Logic bombs: a silent threat lurking in your software. While viruses and trojans are widely known, logic bombs remain a less understood, yet equally dangerous, form of malware. This article explores what they are, how they work, and how to mitigate their risks.
What is a Logic Bomb?
A logic bomb is a piece of malicious code embedded within seemingly harmless software. It lies dormant until a specific trigger condition is met, at which point it unleashes its payload – causing damage or disruption. Unlike viruses that actively spread, logic bombs are stealthy, remaining undetected until activation. Their targeted nature makes traditional antivirus signatures ineffective.
How Logic Bombs Work and Are Triggered
 Programmers create logic bombs to activate under precise circumstances. These triggers might include a specific date, the deletion of a file, or a particular user's login. This specificity makes them challenging to identify and counter. Logic bombs are often deployed by disgruntled insiders with a specific target in mind – an individual, company, or system. They can also be delivered as part of a larger malware attack, with the virus or trojan acting as a delivery mechanism before self-destructing.
Programmers create logic bombs to activate under precise circumstances. These triggers might include a specific date, the deletion of a file, or a particular user's login. This specificity makes them challenging to identify and counter. Logic bombs are often deployed by disgruntled insiders with a specific target in mind – an individual, company, or system. They can also be delivered as part of a larger malware attack, with the virus or trojan acting as a delivery mechanism before self-destructing.
Famous Examples of Logic Bomb Attacks
Several high-profile logic bomb incidents have occurred. A recent example involved Newag trains programmed to malfunction if their GPS location indicated servicing at a competitor's facility (2023). Another notable case saw a coordinated attack in 2013 that simultaneously wiped the hard drives of South Korean banks and media companies. Successful prevention efforts have also taken place, such as the 2008 discovery of a logic bomb at Fannie Mae, preventing a catastrophic server wipe.
How To Detect and Prevent Logic Bombs
 Detecting logic bombs is difficult, and prevention is even more crucial. There's no single software solution; instead, a multi-layered approach is necessary.
Detecting logic bombs is difficult, and prevention is even more crucial. There's no single software solution; instead, a multi-layered approach is necessary.
Thorough code audits are essential, especially for in-house software development, to identify malicious code before deployment. This is particularly critical given that disgruntled employees or former contractors are common sources of logic bomb attacks. Monitoring for unusual software behavior can also help, though this is challenging as some logic bombs produce no immediate alerts.
Ultimately, robust preventative measures are key. This includes rigorous vetting of personnel with code access, combined with standard cybersecurity practices like employee training to avoid downloading untrusted software.
The above is the detailed content of What Is a Logic Bomb?. For more information, please follow other related articles on the PHP Chinese website!
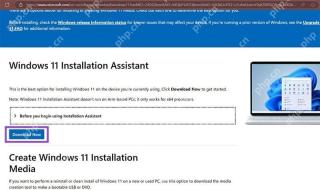 How to Install Windows 11 With No TPM 2.0May 01, 2025 pm 08:01 PM
How to Install Windows 11 With No TPM 2.0May 01, 2025 pm 08:01 PMWindows 10 support is ending in late 2025, prompting many users to upgrade to Windows 11. However, the TPM 2.0 requirement can be a significant hurdle. This guide outlines methods to install Windows 11 even without TPM 2.0, but proceed with caution.
