahoo Mail!?!?) to allow me (or others) to browse your pages without suffering memory leaks.
 Replace String Characters in JavaScriptMar 11, 2025 am 12:07 AM
Replace String Characters in JavaScriptMar 11, 2025 am 12:07 AMDetailed explanation of JavaScript string replacement method and FAQ This article will explore two ways to replace string characters in JavaScript: internal JavaScript code and internal HTML for web pages. Replace string inside JavaScript code The most direct way is to use the replace() method: str = str.replace("find","replace"); This method replaces only the first match. To replace all matches, use a regular expression and add the global flag g: str = str.replace(/fi
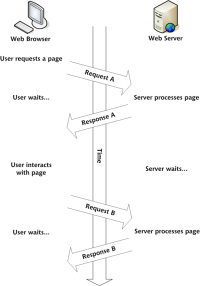 Build Your Own AJAX Web ApplicationsMar 09, 2025 am 12:11 AM
Build Your Own AJAX Web ApplicationsMar 09, 2025 am 12:11 AMSo here you are, ready to learn all about this thing called AJAX. But, what exactly is it? The term AJAX refers to a loose grouping of technologies that are used to create dynamic, interactive web content. The term AJAX, originally coined by Jesse J
 10 jQuery Fun and Games PluginsMar 08, 2025 am 12:42 AM
10 jQuery Fun and Games PluginsMar 08, 2025 am 12:42 AM10 fun jQuery game plugins to make your website more attractive and enhance user stickiness! While Flash is still the best software for developing casual web games, jQuery can also create surprising effects, and while not comparable to pure action Flash games, in some cases you can also have unexpected fun in your browser. jQuery tic toe game The "Hello world" of game programming now has a jQuery version. Source code jQuery Crazy Word Composition Game This is a fill-in-the-blank game, and it can produce some weird results due to not knowing the context of the word. Source code jQuery mine sweeping game
 How do I create and publish my own JavaScript libraries?Mar 18, 2025 pm 03:12 PM
How do I create and publish my own JavaScript libraries?Mar 18, 2025 pm 03:12 PMArticle discusses creating, publishing, and maintaining JavaScript libraries, focusing on planning, development, testing, documentation, and promotion strategies.
 jQuery Parallax Tutorial - Animated Header BackgroundMar 08, 2025 am 12:39 AM
jQuery Parallax Tutorial - Animated Header BackgroundMar 08, 2025 am 12:39 AMThis tutorial demonstrates how to create a captivating parallax background effect using jQuery. We'll build a header banner with layered images that create a stunning visual depth. The updated plugin works with jQuery 1.6.4 and later. Download the
 How do I optimize JavaScript code for performance in the browser?Mar 18, 2025 pm 03:14 PM
How do I optimize JavaScript code for performance in the browser?Mar 18, 2025 pm 03:14 PMThe article discusses strategies for optimizing JavaScript performance in browsers, focusing on reducing execution time and minimizing impact on page load speed.
 Getting Started With Matter.js: IntroductionMar 08, 2025 am 12:53 AM
Getting Started With Matter.js: IntroductionMar 08, 2025 am 12:53 AMMatter.js is a 2D rigid body physics engine written in JavaScript. This library can help you easily simulate 2D physics in your browser. It provides many features, such as the ability to create rigid bodies and assign physical properties such as mass, area, or density. You can also simulate different types of collisions and forces, such as gravity friction. Matter.js supports all mainstream browsers. Additionally, it is suitable for mobile devices as it detects touches and is responsive. All of these features make it worth your time to learn how to use the engine, as this makes it easy to create a physics-based 2D game or simulation. In this tutorial, I will cover the basics of this library, including its installation and usage, and provide a
 Auto Refresh Div Content Using jQuery and AJAXMar 08, 2025 am 12:58 AM
Auto Refresh Div Content Using jQuery and AJAXMar 08, 2025 am 12:58 AMThis article demonstrates how to automatically refresh a div's content every 5 seconds using jQuery and AJAX. The example fetches and displays the latest blog posts from an RSS feed, along with the last refresh timestamp. A loading image is optiona


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Dreamweaver CS6
Visual web development tools

WebStorm Mac version
Useful JavaScript development tools

Zend Studio 13.0.1
Powerful PHP integrated development environment

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.








