Is Apple Pay safe? How to prevent fraud?
It's normal for many people to have doubts about the security of using Apple Pay. After all, there are risks in adding credit or debit card information to a digital wallet or other platform. This guide will dive into Apple Pay’s security mechanisms to help you understand its ability to prevent fraud and make informed decisions.
How safe is Apple Pay?
Apple Pay uses multiple security tools and features to ensure the security of your transactions. Its built-in security features protect your transactions and combine the device password with a face ID, touch ID, or optical ID (depending on your Apple device) to protect your Apple Pay account.
Apple encrypts all sensitive data, including your debit, credit, transportation or prepaid card information, and stores it on the server. Additionally, the card information you enter using the camera is not stored in your device or photo library.
While apps on the App Store are usually strictly reviewed, privacy leaks are still inevitable.
Is there anti-fraud protection on Apple Pay?
Yes, Apple Pay has multiple anti-fraud features. It uses tokenization technology to protect your card information. Instead of sharing your credit or debit card information directly with merchants, Apple creates a unique device account number for your transactions, thus protecting your sensitive information security.
In addition, Apple requires you to authorize payments with your device password or biometric information, making it more difficult for malicious actors to use Apple Pay for transactions. You can also delete lost or stolen cards at any time. Finally, your Apple Pay transactions are protected by end-to-end encryption, ensuring your purchase information is private and secure.
Can Apple Pay prevent scams?
No. Apple Pay cannot completely prevent Apple Pay scams, nor can it provide purchase protection or fraudulent transaction refunds. Therefore, we strongly recommend that you enable two-factor authentication (2FA) and protect your device with your password or biometric information.
Apple Pay Scam Type
Similar to Apple ID scams, cybercriminals can only access your Apple Pay account using your credentials. Because this is difficult, they have to find another way. Here are some common types of Apple Pay scams:
-
Physical scam
-
Online market or overpayment fraud
-
Insecure Wi-Fi Scam
-
Price fraud
-
Physical scam
Physical scam refers to the malicious actor disguised as a legal company representative and stealing your personal information. They may contact you via text or email, inducing you to click on the link to receive the prize or update your payment information. But doing so may cause you to visit malicious websites, thus revealing your Apple Pay information.
- Online market or overpayment fraud
Overpayment scams usually occur on market platforms such as Facebook Marketplace. The scam buys the items you sell, but "accidentally" sends you too much money. They then ask you to refund the difference via Apple Cash, but this is actually a trick to scam your money because the credit card they use is usually the proceeds of theft. By the time you realize what is going on, it may be too late because they may have deactivated their accounts in the market where you interact and are cheated of cash and merchandise.
- Insecure Wi-Fi Scam
Public Wi-Fi networks are often inadequately secure and are easily targeted by hackers and cybercriminals. Therefore, changing your Apple Pay account information when connecting to a public Wi-Fi network can leave you vulnerable to attacks. If you must modify your Apple Pay account information on a public Wi-Fi network, make sure to connect to your VPN service first.

- Price fraud
Similar to phishing scams, hackers and other malicious actors can use prize scams to defraud your money. It works as follows: They falsely inform you that you have won Apple’s prizes by email or text messages containing links and request details of your Apple Pay account. Clicking on the link will endanger your Apple Wallet and your funds may be stolen.
How to protect Apple Pay from scams
To avoid becoming a victim of Apple Pay scams, we recommend you:
- Protect your Apple ID with 2FA.
- Use VPN services to protect your Apple ID account information.
- Install antivirus software on your device to ensure that viruses and malware are cleaned up regularly.
Stay away from Apple Pay scams
While Apple Pay has powerful security features, it doesn't fully protect you from scams. To do this, we recommend using MacKeeper's Identity Theft Protection to protect your data from such scams. Our tools alert you when your Apple Pay-related email address is included in a data breach.
The following are ways to protect your data using MacKeeper’s Identity Theft Protection:
- Open on your MacBook PC MacKeeper.
- Select Identity Theft Protection from the sidebar, and click to open > Check for vulnerabilities.
- Follow the on-screen instructions carefully to keep your email safe.

