 System Tutorial
System Tutorial Windows Series
Windows Series How to add a picture password in Win11 Tutorial on adding a picture password in Win11
How to add a picture password in Win11 Tutorial on adding a picture password in Win11How to add a picture password in Win11 Tutorial on adding a picture password in Win11
A question that bothers many people: How to add a picture password in Windows 11? PHP editor Baicao will reveal the answer to everyone! Don’t hesitate, continue reading the detailed instructions below to easily solve the picture password setting problem and make your Windows 11 login experience more personalized and secure!
Tutorial on adding a picture password in Win11
1. First, press the [Win + i] key combination on the keyboard to open Windows Settings, and then click [Account] on the left sidebar.

2. Under Account, click [Login Options (Windows Hello, Security Key, Password, Dynamic Lock)].

3. The current path is: Account - Login options, click [Picture Password (swipe and click your favorite photo to unlock the device)].

4. When options appear, click [Add].

5. Welcome to use picture password. Picture password is a new way to help you protect your touch screen computer. You need to select a picture and draw various gestures on the picture to create a unique password. After selecting an image, you can "draw" directly on the touch screen to create combinations of circles, lines, and clicks. The size of these gestures. Both location and orientation will become part of the picture password. In the Windows Security Center window that pops up, first verify your account information, enter [Password], and then click [OK].

6. In the settings interface, click [Select Picture].

7. Select the picture you want to set, and then click [Open].

8. After completing the import, click [Use this image].

9. Set your gestures and draw three gestures on the picture. Circles, lines, and points can be used freely. Remember that the gestures and their size, their position and orientation, and the order in which they are drawn, will all become part of the picture's password. Click three locations on the image, which can be anywhere.

10. Confirm your gestures. To complete the setting of the picture password, please repeat these three gestures. (You can click the "Restart" button to reset your picture password at any time.) Click the previously clicked positions in order.

