Setting up a new gaming PC is thrilling, but even tech experts can make costly mistakes. Here are some common pitfalls to avoid for a smooth gaming experience.
1. Using the Motherboard's Display Output Instead of Your GPU

A frequent tech support question is poor gaming performance. Often, the issue is connecting the monitor to the motherboard's integrated graphics instead of the dedicated GPU. Motherboard graphics are fine for basic tasks, but inadequate for high-performance gaming. The motherboard's display port is usually near USB and network ports.

Always use the ports on your graphics card, typically located lower on the PC's rear, in a dedicated slot.
2. Outdated Drivers

While Windows Update keeps drivers current, there's often a lag. Always check for the latest graphics drivers, especially before playing new games, to ensure optimal performance and bug fixes.
3. Disabling Windows Updates and Antivirus

Never disable updates or antivirus for performance gains. Security is paramount. Modern PCs experience minimal performance impact from these, and the risk of malware far outweighs any perceived benefit. Regularly check for updates to avoid large, disruptive installations.
4. Poor PC and Monitor Placement

Protect your PC from spills. Avoid placing drinks near your tower. Ergonomics are key; consider a VESA mount for your monitor to prevent neck strain during extended gaming sessions.
5. Neglecting Data Backup

Always back up your data to an external drive (NAS or DAS) and the cloud. This minimizes downtime in case of hardware failure.
6. Installing Unnecessary Software and Over-Configuration

Avoid dubious optimization software. Windows' built-in tools are usually sufficient. Keep your system clean by sticking to official drivers and software from trusted sources like Steam and GOG. Ninite is a helpful tool for installing common software without bundled extras. When tweaking settings, meticulously document changes to easily revert any negative impacts. A Windows reset (after backing up!) is always an option.
7. Providing Unpaid IT Support

While building a gaming PC enhances IT skills, be cautious about offering free tech support. Set boundaries to avoid unexpected responsibilities. If you help friends or family, guide them towards good security practices.
The above is the detailed content of Bought a New Gaming PC? Don't Make These Infuriating Mistakes. For more information, please follow other related articles on the PHP Chinese website!
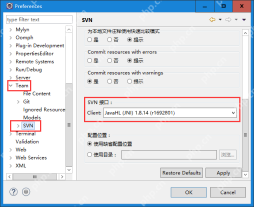 Solve the problem that the svn plugin in eclipse always prompts for password inputMay 07, 2025 pm 05:03 PM
Solve the problem that the svn plugin in eclipse always prompts for password inputMay 07, 2025 pm 05:03 PM1. Background Recently, when using the svn plug-in to manage remote warehouse code in eclipse, prompts to enter passwords are always prompted to enter passwords, which is particularly annoying. After hard work, I finally solved the problem and shared it with you~ 2. Analysis of the password mechanism of the svn plug-in and the cause of the problem. When we use the svn plug-in for the first time and enter the password, a file that saves the password will be generated, and then the svn plug-in will read the username and password information by default every time. When eclipse is started, the configuration information will be automatically read into the program cache. After the password of svn is modified, it is impossible to log in again, and there is no prompt to re-enter the password. At this time, we can delete the relevant configuration files and let the svn plugin prompt us to re-enter the password. However, ec
 How to restore the win8 system details stepsMay 07, 2025 pm 05:00 PM
How to restore the win8 system details stepsMay 07, 2025 pm 05:00 PMThe steps to start system restore in Windows 8 are: 1. Press the Windows key X to open the shortcut menu; 2. Select "Control Panel", enter "System and Security", and click "System"; 3. Select "System Protection", and click "System Restore"; 4. Enter the administrator password and select the restore point. When selecting the appropriate restore point, it is recommended to select the restore point before the problem occurs, or remember a specific date when the system is running well. During the system restore process, if you encounter "The system restore cannot be completed", you can try another restore point or use the "sfc/scannow" command to repair the system files. After restoring, you need to check the system operation status, reinstall or configure the software, and re-back up the data, and create new restore points regularly.
 'Modern Operating System Original Book 3rd Edition'May 07, 2025 pm 04:57 PM
'Modern Operating System Original Book 3rd Edition'May 07, 2025 pm 04:57 PM"Modern Operating Systems (English Edition 3rd Edition)" is a classic work written by Professor Tanenbaum. With his profound experience in the design of three operating systems, the book perfectly integrates theory and practice. The third edition of the book explores a number of topics in depth, such as process, threading, storage management, file systems, I/O deadlock, interface design, multimedia, performance trade-offs, and introduces the latest trends in operating system design. The book not only explains the principles and practices of modern operating systems in detail, but also pays special attention to Linux operating systems, Windows Vista operating systems, embedded operating systems, real-time operating systems and multimedia operating systems. Covering Windows Vista and the latest Linux/Unix operations
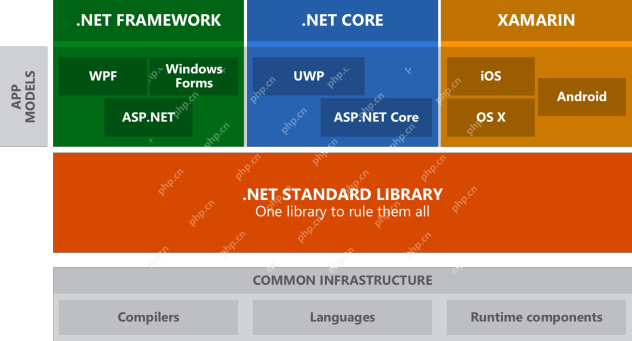 .NET Core Quick Start Tutorial 1. The beginning: Talking about .NET CoreMay 07, 2025 pm 04:54 PM
.NET Core Quick Start Tutorial 1. The beginning: Talking about .NET CoreMay 07, 2025 pm 04:54 PM1. The Origin of .NETCore When talking about .NETCore, we must not mention its predecessor .NET. Java was in the limelight at that time, and Microsoft also favored Java. The Java virtual machine on the Windows platform was developed by Microsoft based on JVM standards. It is said to be the best performance Java virtual machine at that time. However, Microsoft has its own little abacus, trying to bundle Java with the Windows platform and add some Windows-specific features. Sun's dissatisfaction with this led to a breakdown of the relationship between the two parties, and Microsoft then launched .NET. .NET has borrowed many features of Java since its inception and gradually surpassed Java in language features and form development. Java in version 1.6
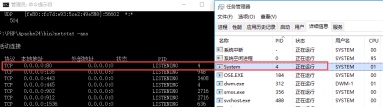 Solve the problem that the 80 port under Windows 10 is occupied by the System with PID 4May 07, 2025 pm 04:51 PM
Solve the problem that the 80 port under Windows 10 is occupied by the System with PID 4May 07, 2025 pm 04:51 PM1. Background Recently, out of curiosity, I updated the Windows 10 system, which is very easy to operate and the experience is quite good. However, when developing in IDEA, when starting the project using port 80, it is found that the port has been occupied. After some attempts, I found a solution and I will share it with you. 2. Solution steps 1. Check the process number PID that occupies port 80 by executing the netstat-ano|findstr "80" command. 2. Since port 80 is occupied by system services, the process cannot be terminated directly. Therefore, use the netshhttpshowservicestate command to view the current HTTP service status. The result is as shown in the figure: from the figure
 10 latest tools for web developersMay 07, 2025 pm 04:48 PM
10 latest tools for web developersMay 07, 2025 pm 04:48 PMWeb development design is a promising career field. However, this industry also faces many challenges. As more businesses and brands turn to the online marketplace, web developers have the opportunity to demonstrate their skills and succeed in their careers. However, as demand for web development continues to grow, the number of developers is also increasing, resulting in increasingly fierce competition. But it’s exciting that if you have the talent and will, you can always find new ways to create unique designs and ideas. As a web developer, you may need to keep looking for new tools and resources. These new tools and resources not only make your job more convenient, but also improve the quality of your work, thus helping you win more business and customers. The trends of web development are constantly changing.
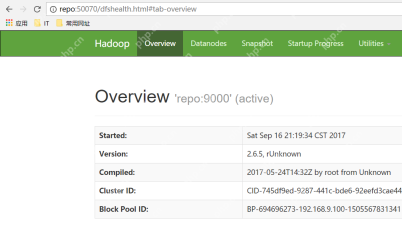 Hadoop pseudo-distributed cluster constructionMay 07, 2025 pm 04:45 PM
Hadoop pseudo-distributed cluster constructionMay 07, 2025 pm 04:45 PMSoftware preparation I am using a virtual machine with CentOS-6.6, with the host name repo. Refer to the steps to install a Linux virtual machine in Windows, I installed JDK in that virtual machine, refer to the guide to installing JDK in Linux. In addition, the virtual machine is configured with a key-free login itself, and the settings for configuring key-free login between each virtual machine are referenced. The download address of Hadoop installation package is: https://mirrors.aliyun.com/apache/hadoop/common/. I am using hadoop 2.6.5 version. Upload the Hadoop installation package to the server and unzip [root@repo~]#tarzxv
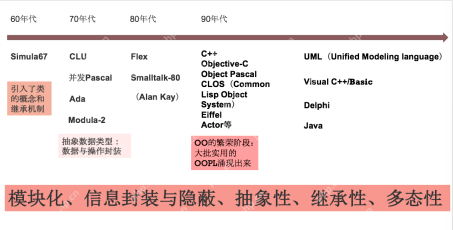 Chapter 4 Class and Object-Oriented Programming Chapter 4 Class and Object-Oriented ProgrammingMay 07, 2025 pm 04:42 PM
Chapter 4 Class and Object-Oriented Programming Chapter 4 Class and Object-Oriented ProgrammingMay 07, 2025 pm 04:42 PMChapter 4 Class and Object-Oriented Programming In the previous chapters, we learned Kotlin's basic language knowledge, type systems and other related knowledge. In this chapter and the next chapter, we will learn Kotlin's support for object-oriented programming and functional programming. In this chapter, we introduce Kotlin's object-oriented programming. 4.1 A brief history of object-oriented programming In the late 1950s, when writing large programs in the FORTRAN language, because there was no encapsulation mechanism, the variables at that time were all "global variables", so variable name conflicts would inevitably occur frequently. In ALGOL60, program blocks identified by Begin-End are used to make the variable names inside the block local to avoid them from outside the block in the program


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software






