 Backend Development
Backend Development PHP Tutorial
PHP Tutorial How to Prevent Session Hijacking: Resolving the Puzzle of Shared Session IDs?
How to Prevent Session Hijacking: Resolving the Puzzle of Shared Session IDs?
Preventing Session Hijacking: Tackling the Conundrum of Multiple Clients Sharing a Single Session ID
The concern raised is crucial for maintaining the security of web applications. The issue revolves around preventing multiple clients from utilizing the same session ID, thereby mitigating session hijacking attempts. However, understanding the limitations of the HTTP protocol is paramount.
The stateless nature of HTTP presents inherent challenges. Once a session ID is issued to a user, it becomes virtually impossible for the server to distinguish between legitimate and unauthorized requests using that session ID. This is because HTTP does not provide a mechanism to detect multiple users sharing a single session ID.
While some measures, such as checking the user agent or IP address, can serve as defense-in-depth techniques, they are not foolproof. User agents can be spoofed, and IP addresses can change for legitimate reasons.
The most effective solution lies in preventing the compromise of session IDs in the first place. This includes utilizing a high degree of entropy in generating session IDs to minimize the risk of guessing. Additionally, transmitting session IDs over HTTPS ensures the confidentiality of the communication.
Utilizing cookies to store session IDs and configuring them with the HttpOnly and Secure attributes adds further protection. Cookies marked with HttpOnly are inaccessible to JavaScript, thwarting cross-site scripting vulnerabilities. Secure cookies disallow transmission over insecure channels.
Periodically regenerating session IDs and invalidating old ones enhances security, reducing the potential impact of compromised session IDs. This practice ensures that even if a session ID is somehow compromised, its usefulness is limited in time.
By adhering to these best practices and embracing the limitations of HTTP, website owners can significantly reduce the risk of session hijacking attacks while maintaining a secure user experience.
The above is the detailed content of How to Prevent Session Hijacking: Resolving the Puzzle of Shared Session IDs?. For more information, please follow other related articles on the PHP Chinese website!
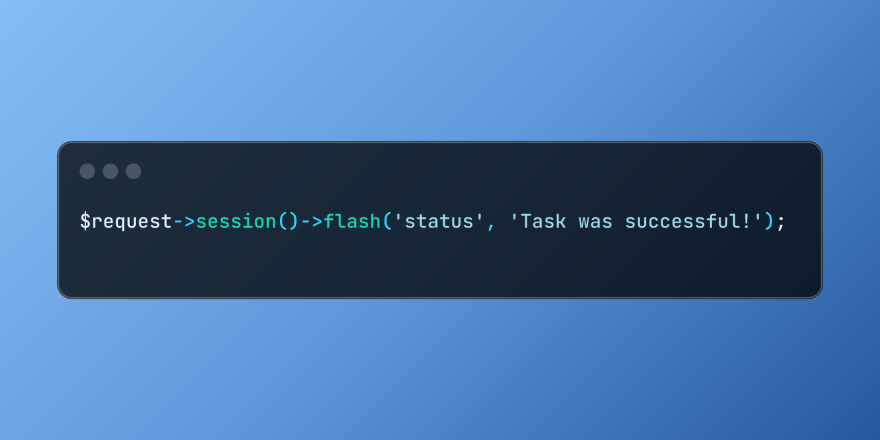 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
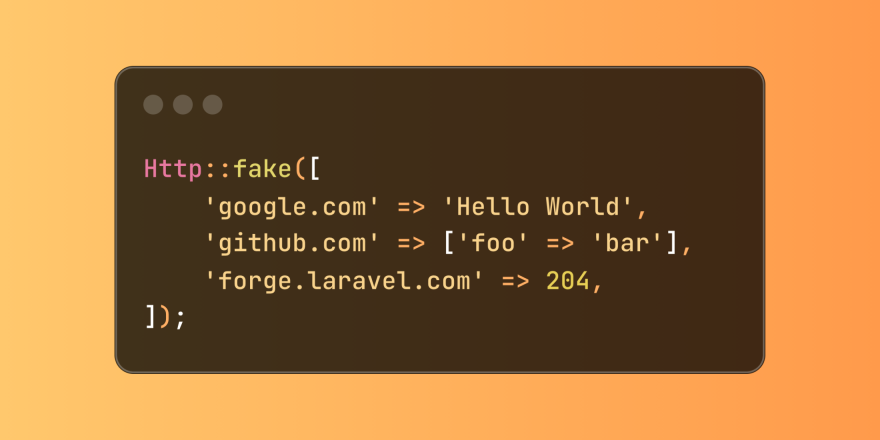 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Zend Studio 13.0.1
Powerful PHP integrated development environment

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Dreamweaver Mac version
Visual web development tools

Atom editor mac version download
The most popular open source editor

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),