Identity theft protection for MacKeeper is the ideal solution to protect your email address and data security. Try it now.
The above is the detailed content of Does Apple Pay Protect You from Scams? Does It Have Fraud Protection?. For more information, please follow other related articles on the PHP Chinese website!
 Second Release Candidate of MacOS Sequoia 15.4 Available for TestingApr 30, 2025 am 10:26 AM
Second Release Candidate of MacOS Sequoia 15.4 Available for TestingApr 30, 2025 am 10:26 AMApple has released a second Release Candidate (RC) build of macOS Sequoia 15.4 for its beta testing program. This follows the initial release candidate builds of Sequoia 15.4, iOS 18.4, and iPadOS 18.4, released just days prior. Release Candidates a
 Easily Create MacOS Virtual Machines with VirtualBuddyApr 30, 2025 am 10:14 AM
Easily Create MacOS Virtual Machines with VirtualBuddyApr 30, 2025 am 10:14 AMVirtualBuddy: Easily virtualize macOS and Linux on Apple Silicon Mac VirtualBuddy provides a simple and fast way to virtualize macOS (and Linux) on any Apple Silicon Mac, providing developers, enthusiasts, and curious users with a way to easily run multiple instances of macOS. VirtualBuddy is fast, performs well, and it is free and open source, so you can easily explore the virtual machine world without any commitment, just prepare enough disk storage and bandwidth to set up a macOS or Linux virtual machine. Whether it is testing different versions
 12 Things to Check Before Buying Second-hand MacBookApr 30, 2025 am 10:01 AM
12 Things to Check Before Buying Second-hand MacBookApr 30, 2025 am 10:01 AMBuying a used Mac on a budget? This guide ensures you avoid a lemon. We'll cover essential checks before you buy, including diagnostics you can perform on the spot. Remember to bring a bootable macOS USB drive and headphones. Step 1: Physical Insp
 How Long Does Updating MacOS Take? Why Is MacOS Update Taking So Long?Apr 30, 2025 am 09:53 AM
How Long Does Updating MacOS Take? Why Is MacOS Update Taking So Long?Apr 30, 2025 am 09:53 AMHow long does it take to update the MacOS system software? Why does it take so long to update? Many Mac users will have this question when they see the software update of the new MacOS system. Both of these questions are very reasonable, and it is important to remember that the answers may vary. However, with modern MacOS, you can make a fairly accurate estimate of the time it takes to install updates to your MacOS system. Let's dive into this topic so you can better understand and prepare to install MacOS updates on your Mac. How long does it take for MacOS updates to be downloaded, installed and completed? MacOS updates can take between 15-20 minutes to several hours to complete, especially if you are considering downloading updates and installing updates to completion
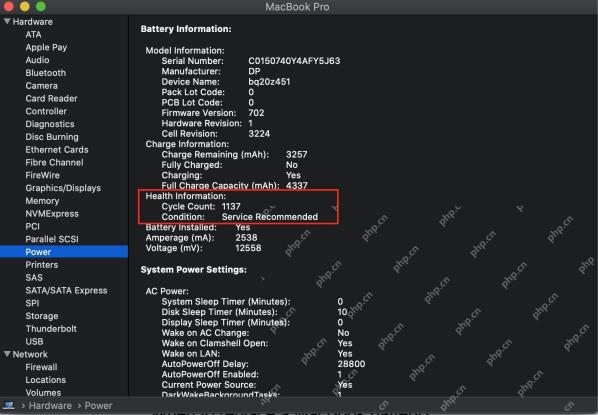 How Long Do MacBook Batteries Last? Here's How You Can Check ItApr 30, 2025 am 09:50 AM
How Long Do MacBook Batteries Last? Here's How You Can Check ItApr 30, 2025 am 09:50 AMUnderstanding MacBook Battery Life: Maximizing Your Mac's Power Concerned about your MacBook's battery performance, or planning a purchase? This guide clarifies MacBook battery lifespan and offers tips for extending it. Most Mac batteries endure appr
 Fixing Safari for Mac Error “This webpage was reloaded because a problem occurred”Apr 30, 2025 am 09:45 AM
Fixing Safari for Mac Error “This webpage was reloaded because a problem occurred”Apr 30, 2025 am 09:45 AMAlthough the Safari browser under the Mac system is excellent, it is not perfect. Safari users occasionally encounter situations where the page refreshes and displays an error message "This page has reloaded because of a problem". You may also see variant information like "repeated problems". Since the error message is quite general, you may be wondering the root cause of the error in Safari and how to fix this on your Mac. Causes causing Safari for Mac to have a "This web page reloaded because a problem occurred" error Usually, if there is a memory problem, a website crash, or an incompatible with Safari, a software error, or other similar issues, you will see this error message in Safari on your Mac
 Get Googly Eyes in Your Mac Menu Bar to Follow Your Cursor AroundApr 30, 2025 am 09:42 AM
Get Googly Eyes in Your Mac Menu Bar to Follow Your Cursor AroundApr 30, 2025 am 09:42 AMNostalgic Mac users may remember an interesting application in the classic Mac OS system: it will place a pair of moving eyes in the Mac menu bar and move with your cursor. While classic Mac OS is long gone, you can still experience this fun on a modern Mac, just use an app called "Googly Eyes". Google Eyes resides in your Mac menu bar, and its pupils will follow your cursor like an older version of the app. When clicking on the mouse/trackpad, the little eyes will blink. Will this revolutionize your computing experience? Probably not. But is it interesting? Absolutely fun! Sometimes, just being fun is enough, right? So, enjoy it, in your Ma
 MacOS Sonoma 14.7.5 & MacOS Ventura 13.7.5 Security Updates ReleasedApr 30, 2025 am 09:40 AM
MacOS Sonoma 14.7.5 & MacOS Ventura 13.7.5 Security Updates ReleasedApr 30, 2025 am 09:40 AMApple has released macOS Sonoma 14.7.5 and macOS Ventura 13.7.5 security updates for Mac users running Sonoma and Ventura operating systems. These updates focus on security patches and do not include other new features available in the latest macOS Sequoia 15.4 update (sequoia 15.4 update is released simultaneously). Additionally, you'll find software updates for new and older iPhones and iPads, as well as updates for Apple TV, Apple Watch, and Apple Vision Pro


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

Dreamweaver CS6
Visual web development tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft






