2025: Navigating the Evolving Cybersecurity Landscape
The cybersecurity landscape in 2025 is marked by a convergence of advanced technologies and persistent threats. This year presents unique challenges, demanding proactive and multifaceted security strategies.

The Rise of AI-Powered Threats:
A recent SoSafe study reveals a startling statistic: 87% of security professionals reported encountering AI-driven cyberattacks in the past year. The sophistication of AI agents, capable of complex tasks and autonomous actions, presents a significant concern. These agents can readily identify vulnerabilities, compromise systems, and exfiltrate sensitive data, posing a substantial threat to businesses and organizations. This mirrors the rapid adoption of generative AI tools like ChatGPT, which similarly disrupted the market in 2022.
However, the same AI technology offers powerful defensive capabilities. Agentic AI in cybersecurity can automate threat detection, response, and remediation, significantly reducing response times and analyst workload. The integration of generative AI (GenAI) and predictive algorithms promises even more effective threat prediction and mitigation strategies.

Healthcare: A Persistent Target:
The healthcare sector remains a prime target for cybercriminals. 2024 saw a record-breaking 276,775,457 compromised healthcare records—a 64.1% increase from the previous year. This underscores the urgent need for robust security measures, including multi-factor authentication, employee training, and layered security systems. Protecting patient data, medical devices, and network infrastructure is paramount.

The Quantum Computing Threat:
The emergence of quantum computing presents a new level of cybersecurity risk. Quantum computers, with their superior processing power, could potentially break current encryption standards, rendering existing security measures obsolete. The potential for widespread data breaches is a serious concern, particularly for financial systems and critical infrastructure. The arrival of "Q-Day," when quantum computers can easily crack public key systems, is looming closer than anticipated. Preparing for this eventuality requires a shift towards quantum-resistant cryptography and proactive security strategies.

Securing Space Assets:
The increasing reliance on space-based assets for communication, surveillance, and various other applications necessitates robust cybersecurity measures. Satellites and ground control centers are vulnerable to cyberattacks, highlighting the need for sophisticated security protocols and defenses. The growing number of satellites in orbit expands the potential attack surface, making space cybersecurity a critical area of focus.

The Persistent Threat of Ransomware:
Ransomware attacks remain a major concern, with AI-powered phishing attacks and social engineering techniques exacerbating the problem. The increasing sophistication of ransomware groups and the high cost of attacks necessitate improved preparedness and robust incident response plans. Small businesses, healthcare providers, and educational institutions are particularly vulnerable.

The Rise of DDoS Attacks:
Distributed Denial-of-Service (DDoS) attacks are on the rise, with DDoS-for-hire services becoming increasingly sophisticated. The use of DDoS attacks in cyber warfare and extortion schemes underscores the need for robust mitigation strategies and network security solutions.
Conclusion:
2025 presents a complex cybersecurity landscape, with both new and persistent threats. The convergence of AI, quantum computing, and the increasing reliance on interconnected systems demands a proactive and multi-layered approach to security. Organizations must invest in advanced security technologies, employee training, and robust incident response plans to effectively mitigate these risks and protect their valuable assets.
The above is the detailed content of Key Cybersecurity Challenges In 2025—Trends And Observations. For more information, please follow other related articles on the PHP Chinese website!
 Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AM
Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AMScientists have extensively studied human and simpler neural networks (like those in C. elegans) to understand their functionality. However, a crucial question arises: how do we adapt our own neural networks to work effectively alongside novel AI s
 New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AM
New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AMGoogle's Gemini Advanced: New Subscription Tiers on the Horizon Currently, accessing Gemini Advanced requires a $19.99/month Google One AI Premium plan. However, an Android Authority report hints at upcoming changes. Code within the latest Google P
 How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AM
How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AMDespite the hype surrounding advanced AI capabilities, a significant challenge lurks within enterprise AI deployments: data processing bottlenecks. While CEOs celebrate AI advancements, engineers grapple with slow query times, overloaded pipelines, a
 MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AM
MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AMHandling documents is no longer just about opening files in your AI projects, it’s about transforming chaos into clarity. Docs such as PDFs, PowerPoints, and Word flood our workflows in every shape and size. Retrieving structured
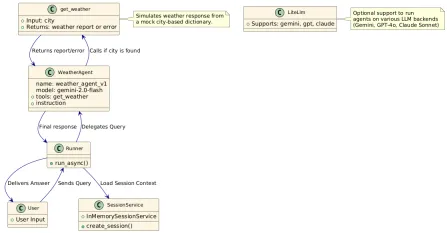 How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AM
How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AMHarness the power of Google's Agent Development Kit (ADK) to create intelligent agents with real-world capabilities! This tutorial guides you through building conversational agents using ADK, supporting various language models like Gemini and GPT. W
 Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AM
Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AMsummary: Small Language Model (SLM) is designed for efficiency. They are better than the Large Language Model (LLM) in resource-deficient, real-time and privacy-sensitive environments. Best for focus-based tasks, especially where domain specificity, controllability, and interpretability are more important than general knowledge or creativity. SLMs are not a replacement for LLMs, but they are ideal when precision, speed and cost-effectiveness are critical. Technology helps us achieve more with fewer resources. It has always been a promoter, not a driver. From the steam engine era to the Internet bubble era, the power of technology lies in the extent to which it helps us solve problems. Artificial intelligence (AI) and more recently generative AI are no exception
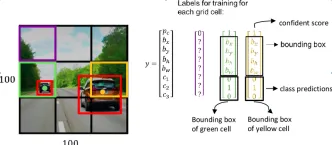 How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AM
How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AMHarness the Power of Google Gemini for Computer Vision: A Comprehensive Guide Google Gemini, a leading AI chatbot, extends its capabilities beyond conversation to encompass powerful computer vision functionalities. This guide details how to utilize
 Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AM
Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AMThe AI landscape of 2025 is electrifying with the arrival of Google's Gemini 2.0 Flash and OpenAI's o4-mini. These cutting-edge models, launched weeks apart, boast comparable advanced features and impressive benchmark scores. This in-depth compariso


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Chinese version
Chinese version, very easy to use

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function







