This article explores the ever-present threat of phishing scams and provides comprehensive strategies for prevention and detection. Recent examples highlight the sophistication and pervasiveness of these attacks, targeting individuals and businesses alike.
The article clearly defines phishing as a deceptive practice where criminals impersonate legitimate entities to obtain personal information. Several real-world examples are cited, including malware attacks disguised as Eventbrite updates, Booking.com payment verification scams, and fraudulent charity appeals exploiting the Israel-Palestine conflict.
The mechanics of a phishing attack are detailed, outlining the steps involved: obtaining contact information, initiating contact via various channels, employing deceptive tactics like fake prizes or urgent requests, and ultimately aiming to infect devices with malware or steal financial data. The article emphasizes that the goal is always to elicit a specific action from the victim, leading to compromised security.
The potential victim profile is broadened beyond high-profile targets, emphasizing that anyone with an online presence is vulnerable. A detailed list of warning signs is provided, including spelling errors, urgency tactics, threatening language, suspicious links, and generic greetings.
The core of the article focuses on preventative measures. A multi-pronged approach is recommended, including:
-
Understanding Phishing Tactics: Recognizing common characteristics of phishing emails and messages. A specific example of a Booking.com phishing email is analyzed, illustrating how timing and urgency are exploited.
-
Practicing Cyber Hygiene: This section stresses the importance of strong, unique passwords, multi-factor authentication, avoiding suspicious emails and attachments, and never clicking unknown links. The dangers of reusing passwords and the benefits of MFA are highlighted.
-
Utilizing Security Tools: The article advocates for using spam filters, robust antivirus software, and call-blocking features on mobile devices. The importance of regularly updating apps and operating systems is stressed.
-
Managing Online Privacy: This section recommends updating social media privacy settings, avoiding public Wi-Fi, and requesting data brokers to remove personal information.
-
Responding to Suspicious Contact: The article emphasizes ignoring strange messages and calls, verifying websites before visiting them, and never replying to suspicious emails.
-
Additional Protective Measures: Further recommendations include avoiding pop-up ads (and using ad blockers), and being cautious about sharing personal information online.
The article concludes by categorizing various types of phishing attacks (spear phishing, email phishing, whaling, BEC, pharming, vishing, smishing, social media phishing, malware, and watering hole attacks), providing concise explanations of each. Finally, it outlines how to report phishing attempts to relevant authorities. The inclusion of screenshots throughout enhances the guide's clarity and practical application.







The above is the detailed content of How to Prevent Phishing? How to Stop Email Scams? Protect Yourself. For more information, please follow other related articles on the PHP Chinese website!
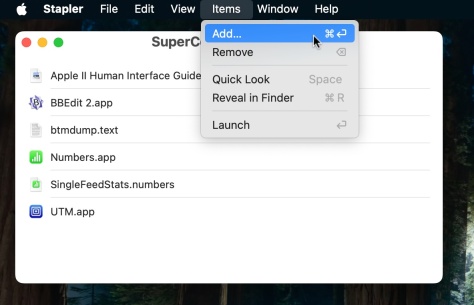 Launch All Apps & Documents Related to a Project with Stapler for MacMay 13, 2025 am 10:37 AM
