RSA Conference 2025: Artificial intelligence empowers network security, opportunities and challenges coexist

This article will review RSA Conference 2025 to explore the transformative power and challenges of using autonomous artificial intelligence in cybersecurity protection suites. In addition, I will highlight some announcements that I think are worth watching and share Six Five Media video conversations with Cisco and Cohesity that explore several important topics related to modern artificial intelligence. Let's get started.
Autonomous Artificial Intelligence: Prospects and Challenges
Many experts (myself included) talk about the duality between AI security and secure AI. In other words, it is necessary to protect the use of AI applications and workloads, but also to leverage the power of AI to reduce analyst workload and strengthen cyber defense. Given that the RSA Conference has paid close attention to autonomous artificial intelligence and its potential to enhance network security this year, two points are very obvious.
First, solutions providers that avoid AI hype, listen carefully to customer needs and educate in the short term will benefit from becoming trusted consultants – and earning business returns in the long term. Second, a thorough transformation of identity access management is needed to manage the authority, delegation, and hierarchy of agents and super agents. Companies that are the first to solve this complex problem will benefit greatly.
The pace of modern AI applications is developing excitingly and has great potential to turn their advantages to defenders. Artificial intelligence is definitely a double-edged sword, but autonomous AI coupled with automation is expected to effectively combat bad actors’ current use of generative AI to significantly improve phishing and lateral mobility solutions.
RSA Conference Announcement Key points and Insights
As in previous years, RSA Conference 2025 provides a platform for announcements from many cybersecurity infrastructure providers. Four of these announcements seem particularly eye-catching to me:
Cisco - Cisco announced new features related to its XDR platform, including instant attack verification, improved forensics and a storyboard feature that makes it clearer to visualize complex attack chains. I like the maturity of the company's endpoint protection suite, and I think there is a lot of promise for additional enhancements to supply chains and industrial IoT threat defense. Additionally, in my opinion, Cisco's acquisition of Robust Intelligence is probably one of its most successful acquisitions in recent years. It provides the company’s artificial intelligence defense platform with automated red team capabilities and supports the newly launched Foundation AI open source inference model designed for enhanced security applications.
HP Enterprise – HPE announced enhanced network access control capabilities, OpsRamp integration for finer network observability and new SSE mesh connectivity – all aimed at increasing reliability, ensuring resilience and enhancing security. I love the deeper automation and dynamic routing capabilities designed to simplify networking and secure operations. However, HPE has the opportunity to use its HP Labs research team to dig deeper into security issues and provide threat intelligence research similar to Cisco Talos.
Microsoft — On Sunday before the official opening of the RSA conference, I attended Microsoft’s Preparation Day event the following year and met with executives during the event. I'm still impressed by the company's continued focus on its security future initiative . Microsoft claims it now has more than 34,000 engineers working on cybersecurity application improvement and innovation. This level of investment in technology resources is incredible and reflects the company's commitment to safety. Speaking with a handful of smaller security solutions providers, I also learned that Microsoft Defender is benefiting from the company’s security focus, making significant progress in its ability to provide AI workload alerts, endpoint protection and network repair.
Palo Alto Networks — Palo Alto Networks’ activities at the RSA conference are very important. This includes its announcement of its intention to acquire Protect AI to further achieve its modern AI security goals, as well as enhancements to its AI Cortex risk management and email security. The company also witnessed increasing adoption of its secure enterprise browser, which provides layered protection. My conversations with executives also made it clear that Prisma AIRS is one of the most anticipated suite of cybersecurity solutions in the company's history; it includes model scanning, situation management, AI red team, runtime security, and proxy security. I can understand Palo Alto Networks’ enthusiasm because I believe the company has one of the broadest and most in-depth AI security suites.
Deeply discuss conversations with Cisco and Cohesity
At this year's RSA conference, I had the opportunity to conduct a Six Five Media video interview with Cisco and Cohesity. The first interview was with Cisco's Tom Gillis , who leads the company's database infrastructure and security operations. We discussed the company’s announcement at the RSA conference, as well as Gillis’ vision for autonomous AI integration and its potential impact on driving improved security outcomes.
The second interview was with Vasu Murthy , who led all of Cohesity’s product development efforts. We discuss the company's new RecoveryAgent, which incorporates intellectual property rights acquired by its Veritas, and Murthy's long-term vision for the product portfolio, and how Cohesity can use technologies such as zero-trust security architecture, enhanced multi-factor authentication, machine learning-based ransomware detection to protect more than 100 exobes of enterprise data around the world.
Companies worth paying attention to
At the RSA conference, I also had the opportunity to spend time with some companies, including Forescout, InfoSec Global and Swissbit. Forescout provides cyber risk, compliance and threat mitigation capabilities through asset intelligence, continuous assessment and continuous control in IT and OT environments. I love that the company adopts an open platform that integrates with over 100 security and IT products. Forescout Research – Vedere Labs also provides in-depth device intelligence and organizes its unique telemetry data and other threat intelligence sources to enrich its platform.
As a pioneer and leader in crypto situation management, InfoSec Global aims to protect enterprise digital infrastructure by enabling organizations to discover, count, repair and manage crypto assets. Its AgileSec platform coordinates agile encryption management in cloud and on-premises environments through centralized policy execution—even during the transition from traditional encryption to post-quantum encryption. The company told me that global financial institutions, large tech companies and government agencies rely on their own capabilities and integration with third parties to ensure compliance, enhance resilience and achieve post-quantum readiness. Encryption situation management is still in its infancy, but the future risks associated with using quantum computing to crack encryption are undoubtedly worthy of careful study.
Swissbit is a security solution provider that combines its advantages in flash memory and embedded IoT device design, enabling digital authentication and physical access control. Swissbit iShield Key offers these features in the form of a simple and flexible USB key that can proactively protect users from cyber attacks such as phishing, social engineering, and account takeover. Its latest product iteration, iShield Key 2, is the first FIDO security key to obtain FIPS 140-3 Level 3 certification, ensuring enhanced security for demanding applications. I like its flexibility, similar to the Swiss Army Knife (pun), which can solve many use cases including badge access, device authentication and more.
The power of the platform
Overall, cybersecurity solution providers are double the focus on the power of the platform to provide easy-to-manage and enhanced security measures. The surge in tools is unsustainable, especially when bad actors exploit generative AI and ultimately exploit autonomous AI to attack organizations. The platform approach can provide a higher level of value and improved protection in large part through a suite of solutions that work better together. In my opinion, RSA Conference 2025 has largely proved the value of a security platform, and although the hype cycle is now totally focused on autonomous AI, it does have huge long-term prospects.
The above is the detailed content of RSA Conference 2025 Highlights, Insights And Companies To Watch. For more information, please follow other related articles on the PHP Chinese website!
 Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AM
Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AMCyberattacks are evolving. Gone are the days of generic phishing emails. The future of cybercrime is hyper-personalized, leveraging readily available online data and AI to craft highly targeted attacks. Imagine a scammer who knows your job, your f
 Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AM
Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AMIn his inaugural address to the College of Cardinals, Chicago-born Robert Francis Prevost, the newly elected Pope Leo XIV, discussed the influence of his namesake, Pope Leo XIII, whose papacy (1878-1903) coincided with the dawn of the automobile and
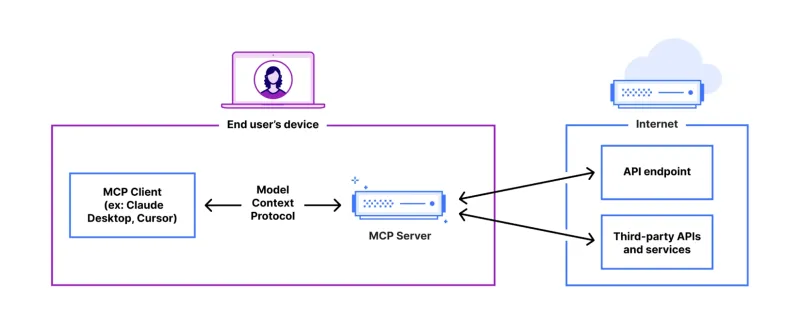 FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AM
FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AMThis tutorial demonstrates how to integrate your Large Language Model (LLM) with external tools using the Model Context Protocol (MCP) and FastAPI. We'll build a simple web application using FastAPI and convert it into an MCP server, enabling your L
 Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AM
Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AMExplore Dia-1.6B: A groundbreaking text-to-speech model developed by two undergraduates with zero funding! This 1.6 billion parameter model generates remarkably realistic speech, including nonverbal cues like laughter and sneezes. This article guide
 3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AM
3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AMI wholeheartedly agree. My success is inextricably linked to the guidance of my mentors. Their insights, particularly regarding business management, formed the bedrock of my beliefs and practices. This experience underscores my commitment to mentor
 AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AM
AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AMAI Enhanced Mining Equipment The mining operation environment is harsh and dangerous. Artificial intelligence systems help improve overall efficiency and security by removing humans from the most dangerous environments and enhancing human capabilities. Artificial intelligence is increasingly used to power autonomous trucks, drills and loaders used in mining operations. These AI-powered vehicles can operate accurately in hazardous environments, thereby increasing safety and productivity. Some companies have developed autonomous mining vehicles for large-scale mining operations. Equipment operating in challenging environments requires ongoing maintenance. However, maintenance can keep critical devices offline and consume resources. More precise maintenance means increased uptime for expensive and necessary equipment and significant cost savings. AI-driven
 Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AM
Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AMMarc Benioff, Salesforce CEO, predicts a monumental workplace revolution driven by AI agents, a transformation already underway within Salesforce and its client base. He envisions a shift from traditional markets to a vastly larger market focused on
 AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AM
AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AMThe Rise of AI in HR: Navigating a Workforce with Robot Colleagues The integration of AI into human resources (HR) is no longer a futuristic concept; it's rapidly becoming the new reality. This shift impacts both HR professionals and employees, dem


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 Linux new version
SublimeText3 Linux latest version

WebStorm Mac version
Useful JavaScript development tools