11. Click [Finish], so the picture password is set successfully.
The above is the detailed content of How to add a picture password in Win11 Tutorial on adding a picture password in Win11. For more information, please follow other related articles on the PHP Chinese website!
 The New Surface Pro Doesn't Feel ProMay 08, 2025 am 06:01 AM
The New Surface Pro Doesn't Feel ProMay 08, 2025 am 06:01 AMThe new Surface Pro: A step back? Microsoft's latest Surface Pro offers connectivity via two USB-C ports, supporting charging, USB 3.2 data transfer, and DisplayPort 1.4a (up to two 4K monitors at 60Hz). However, the device ships without a power ad
 Microsoft Challenges the MacBook Air With New Surface LaptopMay 08, 2025 am 03:02 AM
Microsoft Challenges the MacBook Air With New Surface LaptopMay 08, 2025 am 03:02 AMMicrosoft's latest Surface Laptop aims to rival the MacBook Air, but with some notable compromises. The absence of a Surface Connect port marks a significant departure from previous models, reflecting the growing prevalence of Thunderbolt and USB do
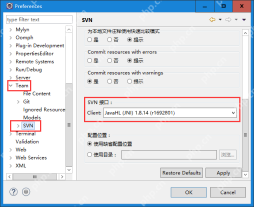 Solve the problem that the svn plugin in eclipse always prompts for password inputMay 07, 2025 pm 05:03 PM
Solve the problem that the svn plugin in eclipse always prompts for password inputMay 07, 2025 pm 05:03 PM1. Background Recently, when using the svn plug-in to manage remote warehouse code in eclipse, prompts to enter passwords are always prompted to enter passwords, which is particularly annoying. After hard work, I finally solved the problem and shared it with you~ 2. Analysis of the password mechanism of the svn plug-in and the cause of the problem. When we use the svn plug-in for the first time and enter the password, a file that saves the password will be generated, and then the svn plug-in will read the username and password information by default every time. When eclipse is started, the configuration information will be automatically read into the program cache. After the password of svn is modified, it is impossible to log in again, and there is no prompt to re-enter the password. At this time, we can delete the relevant configuration files and let the svn plugin prompt us to re-enter the password. However, ec
 How to restore the win8 system details stepsMay 07, 2025 pm 05:00 PM
How to restore the win8 system details stepsMay 07, 2025 pm 05:00 PMThe steps to start system restore in Windows 8 are: 1. Press the Windows key X to open the shortcut menu; 2. Select "Control Panel", enter "System and Security", and click "System"; 3. Select "System Protection", and click "System Restore"; 4. Enter the administrator password and select the restore point. When selecting the appropriate restore point, it is recommended to select the restore point before the problem occurs, or remember a specific date when the system is running well. During the system restore process, if you encounter "The system restore cannot be completed", you can try another restore point or use the "sfc/scannow" command to repair the system files. After restoring, you need to check the system operation status, reinstall or configure the software, and re-back up the data, and create new restore points regularly.
 'Modern Operating System Original Book 3rd Edition'May 07, 2025 pm 04:57 PM
'Modern Operating System Original Book 3rd Edition'May 07, 2025 pm 04:57 PM"Modern Operating Systems (English Edition 3rd Edition)" is a classic work written by Professor Tanenbaum. With his profound experience in the design of three operating systems, the book perfectly integrates theory and practice. The third edition of the book explores a number of topics in depth, such as process, threading, storage management, file systems, I/O deadlock, interface design, multimedia, performance trade-offs, and introduces the latest trends in operating system design. The book not only explains the principles and practices of modern operating systems in detail, but also pays special attention to Linux operating systems, Windows Vista operating systems, embedded operating systems, real-time operating systems and multimedia operating systems. Covering Windows Vista and the latest Linux/Unix operations
 .NET Core Quick Start Tutorial 1. The beginning: Talking about .NET CoreMay 07, 2025 pm 04:54 PM
.NET Core Quick Start Tutorial 1. The beginning: Talking about .NET CoreMay 07, 2025 pm 04:54 PM1. The Origin of .NETCore When talking about .NETCore, we must not mention its predecessor .NET. Java was in the limelight at that time, and Microsoft also favored Java. The Java virtual machine on the Windows platform was developed by Microsoft based on JVM standards. It is said to be the best performance Java virtual machine at that time. However, Microsoft has its own little abacus, trying to bundle Java with the Windows platform and add some Windows-specific features. Sun's dissatisfaction with this led to a breakdown of the relationship between the two parties, and Microsoft then launched .NET. .NET has borrowed many features of Java since its inception and gradually surpassed Java in language features and form development. Java in version 1.6
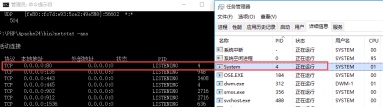 Solve the problem that the 80 port under Windows 10 is occupied by the System with PID 4May 07, 2025 pm 04:51 PM
Solve the problem that the 80 port under Windows 10 is occupied by the System with PID 4May 07, 2025 pm 04:51 PM1. Background Recently, out of curiosity, I updated the Windows 10 system, which is very easy to operate and the experience is quite good. However, when developing in IDEA, when starting the project using port 80, it is found that the port has been occupied. After some attempts, I found a solution and I will share it with you. 2. Solution steps 1. Check the process number PID that occupies port 80 by executing the netstat-ano|findstr "80" command. 2. Since port 80 is occupied by system services, the process cannot be terminated directly. Therefore, use the netshhttpshowservicestate command to view the current HTTP service status. The result is as shown in the figure: from the figure
 10 latest tools for web developersMay 07, 2025 pm 04:48 PM
10 latest tools for web developersMay 07, 2025 pm 04:48 PMWeb development design is a promising career field. However, this industry also faces many challenges. As more businesses and brands turn to the online marketplace, web developers have the opportunity to demonstrate their skills and succeed in their careers. However, as demand for web development continues to grow, the number of developers is also increasing, resulting in increasingly fierce competition. But it’s exciting that if you have the talent and will, you can always find new ways to create unique designs and ideas. As a web developer, you may need to keep looking for new tools and resources. These new tools and resources not only make your job more convenient, but also improve the quality of your work, thus helping you win more business and customers. The trends of web development are constantly changing.


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 English version
Recommended: Win version, supports code prompts!

Atom editor mac version download
The most popular open source editor





