This updated article (originally published November 1, 2019) explores the dangers of spyware and how to protect your computer. Unlike ransomware, spyware silently monitors and records your computer activity, potentially stealing your identity or compromising your accounts. This guide provides steps to minimize your risk.
Strengthening Your System's Defenses
Robust computer protection is paramount. Most antivirus software for Windows and macOS offers protection against keyloggers, webcam hijacking, and other spyware, particularly when kept updated. While free antivirus programs often suffice for home users, paid versions provide enhanced security.
We recommend four effective and user-friendly free antivirus options, all highly rated by AV-Comparatives: Windows Defender (built into Windows), AVG Free (available for Windows and macOS, with a paid "ultimate" version), Bitdefender (free for Windows, with a paid version including macOS support), and Avast (free for Windows and macOS, with a paid version). Paid versions typically include features like advanced web link scanning and proactive attack prevention.

Beyond primary antivirus, consider supplementary protection. For Windows, Spybot (free) provides deep scans, while Norton Power Eraser offers a more thorough system check if spyware is suspected. Trend Micro's HouseCall, a browser-based scanner, works across operating systems.
Preventing Spyware Infection
Even with strong antivirus, vigilance is crucial. Spyware can infiltrate through various means. Shared computers should utilize separate user accounts with strong passwords (Windows: Settings > Accounts; macOS: System Preferences > Users & Groups).
Be cautious of suspicious links in emails or social media, even from trusted sources, as accounts may be compromised. Only download software from official websites or reputable app stores (Mac App Store, Microsoft Store). Thoroughly review browser extensions before installation, checking user reviews and professional tech site endorsements.
Recognizing Spyware Warning Signs
Maintain awareness, even with robust security. Sudden performance drops, excessive hard drive activity, unexplained application launches (especially fleeting windows), unusual mouse movements or text input, OS setting changes, and unfamiliar shortcuts are all potential red flags.
Spyware consumes system resources. Use Task Manager (Windows) or Activity Monitor (macOS) to identify unfamiliar processes. Perform web searches on unknown applications to determine their legitimacy. Regularly update your operating system, software, and security tools. While spyware is constantly evolving, so are security measures; staying updated is key to minimizing risk.
The above is the detailed content of Make sure no one is spying on your computer. For more information, please follow other related articles on the PHP Chinese website!
 How to fix Microsoft Teams Error tag 7ita9 in Windows?May 06, 2025 pm 04:00 PM
How to fix Microsoft Teams Error tag 7ita9 in Windows?May 06, 2025 pm 04:00 PMMicrosoft Teams is widely used for virtual meetings, team collaboration, and workplace communication. But from time to time, users encounter technical issues th
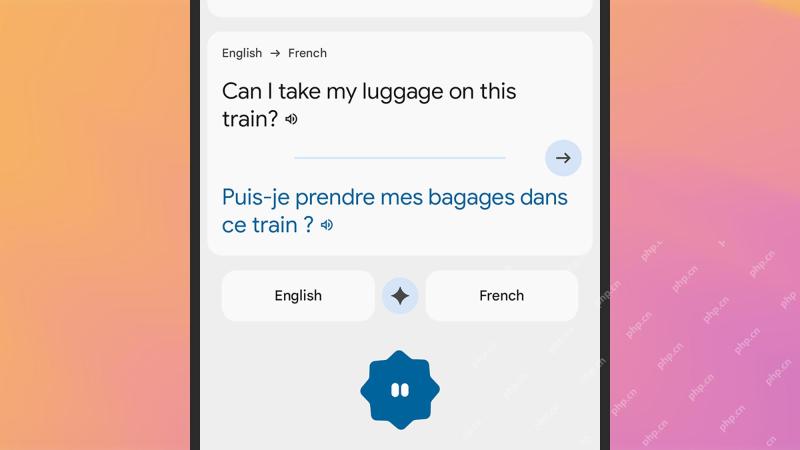 How to get real-time translations on your phoneMay 06, 2025 am 09:44 AM
How to get real-time translations on your phoneMay 06, 2025 am 09:44 AMAI-powered mobile translation apps have dramatically improved real-time conversation capabilities. With a strong internet connection, most apps now seamlessly translate spoken words, eliminating the need for manual typing or pronunciation struggles.
 How to fix Windows update error 0x80071160?May 05, 2025 pm 10:00 PM
How to fix Windows update error 0x80071160?May 05, 2025 pm 10:00 PMWhile many users dont realize that, Windows updates are among the most important features for maintaining the systems stability and security, as well as ensurin
 Must-Know Things: What to Check When Buying a Used LaptopMay 05, 2025 pm 08:01 PM
Must-Know Things: What to Check When Buying a Used LaptopMay 05, 2025 pm 08:01 PMThis MiniTool guide provides essential checks before buying a used laptop. It details how to assess the physical condition, test key hardware, and evaluate the software to ensure a sound purchase. Quick Navigation: What to Check When Buying a Used
 What to Do Before Replacing a Hard Drive? Learn Essentials!May 04, 2025 pm 08:02 PM
What to Do Before Replacing a Hard Drive? Learn Essentials!May 04, 2025 pm 08:02 PMUpgrade the hard drive and improve the computer performance! This article will guide you the steps you need to take before replacing a hard drive on your Windows computer with a larger disk or SSD to avoid unnecessary hassle. Preparation: Choose the right hard drive: When choosing a hard disk, you should not only consider the difference between SSD and HDD, but also consider factors such as storage capacity, form factor size and budget. SSD capacity ranges from 256GB to 4TB or even larger, choose the capacity that suits your needs. Also, check which SSD slot is used for your laptop or desktop and make sure that the SSD you choose (such as 2.5-inch and 3.5-inch SATA SSD, M.2 2280/2230/2242 SSD, etc.) is compatible with your computer. Finally, according to
 Sultan's Game Save File Location: A Detailed Roadmap GuideMay 04, 2025 pm 08:01 PM
Sultan's Game Save File Location: A Detailed Roadmap GuideMay 04, 2025 pm 08:01 PMMastering Sultan's Game: Save File Location and Backup Strategies This guide helps you locate and protect your Sultan's Game save files. Released on March 31st, 2025, Sultan's Game's engaging narratives and appealing visuals have made it a popular c
 A Step-by-Step Guide to Copy ESXi VM to a USB DriveMay 03, 2025 pm 08:01 PM
A Step-by-Step Guide to Copy ESXi VM to a USB DriveMay 03, 2025 pm 08:01 PMOffsite VM backups are crucial. This guide demonstrates how to easily copy ESXi virtual machines to a USB drive for secure, accessible storage. Method 1: Manual VM File Download This method copies the core VM files. Power off the target VM in the V
 Windows 10 KB5055612: New Features & What if It Failed to InstallMay 02, 2025 pm 08:01 PM
Windows 10 KB5055612: New Features & What if It Failed to InstallMay 02, 2025 pm 08:01 PMThis non-security update, KB5055612 for Windows 10 version 22H2 and related versions, released April 22, 2025, offers several quality improvements. This guide details installation and troubleshooting steps. KB5055612: Key Improvements This update enh


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SublimeText3 Chinese version
Chinese version, very easy to use

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.






