 Backend Development
Backend Development PHP Tutorial
PHP Tutorial How to Optimize PHP Prepared Statements for SQL Injection Avoidance?
How to Optimize PHP Prepared Statements for SQL Injection Avoidance?
PHP Prepared Statement Optimization for SQL Injection Avoidance
Background
Prepared statements are an effective means of preventing SQL injections, a common security vulnerability. They involve creating a pre-defined statement that prevents direct insertion of user-input into the query, thereby reducing the risk of malicious code execution.
The Issue
When executing a prepared statement for table updates, it is crucial to adhere to specific guidelines to ensure its proper execution. Errors in the statement or improper variable binding can result in unexpected outcomes, such as failing to update the database or displaying incorrect row counts.
The Solution
- Prepare and Check: Always check if the prepared statement fails using if ($stmt === false). If it fails, use trigger_error($this->mysqli->error, E_USER_ERROR) to report the error.
- Bind Parameters in Order: The parameters in the bind_param function must be in the same order as they appear in the SQL statement. Reversing the order can lead to incorrect results.
- No Escaping for Parameters: When using parameters, there is no need to manually escape input data. The database handles escaping internally. If you attempt to escape the content, you risk introducing additional escape characters ('') into the actual content.
- Set Parameters After Binding: Set the parameter values after binding them to avoid binding issues.
Regarding Field Declarations
In terms of updating fields in a table, it is not necessary to declare all fields in the UPDATE statement. You can specify only the fields you wish to modify, and the other fields will remain unchanged.
Conclusion
By following these guidelines when using prepared statements, you can effectively prevent SQL injections and ensure the accuracy of your database updates. Remember to handle errors properly, bind parameters correctly, avoid manual escaping, and set parameters after binding. By implementing these practices, your PHP scripts will operate more securely and reliably when interacting with databases.
The above is the detailed content of How to Optimize PHP Prepared Statements for SQL Injection Avoidance?. For more information, please follow other related articles on the PHP Chinese website!
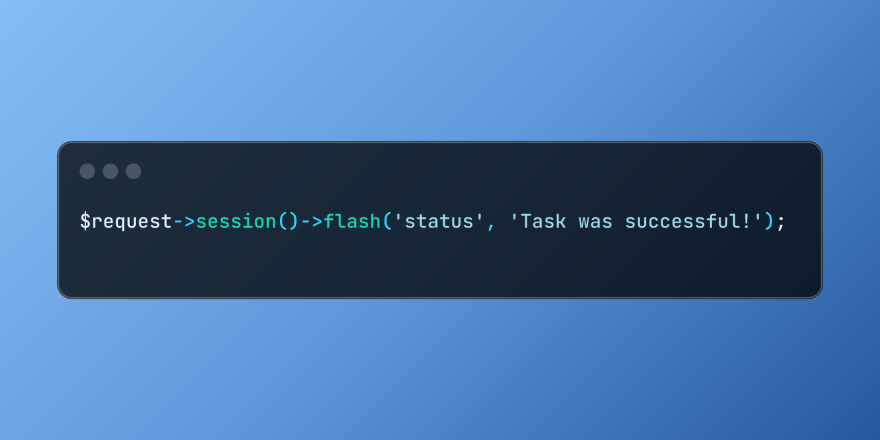 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
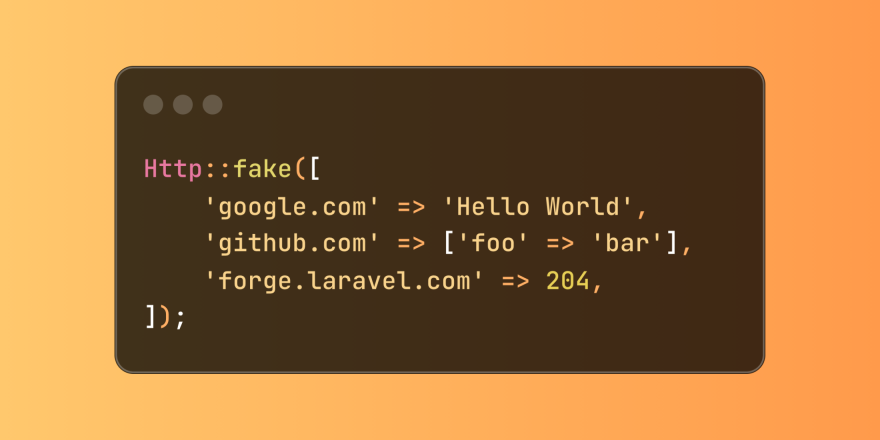 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

WebStorm Mac version
Useful JavaScript development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SublimeText3 English version
Recommended: Win version, supports code prompts!





