Understand ansible architecture and working principles
Ansible is a model-driven configuration manager that supports multi-node publishing and remote task execution. By default, SSH is used for remote connections. There is no need to install additional software on managed nodes and it can be extended using a variety of programming languages.

The picture above shows the basic architecture of ansible. From the picture above, you can understand that it consists of the following parts:
- Core: ansible
- Core Modules: These are the modules that come with ansible
- Extension modules (Custom Modules): If the core module is not enough to complete a certain function, you can add extension modules
- Plugins: Complete the supplement of module functions
- Playbooks: Ansible's task configuration file, which defines multiple tasks in the playbook and is automatically executed by ansible
- Connectior Plugins: ansible connects to each host based on connection plug-ins. Although ansible uses ssh to connect to each host, it also supports other connection methods, so a connection plug-in is required
- Host Inventory: Define the hosts managed by ansible


The above are two ansible working principle diagrams found on the Internet. Both diagrams are basically expansions based on the architecture diagram. You can understand from the picture above:
1. The management terminal supports three ways to connect to the managed terminal: local, ssh, and zeromq. The default is to use the ssh-based connection---this part corresponds to the connection module in the basic architecture diagram;
2. Host Inventory (host group) can be classified according to application type, etc. The management node implements corresponding operations through various modules - a single module, batch execution of a single command, we can call it ad-hoc ;
3. The management node can use playbooks to implement a collection of multiple tasks to implement a type of functions, such as the installation and deployment of web services, batch backup of database servers, etc. We can simply understand playbooks as configuration files that the system operates by combining multiple ad-hoc operations.
After installing ansible, we found that ansible provides us with seven instructions in total: ansible, ansible-doc, ansible-galaxy, ansible-lint, ansible-playbook, ansible-pull, ansible-vault. Here we only look at the usage part, and the detailed part can be obtained through the "command -h" method.
1.[root@localhost ~]# ansible -h 2.Usage: ansible [options]
Ansible is the core part of the command, which is mainly used to execute ad-hoc commands, that is, a single command. By default, the host and options parts need to be followed. When the module is not specified by default, the command module is used. Such as:
1.[root@361way.com ~]# ansible 192.168.0.102 -a 'date' 2192.168.0.102 | success | rc=0 >> 3Tue May 12 22:57:24 CST 2015
However, the default module can be modified in ansible.cfg. The parameters under the ansible command are explained as follows:
- Parameters:
- -a 'Arguments', --args='Arguments' command line parameters
- -m NAME, --module-name=NAME The name of the execution module. The command module is used by default, so if you only execute a single command, you do not need the -m parameter
- -i PATH, --inventory=PATH specifies the path to the inventory host file, the default is /etc/ansible/hosts.
- -u Username, --user=Username execution user, use this remote username instead of the current user
- -U --sud-user=SUDO_User Which user to sudo to, the default is root
- -k --ask-pass login password, prompt for SSH password instead of assuming key-based authentication
- -K --ask-sudo-pass prompts for password use sudo
- -s --sudo sudo run
- -S --su Use su command
- -l --list displays all supported modules
- -s --snippet specifies the module to display script snippets