Launch All Apps & Documents Related to a Project with Stapler for MacMay 13, 2025 am 10:37 AMLongtime Mac users may recall a handy old shareware application for the Classic Macintosh called Stapler, which essentially helped manage projects by grouping a series of apps and documents into a single document that when opened would then launch al
 How to Get Apple Intelligence on Your iPhone, iPad, or MacMay 13, 2025 am 10:32 AM
How to Get Apple Intelligence on Your iPhone, iPad, or MacMay 13, 2025 am 10:32 AMApple Intelligence is a set of AI features that Apple is rolling out in beta, and will debut to a larger set of Apple device owners in the fall. Apple Intelligence offers many features from writing and creating text and emails, to taking actions and
 MacOS Sonoma 14.6.1 & Ventura 13.6.9 Released with Bug FixesMay 13, 2025 am 10:25 AM
MacOS Sonoma 14.6.1 & Ventura 13.6.9 Released with Bug FixesMay 13, 2025 am 10:25 AMIf you feel like you have spent a significant amount of your time updating system software on your Apple devices lately, you’re in for a treat; another round of system software updates! This time around, Apple has released MacOS Sonoma 14.6.1 alon
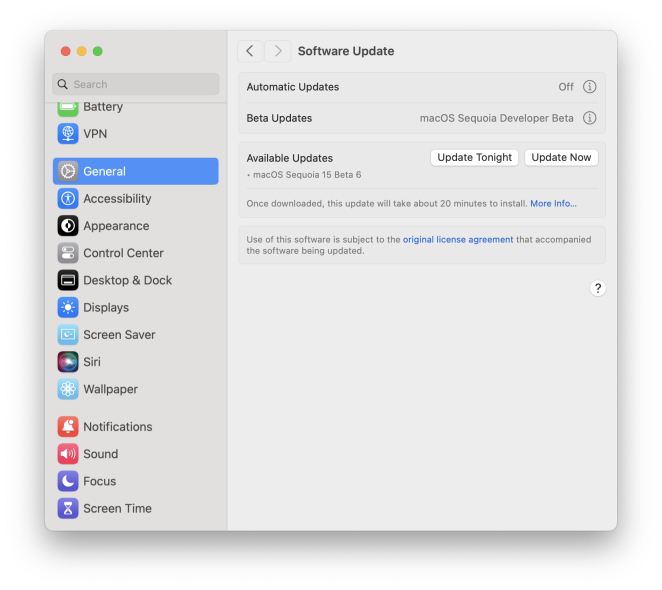 MacOS Sequoia 15 Beta 6 Available for TestingMay 13, 2025 am 10:23 AM
MacOS Sequoia 15 Beta 6 Available for TestingMay 13, 2025 am 10:23 AMApple has issued the 6th beta version of MacOS Sequoia for users enrolled in the developer beta testing program. Usually a matching public beta build arrives soon after, which in this case dev beta 6 would be versioned as public beta 4. MacOS Sequoia
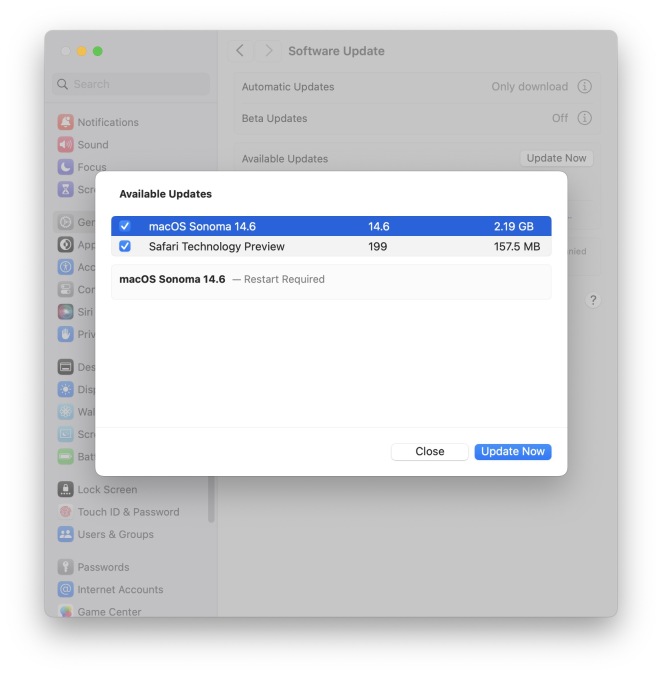 MacOS Sonoma 14.6 Update Released with Bug Fixes & Security UpdatesMay 13, 2025 am 10:20 AM
MacOS Sonoma 14.6 Update Released with Bug Fixes & Security UpdatesMay 13, 2025 am 10:20 AMApple has released macOS Sonoma 14.6 for Mac users running the Sonoma operating system. The MacOS Sonoma 14.6 software update primarily focuses on bug fixes and security updates for most Macs, however it does include a nice new feature specifically
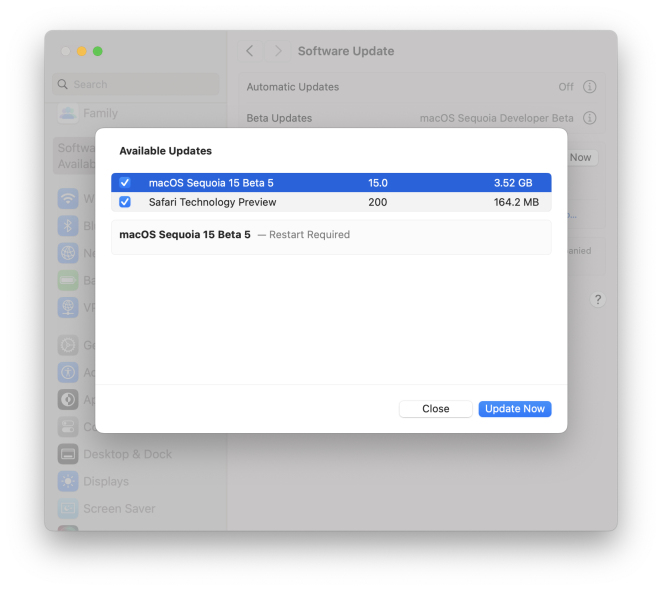 MacOS Sequoia 15 Beta 5 Available to DownloadMay 13, 2025 am 10:06 AM
MacOS Sequoia 15 Beta 5 Available to DownloadMay 13, 2025 am 10:06 AMMacOS Sequoia beta 5 is now available for users enrolled in the developer beta testing program to download and install onto their Macs. MacOS Sequoia beta 5 carries the build of 24A5309e, and usually a new developer beta build is soon followed by a m
 Beta 2 of iOS 18.1, MacOS Sequoia 15.1, & iPadOS 18.1 Released with Apple IntelligenceMay 13, 2025 am 09:49 AM
Beta 2 of iOS 18.1, MacOS Sequoia 15.1, & iPadOS 18.1 Released with Apple IntelligenceMay 13, 2025 am 09:49 AMApple has released the second beta of iOS 18.1, iPadOS 18.1, and MacOS Sequoia 15.1, each with support for Apple Intelligence AI features, on supported devices anyway. The release of these new beta updates is unusual in that they’re concurrent wit
 How to Uninstall VMWare Fusion on MacMay 13, 2025 am 09:44 AM
How to Uninstall VMWare Fusion on MacMay 13, 2025 am 09:44 AMYou might be aware that VMWare Fusion Pro is now free to download and install, and perhaps you installed it on a Mac to test virtual machines or to play around with, and now you’ve decided you no longer need VMware on the Mac. But VMware Fusion P


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool






