 web3.0
web3.0 How to apply for Huobi Huobi API interface_Detailed explanation of Huobi Huobi API interface application process
How to apply for Huobi Huobi API interface_Detailed explanation of Huobi Huobi API interface application processHow to apply for Huobi Huobi API interface_Detailed explanation of Huobi Huobi API interface application process
Applying for the Huobi API interface requires six steps: 1. Register a Huobi account and select "Global Station"; 2. Complete real-name authentication (L1/L2/L3); 3. Log in and enter the API management page; 4. Create an API key, fill in basic information and select permissions; 5. Generate and save Access Key and Secret Key; 6. Integrate API to the application, pay attention to security matters and change the key regularly.

1. Account registration and real-name authentication
- Register a hot account
Visit the official website of Huobi (for example), click the "Register" button, and use your email address or mobile phone number to complete the registration 19 . If you need to use advanced features, it is recommended to select the Global Site account. - Complete real-name authentication
After logging in, enter "Personal Center" and select "Identity Authentication". Upload the ID card (such as ID card, passport) and address certificate (such as water and electricity bill) according to the prompts, and complete the L1 basic authentication or L2 primary authentication 21 22 . Some permissions (such as withdrawal of coins) require advanced authentication (L3) and require facial recognition and more information review.
2. Enter the API management page
- Log in and access API management
After logging in to your account, click the "Account" icon in the upper right corner of the page and select "API Management" (some interfaces are displayed as "API Key" or "API Settings"). If you access it for the first time, you need to read and agree to the API usage protocol.
3. Create API key
-
Fill in API basic information
- API name : Name the key (such as "quantitative trading robot") to facilitate the distinction between uses.
- IP binding : It is recommended to fill in the IP address that is allowed to access (multiple IPs are separated by English commas) to improve security. All IP access is allowed if left blank (not recommended).
-
Select permission configuration
- Read permission : Only query account balance, market data, etc.
- Trading permissions : Allow orders, withdrawals and other operations, and require prudent authorization.
- Withdrawal permission : Allow withdrawal through API, which is a high-risk permission. It is recommended to enable it only if necessary and set a whitelist of withdrawal addresses.
- Other permissions : Check transfer, loan, contract and other functions according to your needs.
- Security Verification
Before submission, you must complete the secondary verification through the SMS verification code or Google Authenticator to ensure the identity of the operator.
4. Obtain and save the API key
- Generate a key pair
After verification is passed, the system generates Access Key and Secret Key . The key is displayed only once and needs to be copied and saved immediately to a secure location (such as the Encryption Password Manager) to avoid leakage. - View and manage keys
On the API Management page, you can view the created key list, which supports editing permissions, modifying IP bindings, or deleting discarded keys .
5. Configuring and using API
Fill in the obtained key into the development environment (such as Python, Java, etc.), and the sample code is as follows (Python):
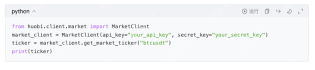
-
Safety precautions
- Regularly replace the key : It is recommended to replace it every 3-6 months to reduce the risk of leakage 9 .
- Limit permission scope : Follow the principle of minimum permissions and only necessary functions are opened 69 .
- Monitor usage log : View call records on the API management page and discover abnormal behaviors in a timely manner 9 .
6. Permission upgrade and audit
- Complete L2 or L3 real-name authentication.
- The account has no violation records and the funds flow is normal .
- After submitting the upgrade application, wait for platform review (usually 1-3 working days).
Frequently Asked Questions
- What to do if you forget Secret Key?
The existing key needs to be deleted and regenerated, and the old key will be invalid. - What is the API request frequency limit?
Different permission levels are different. Normal permissions are usually 5-20 times/second, and advanced permissions can be applied for promotion. - How to apply for a business account?
Enterprise qualifications (such as business licenses, legal person identity certificates) must be submitted through the Huobi Open Platform, and exclusive permissions must be assigned after the review is approved.
The above is the detailed content of How to apply for Huobi Huobi API interface_Detailed explanation of Huobi Huobi API interface application process. For more information, please follow other related articles on the PHP Chinese website!
