Slow Mist: X Account Security Troubleshooting and Reinforcement Guide
- PHPzOriginal
- 2024-08-01 00:15:031145browse
Author: Yao, Slow Mist Technology
Background Overview
Recent incidents of Web3 project developers/celebrities’ X accounts being stolen and used to send phishing tweets have occurred frequently. Hackers are good at using various means to steal To obtain user accounts, the more common routines are as follows:
- induce users to click on fake Calendly/Kakao meeting reservation links, thereby stealing user account authorization or controlling the user’s device;
- private messages to trick users into downloading Trojans Programs (fake games, conference programs, etc.), in addition to stealing private keys/mnemonic phrases, Trojans may also steal X account permissions;
- Use SIM Swap attacks to steal X account permissions that rely on mobile phone numbers.
The SlowMist security team has assisted in resolving many similar incidents. For example, on July 20, the account of TinTinLand project party X was stolen, and the attacker pinned a tweet containing a phishing link. With the assistance of the SlowMist security team, TinTinLand promptly solved the problem of account theft and conducted authorization review and security reinforcement of the X account.

Considering the frequent occurrence of victims, many users do not know much about how to enhance the security of the Specific steps.
Authorization troubleshooting
Let’s take the Web side as an example. After opening the x.com page, click "More" on the sidebar and find the "Settings and privacy" option. This is mainly used to set the security and privacy of the account. privacy.


After entering the "Settings" column, select "Security and account access" to set up the security and authorized access of the account.
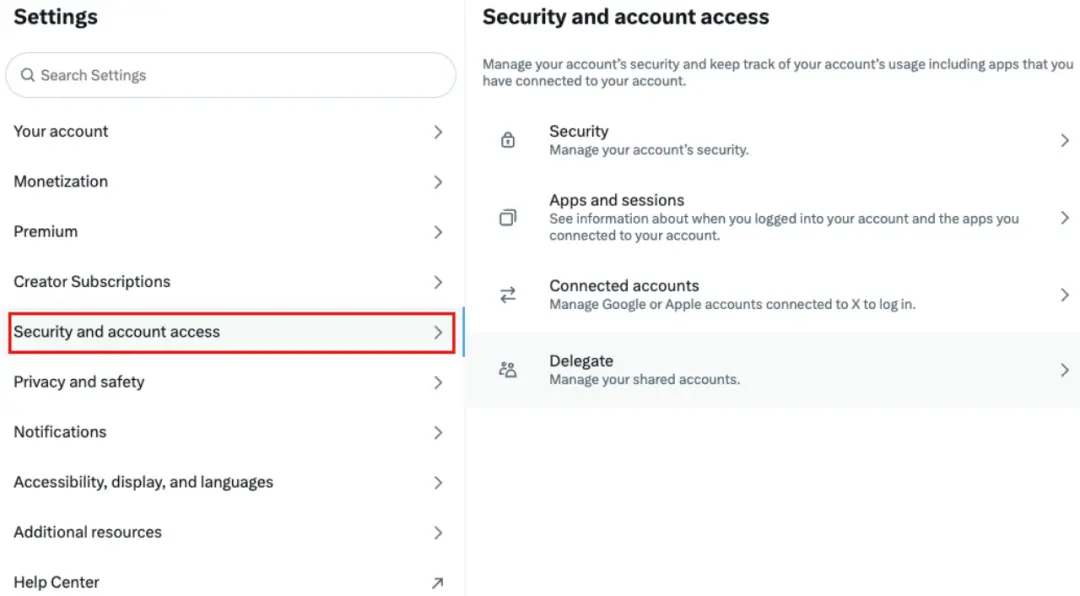
View authorized applications
Many phishing methods use users to mistakenly click on authorized application links, causing the X account's tweeting permission to be authorized, and then the account is used to send phishing messages.
Troubleshooting method: Select the "Apps and sessions" column to check which applications the account has been authorized to, as shown below, the demo account has been authorized to these 3 applications.

After selecting a specific application, you can see the corresponding permissions. Users can remove permissions through "Revoke app permissions".

Check the delegation status
Troubleshooting method: Settings → Security and account access → Delegate

If you find that the current account has enabled invitation management, you need to enter "Members you've" "delegated" to check which accounts the current account is shared with, and cancel delegation as soon as possible after sharing is no longer needed.

Check the abnormal login log
If the user suspects that the account has been logged in maliciously, they can check the login log to check the device, date and location of the abnormal login.
Troubleshooting method: Settings → Security and account access → Apps and sessions → Account access history
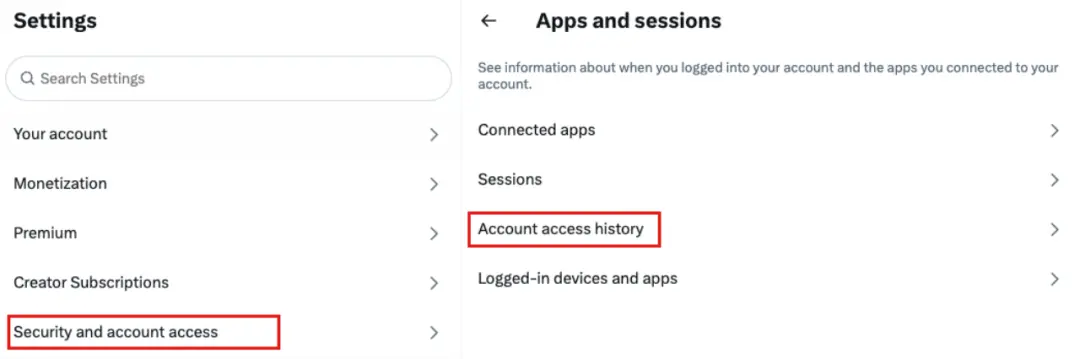
As shown below, enter Account access history to view the model, login date, IP and region of the logged-in device. If If abnormal login information is found, it means that the account may have been stolen.

Check the login device
If a malicious login occurs after the X account is stolen, the user can check the login device of the current account and then kick the malicious login device offline.
Troubleshooting method: Select "Log out the device shown" to log out the account from a device.


Security Settings
2FA Verification
Users can turn on 2FA verification to enable double verification insurance for their accounts to avoid the risk of their accounts being taken over directly after password leaks.
Configuration method: Settings → Security and account access → Security→ Two-factor authentication

You can set up the following 2FA to enhance the security of your account, such as SMS verification code, authenticator and security key .

額外的密碼保護
除了設定帳號密碼和 2FA 外,用戶還可以開啟額外的密碼保護來進一步增強X帳號安全性。
設定方法:Settings → Security and account access → Security → Additional password protection

登入用戶定期根據排查步驟對X帳號進行授權排查,以加強帳號的安全性,降低被駭客攻擊的風險。如果發現帳號被黑,請立即採取措施,修改帳號密碼,進行授權排查,撤銷可疑授權,並對帳號進行安全增強設定。
The above is the detailed content of Slow Mist: X Account Security Troubleshooting and Reinforcement Guide. For more information, please follow other related articles on the PHP Chinese website!

