This updated article (originally published September 12, 2019) guides you through the steps to take if you suspect an online account compromise. Acting swiftly is crucial to minimize potential damage.
Confirming a Hack

With frequent data breaches reported, vigilance is key. Stay informed by following reputable tech news sources (like this one!) on platforms such as Twitter or RSS. Consider setting up Google Alerts for hacks affecting your key accounts.
If a breach affecting your accounts is reported, use Have I Been Pwned? This website aggregates leaked credentials from various data breaches, listing billions of compromised accounts. Entering your email address reveals if your information is associated with any breaches. A match doesn't guarantee exposure, but it signals potential compromise. Sign up for future alerts.
Also, check your email for breach notifications directly from affected apps and sites. Ensure your contact details are accurate and that emails aren't ending up in your spam folder. These notifications often include recovery instructions, sometimes even preemptively resetting your password.
Detecting Unusual Activity

Most platforms provide account activity logs. Suspicious activity, like logins from unfamiliar locations, warrants investigation.
- Gmail: At the bottom of your inbox, click "Details" to view recent activity, including app and location details.
- Facebook: Access the passwords and security settings, then "See more" under "Where You're Logged In" to review login times, devices, and locations.
- Twitter: Go to settings and privacy, then "Security and account access," "Apps and sessions," and "Sessions" to see active sessions and connected apps.
- Instagram: Check recent login activity through the dedicated page in your settings.
Regularly (e.g., weekly) reviewing this activity significantly improves early detection of unauthorized access.
Securing Your Accounts

If a breach is confirmed, immediately remove unauthorized access. Most platforms allow logging out of all active sessions except your current one. On Facebook, flag unrecognized logins and remotely log out devices using the three-dot menu.
Next, change your password immediately. Choose a strong, unique password—different from those used on other accounts. A password manager can assist if remembering passwords is challenging. Enable two-factor authentication for enhanced security.
If locked out, contact the platform's support team. Provide verification details (security questions, account age, devices used, location) to regain access. Account recovery isn't automated and can take time. While waiting, change passwords on other accounts where you've used the same credentials to prevent further compromise. Never reuse passwords; unique passwords are essential for robust security.
The above is the detailed content of How to check to see if you’ve been hacked. For more information, please follow other related articles on the PHP Chinese website!
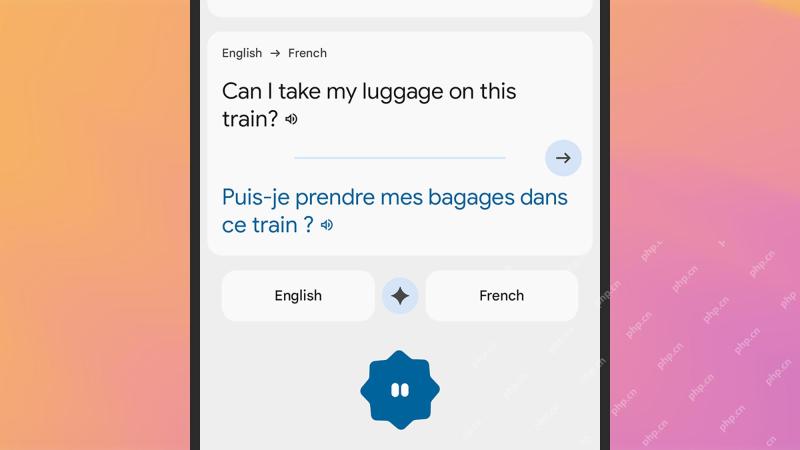 How to get real-time translations on your phoneMay 06, 2025 am 09:44 AM
How to get real-time translations on your phoneMay 06, 2025 am 09:44 AMAI-powered mobile translation apps have dramatically improved real-time conversation capabilities. With a strong internet connection, most apps now seamlessly translate spoken words, eliminating the need for manual typing or pronunciation struggles.
 How to fix Windows update error 0x80071160?May 05, 2025 pm 10:00 PM
How to fix Windows update error 0x80071160?May 05, 2025 pm 10:00 PMWhile many users dont realize that, Windows updates are among the most important features for maintaining the systems stability and security, as well as ensurin
 Must-Know Things: What to Check When Buying a Used LaptopMay 05, 2025 pm 08:01 PM
Must-Know Things: What to Check When Buying a Used LaptopMay 05, 2025 pm 08:01 PMThis MiniTool guide provides essential checks before buying a used laptop. It details how to assess the physical condition, test key hardware, and evaluate the software to ensure a sound purchase. Quick Navigation: What to Check When Buying a Used
 What to Do Before Replacing a Hard Drive? Learn Essentials!May 04, 2025 pm 08:02 PM
What to Do Before Replacing a Hard Drive? Learn Essentials!May 04, 2025 pm 08:02 PMUpgrade the hard drive and improve the computer performance! This article will guide you the steps you need to take before replacing a hard drive on your Windows computer with a larger disk or SSD to avoid unnecessary hassle. Preparation: Choose the right hard drive: When choosing a hard disk, you should not only consider the difference between SSD and HDD, but also consider factors such as storage capacity, form factor size and budget. SSD capacity ranges from 256GB to 4TB or even larger, choose the capacity that suits your needs. Also, check which SSD slot is used for your laptop or desktop and make sure that the SSD you choose (such as 2.5-inch and 3.5-inch SATA SSD, M.2 2280/2230/2242 SSD, etc.) is compatible with your computer. Finally, according to
 Sultan's Game Save File Location: A Detailed Roadmap GuideMay 04, 2025 pm 08:01 PM
Sultan's Game Save File Location: A Detailed Roadmap GuideMay 04, 2025 pm 08:01 PMMastering Sultan's Game: Save File Location and Backup Strategies This guide helps you locate and protect your Sultan's Game save files. Released on March 31st, 2025, Sultan's Game's engaging narratives and appealing visuals have made it a popular c
 A Step-by-Step Guide to Copy ESXi VM to a USB DriveMay 03, 2025 pm 08:01 PM
A Step-by-Step Guide to Copy ESXi VM to a USB DriveMay 03, 2025 pm 08:01 PMOffsite VM backups are crucial. This guide demonstrates how to easily copy ESXi virtual machines to a USB drive for secure, accessible storage. Method 1: Manual VM File Download This method copies the core VM files. Power off the target VM in the V
 Windows 10 KB5055612: New Features & What if It Failed to InstallMay 02, 2025 pm 08:01 PM
Windows 10 KB5055612: New Features & What if It Failed to InstallMay 02, 2025 pm 08:01 PMThis non-security update, KB5055612 for Windows 10 version 22H2 and related versions, released April 22, 2025, offers several quality improvements. This guide details installation and troubleshooting steps. KB5055612: Key Improvements This update enh
 Unlock Helpful Methods to Fix KB5055642 Not InstallingMay 02, 2025 pm 06:01 PM
Unlock Helpful Methods to Fix KB5055642 Not InstallingMay 02, 2025 pm 06:01 PMTroubleshooting KB5055642 Installation Problems on Windows 11 This guide offers solutions for users encountering issues installing Windows 11 Insider Preview Build 26200.5562 (KB5055642), released April 21, 2025. This update introduces enhanced featu


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

Atom editor mac version download
The most popular open source editor

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

WebStorm Mac version
Useful JavaScript development tools

Dreamweaver CS6
Visual web development tools