 Top 10 Virtual Currency Trading Platforms Ranking Top 10 Virtual Currency Trading Platform AppsMay 15, 2025 pm 06:39 PM
Top 10 Virtual Currency Trading Platforms Ranking Top 10 Virtual Currency Trading Platform AppsMay 15, 2025 pm 06:39 PMTop 10 virtual currency trading platforms rankings: 1. OKX, 2. Binance, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bitfinex, 7. Bittrex, 8. Poloniex, 9. Gemini, 10. KuCoin. These platforms all provide a variety of digital asset trading services, support spot, futures and leveraged trading, and provide staking and lending services. The user interface is simple and mobile application functions are powerful.
 Top 10 digital currency exchange app rankings Latest top 10 digital currency exchange rankingsMay 15, 2025 pm 06:36 PM
Top 10 digital currency exchange app rankings Latest top 10 digital currency exchange rankingsMay 15, 2025 pm 06:36 PMTop 10 digital currency exchange app rankings: 1. Binance, 2. OKX, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bittrex, 7. Bitfinex, 8. KuCoin, 9. Gemini, 10. Poloniex, these exchanges have their own characteristics, providing a wealth of trading options and powerful security measures, suitable for users of different levels of use.
 The latest ranking of the top ten virtual currency trading platforms, the latest ranking of the top ten currency exchange appsMay 15, 2025 pm 06:33 PM
The latest ranking of the top ten virtual currency trading platforms, the latest ranking of the top ten currency exchange appsMay 15, 2025 pm 06:33 PMThe latest ranking of the top ten virtual currency trading platforms: 1. Binance, 2. OKX, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bitfinex, 7. Bybit, 8. KuCoin, 9. FTX, 10. Gemini, these platforms perform well in user experience, security, trading volume and supported currencies, and are suitable for traders of different levels.
 Top 10 Currency Exchange App Latest Rankings of Top 10 Cryptocurrency ExchangesMay 15, 2025 pm 06:30 PM
Top 10 Currency Exchange App Latest Rankings of Top 10 Cryptocurrency ExchangesMay 15, 2025 pm 06:30 PMTop 10 currency exchange apps: 1. Binance, 2. OKX, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bybit, 7. KuCoin, 8. Bitfinex, 9. Gemini, 10. Bitstamp, these platforms are highly regarded for their advantages in user experience, security and transaction volume.
 Ranking of the top ten cryptocurrency exchanges Apps Ranking of the top ten cryptocurrency exchangesMay 15, 2025 pm 06:27 PM
Ranking of the top ten cryptocurrency exchanges Apps Ranking of the top ten cryptocurrency exchangesMay 15, 2025 pm 06:27 PMThe top ten cryptocurrency exchanges are: 1. Binance, 2. OKX, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bittrex, 7. Bitfinex, 8. KuCoin, 9. Gemini, 10. Bybit, these exchanges are highly regarded for their high trading volume, diverse trading products, user-friendly interfaces and strict security measures.
 Top 10 virtual currency trading platforms rankings Top 10 virtual currency exchange appsMay 15, 2025 pm 06:24 PM
Top 10 virtual currency trading platforms rankings Top 10 virtual currency exchange appsMay 15, 2025 pm 06:24 PMTop 10 virtual currency trading platforms rankings: 1. OKX, 2. Binance, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bitfinex, 7. Bittrex, 8. Poloniex, 9. Gemini, 10. KuCoin. These platforms all provide a variety of digital asset trading services, support spot, futures and leveraged trading, and provide staking and lending services. The user interface is simple and mobile application functions are powerful.
 The latest ranking of the top ten digital currency exchange apps The latest ranking of the top ten digital currency exchange appsMay 15, 2025 pm 06:21 PM
The latest ranking of the top ten digital currency exchange apps The latest ranking of the top ten digital currency exchange appsMay 15, 2025 pm 06:21 PMThe top ten digital currency exchange apps are: 1. Binance, 2. OKX, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bittrex, 7. Bitfinex, 8. KuCoin, 9. Gemini, 10. Poloniex. These exchanges have their own characteristics, providing rich trading options and powerful security measures, suitable for users of different levels of use.
 Top 10 digital currency trading platform app rankings Ranking of the latest top 10 digital currency trading platform appsMay 15, 2025 pm 06:18 PM
Top 10 digital currency trading platform app rankings Ranking of the latest top 10 digital currency trading platform appsMay 15, 2025 pm 06:18 PMTop 10 digital currency trading platforms app rankings: 1. Binance, 2. OKX, 3. Huobi, 4. Coinbase, 5. Kraken, 6. Bitfinex, 7. Bybit, 8. KuCoin, 9. FTX, 10. Gemini, these platforms perform well in user experience, security, trading volume and supported currencies, and are suitable for traders of different levels.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

WebStorm Mac version
Useful JavaScript development tools

Atom editor mac version download
The most popular open source editor

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software








