 Mobile Tutorial
Mobile Tutorial Mobile News
Mobile News Google Pixel series phones have been exposed to security vulnerabilities: they can remotely execute code and install malware
Google Pixel series phones have been exposed to security vulnerabilities: they can remotely execute code and install malwareIT Home News on August 16th, technology blog iVerify published a blog post yesterday (August 15th), reporting that Google Pixel series mobile phones have security vulnerabilities that, if exploited by attackers, can remotely execute code, install malware, etc. Summary of the Vulnerability The vulnerability is rooted in a third-party Android software package called Showcase.apk, developed by Smith Micro to help Verizon set phones in stores into retail demo mode. IT House cited the media report that the application can not only remotely execute code and install software, but also download configuration files through unencrypted HTTP network connections, which means hackers can use this vulnerability to hijack Pixel devices. Verizon no longer uses Showcase, but the APK is still included in the Android version of Google Pixel smartphones. Scope of Impact Google has pre-installed the application on several previous Pixel phones, but the latest Pixel 9 series phones have removed the application and are therefore not affected. Fix Google disclosed the vulnerability in May this year and has not yet fixed it, but Google said it plans to remove the app through an update.

The above is the detailed content of Google Pixel series phones have been exposed to security vulnerabilities: they can remotely execute code and install malware. For more information, please follow other related articles on the PHP Chinese website!
 Nubia Flip 2 is launched: Deeply integrating the DeepSeek big model, priced starting from 3,399 yuanMar 12, 2025 pm 01:21 PM
Nubia Flip 2 is launched: Deeply integrating the DeepSeek big model, priced starting from 3,399 yuanMar 12, 2025 pm 01:21 PMNubia released its first folding screen mobile phone Flip2 of the year, priced from 3,399 yuan and starting from 2,899 yuan after the state subsidy. This mobile phone deeply integrates the DeepSeek big model with 671 billion parameters, and innovatively proposes the concept of "AITogether". Through the intelligent scheduling system of the Nebula Engine, it realizes the coordinated operation of multiple expert big models, bringing users a new experience in AI interaction, image creation and office efficiency. Flip2 supports voice commands to automatically match the best AI services without the need to start the application separately. Its 3.0-inch vertical external screen is compatible with more than 300 applications and supports split-screen operation in folded state. The industry's first full voice AI cute pet system supports anthropomorphic dialogue and 3D dynamic interaction, and can be used with L
 The industry's first full-size embedded DeepSeek small fold in 2025! Nubia Flip 2 debutsMar 12, 2025 pm 01:27 PM
The industry's first full-size embedded DeepSeek small fold in 2025! Nubia Flip 2 debutsMar 12, 2025 pm 01:27 PMOn March 4, Nubia Flip2 was officially released. This phone is the industry's first national-level small folding screen phone with a built-in full-size DeepSeek big model. The Nubia Flip2 system deeply integrates a full-size DeepSeek model with 671 billion parameters. It can search through intelligent networking and quickly call it with one click without downloading or launching the application separately. This function has stronger performance, faster operation speed and more stable. Users only need to expand their phone, press and hold the power button or enter the voice interaction mode through the smart voice app, and say keywords such as "think deeply" and "deep reasoning". The system can perform fuzzy matching and automatically enable DeepSeek to generate content. Nubia's first proposed "AITogether" theory
 Fliggy's 'AI Itinerary Assistant' will be launched soon, integrating DeepSeek and Tongyi Qianwen's main modelMar 12, 2025 pm 01:15 PM
Fliggy's 'AI Itinerary Assistant' will be launched soon, integrating DeepSeek and Tongyi Qianwen's main modelMar 12, 2025 pm 01:15 PMFliggy launched the "AI Itinerary Assistant" on March 5, integrating the capabilities of DeepSeek-R1 and Alibaba Cloud Tongyi Qianwen's big model, becoming the first AI product in the online travel industry that integrates multiple big models. The product will be fully opened after a brief internal test. Users only need to click "Ask" in the itinerary bar at the bottom of the Fliggy App to experience it. Fliggy said that the "AI Itinerary Assistant" can quickly respond to user needs, provide itinerary inspiration, planning suggestions, gameplay recommendations and product screening, and generate personalized and detailed interesting itinerary plans, greatly saving users time to collect information and organize strategies. In addition, new features will be updated intensively within the next three months. To optimize the user experience, "AI Itinerary Assistant" not only provides text Q&A, but also generates an exclusive route map based on the answers.
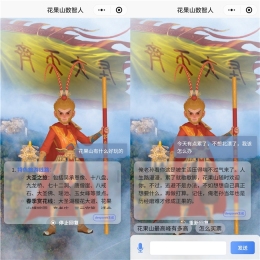 The first dual-core cultural and tourism digital hominid in the country! Tencent Cloud helps Huaguoshan Scenic Area connect to DeepSeek, making the 'Sage Monkey King' smarter and warmerMar 12, 2025 pm 12:57 PM
The first dual-core cultural and tourism digital hominid in the country! Tencent Cloud helps Huaguoshan Scenic Area connect to DeepSeek, making the 'Sage Monkey King' smarter and warmerMar 12, 2025 pm 12:57 PMLianyungang Huaguoshan Scenic Area joins hands with Tencent Cloud to launch the first "dual-core brain" Digital Homo sapiens in the cultural and tourism industry - Monkey King! On March 1, the scenic spot officially connected the Monkey King to the DeepSeek platform, so that it has the two AI model capabilities of Tencent Hunyuan and DeepSeek, bringing tourists a smarter and more considerate service experience. Huaguoshan Scenic Area has previously launched the Monkey King of the Digital Homo sapiens based on Tencent Hunyuan model. This time, Tencent Cloud further utilizes technologies such as the big model knowledge engine to connect it to DeepSeek to achieve a "dual-core" upgrade. This makes the Monkey King's interactive ability to a higher level, faster response speed, stronger understanding ability, and more warmth. Monkey King has strong natural language processing capabilities and can understand various ways of asking questions from tourists.
 The Samsung Galaxy S25 series mobile phones in China officially announced that they support the DeepSeek-R1 model, and you can experience it by entering the AI 'intelligent center'Mar 12, 2025 pm 01:36 PM
The Samsung Galaxy S25 series mobile phones in China officially announced that they support the DeepSeek-R1 model, and you can experience it by entering the AI 'intelligent center'Mar 12, 2025 pm 01:36 PMSamsung Galaxy S25 domestic version ushers in AI upgrade! Samsung China officially announced that the Galaxy S25 series officially integrates the DeepSeek-R1 big model, significantly enhancing AI capabilities. There is no need to download additional applications or register an account. Users only need to update Samsung Life Assistant to the latest version, or enable the DeepSeek-R1 intelligent body through the Samsung Smart Homepage (negative one screen) and Samsung Bixby's "Artificial Body Center". The experience includes functions such as in-depth thinking, network search, emotional value analysis, context memory, and image recognition. In addition, Samsung also revealed that Bixby's "language chat visual" function will be launched soon, which will further improve Bixby's emotional interaction capabilities and provide a more comprehensive AI experience.


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

Zend Studio 13.0.1
Powerful PHP integrated development environment

Atom editor mac version download
The most popular open source editor

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

Dreamweaver Mac version
Visual web development tools