- -f --forks=NUM Number of parallel tasks. NUM is specified as an integer, the default is 5. #ansible testhosts -a "/sbin/reboot" -f 10 Restart all machines in the testhosts group, 10 machines at a time
- --private-key=PRIVATE_KEY_FILE private key path, use this file to verify the connection
- -v --verbose details
- all executes for all hosts defined by hosts
- -M MODULE_PATH, --module-path=MODULE_PATH The path of the module to be executed, the default is /usr/share/ansible/
- --list-hosts only prints which hosts will execute this playbook file, not actually executes the playbook file
- -o --one-line compressed output, summarized output. Try to output everything on one line.
- -t Directory, --tree=Directory Save the contents in this output directory, saving the results in a file on each host.
- -B background running timeout
- -P Investigate background program time
- -T Seconds, --timeout=Seconds time in seconds
- -P NUM, --poll=NUM Poll background work every few seconds. Required - b
- -c Connection, --connection=Connection connection type to use. Possible options are paramiko(SSH), SSH and local. Local is mainly used for crontab or startup.
- --tags=TAGS Only execute the task with the specified tags Example: ansible-playbook test.yml --tags=copy Only execute the task with the tag copy
- --list-hosts only prints which hosts will execute this playbook file, not actually executes the playbook file
- --list-tasks List all tasks that will be executed
- -C, --check just tests what will be changed and will not actually execute it; instead, it tries to predict some possible changes
- --syntax-check Perform syntax check of the script, but do not execute it
- -l SUBSET, --limit=SUBSET further limit the selected host/group mode --limit=192.168.0.15 Only execute this ip
- --skip-tags=SKIP_TAGS Only run plays and tasks with tags that do not match these values --skip-tags=copy_start
- -e EXTRA_VARS, --extra-vars=EXTRA_VARS Extra variables set as key=value or YAML/JSON
- #cat update.yml
- ---
- - hosts: {{ hosts }}
- remote_user: {{ user }}
- ............
- #ansible-playbook update.yml --extra-vars "hosts=vipers user=admin" Pass {{hosts}}, {{user}} variables, hosts can be ip or group name
- -l,--limit Execute tasks on the specified host/group--limit=192.168.0.10, 192.168.0.11 or -l 192.168.0.10, 192.168.0.11 Execute tasks only on these 2 IPs
# ansible-doc -h Usage: ansible-doc [options] [module...]
该指令用于查看模块信息,常用参数有两个-l 和 -s ,具体如下:
- //列出所有已安装的模块
- # ansible-doc -l
- //查看具体某模块的用法,这里如查看command模块
- # ansible-doc -s command
# ansible-galaxy -h Usage: ansible-galaxy [init|info|install|list|remove] [--help] [options] ...
ansible-galaxy 指令用于方便的从https://galaxy.ansible.com/ 站点下载第三方扩展模块,我们可以形象的理解其类似于centos下的yum、python下的pip或easy_install 。如下示例:
[root@localhost ~]# ansible-galaxy install aeriscloud.docker - downloading role 'docker', owned by aeriscloud - downloading role from https://github.com/AerisCloud/ansible-docker/archive/v1.0.0.tar.gz - extracting aeriscloud.docker to /etc/ansible/roles/aeriscloud.docker - aeriscloud.docker was installed successfully
这个安装了一个aeriscloud.docker组件,前面aeriscloud是galaxy上创建该模块的用户名,后面对应的是其模块。在实际应用中也可以指定txt或yml 文件进行多个组件的下载安装。这部分可以参看官方文档。
ansible-lint是对playbook的语法进行检查的一个工具。用法是ansible-lint playbook.yml 。
该指令是使用最多的指令,其通过读取playbook 文件后,执行相应的动作,这个后面会做为一个重点来讲。
该指令使用需要谈到ansible的另一种模式---pull 模式,这和我们平常经常用的push模式刚好相反,其适用于以下场景:你有数量巨大的机器需要配置,即使使用非常高的线程还是要花费很多时间;你要在一个没有网络连接的机器上运行Anisble,比如在启动之后安装。这部分也会单独做一节来讲。
ansible-vault主要应用于配置文件中含有敏感信息,又不希望他能被人看到,vault可以帮你加密/解密这个配置文件,属高级用法。主要对于playbooks里比如涉及到配置密码或其他变量时,可以通过该指令加密,这样我们通过cat看到的会是一个密码串类的文件,编辑的时候需要输入事先设定的密码才能打开。这种playbook文件在执行时,需要加上 --ask-vault-pass参数,同样需要输入密码后才能正常执行。具体该部分可以参查官方博客。
注:上面七个指令,用的最多的只有两个ansible 和ansible-playbook ,这两个一定要掌握,其他五个属于拓展或高级部分。
The above is the detailed content of Understand ansible architecture and working principles. For more information, please follow other related articles on the PHP Chinese website!