 Acer Has Two New Monitors for GamingMay 01, 2025 am 06:06 AM
Acer Has Two New Monitors for GamingMay 01, 2025 am 06:06 AMThe Acer Predator XB323QK V4 and Nitro XV240 F6: A Tale of Two Monitors Acer offers two distinct gaming monitors catering to different needs: the color-focused XB323QK V4 and the speed-demon XV240 F6. Let's break down their key features. The XB323QK
 I Bought RAM and an NVMe on eBay, Here's How It WentMay 01, 2025 am 06:01 AM
I Bought RAM and an NVMe on eBay, Here's How It WentMay 01, 2025 am 06:01 AMeBay: A Surprisingly Good Source for New Computer Hardware? While eBay is renowned for its diverse selection of used goods, it's not always the first place that springs to mind when purchasing new computer components. However, my recent experience s
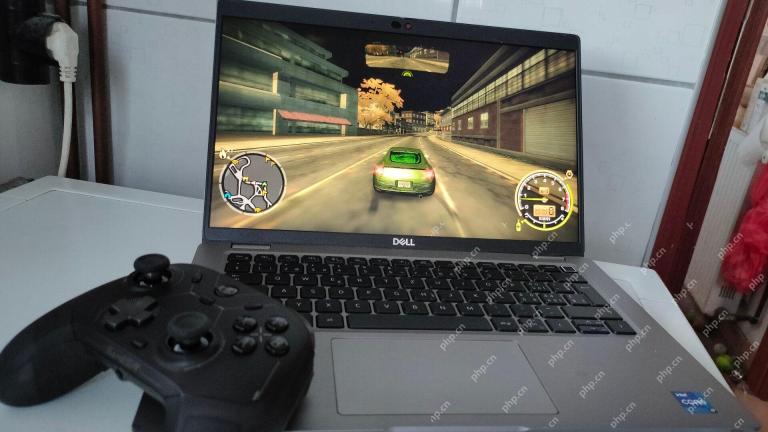 I Upgraded My Laptop's RAM, the Performance Boost Wasn't What You'd ExpectMay 01, 2025 am 03:08 AM
I Upgraded My Laptop's RAM, the Performance Boost Wasn't What You'd ExpectMay 01, 2025 am 03:08 AMUpgrading your aging laptop? Adding RAM is the easiest and often the only practical upgrade besides storage. My recent experience upgrading a Dell Latitude 5420 proved surprisingly impactful. More RAM Wasn't the Initial Goal My used Dell 5420, while
 5 Reasons Why I Love Coiled Keyboard CablesMay 01, 2025 am 03:07 AM
5 Reasons Why I Love Coiled Keyboard CablesMay 01, 2025 am 03:07 AMLet's be honest: unless you're a keyboard enthusiast, you've probably overlooked the cable bundled with your keyboard. But for those who appreciate the finer details, even a simple USB cable can be a source of aesthetic pleasure. 5 Reasons Why Coiled
 Today's NYT Connections Hints and Answer for April 30th (#689)May 01, 2025 am 03:05 AM
Today's NYT Connections Hints and Answer for April 30th (#689)May 01, 2025 am 03:05 AMToday's NYT Connections Game Hints and Answers Need a hand with today's Connections game? Here are some clues to get you started: Yellow: Think about what's under your feet. Green: Where you rest your head (or bottom!). Blue: How others see you. Pu
 Don't Waste Your Money on RGB, Buy a Better MotherboardMay 01, 2025 am 03:04 AM
Don't Waste Your Money on RGB, Buy a Better MotherboardMay 01, 2025 am 03:04 AMBuilding a new PC? Don't get sidetracked by flashy RGB lighting! While those vibrant fans and memory sticks are tempting, overlooking the motherboard is a critical mistake. This often-underappreciated component is crucial for your PC's performance
 Razer Monitor Stand Chroma Review: Compact RGB Stand With 4-Port HubMay 01, 2025 am 03:03 AM
Razer Monitor Stand Chroma Review: Compact RGB Stand With 4-Port HubMay 01, 2025 am 03:03 AMRazer Monitor Stand Chroma Review: Take into account both high-end design and practicality? The Razer Monitor Stand Chroma is a high-end compact aluminum stand with RGB lighting and a USB hub, but its relatively small size and high price limits its overall appeal. Rating: 7/10 Advantages and Disadvantages: advantage: Streamlined design Sturdy and durable USB hub performs well Remapable buttons shortcoming: The bracket is relatively shallow The included USB-C cable is too short Fingerprints easily contaminated on the surface The maximum brightness of RGB lights is low Extremely expensive Price and purchase channels: Razer Mo


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

WebStorm Mac version
Useful JavaScript development tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Zend Studio 13.0.1
Powerful PHP integrated development environment







