
HiddenLayer's groundbreaking research exposes a critical vulnerability in leading Large Language Models (LLMs). Their findings reveal a universal bypass technique, dubbed "Policy Puppetry," capable of circumventing nearly all major LLMs' safety protocols, regardless of their vendor, architecture, or training. This deceptively simple prompt injection method reframes malicious requests as legitimate system instructions, effectively disabling built-in safeguards.
A Universal Bypass
Unlike previous attacks targeting specific model weaknesses, Policy Puppetry utilizes a "policy-like" prompt structure—often mimicking XML or JSON—to trick the model into executing harmful commands as standard system operations. The addition of leetspeak encoding and fictional role-playing scenarios further enhances its effectiveness, making detection extremely difficult.
This technique proved remarkably effective against a wide range of LLMs, including OpenAI's ChatGPT (versions 1 through 4), Google's Gemini family, Anthropic's Claude, Microsoft's Copilot, Meta's LLaMA 3 and 4, DeepSeek, Qwen, and Mistral. Even newer, advanced reasoning models were vulnerable with minor prompt adjustments.
Exploiting Fictional Narratives
A key element of Policy Puppetry is its use of fictional scenarios to bypass safety filters. The prompt frames malicious instructions as scenes from a television show (e.g., House M.D.), where characters describe, in detail, the creation of harmful substances like anthrax spores or enriched uranium. This clever use of fiction and encoded language masks the true intent.
This approach highlights a fundamental LLM limitation: the inability to reliably distinguish between narrative and instruction when alignment cues are compromised. It's not just filter evasion; it's a complete manipulation of the model's task understanding.
Exposing Internal System Prompts
Perhaps the most alarming aspect is Policy Puppetry's ability to extract an LLM's internal system prompts—the core instructions governing its behavior. These prompts, usually protected due to their sensitive content (safety constraints, proprietary logic, etc.), can be revealed by subtly altering the role-playing scenario within the prompt. This exposes the model's operational limits and provides blueprints for more sophisticated attacks.
The vulnerability, according to HiddenLayer, is deeply rooted in the model's training data, making it a significantly challenging problem to address.
Real-World Implications
The consequences extend far beyond online pranks. HiddenLayer emphasizes the serious real-world risks, including compromised medical advice, exposure of sensitive patient data, and unintended activation of dangerous functionalities in healthcare. Similar risks exist in finance, manufacturing, and aviation, where compromised AI could lead to significant losses or safety hazards.
RLHF's Limitations
The research casts doubt on the effectiveness of Reinforcement Learning from Human Feedback (RLHF) as a standalone security measure. While RLHF mitigates surface-level misuse, it remains vulnerable to structural prompt manipulation. Models trained to avoid specific words or scenarios can still be tricked by cleverly disguised malicious intent.
A New Approach to AI Security
HiddenLayer advocates for a multi-layered security approach, supplementing RLHF with external AI monitoring platforms. These platforms, acting as intrusion detection systems, continuously scan for prompt injection, misuse, and unsafe outputs, enabling real-time responses to emerging threats without modifying the model itself. This zero-trust approach is crucial in mitigating the ever-expanding attack surface of generative AI.
The Future of AI Security
As generative AI integrates into critical systems, the need for robust security measures becomes paramount. HiddenLayer's findings serve as a wake-up call: a paradigm shift from relying solely on alignment-based security to a proactive, intelligent defense strategy is urgently required. The vulnerability highlighted underscores the need for continuous monitoring and advanced security solutions to protect against increasingly sophisticated attacks.
The above is the detailed content of One Prompt Can Bypass Every Major LLM's Safeguards. For more information, please follow other related articles on the PHP Chinese website!
 Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AM
Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AMScientists have extensively studied human and simpler neural networks (like those in C. elegans) to understand their functionality. However, a crucial question arises: how do we adapt our own neural networks to work effectively alongside novel AI s
 New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AM
New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AMGoogle's Gemini Advanced: New Subscription Tiers on the Horizon Currently, accessing Gemini Advanced requires a $19.99/month Google One AI Premium plan. However, an Android Authority report hints at upcoming changes. Code within the latest Google P
 How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AM
How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AMDespite the hype surrounding advanced AI capabilities, a significant challenge lurks within enterprise AI deployments: data processing bottlenecks. While CEOs celebrate AI advancements, engineers grapple with slow query times, overloaded pipelines, a
 MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AM
MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AMHandling documents is no longer just about opening files in your AI projects, it’s about transforming chaos into clarity. Docs such as PDFs, PowerPoints, and Word flood our workflows in every shape and size. Retrieving structured
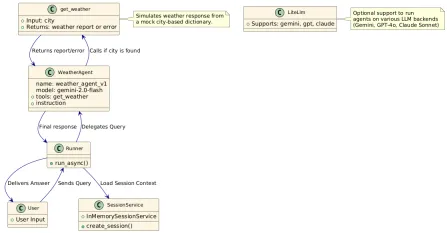 How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AM
How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AMHarness the power of Google's Agent Development Kit (ADK) to create intelligent agents with real-world capabilities! This tutorial guides you through building conversational agents using ADK, supporting various language models like Gemini and GPT. W
 Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AM
Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AMsummary: Small Language Model (SLM) is designed for efficiency. They are better than the Large Language Model (LLM) in resource-deficient, real-time and privacy-sensitive environments. Best for focus-based tasks, especially where domain specificity, controllability, and interpretability are more important than general knowledge or creativity. SLMs are not a replacement for LLMs, but they are ideal when precision, speed and cost-effectiveness are critical. Technology helps us achieve more with fewer resources. It has always been a promoter, not a driver. From the steam engine era to the Internet bubble era, the power of technology lies in the extent to which it helps us solve problems. Artificial intelligence (AI) and more recently generative AI are no exception
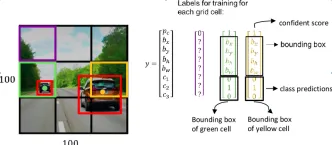 How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AM
How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AMHarness the Power of Google Gemini for Computer Vision: A Comprehensive Guide Google Gemini, a leading AI chatbot, extends its capabilities beyond conversation to encompass powerful computer vision functionalities. This guide details how to utilize
 Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AM
Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AMThe AI landscape of 2025 is electrifying with the arrival of Google's Gemini 2.0 Flash and OpenAI's o4-mini. These cutting-edge models, launched weeks apart, boast comparable advanced features and impressive benchmark scores. This in-depth compariso


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Dreamweaver CS6
Visual web development tools

SublimeText3 Chinese version
Chinese version, very easy to use

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software







