 Hardware Tutorial
Hardware Tutorial Hardware News
Hardware News Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devicesUnpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices

An unpatchable Yubico two-factor authentication key vulnerability has broken the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. The Feitian A22 JavaCard and other devices using Infineon SLB96xx series TPMs are also vulnerable.All vulnerable 2FA keys should be assumed compromised and replaced with non-vulnerable ones as soon as possible.
Two-factor (2FA) security authentication uses a unique code generated by a software app (e.g. Microsoft Authenticator) or a hardware key (e.g. Yubikey) in addition to a password to log into online accounts. A growing number of account providers, such as banks, have implemented 2FA security in order to reduce the theft of data and money.
Two-factor authentication keys depend on the generation of a unique code using methods that are difficult to reverse engineer. Modern 2FA apps and keys often use more complex math such as elliptic curve algorithms (deep dive into the mathematics at IBM's site).
Side-channel attacks monitor aspects of an electronic device to create an attack. For the vulnerable Infineon TPM chips used in the Yubico, Feitian, and other 2FA keys, the researchers at Ninjalabs spent two years capturing and deciphering the radio emissions from the chips to create an attack.
Hackers would need up to an hour of access to the key to capture the radio emissions, then a day or two to decipher the data and create a copy of the 2FA key. The math and techniques are rather complex, so readers with know-how in cryptography, math, and electronics can read the complex methods in the NinjaLab's article. NinjaLab previously revealed similar vulnerabilities in other Google Titan, Feitian, Yubico, and NXP keys.
Users of Yubico 2FA keys should consult the Yubico security advisoryto see if their keys are vulnerable. Users of other devices will need to ask the makers if the devices use vulnerable Infineon SLB96xx series TPMs. Affected devices cannot be patched to fix the security vulnerability.
All affected key owners should strongly consider switching to alternatives after confirming the alternatives are not vulnerable. Alternative 2FA keys include the Feitian or iShield.



The above is the detailed content of Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. For more information, please follow other related articles on the PHP Chinese website!
 Review: Dio Node Aims to Bring Cost-Effective AirPlay Speakers to Your Entire HomeApr 15, 2025 am 06:12 AM
Review: Dio Node Aims to Bring Cost-Effective AirPlay Speakers to Your Entire HomeApr 15, 2025 am 06:12 AMDio is a small company focused on delivering a single product for the Apple ecosystem: a low-cost AirPlay speaker system known as Dio Node. Initially launched as a crowdfunded Indiegogo campaign back in 2022, the Dio Node began shipping to backers la
 How to Find Your Apple TV Siri Remote Using Your iPhoneApr 15, 2025 am 01:07 AM
How to Find Your Apple TV Siri Remote Using Your iPhoneApr 15, 2025 am 01:07 AMIn iOS 17 and tvOS 17 and later, Apple includes a feature that lets Apple TV users locate a misplaced Siri Remote using their iPhone. Keep reading to learn how it's done.Prior to the launch of the latest Apple TV 4K, there were rumors that Apple wo
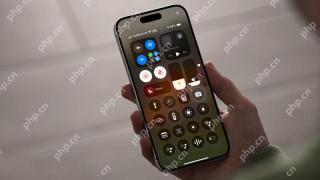 Worried About iPhone Privacy? Do This With Control CenterApr 15, 2025 am 12:59 AM
Worried About iPhone Privacy? Do This With Control CenterApr 15, 2025 am 12:59 AMIn iOS, the Control Center can be used to quickly take a picture, jot down a note, turn on the lights, control your Apple TV, and much more. It's useful and convenient because you don't even have to unlock your iPhone or iPad to use it. However, with
 Razer PC Remote Play lets you stream games to your iPhone – and it could convince me to switch from my gaming PCApr 12, 2025 am 09:32 AM
Razer PC Remote Play lets you stream games to your iPhone – and it could convince me to switch from my gaming PCApr 12, 2025 am 09:32 AMRazer has launched its PC Remote Play game streaming serviceThis lets you stream games from your PC to a mobile deviceIt comes with optimization features and works with controllersI love my gaming PC, but it’s not the most portable device in the wo
 All the best PS5 controllers we recommend shopping for during Black Friday this weekApr 12, 2025 am 09:02 AM
All the best PS5 controllers we recommend shopping for during Black Friday this weekApr 12, 2025 am 09:02 AMThe best PS5 controllers aren't as abundant as other platforms when it comes to overall choice. That's obviously a bit of a shame, but what is available is still absolutely worth a look - especially if you're in the market for a DualSense alternative
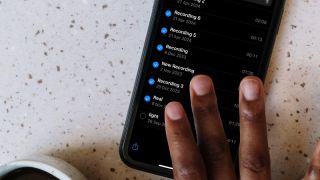 Select Faster on iPhone With This Two-Finger TrickApr 12, 2025 am 12:53 AM
Select Faster on iPhone With This Two-Finger TrickApr 12, 2025 am 12:53 AMYour iPhone has multiple touch and gesture capabilities that can enhance how you interact with apps. Some, like pinch and zoom, are well known enough to be considered second nature, but others are less obvious, like the one we're about to explain.Two
 How to Adjust Mac Volume and Brightness More PreciselyApr 11, 2025 pm 09:01 PM
How to Adjust Mac Volume and Brightness More PreciselyApr 11, 2025 pm 09:01 PMOn a Mac that has a top row of function keys, Apple includes volume and brightness controls that can be used to make adjustments in stepwise increments. However, there may be times when you want to make more fine grained adjustments to these settings
 The best JRPGs to play in 2025Apr 11, 2025 am 11:39 AM
The best JRPGs to play in 2025Apr 11, 2025 am 11:39 AMThe best JRPGs (Japanese role-playing games) in 2025 use theatrical storytelling and vibrant ensemble casts to weave powerful experiences that stay with us long after we put the controller down.Contrary to the name, JRPGs aren't necessarily all from


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Zend Studio 13.0.1
Powerful PHP integrated development environment

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.