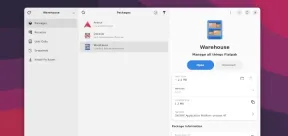 Warehouse: A GUI for Effortlessly Handling Flatpak AppsMay 09, 2025 am 11:30 AM
Warehouse: A GUI for Effortlessly Handling Flatpak AppsMay 09, 2025 am 11:30 AMA GUI for Effortless Flatpak Management: Introducing Warehouse Managing a growing collection of Flatpak applications can be cumbersome using only the command line. Enter Warehouse, a user-friendly graphical interface designed to streamline Flatpak a
 8 Powerful Linux Commands to Identify Hard Drive BottlenecksMay 09, 2025 am 11:03 AM
8 Powerful Linux Commands to Identify Hard Drive BottlenecksMay 09, 2025 am 11:03 AMThis article provides a comprehensive guide to identifying and resolving hard drive bottlenecks in Linux systems. Experienced server administrators will find this particularly useful. Slow disk operations can severely impact application performance,
 4 Best QR Code Generators for Linux UsersMay 09, 2025 am 10:27 AM
4 Best QR Code Generators for Linux UsersMay 09, 2025 am 10:27 AMEfficient QR code generation tool under Linux system In today's digital world, QR codes have become a way to quickly and conveniently share information, simplifying data access from URLs, texts, contacts, Wi-Fi credentials, and even payment information. Linux users can use a variety of tools to create QR codes efficiently. Let's take a look at some popular QR code generators that can be used directly on Linux systems. QRencode QRencode is a lightweight command line tool for generating QR codes on Linux. It is well-received for its simplicity and efficiency and is popular with Linux users who prefer direct methods. Using QRencode, you can use the URL,
 elementary OS 8: A User-Friendly Linux for macOS and WindowsMay 09, 2025 am 10:19 AM
elementary OS 8: A User-Friendly Linux for macOS and WindowsMay 09, 2025 am 10:19 AMElementary OS 8 Circe: A Smooth and Stylish Linux Experience Elementary OS, a Ubuntu-based Linux distribution, has evolved from a simple theme pack into a fully-fledged, independent operating system. Known for its user-friendly interface, elegant de
 40 Linux Commands for Every Machine Learning EngineerMay 09, 2025 am 10:06 AM
40 Linux Commands for Every Machine Learning EngineerMay 09, 2025 am 10:06 AMMastering Linux is crucial for any machine learning (ML) engineer. Its command-line interface offers unparalleled flexibility and control, streamlining workflows and boosting productivity. This article outlines essential Linux commands, explained fo
 Arch Linux Cheat Sheet: Essential Commands for BeginnersMay 09, 2025 am 09:54 AM
Arch Linux Cheat Sheet: Essential Commands for BeginnersMay 09, 2025 am 09:54 AMArch Linux: A Beginner's Command-Line Cheat Sheet Arch Linux offers unparalleled control but can feel daunting for newcomers. This cheat sheet provides essential commands to confidently manage your system. System Information & Updates These com
 How to Install Scikit-learn for Machine Learning on LinuxMay 09, 2025 am 09:53 AM
How to Install Scikit-learn for Machine Learning on LinuxMay 09, 2025 am 09:53 AMThis guide provides a comprehensive walkthrough of installing and using the Scikit-learn machine learning library on Linux systems. Scikit-learn (sklearn) is a powerful, open-source Python library offering a wide array of tools for various machine l
 How to Install Kali Linux Tools in UbuntuMay 09, 2025 am 09:46 AM
How to Install Kali Linux Tools in UbuntuMay 09, 2025 am 09:46 AMThis guide explains how to leverage Docker for accessing Kali Linux tools, a safer and more efficient alternative to outdated methods like Katoolin. Katoolin is no longer actively maintained and may cause compatibility problems on modern systems. Do


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Atom editor mac version download
The most popular open source editor

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

WebStorm Mac version
Useful JavaScript development tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function






